A technician recently ran a new cable over fluorescent lighting. Assuming the technician used the appropriate cables, which of the following connectors should be used to terminate it?
A network technician is reviewing the following output from a router:
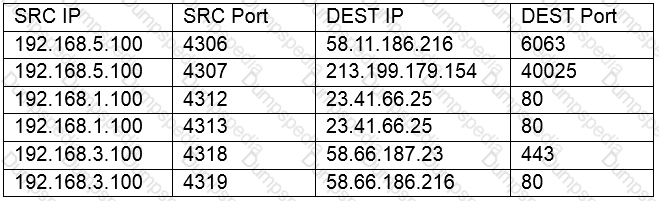
Which of the following is this an example of?
A consulting company was hired to project and deploy a new datacenter in a different city. This new facility must have the same components installed as the current datacenter to be ready to take over all the network services as soon as the primary site becomes unavailable. Which of the following describes what will be deployed in the new location?
Some users are reporting a high response time to access network resources after a new network router was installed. Which of the following documents should be updated every time a change is implemented on the network to have information about the metrics that represents how the network behaves during the normal scenarios?
A user has reported an issue with wireless VoIP phones dropping calls during business hours. When working late or in the evenings, the user does not experience call drops. When the network technician investigates the issue, all WAPs have balanced the number of connections evenly and are not dropping off the network. The network technician connects to the wireless network in the user’s office and starts a continuous ping to an external server. The results show a drastic and varied response time for each packet. Which of the following is the MOST likely cause of the dropped calls?
A company is contracting a new third-party organization that will handle storage of the company’s critical data. Which of the following policies would ensure the data remains confidential?
A brokerage firm requires high-speed network connectivity between several buildings in the financial district. Which of the following topologies would BEST meet this requirement?
A network technician is installing a wireless solution. The solution needs to support new and legacy wireless network clients at the maximum possible speed. Which of the following wireless standards should the technician install?
A network technician is segmenting a network to allow for unauthenticated public connections to a server. Which of the following devices would BEST safeguard the internal network from the public-facing server?
A server rack was moved from one floor to another. The network engineer needs to determine what physical changes to make on the network to ensure the server rack has connectivity. Which of the following should the network engineer consult?
Which of the following MUST be installed on an employee’s computer if the remote access VPN implements an SSL VPN with PKI authentication?
A network technician is assisting a user who is having problems accessing a particular website. Other users are reporting that the website is accessible outside of the office. The technician suspects the problem is with the company's firewall. Which of the following should the technician use to troubleshoot?
A technician has been asked to diagnose problems with DHCP addressing on a VLAN. The DHCP server responds to pings from the technician's machine. Which of the following should the technician use to help diagnose the problem?
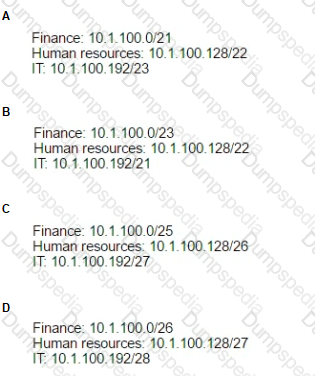
The corporate head office has assigned the subnet of 10.1.100.0/24 to a network technician. The technician wants to create subnets for the finance department, human resources, and IT. Given the following device counts:
Finance: 70 devices
Human resources: 38 devices
IT: 16 devices
Which of the following outlines how the technician should allocate the address space given?
A company has decided to allow certain users lo work remotely by opening up a VPN connection through the firewall. The security policy has been updated to allow VPN connections only from certain users and lo specific areas on the network Along with configuring the correct policies on the firewall, which of the following also needs to be configured on users' mobile devices to allow these VPN connections?
A network technician is reviewing switch ACLs to determine if they are causing communication issues with one PC. The PC’s IP address is 192.168.12.66. Which of the following is the network range found in the ACL that could have affected this PC?
Management at a company wants to increase the bandwidth available to users after receiving several complaints. A technician reports to management that 50% of the company bandwidth is being utilized by wireless devices outside the company’s property. Given budget constraints, which of the following solutions should the technician propose to management?
A network technician is assisting a user who is experiencing connectivity problems with the VPN. The technician has confirmed the VPN is functioning and other users at the site cannot access the Internet. Which of the following commands would MOST likely be used to further troubleshoot?
