How many pre-defined exclusions are included by default in SmartEvent R77 as part of the product installation?
You have selected the event Port Scan from Internal Network in SmartEvent, to detect an event when 30 port scans have occurred within 60 seconds. You also want to detect two port scans from a host within 10 seconds of each other. How would you accomplish this?
Review the rules.
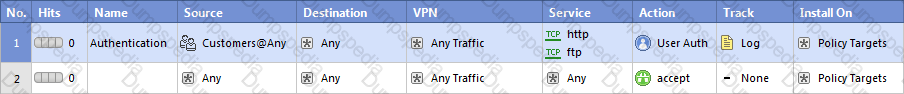
Assume domain UDP is enabled in the impled rules.
What happens when a user from the internal network tries to browse to the internet using HTTP? The user:
Review the Rule Base displayed.
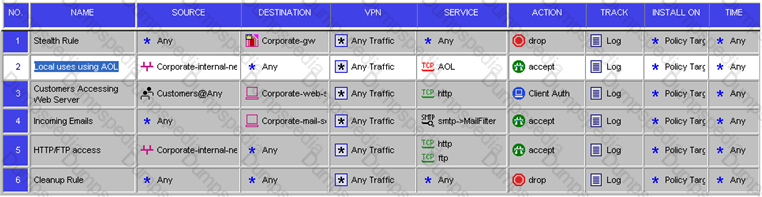
For which rules will the connection templates be generated in SecureXL?
To run GAiA in 64bit mode, which of the following is true?
1) Run set edition default 64-bit.
2) Install more than 4 GB RAM.
3) Install more than 4 TB of Hard Disk.
Which of the following CLISH commands would you use to set the admin user's shell to bash?
The connection to the ClusterXL member ‘A’ breaks. The ClusterXL member ‘A’ status is now ‘down’. Afterwards the switch admin set a port to ClusterXL member ‘B’ to ‘down’. What will happen?
Which statements about Management HA are correct?
1) Primary SmartCenter describes first installed SmartCenter
2) Active SmartCenter is always used to administrate with SmartConsole
3) Active SmartCenter describes first installed SmartCenter
4) Primary SmartCenter is always used to administrate with SmartConsole
Fill in the blank. To verify that a VPN Tunnel is properly established, use the command _________
Many companies have defined more than one administrator. To increase security, only one administrator should be able to install a Rule Base on a specific Firewall. How do you configure this?
A host on the Internet initiates traffic to the Static NAT IP of your Web server behind the Security Gateway. With the default settings in place for NAT, the initiating packet will translate the _________.
Suppose the Security Gateway hard drive fails and you are forced to rebuild it. You have a snapshot file stored to a TFTP server and backups of your Security Management Server. What is the correct procedure for rebuilding the Gateway quickly?
You are the Security Administrator for MegaCorp. A Check Point firewall is installed and in use on a platform using GAiA. You have trouble configuring the speed and duplex settings of your Ethernet interfaces. Which of the following commands can be used in CLISH to configure the speed and duplex settings of an Ethernet interface and will survive a reboot? Give the BEST answer.
Assume you are a Security Administrator for ABCTech. You have allowed authenticated access to users from Mkting_net to Finance_net. But in the user’s properties, connections are only permitted within Mkting_net. What is the BEST way to resolve this conflict?
How can you check whether IP forwarding is enabled on an IP Security Appliance?
Which Security Gateway R77 configuration setting forces the Client Authentication authorization time-out to refresh, each time a new user is authenticated? The:
Your company’s Security Policy forces users to authenticate to the Gateway explicitly, before they can use any services. The Gateway does not allow the Telnet service to itself from any location. How would you configure authentication on the Gateway? With a:
You enable Automatic Static NAT on an internal host node object with a private IP address of 10.10.10.5, which is NATed into 216.216.216.5. (You use the default settings in Global Properties / NAT.)
When you run fw monitor on the R77 Security Gateway and then start a new HTTP connection from host 10.10.10.5 to browse the Internet, at what point in the monitor output will you observe the HTTP SYN-ACK packet translated from 216.216.216.5 back into 10.10.10.5?
Fill in the blanks. To view the number of concurrent connections going through your firewall, you would use the command and syntax __ ___ __ __________ __ .
What command syntax would you use to see accounts the gateway suspects are service accounts?
Your organization maintains several IKE VPN’s. Executives in your organization want to know which mechanism Security Gateway R77 uses to guarantee the authenticity and integrity of messages. Which technology should you explain to the executives?
Where does the security administrator activate Identity Awareness within SmartDashboard?
Several Security Policies can be used for different installation targets. The Firewall protecting Human Resources’ servers should have its own Policy Package. These rules must be installed on this machine and not on the Internet Firewall. How can this be accomplished?