Fill in the blank.
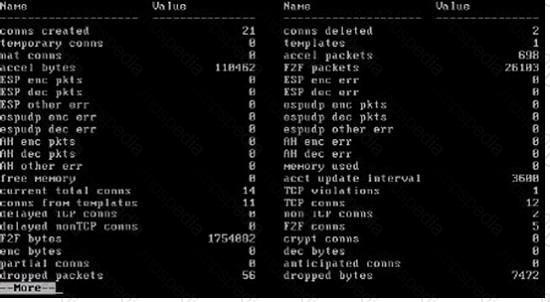
To verify SecureXL statistics, you would use the command _____.
Fred is troubleshooting a NAT issue and wants to check to see if the inbound connection from this internal network is being translated across the interface in the firewall correctly. He decides to use the fw monitor to capture the traffic from the source 192.168.3.5 or the destination of 10.1.1.25 on his Security Gateway. Green that has an IP of 192.168.4.5. What command captures this traffic in a file that he can download and review with WireShark?
In the following cluster configuration; if you reboot sglondon_1 which device will be active when sglondon_1 is back up and running? Why?
When using Captive Portal to send unidentified users to a Web portal for authentication, which of the following is NOT a recommended use for this method?
Which of the following access options would you NOT use when configuring Captive Portal?
MultiCorp has bought company OmniCorp and now has two active AD domains. How would you deploy Identity Awareness in this environment?
Identity Agent is a lightweight endpoint agent that authenticates securely with Single Sign-On (SSO). Which of the following is NOT a recommended use for this method?
The following graphic illustrates which command being issued on Secure Platform?
Where is the encryption domain for a SmartLSM Security Gateway configured in R71?
What is the proper CLISH syntax to configure a default route via 192.168.255.1 in GAiA?
A user cannot authenticate to SSL VPN. You have verified the user is assigned a user group and reproduced the problem, confirming a failed-login session. You do not see an indication of this attempt in the traffic log. The user is not using a client certificate for login.
To debug this error, where in the authentication process could the solution be found?
Remote clients are using SSL VPN to authenticate via LDAP server to connect to the organization. Which gateway process is responsible for the authentication?
You configure a Check Point QoS Rule Base with two rules:
an H.323 rule with a weight of 10, and the Default Rule with a weight of 10.
The H.323 rule includes a per-connection guarantee of 384 Kbps. and a per-connection limit of 512 Kbps. The per-connection guarantee is for four connections, and no additional connections are allowed in the Action properties. If traffic is passing through the QoS Module matches both rules, which of the following statements is TRUE?
Review the following list of actions that Security Gateway R75 can take when it controls packets. The Policy Package has been configured for Simplified Mode VPN. Select the response below that includes the available actions:
Where do you define NAT properties so that NAT is performed either client side or server side? In SmartDashboard under:
Which command line interface utility allows the administrator to verify the Security Policy name and timestamp currently installed on a firewall module?
You plan to incorporate OPSEC servers, such as Web sense and Trend Micro, to do content filtering. Which segment is the BEST location for these OPSEC servers, when you consider Security Server performance and data security?
All of the following are used by the DLP engine to match a message during a scan, EXCEPT:
Which of the following describes the default behavior of an R77 Security Gateway?
You intend to upgrade a Check Point Gateway from R65 to R76.
To avoid problems, you decide to back up the Gateway.
Which approach allows the Gateway configuration to be completely backed up into a manageable size in the least amount of time?
You are the MegaCorp Security Administrator. This company uses a firewall cluster, consisting of two cluster members. The cluster generally works well but one day you find that the cluster is behaving strangely. You assume that there is a connectivity problem with the cluster synchronization link (cross-over cable). Which of the following commands is the BEST for testing the connectivity of the crossover cable?
Fill in the blank.
MultiCorp is located in Atlanta. It has a branch office in Europe, Asia, and Africa. Each location has its own AD controller for local user login. How many ADqueries have to be configured?
The process that performs the authentication for legacy session authentication is:
When troubleshooting user authentication, you may see the following entries in a debug of the user authentication process. In which order are these messages likely to appear?
While authorization for users managed by SmartDirectory is performed by the gateway, the authentication mostly occurs in _____.
What is the purpose of the pre-defined exclusions included with SmartEvent R77?
In a R77 ClusterXL Load Sharing configuration, which type of ARP related problem can force the use of Unicast Mode (Pivot) configuration due to incompatibility on some adjacent routers and switches?
When distributing IPSec packets to gateways in a Load Sharing Multicast mode cluster, which valid Load Sharing method will consider VPN information?
Included in the customer’s network are some firewall systems with the Performance Pack in use. The customer wishes to use these firewall systems in a cluster (Load Sharing mode). He is not sure if he can use the Sticky Decision Function in this cluster. Explain the situation to him.
By default, a standby Security Management Server is automatically synchronized by an active Security Management Server, when:
Your organization has many VPN-1 Edge gateways at various branch offices, to allow VPN-1 Secure Client users to access company resources. For security reasons, your organization's Security Policy requires all Internet traffic initiated behind the VPN-1 Edge gateways first be inspected by your headquarters' VPN-1 Pro Security Gateway.
How do you configure VPN routing in this star VPN Community?
You receive an alert indicating a suspicious FTP connection is trying to connect to one of your internal hosts. How do you block the connection in real time and verify the connection is successfully blocked?
What happens when an Administrator activates the DLP Portal for Self Incident Handling and enters its fully qualified domain name (DNS name)?
