R80 Security Management Server can be installed on which of the following operating systems?
Administrator wishes to update IPS from SmartConsole by clicking on the option “update now” under the IPS tab. Which device requires internet access for the update to work?
Which of the following is NOT an element of VPN Simplified Mode and VPN Communities?
Fill in the blank: RADIUS Accounting gets ______ data from requests generated by the accounting client
Fill in the blank: A _______ is used by a VPN gateway to send traffic as if it were a physical interface.
Which type of Endpoint Identity Agent includes packet tagging and computer authentication?
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his desktop with a static IP (10.0.0.19). He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
3) Changes from static IP address to DHCP for the client PC.
What should John request when he cannot access the web server from his laptop?
Which of the following authentication methods can be configured in the Identity Awareness setup wizard?
The system administrator of a company is trying to find out why acceleration is not working for the traffic. The traffic is allowed according to the rule base and checked for viruses. But it is not accelerated. What is the most likely reason that the traffic is not accelerated?
The WebUI offers three methods for downloading Hotfixes via CPUSE. One of them is Automatic method. How many times per day will CPUSE agent check for hotfixes and automatically download them?
As a Security Administrator, you must refresh the Client Authentication authorized time-out every time a new user connection is authorized. How do you do this? Enable the Refreshable Timeout setting:
Which of the following is NOT a valid option when configuring access for Captive Portal?
Which of the following are available SmartConsole clients which can be installed from the R77 Windows CD? Read all answers and select the most complete and valid list.
Which of the following is NOT an option for internal network definition of Anti-spoofing?
How would you deploy TE250X Check Point appliance just for email traffic and in-line mode without a Check Point Security Gateway?
During the Check Point Stateful Inspection Process, for packets that do not pass Firewall Kernel Inspection and are rejected by the rule definition, packets are:
Vanessa is expecting a very important Security Report. The Document should be sent as an attachment via e-mail. An e-mail with Security_report.pdf file was delivered to her e-mail inbox. When she opened the PDF file, she noticed that the file is basically empty and only few lines of text are in it. The report is missing some graphs, tables and links. Which component of SandBlast protection is her company using on a Gateway?
If the first packet of an UDP session is rejected by a security policy, what does the firewall send to the client?
Where does the security administrator activate Identity Awareness within SmartDashboard?
When logging in for the first time to a Security management Server through SmartConsole, a fingerprint is saved to the:
Which of the following is NOT a valid application navigation tab in the R80 SmartConsole?
The default method for destination NAT is _____________, where NAT occurs on the Inbound interface closest to the client.
Fill in the blank: The _________ software blade enables Application Security policies to allow, block, or limit website access based on user, group, and machine identities.
You installed Security Management Server on a computer using GAiA in the MegaCorp home office. You use IP address 10.1.1.1. You also installed the Security Gateway on a second GAiA computer, which you plan to ship to another Administrator at a MegaCorp hub office. What is the correct order for pushing SIC certificates to the Gateway before shipping it?
1. Run cpconfig on the Gateway, select Secure Internal Communication, enter the activation key, and reconfirm.
2. Initialize Internal Certificate Authority (ICA) on the Security Management Server.
3. Configure the Gateway object with the host name and IP addresses for the remote site.
4. Click the Communication button in the Gateway object's General screen, enter the activation key, and click Initialize and OK.
5. Install the Security Policy.
You are the Check Point administrator for Alpha Corp with an R80 Check Point estate. You have received a call by one of the management users stating that they are unable to browse the Internet with their new tablet connected to the company Wireless. The Wireless system goes through the Check Point Gateway. How do you review the logs to see what the problem may be?
After the initial installation on Check Point appliance, you notice that the Management interface and default gateway are incorrect. Which commands could you use to set the IP to 192.168.80.200/24 and default gateway to 192.168.80.1.
Which of the following is an authentication method used for Identity Awareness?
John is using Management HA. Which Smartcenter should be connected to for making changes?
Fill in the blank: The position of an implied rule is manipulated in the __________________ window.
SandBlast offers flexibility in implementation based on their individual business needs. What is an option for deployment of Check Point SandBlast Zero-Day Protection?
Fill in the blank: It is Best Practice to have a _____ rule at the end of each policy layer.
Which VPN routing option uses VPN routing for every connection a satellite gateway handles?
Which utility allows you to configure the DHCP service on GAIA from the command line?
Which of the following commands can be used to remove site-to-site IPSEC Security Associations (SA)?
Vanessa is a Firewall administrator. She wants to test a backup of her company’s production Firewall cluster Dallas_GW. She has a lab environment that is identical to her production environment. She decided to restore production backup via SmartConsole in lab environment. Which details she need to fill in System Restore window before she can click OK button and test the backup?
You want to define a selected administrator's permission to edit a layer. However, when you click the + sign in the “Select additional profile that will be able edit this layer” you do not see anything. What is the most likely cause of this problem? Select the BEST answer.

Which of the following is NOT an authentication scheme used for accounts created through SmartConsole?
ABC Corp., and have recently returned from a training course on Check Point's new advanced R80 management platform. You are presenting an in-house R80 Management to the other administrators in ABC Corp.
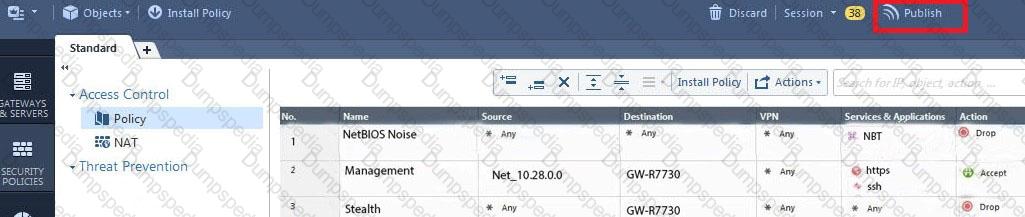
How will you describe the new “Publish” button in R80 Management Console?
Fill in the blank: To build an effective Security Policy, use a ________ and _______ rule.
Which pre-defined Permission Profile should be assigned to an administrator that requires full access to audit all configurations without modifying them?
You are the administrator for Alpha Corp. You have logged into your R80 Management server. You are making some changes in the Rule Base and notice that rule No.6 has a pencil icon next to it.
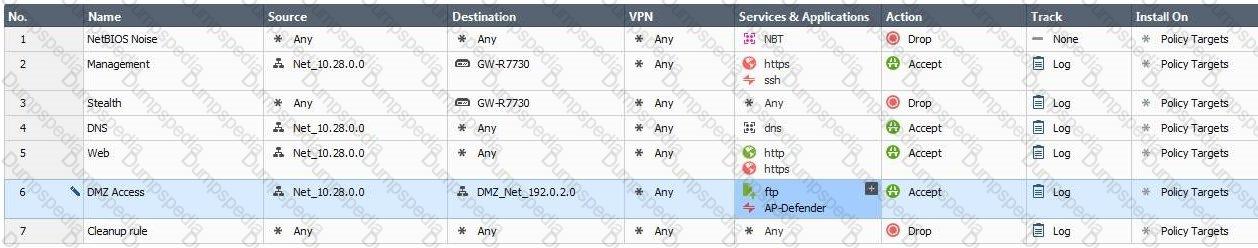
What does this mean?
Fill in the blanks: The _________ collects logs and sends them to the _________ .
Fill in the blank: With the User Directory Software Blade, you can create R80 user definitions on a(an) ___________ Server.
Which of the following technologies extracts detailed information from packets and stores that information in state tables?
Choose the Best place to find a Security Management Server backup file named backup_fw, on a Check Point Appliance.