A user reports network resources can no longer be accessed. The PC reports a link but will only accept static IP addresses. The technician pings other devices on the subnet, but the PC displays the message Destination unreachable. Which of the following are MOST likley the causes of this issue? (Select TWO).
A bookstore uses a Faraday cage to comply with credit card regulations Customers report that their cellular phones have no signal when they are in the bookstore Which of the following is the MOST likely cause?
A user no longer has access to network resources after a recent office move, but all other users in the building are able to connect at 100MB connections. After further investigation, a network technician notices the following information:
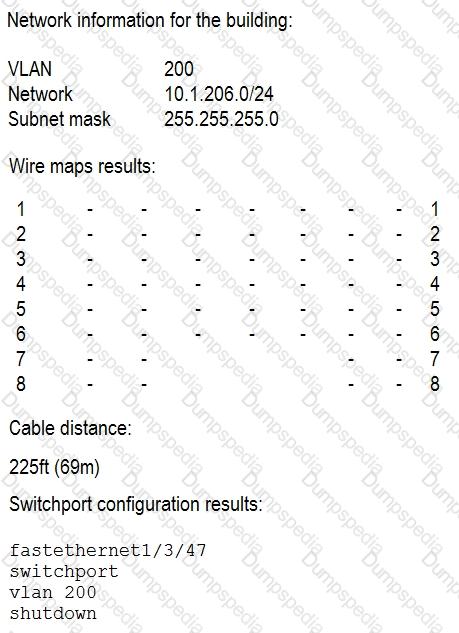
Which of the following is causing the network connection issues?
A network technician has installed multiple new lightweight access points across the network. Which of the following devices should the technician use to manage the new access points?
Which of the following network topologies typically has all devices on a network directly connected to every other network device?
When deploying UTP cables In a networking environment, which of the following are acceptable standards? (Select TWO).
A company runs Linux servers In its own datacenter and also on a popular public cloud service provider. The servers hosted by the cloud provider can only be accessed with proper authorization and are only accessed by the company’s datacenter. Which of the following BEST describes the type of cloud architecture being used? (Select TWO).
A network technician Is segmenting network traffic Into various broadcast domains. Which of the following should the network technician utilize?
A technician is troubleshooting a server In the finance office that hosts an internal accounting program. The ticketing desk has received several calls from users reporting that access to the accounting program is degraded, and they are experiencing severe delays, sometimes timing out entirely. The problem has been isolated to the server. Which of the following tools should the technician use on the server to narrow down the issue?
A corporate manager says wireless phones do not work properly inside the main building. After a troubleshooting process, the network administrator detects that the voice packets are arriving on the wireless phones with different delay times. Which of the following performance issues is the company facing?
Ann a customer was using a coffee shop's public WiFi and had her connection briefly interrupted, but It reconnected again Unbeknownst to Ann. the disconnection was intentional and was connected to a malicious user's device. Which of the following attacks did Ann experience? (Select TWO).
A technician is setting up a surveillance system at a small office. The customer would like to have the network controlled by the office's firewall/router device. The office has a coaxial ISP connection with an ISP provided cable modem. Which of the following should the technician configure on the cable modem to meet the customer requirements?
A Route with NAT
B. PPP
C. PPPoE
D. Bridge mode
A technician has been assigned to capture packets on a specific switchport. Which of the following switch feature MUST be used to accomplish this?
A network technician is performing an initial configuration of a new network switch. Per company policy, the only authorized manner for remotely administering the switch is through a command line. Which of the following protocols should the technician disable to adhere to the company policy?
A user does not have access to network services but has Internet access. The technician notices the
computer has an IP address of 192.168.1.144 when the network is 10.10.10.0. Which of the following is MOST likely the issue?
A network technician arrives at a remote office and is unable to connect a laptop to corporate resources using the wireless network. After checking the IP address, the network technician notices the assigned IP address does not belong to the corporate network IP scheme. Which of the following has the network technician discovered?
A network topology requires a switch to be placed in an unsecured location. Which of the following techniques should be used to prevent unauthorized access? (Choose two.)
A wireless access point that was working in a large warehouse last week is now offline. The technician observes there is no power to the device. The technician verifies PoE is working on the switchport, and then confirms the wireless access point is still not powering up. Which of the following is the MOST likely issue?