Assume an intruder has compromised your current IKE Phase 1 and Phase 2 keys.
Which of the following options will end the intruder's access, after the next Phase 2 exchange occurs?
Rachel is the Security Administrator for a university. The university's FTP servers have old hardware and software. Certain FTP commands cause the FTP servers to malfunction.
Upgrading the FTP servers is not an option at this time.
Which of the following options will allow Rachel to control which FTP commands pass through the Security Gateway protecting the FTP servers?
Regarding QoS guarantees and limits, which of the following statements is FALSE?
Why would an old Connecter Gateway IP be displayed to remote SSL Network Extender users, after changing it to a different IP? You must:
Public keys and digital certificates provide which of the following? Select three.
Check Point recommends that you back up systems running Check Point products. Run your back ups during maintenance windows to limit disruptions to services, improve CPU usage, and simplify time allotment. Which back up method does Check Point recommend anytime outside a maintenance window?
Check Point recommends that you back up systems running Check Point products. Run your back ups during maintenance windows to limit disruptions to services, improve CPU usage, and simplify time allotment. Which back up method does Check Point recommend every couple of months, depending on how frequently you make changes to the network or policy?
What process is responsible for transferring the policy file from SmartCenter to the Gateway?
MegaCorps' disaster recovery plan is past due for an update to the backup and restore section to enjoy the benefits of the new distributed R77 installation. You must propose a plan that meets the following required and desired objectives:
Required: Security Policy repository must be backed up no less frequently than every 24 hours.
Desired: Back up R77 components enforcing the Security Policies at least once a week.
Desired: Back up R77 logs at least once a week.
You develop a disaster recovery plan proposing the following:
The corporate IT change review committee decides your plan:
David wants to manage hundreds of gateways using a central management tool. What tool would David use to accomplish his goal?
The process _____ is responsible for GUI Client communication with the SmartCenter.
You configure a Check Point QoS Rule Base with two rules: an HTTP rule with a weight of 40, and the Default Rule with a weight of 10. If the only traffic passing through your QoS Module is HTTP traffic, what percent of bandwidth will be allocated to the HTTP traffic?
In GAiA, if one is unsure about a possible command, what command lists all possible commands.
A Threat Prevention profile is a set of configurations based on the following. Select the right answer.
You have pushed a policy to your firewall and you are not able to access the firewall. What command will allow you to remove the current policy from the machine?
MicroCorp experienced a security appliance failure. (LEDs of all NICs are off.) The age of the unit required that the RMA-unit be a different model. Will a revert to an existing snapshot bring the new unit up and running?
Which graded parameters help determine the protections to activate for security and which can be safely deactivated? Select the most correct answer.
Katie has enabled User Directory and applied the license to Security Management Server, Green. Her supervisor has asked her to configure the Password Strength options of the least one digit, one symbol, 8 characters long and include an uppercase character. How should she accomplish this?
In Gaia, the operating system can be changed to 32-bit or 64-bit, provided the processor supports 64-bit. What command toggles to 64-bit.
There are times when you want to use Link Selection to manage high-traffic VPN connections. With Link Selection you can:
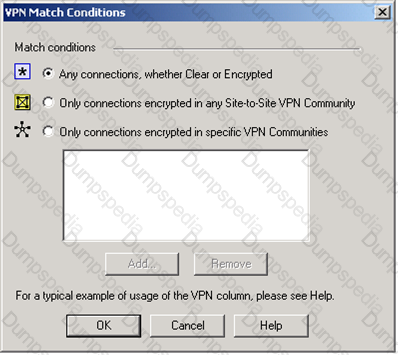
You are trying to configure Directional VPN Rule Match in the Rule Base. But the Match column does not have the option to see the Directional Match. You see the following window. What must you enable to see the Directional Match?
Exhibit:
There are times when you want to use Link Selection to manage high-traffic VPN connections. With Link Selection you can:
You want VPN traffic to match packets from internal interfaces. You also want the traffic to exit the Security Gateway bound for all site-to-site VPN Communities, including Remote Access Communities. How should you configure the VPN match rule?
You have three Gateways in a mesh community. Each gateway’s VPN Domain is their internal network as defined on the Topology tab setting All IP Addresses behind Gateway based on Topology information.
You want to test the route-based VPN, so you created VTIs among the Gateways and created static route entries for the VTIs. However, when you test the VPN, you find out the VPN still go through the regular domain IPsec tunnels instead of the routed VTI tunnels.
What is the problem and how do you make the VPN use the VTI tunnels?
Due to some recent performance issues, you are asked to add additional processors to your firewall. If you already have CoreXL enabled, how are you able to increase Kernel instances?
You want to verify that your Check Point cluster is working correctly.
Which command line tool can you use?
Which of the following statements is FALSE regarding OSPF configuration on Secure Platform Pro?
You need to publish GaiA routes using the OSPF routing protocol. What is the correct command structure, once entering the route command, to implement OSPF successfully?
MultiCorp is running Smartcenter R71 on an IPSO platform and wants to upgrade to a new Appliance with R77. Which migration tool is recommended?
MegaCorp is running Smartcenter R70, some Gateways at R65 and some other Gateways with R60. Management wants to upgrade to the most comprehensive IPv6 support. What should the administrator do first?
Paul has just joined the MegaCorp security administration team. Natalie, the administrator, creates a new administrator account for Paul in SmartDashboard and installs the policy. When Paul tries to login it fails. How can Natalie verify whether Paul’s IP address is predefined on the security management server?