Scenario: A Citrix Architect needs to assess a NetScaler Gateway deployment that was recently completed by a customer and is currently in pre-production testing. The NetScaler Gateway needs to use ICA proxy to provide access to a XenApp and XenDesktop environment. During the assessment, the customer informs the architect that users are NOT able to launch published resources using the Gateway virtual server.
Click the Exhibit button to view the troubleshooting details collected by the customer.

What is the cause of this issue?
Scenario: A Citrix Architect has configured a load balancing virtual server for RADIUS authentication. The architect observes that, when the radius authentication action has the virtual server IP address, the authentication falls. However, when any of the individual server IP addresses are used, the authentication works fine.
How should the architect troubleshoot this issue?
Scenario: A Citrix Architect holds a design discussion with a team of Workspacelab members, and they capture the following requirements for the Citrix ADC design project:
Click the Exhibit button to review the output of aaad.debug and the configuration of the authentication policy.
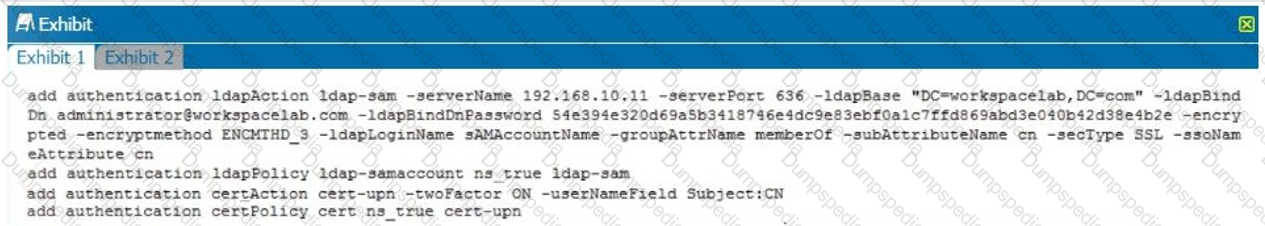
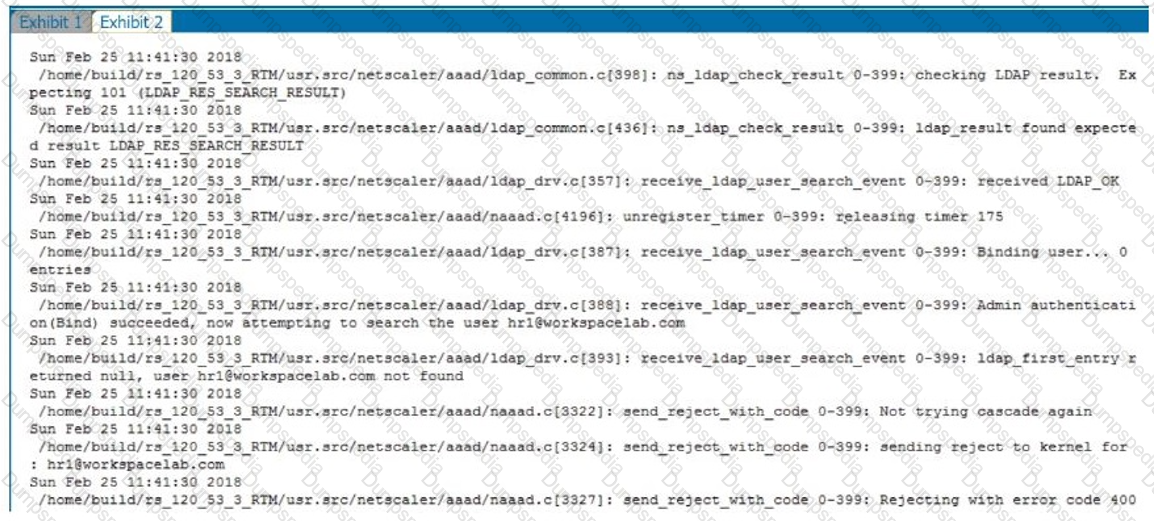
What is causing this issue?
 Scenario: A Citrix Architect has executed the following commands on the Citrix ADC:
Scenario: A Citrix Architect has executed the following commands on the Citrix ADC:
In which scenario will the timeout work as configured?
Scenario: A junior Citrix Architect would like to use nFactor to perform authentication based on the domain. The junior architect has reached out to a supervisor for assistance and has been provided with the following step-by-step configuration guide:
What must the junior architect bind In order for the authentication to work correctly?
Scenario: A Citrix Architect has implemented two high availability pairs of MPX 5500 and MPX 11500 devices respectively with 12.0.53.13 nc version. The NetScaler devices are set up to handle NetScaler Gateway, Load Balancing, Application Firewall, and Content Switching. The Workspacelab infrastructure is set up to be monitored with NMAS version 12.0.53.13 nc by the Workspacelab administrators. The Workspacelab team wants to implement one more pair of NetScaler MPX 7500 devices with version 12.0.53.13 nc.
The Citrix consulting team has assigned the task to implement these NetScaler devices in the infrastructure and set them up to be monitored and managed by NMAS.
The following are the requirements that were discussed during the project initiation call:
Which process should the architect utilize to ensure that the deployment of MPX 11500 devices are optimized and that it is correct, before deploying the devices in production?
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria.
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings.
Which setting is preventing the security requirements of the organization from being met?
Which markup language can a Citrix use along with NITRO API to create a StyleBook?
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria.
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings.
Which setting is preventing the security requirements of the organization from being met?
Scenario: Based on a discussion between a Citrix Architect and a team of Workspacelab members, the MPX Logical layout for Workspacelab has been created across three (3) sites.
They captured the following requirements during the design discussion held for a Citrix ADC design project:
Which design decision must the architect make to meet the design requirements above?
Scenario: A Citrix Architect needs to design a new Citrix Gateway deployment. During the design discussions, the architect documents the key requirements about when to provide VPN access for incoming connections to the Citrix Gateway virtual server. Click the Exhibit button to view the requirements.

