Usethe table to match the BEST Management High Availability synchronication-status descriptions for your Security Management Server (SMS).
Exhibit:
MegaCorp is using SmartCenter Server with several gateways. Their requirements result in a heavy log load. Would it be feasible to add the SmartEvent Correlation Unit and SmartEvent Server to their SmartCenter Server?
Complete this statement from the options provided. Using Captive Portal, unidentified users may be either; blocked, allowed to enter required credentials, or required to download the _____________.
Study the Rule base and Client Authentication Action properties screen -
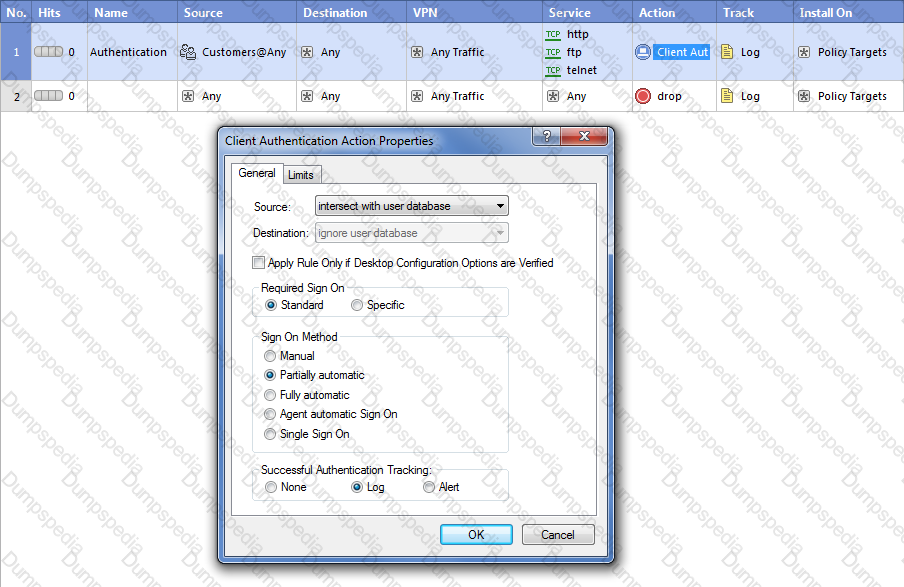
After being authenticated by the Security Gateway, when a user starts an HTTP connection to a Web site, the user tries to FTP to another site using the command line. What happens to the user? The:
You cannot use SmartDashboard’s User Directory features to connect to the LDAP server. What should you investigate?
1) Verify you have read-only permissions as administrator for the operating system.
2) Verify there are no restrictions blocking SmartDashboard's User Manager from connecting to the LDAP server.
3) Check that the login Distinguished Name configured has root permission (or at least write permission Administrative access) in the LDAP Server's access control configuration.
You intend to upgrade a Check Point Gateway from R71 to R80. Prior to upgrading, you want to back up the Gateway should there be any problems with the upgrade. Which of the following allows for the Gateway configuration to be completely backed up into a manageable size in the least amount of time?
Your company has the requirement that SmartEvent reports should show a detailed and accurate view of network activity but also performance should beguaranteed. Which actions should be taken to achieve that?
1) Use same hard drive for database directory, log files, and temporary directory.
2) Use Consolidation Rules.
3) Limit logging to blocked traffic only.
4) Use Multiple Database Tables.
The connection to the ClusterXL member ‘A’ breaks. The ClusterXL member ‘A’ status is now ‘down’. Afterwards the switch admin set a port to ClusterXL member ‘B’ to ‘down’. What will happen?
Type the full cphaprob command and syntax that will show full synchronization status.
Which statements about Management HA are correct?
1) Primary SmartCenter describes first installed SmartCenter
2) Active SmartCenter is always used to administrate with SmartConsole
3) Active SmartCenter describes first installed SmartCenter
4) Primary SmartCenter is always used to administrate with SmartConsole
Type the full fw command and syntax that allows you to disable only sync on a cluster firewall member.
Please choose correct command syntax to add an “emailserver1” host with IP address 10.50.23.90 using GAiA management CLI?
Fred is troubleshooting a NAT issue and wants to check to see if the inboundconnection from his internal network is being translated across the interface in the firewall correctly. He decides to use the fw monitor to capture the traffic from the source 192.168.3.5 or the destination of 10.1.1.25 on his Security Gateway, Green thathas an IP of 192.168.4.5. What command captures this traffic in a file that he can download and review with WireShark?
Session unique identifiers are passed to the web api using which http header option?
Using mgmt_cli, what is the correct syntax to import a host object called Server_1 from the CLI?
John is using Management HA. Which Smartcenter should be connected to for marking changes?
Check Point Management (cpm) is the main management process in that it provides the architecture for the consolidated management console. It empowers the migration from legacy Client side logic to Server side-logic. The cpm process:
You find one of your cluster gateways showing “Down” when you run the “cphaprob stat” command. You then run the “clusterXL_admin up” on the down member but unfortunately the member continues to show down. What command do you run to determine the case?