A university has a lecture hall containing 100 students. Currently, the lecture hall has two 802.11ac wireless access points, which can accommodate up to 50 devices each. Several students report they are unable to connect devices to the wireless network. Which of the following is MOST likely the issue?
A network technician installed a new host on the network. The host is not connecting to the company’s cloud servers. The technician attemtps to ping a server using the AP address with no success. Checking the IP address using ipconfing displays:
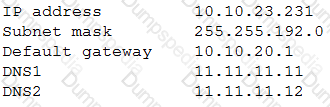
Which of the following should the technician perform NEXT to determine where the issue is located?
Which of the following is used to define the duration during which a client can use an IP address?
Two buildings used to be connected by a wireless bridge, but they are upgrading to fiber. Which of the following new devices would be required at the demarcation points?
Which of the following technologies should be used in high-throughput networks to reduce network overhead?
A technician Is reviewing network device logs in an attempt to trace an attack that occurred on the network. Which of the following protocols would affect whether or not the technician can properly trace the attack through the network using the logs?
A network technician has finished configuring a new DHCP for a network. To ensure proper functionality, which of the following ports should be allowed on the server’s local firewall? (Select TWO).
Joe, a technician, is attempting to resolve an issue with an off-site router remotely. Joe needs to reset the WAN connection settings and wants to ensure he will have access to the router at all times to monitor the changes.
Which of the following solutions would BEST meet this goal?
A network extension needs to be run to a location 500ft (152m) from the nearest switch. Which of the following solutions would work BEST? (Select TWO).
A network technician is installing a new network switch in the MDF. The technician is using fiber to connect the switch back to the core. Which of the following transceiver types should the technician use?
A technician is wiring a new digital subscriber line in the corporate MDF. Which of the following marks the termination point?
A user recently made changes to a PC that caused it to be unable to access websites by both FQDN and IP Local resources, such as the file server remain accessible. Which of the following settings did the user MOST likely misconfigure?
A store owner would like to have secure wireless access available for both equipment and patron use. Which of the following features should be configured to allow different wireless access through the same
equipment?
Which of the following would MOST likely provide continuous power during a short brownout?
Given the following output:
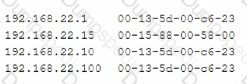
Which of the following attacks is this MOST likely an example of?
A workstation is configured with the following network details:
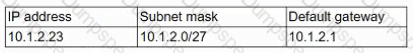
Software on the workstation needs to send a query to the local subnet broadcast address. To which of the following addresses should the software be configured to send the query?
The lack of which of the following components might make a virtual router less efficient than a physical router?
A Chief Information Security Officer (CISO) has learned of a zero-day exploit that is being used against a vendor product that is currently deployed within the organization. The network team needs to provide a list of potentially vulnerable assets for the network security team to scan. Which of the following will the network learn MOST likely use?
A company has a DNS a record for the following address: products.companyXYZ. The company wuld to like to add another record,sales.companyXYZ.com, which continually points to the same IP address as product.companyXYZ.com. Which of the following DNS record types would BEST accomplish this?
A technician needs to manage equipment using either an IP address or a serial port. There is a pair of copper wires from the management center to the location of the equipment. Which of the following networking devices should be used to successfully communicate to the equipment?
A network engineer utilizes a box of Cat5e cable in a datacenter for use between 10Gbps switches in a single rack. After the engineer finishes the installation, switch administrators notice random speed drops and
intermittent connection issues. Which of the following is this an example of?
A small business utilizes a SOHO router and wishes to secure its existing wireless infrastructure. The business has fewer than ten devices, which are a mixture of old and new machines. Due to the varying ages of the machines, the latest wireless encryption methods may not be supported on all devices. Which of the following would be the MOST cost-effective method to add a layer of security while allowing all machines to connect?
When trying to determine why users are unable to access a web-based application that was working the previous day, which of the following should be the FIRST QUESTION NO: to ask to determine the scope of the issue?
Joe, a network technician, has received a report that one of his clients is experiencing an issue connecting to the network. Joe observes two clients are connected to a hub, which is connected to separate wall jacks. Which of the following has MOST likely occurred?
Management asks a network technician to install a new connection between two main locations. Management requests that the connection be the fastest possible for data replication. Which of the following would be the MOST appropriate type?
