ALL of the following options are provided by the GAiA sysconfig utility, EXCEPT:
When using AD Query to authenticate users for Identity Awareness, identity data is received seamlessly from the Microsoft Active Directory (AD). What is NOT a recommended usage of this method?
Which of the following methods is NOT used by Identity Awareness to catalog identities?
How are locally cached usernames and passwords cleared from the memory of a R77 Security Gateway?
During which step in the installation process is it necessary to note the fingerprint for first-time verification?
The customer has a small Check Point installation which includes one Windows 2008 server as SmartConsole and Security Management Server with a second server running GAiA as Security Gateway. This is an example of a(n):
Which R77 SmartConsole tool would you use to verify the installed Security Policy name on a Security Gateway?
Which of the following items should be configured for the Security Management Server to authenticate via LDAP?
An Administrator without access to SmartDashboard installed a new IPSO-based R77 Security Gateway over the weekend. He e-mailed you the SIC activation key and the IP address of the Security Gateway. You want to confirm communication between the Security Gateway and the Management Server by installing the Policy. What might prevent you from installing the Policy?
How granular may an administrator filter an Access Role with identity awareness? Per:
MegaCorp’s security infrastructure separates Security Gateways geographically. You must request a central license for one remote Security Gateway.
How do you apply the license?
Suppose the Security Gateway hard drive fails and you are forced to rebuild it. You have a snapshot file stored to a TFTP server and backups of your Security Management Server.
What is the correct procedure for rebuilding the Gateway quickly?
You have just installed your Gateway and want to analyze the packet size distribution of your traffic with SmartView Monitor.
Unfortunately, you get the message.
"There are no machines that contain Firewall Blade and SmartView Monitor."
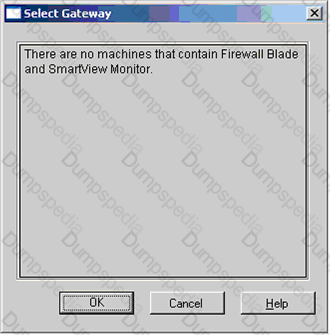
What should you do to analyze the packet size distribution of your traffic? Give the BEST answer.
You have detected a possible intruder listed in SmartView Tracker’s active pane. What is the fastest method to block this intruder from accessing your network indefinitely?
You manage a global network extending from your base in Chicago to Tokyo, Calcutta and Dallas. Management wants a report detailing the current software level of each Enterprise class Security Gateway. You plan to take the opportunity to create a proposal outline, listing the most cost-effective way to upgrade your Gateways.
Which two SmartConsole applications will you use to create this report and outline?
Identify the correct step performed by SmartUpdate to upgrade a remote Security Gateway. After selecting Packages > Distribute and Install Selected Package and choosing the target Gateway, the:
Jennifer McHanry is CEO of ACME. She recently bought her own personal iPad. She wants use her iPad to access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the R77 Firewall Rule Base.
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network destinations. Select accept as the Action.
Ms. McHanry tries to access the resource but is unable. What should she do?
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop with a static IP (10.0.0.19). He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
3) Changes from static IP address to DHCP for the client PC.
What should John do when he cannot access the web server from a different personal computer?
You want to generate a cpinfo file via CLI on a system running GAiA. This will take about 40 minutes since the log files are also needed.
What action do you need to take regarding timeout?
Your users are defined in a Windows 2008 R2 Active Directory server. You must add LDAP users to a Client Authentication rule. Which kind of user group do you need in the Client Authentication rule in R77?
Where is the easiest and BEST place to find information about connections between two machines?
Which of the following items should be configured for the Security Management Server to authenticate using LDAP?
Complete this statement from the options provided. Using Captive Portal, unidentified users may be either; blocked, allowed to enter required credentials, or required to download the _____________.
You are conducting a security audit. While reviewing configuration files and logs, you notice logs accepting POP3 traffic, but you do not see a rule allowing POP3 traffic in the Rule Base. Which of the following is the most likely cause?
When you change an implicit rule’s order from Last to First in Global Properties, how do you make the change take effect?
In SmartView Tracker, which rule shows when a packet is dropped due to anti-spoofing?
SmartView Monitor is mainly for which kind of work –
1. Monitoring Performance and traffic
2. Provision Package
3. Managing licenses
4. Managing VPN Tunnels
A host on the Internet initiates traffic to the Static NAT IP of your Web server behind the Security Gateway. With the default settings in place for NAT, the initiating packet will translate the _________.
The fw monitor utility is used to troubleshoot which of the following problems?
Lilly needs to review VPN History counters for the last week.
Where would she do this?
Peter is your new Security Administrator. On his first working day, he is very nervous and enters the wrong password three times. His account is locked.
What can be done to unlock Peter’s account? Give the BEST answer.
Which feature or command provides the easiest path for Security Administrators to revert to earlier versions of the same Security Policy and objects configuration?
The customer has a small Check Point installation which includes one Windows 7 workstation as the SmartConsole, one GAiA device working as Security Management Server, and a third server running SecurePlatform as Security Gateway. This is an example of a(n):
With the User Directory Software Blade, you can create R77 user definitions on a(n) _________ Server.
When configuring anti-spoofing on the Security Gateway object interfaces, which of the following is NOT a valid R77 topology configuration?
Your shipping company uses a custom application to update the shipping distribution database. The custom application includes a service used only to notify remote sites that the distribution database is malfunctioning. The perimeter Security Gateway’s Rule Base includes a rule to accept this traffic. Since you are responsible for multiple sites, you want notification by a text message to your cellular phone, whenever traffic is accepted on this rule. Which of the following would work BEST for your purpose?
Which SmartConsole component can Administrators use to track changes to the Rule Base?
If you were NOT using IKE aggressive mode for your IPsec tunnel, how many packets would you see for normal Phase 1 exchange?