Events can be categorized and assigned to System Administrators to track their path through the workflow. Which of the following is NOT an option?
Fill in the blank: TheR80 feature ________ permits blocking specific IP addresses for a specified time period.
What command syntax would you use to turn on PDP logging in a distributed environment?
Select the command set best used to verify proper failover function of a new ClusterXL configuration.
All R80 Security Servers can perform authentication with the exception of one. Which of the Security Servers can NOT perform authentication?
Which command would provide the most comprehensive diagnostic information to Check Point Technical Support?
In Gaia, if one is unsure about a possible command, what command lists all possible commands.
The system administrator of a company is trying to find out why acceleration is not working for the traffic. The traffic is allowed according to the rule base and checked for viruses. But it is not accelerated. What is the most likely reason that the traffic is not accelerated?
ALL of the following options are provided by the GAiAsysconfig utility, EXCEPT:
You are running a R80 Security Gateway on GAiA. In case of a hardware failure, you have a server with the exact same hardware and firewall version installed. What back up method could be used to quickly put the secondary firewall into production?
Check Point APIs allow system engineers and developers to make changes to their organization’s security policy with CLI tools and Web Services for all of the following except?
MultiCorp is located in Atlanta. It has a branch office in Europe, Asia, and Africa. Each location has its own AD controller for local user login. How many ADqueries have to be configured?
Fill in the blank. The command that typically generates the firewall application, operating system, and hardware specific drivers is_________ .
Paul has just joined the MegaCorp security administration team. Natalie, the administrator, creates a newadministrator account for Paul in SmartDashboard and installs the policy. When Paul tries to login it fails. How can Natalie verify whether Paul’s IP address is predefined on the security management server?
Which of the following CLISH commands would you use to set the admin user's shell to bash?
You want VPN traffic to match packets from internal interfaces. You also want the traffic to exit theSecurity Gateway bound for all site-to-site VPN Communities, including Remote Access Communities. How should you configure the VPN match rule?
Which of the following items should be configured for the Security Management Server to authenticate using LDAP?
You run cphaprob -a if. When you review the output, you find the word DOWN. What does DOWN mean?
John is configuring a new R80 Gateway cluster but he can not configure the cluster as Third Party IP Clustering because thisoption is not available in Gateway Cluster Properties.
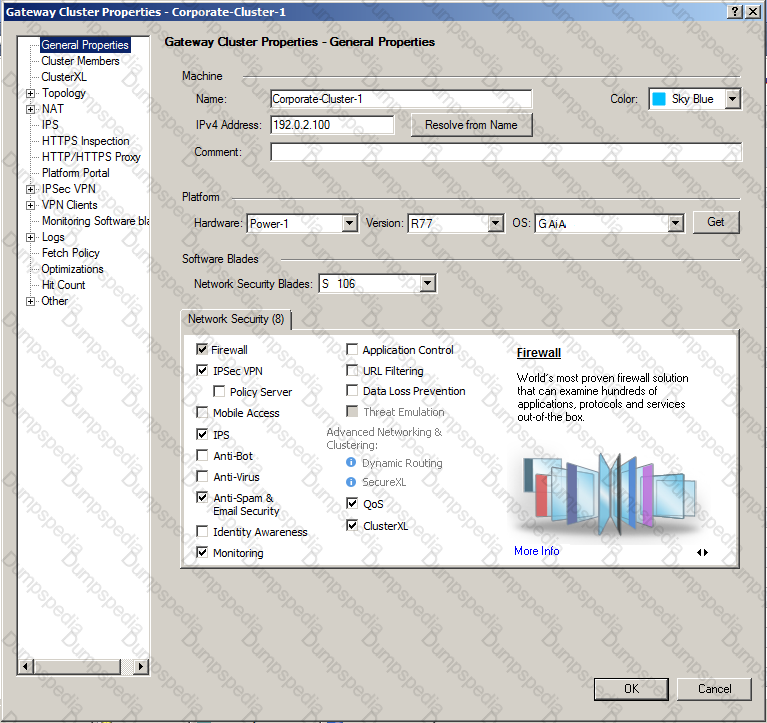
What’s happening?
Your organization maintains several IKE VPN’s. Executives in your organization want to know which mechanism Security Gateway R80 uses to guarantee the authenticity and integrity of messages. Which technology should you explain to the executives?
Type the command and syntax to view critical devices on a cluster member in a ClusterXL environment.
To qualify as an Identity Awareness enabled rule, which column MAY include an Access Role?
MegaCorps' disaster recovery plan is past due for an update to the backup and restore section to enjoy the benefits of the new distributed R80 installation. You must propose a plan that meets the following required and desired objectives:
Required: Security Policy repository must be backed up no less frequently than every 24 hours.
Desired: Back up R80 components enforcing the Security Policies at least once a week.
Desired: Back up R80 logs at least once a week.