A technician is connecting multiple switches to create a large network for a new office. The switches are unmanaged Layer 2 switches with multiple connections between each pair. The network is experiencing an extreme amount of latency. Which of the following is MOST likely occurring?
A network support team needs to install a wireless network at a new branch office. The team must provide the strongest security to prevent unauthenticated users from viewing the traffic on the wireless network Which of the following solutions would BEST meet these needs?
A network analyst is providing access to an FTP server that stores files that are needed by external contractors who are working on a project. In which of the following network locations should the FTP server be placed to achieve the MOST secure environment?
In the past, users brought personal laptops to the office to bypass some of the security protocols on their desktops. Due to new security initiatives, management has asked that users not be allowed to attach personal devices to the network. Which of the following should a technician use to BEST meet this goal?
A network engineer wants to implement a technology that allows for an all-in-one approach to incoming and outgoing traffic from the Internet. This device should be able to filter content and scan for malicious information in each packet. Which of the following types of devices would be necessary?
Which of the following would block access to an untagged port when connected to a Layer 2 device?
A technician is making the population of routers more secure. Which of the following are the BEST options for making authentication more secure? (Choose two.)
Which of the following would be BEST for continually monitoring and alerting of possible attacks on a network?
A new DSL circuit was installed to replace the cable service and is not functioning. A network administrator needs to create a cable to connect the circuit. Which of the following connector types should the network administrator use on the cable?
A network technician attempts to limit access to a wireless network by using WPA2 and a pre-shared key; however, employees have been sharing this key with others. Which of the following methods should the technician configure on the wireless access point to ensure only corporate systems can connect using the least amount of effort?
A system administrator reports that one of the two domain name servers does not seem to be responding to DNS requests from clients. The servers are both up and running, name service is running on them, and DNS requests appear in the logs. Both servers respond to queries made at the console. Which of the following tools should the systems administrator use to gather more information?
A network technician needs to upgrade a production Windows server to the latest service pack. In which of the following should the work plan and recovery procedure be documented?