You develop a disaster recovery plan proposing the following:
* Use the utility cron to run the command upgrade_export each night on the Security Management Servers.
* Configure the organization's routine backup software to back up files created by the command upgrade_export.
* Configure GAiA back up utility to back up Security Gateways every Saturday night.
* Use the utility cron to run the command upgrade_export each Saturday night on the log servers.
* Configure an automatic, nightly logswitch.
* Configure the organization's routine back up software to back up the switched logs every night.
The corporate IT change review committee decides your plan:
What mechanism does a gateway configured with Identity Awareness and LDAP initially use to communicate with aWindows 2003 or 2008 server?
You have adiskless appliance platform. How do you keep swap file wear to a minimum?
You enable Hide NAT on the network object, 10.1.1.0 behind the Security Gateway’s external interface. You browse to the Google Website from host, 10.1.1.10 successfully. You enable a log on the rule that allows 10.1.1.0 to exit the network. How many log entries do you see for that connection in SmartView Tracker?
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimizemalware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop with a static IP (10.0.0.19). He wants tomove around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
What should John do when he cannot access the web server from a different personal computer?
Suppose the Security Gateway hard drive fails and you are forced to rebuild it. You have a snapshot file stored to a TFTP server andbackups of your Security Management Server. What is the correct procedure for rebuilding the Gateway quickly?
The Identity Agent is a lightweight endpoint agent that authenticates securely with Single Sign-On (SSO). What is nota recommended usage of this method?
Your perimeter Security Gateway’sexternal IP is 200.200.200.3. Your network diagram shows:
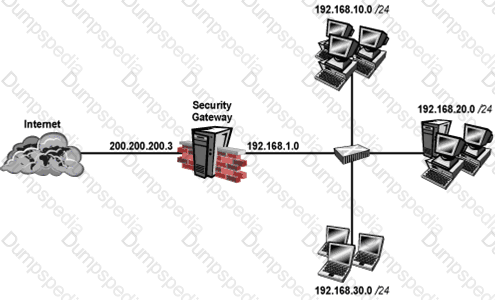
Required: Allow only network 192.168.10.0 and 192.168.20.0 to go out to the Internet, using 200.200.200.5.
The local network 192.168.1.0/24 needs to use 200.200.200.3 to go out to the Internet.
Assuming you enable all the settings in the NAT page of Global Properties, how could you achieve these requirements?
Match the followingcommands to their correct function.
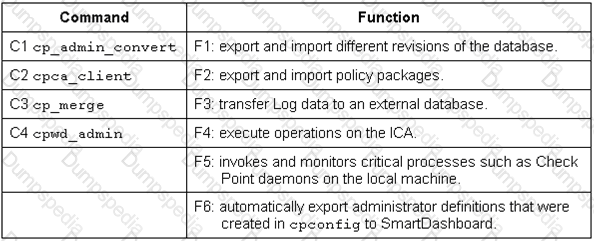
Each command has one function only listed.
Which operating systems are supported by a Check Point Security Gateway on an open server? Select MOST complete list.
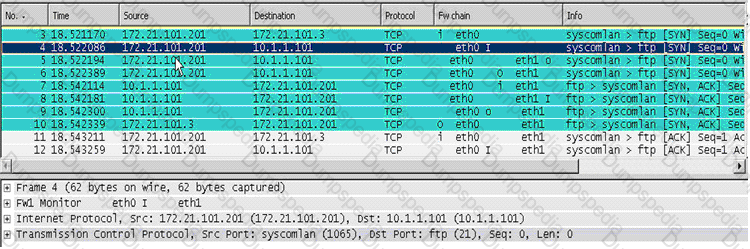
Looking at the SYN packets in the Wireshark output, select the statement that is true about NAT.
You want to implement Static Destination NAT in order to provide external, Internet users access to an internal Web Serverthat has a reserved (RFC 1918) IP address. You have an unused valid IP address on the network between your Security Gateway and ISP router. You control the router that sits between the firewall external interface and the Internet.
What is an alternative configuration if proxy ARP cannot be used on your Security Gateway?
You are a Security Administrator who has installed Security Gateway R80 on your network. You need to allow a specific IP address range for a partner site to access your intranet Web server. To limit the partner’s access for HTTP and FTP only, you did the following:
1)Created manual Static NAT rules for the Web server.
2) Cleared the following settings in the Global Properties > Network Address Translation screen:
- Allow bi-directional NAT
- Translate destination on client side
Do the above settings limit the partner’s access?
Which of the following statements accurately describes the command upgrade_export?
Which Security Gateway R80 configuration setting forces the Client Authentication authorization time-out to refresh, each time a new user is authenticated? The:
You are responsible for the configuration of MegaCorp’s Check Point Firewall. You need to allow two NAT rules to match a connection. Is it possible? Give the BEST answer.
Your internal network is configured to be 10.1.1.0/24. This network is behind your perimeter R80 Gateway, which connects to your ISP provider. How do you configure the Gateway to allow this network to go out to the Internet?