A network manager notices several outages have occurred due to modifications that were made without being properly tested. Which of the following will the network manager MOST likely implement to prevent future occurrences?
A company needs a secure way to provide building blueprints to an engineering partner frequently. The Chief Information Officer (CIO) states that a secure protocol must be used for transfer, and the partner needs to initiate a secure connection to the company's router. Which of the following would BEST meet the requirements? (Choose two.)
Which of the following additional capabilities does a next generation firewall provide beyond a standard network firewall? (Choose two.)
Which of the following steps is a network technician MOST likely to take to secure a new network printer? (Choose two.)
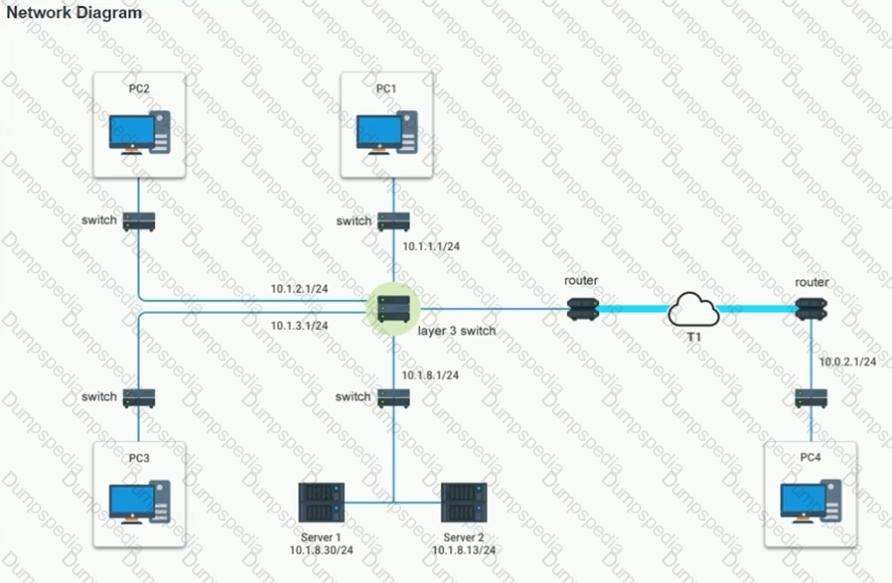
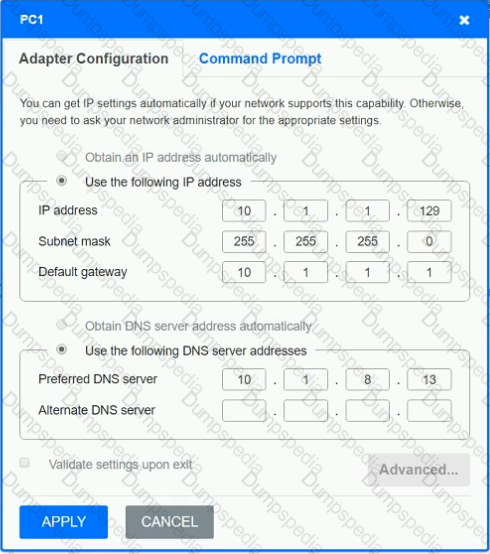
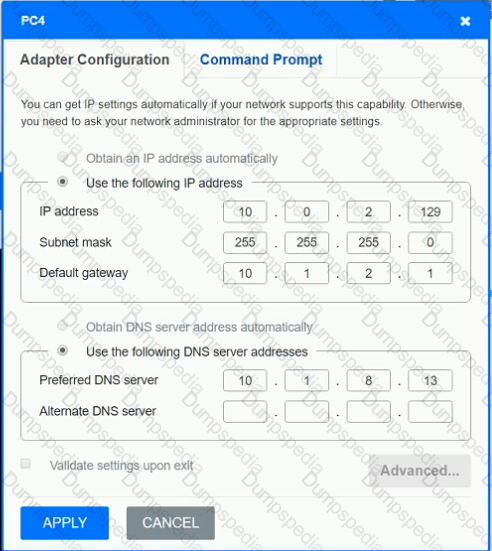
After recent changes to the pictured network, several users are unable to access the servers. Only PC1, PC2, PC3, and PC4 are clickable and will give you access to the command prompt and the adapter configuration tabs.
INSTRUCTIONS
Verify the settings by using the command prompt, after making any system changes.
Next, restore connectivity by making the appropriate changes to the infrastructure.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
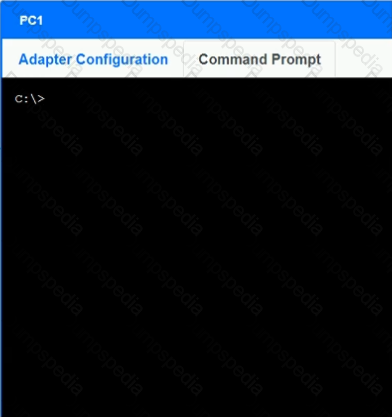
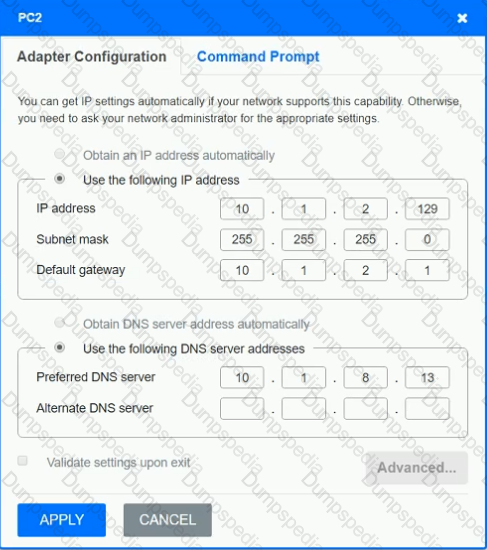
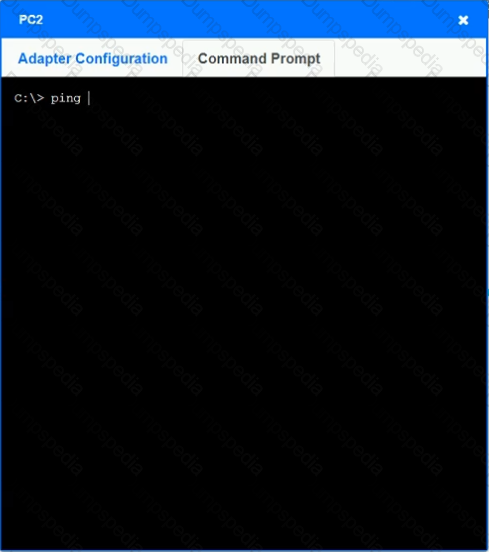
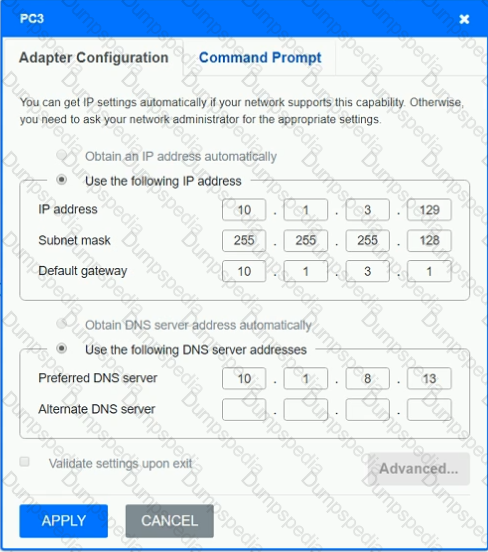
A network administrator is deploying a new switch in an existing IDF. The current switch has only copper Ethernet ports available to use for the trunk ports. Which of the following cable types should the network administrator deploy?
A company must create a way for partners to access a web portal to update documents for a project. This should be done only via web browser in a transparent way for the users. Which of the following should be used?
Which of the following manages the delegation of physical equipment to the virtual components?
A switch is being configured for installation into a new building. The network design is such that the only DHCP server resides in the datacenter. A traditional three-layer network hierarchy is being used, and all
buildings have a Layer 3 connection back to the core. Which of the following should the technician configure to get DHCP working properly in the new building?
A network technician is installing a network printer in a factory setting. The connection from the switch contains an LC connector, yet the printer only supports an RJ45 connector. Which of the following should the technician use?
A network administrator is configuring a link-state routing protocol for traffic. Which of the following routing protocols should be implemented?
A network technician built a wireless network in a ten-story office building but has found it does not perform well. The technician performed the following steps during the installation:
* Researched and decided that 802.11ac would be the best technology
* Ensured the switch supports PoE+
* Purchased an AP for each floor and spare APs in case of failure
* Put each AP into non-overlapping channels
Which of the following is the MOST likely reason users are experiencing poor performance?
A new network Technician is responsible for bringing a building onto the corporate network. The technician is not aware of the proper settings for the new switches. Which of the following should the technician reference to find these settings?
Which of the following would an organization MOST likely have users sign before granting administrative access?
Users at an office site notice the wireless network is unavailable for a short period after a brownout. Which of the following technologies is MOST cost effective to sustain network equipment during a brief power event?
A network technician is implementing a new IPv6 addressing scheme al a local office. This is a large office, and the network manager would like a solution that saves time and allows for automatic addressing of nodes. Which of the following would BEST accomplish this?
A network administrator needs to extend an organization's network to a nearby building that has unused SMF already installed. The network administrator has decided to create a switch-to-switch uplink. Which of the following standards would be the BEST to use?
A network administrator is installing the company first external-facing web server and examining where to place it on the network. In which of the following zones should the server be configured?
Which of the following relies on metrics such as total number of connections or CPU'RAM usage to help maintain performance and availability?
A OLP system configured on a network's point of egress captured sensitive company documents going out to the Internet from an Internal workstation. The user o that workstation left to work for a competitor the next day. Which of the following attacks is lib MOST likely an example of?
While attempting to add a new computer to the company network the network technician is unable to connect automatically. The technician runs a command and is presented with the following output:

The technician assigns a static IP address and is able to connect to the network. Which of the following BEST describes the cause of the issue?
A company wants to provide its sales representatives with an easy-to-use method of securely connecting to the corporate network from any client network. Which of the following methods should the network technician implement?
Several network changes were made to a company’s firewall, and users have no longer been able to access websites by name. A technician suspects there is a port misconfiguration. Which of the following ports was
misconfigured?
A network administrator is configuring a database server and would like to ensure the database engine is listening on a certain port. Which of the following commands should the administrator use to accomplish this goal?