Which policy expression will meet these requirements?

Scenario: A Citrix Architect has deployed an authentication setup with a ShareFile load-balancing virtual server. The NetScaler is configured as the Service Provider and Portalguard server is utilized as the SAML Identity Provider. While performing the functional testing, the architect finds that after the users enter their credentials on the logon page provided by Portalguard, they get redirected back to the Netscaler Gateway page at uri /cgi/samlauth/ and receive the following error.

The events in the /var/log/ns.log at the time of this issue are as follows:

What should the architect change in the SAML action to resolve this issue?
Which session parameter does the default authorization setting control when authentication, authorization, and auditing profiles are configured?
Scenario: A Citrix Architect needs to design a new NetScaler Gateway deployment to provide secure RDP access to backend Windows machines.
Click the Exhibit button to view additional requirements collected by the architect during the design discussions.
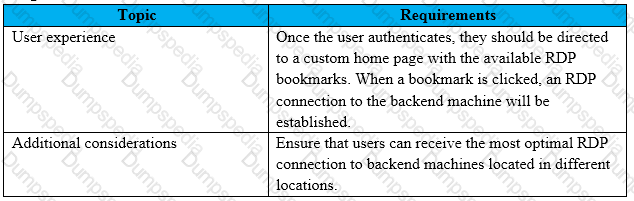
To meet the customer requirements, the architect should deploy the RDP proxy through ______ using a________ solution. (Choose the correct option to complete the sentence.)
Under which two circumstances will a service be taken out of the slow start phase with automated slow start? (Choose two.)
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria.
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings.

Which setting is preventing the security requirements of the organization from being met?
A Citrix Architect can execute a configuration job using a DeployMasterConfiguration template on a NetScaler_________deployed_________. (Choose the correct option to complete sentence.)
Scenario: A Citrix Architect needs to design a hybrid Citrix Virtual App and Citrix Virtual Desktop environment which will include Citrix Cloud as well as resource locations in an on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
Click the Exhibit button to view the conceptual environment architecture.

The architect should use _____ in Location A, and should use ________ in Location B. (Choose the correct option to complete the sentence.)
Scenario: A Citrix Architect needs to design a new Citrix ADC Gateway deployment to provide secure RDP access to backend Windows machines.
Click the Exhibit button to view additional requirements collected by the architect during the design discussions.

To meet the customer requirements, the architect should deploy the RDP proxy through _______, using a _________ solution. (Choose the correct option to complete the sentence.)
Scenario: A Citrix Architect needs to configure a full VPN session profile to meet the following requirements:
Which settings will meet these requirements?
A Citrix Architect can execute a configuration job using a DeployMasterConfiguration template on a Citrix ADC _________deployed_________. (Choose the correct option to complete sentence.)
Scenario: A Citrix Architect needs to design a new multi-datacenter Citrix ADC deployment. The customer wants Citrix ADC to provide access to various backend resources by using Global Server Load Balancing (GSLB) in an Active-Active deployment. Click the Exhibit button to view additional requirements identified by the architect.

Which GSLB algorithm or method should the architect use for the deployment based on the stated requirements?
Which parameter indicates the number of current users logged on to the Citrix gateway?
Scenario: A Citrix Architect needs to design a new multi-datacenter Citrix ADC deployment. The customer wants Citrix ADC to provide access the various backend resources by using Global Server Load Balancing (GSLB) in an Active-Active deployment.
Click the Exhibit button to view additional requirements identified by the architect.

Which GSLB algorithm or method should the architect use for the deployment based on the stated requirements?
Scenario: More than 10,000 users will access a customer’s environment. The current networking infrastructure is capable of supporting the entire workforce of users. However, the number of support staff is limited, and management needs to ensure that they are capable of supporting the full user base.
Which business driver is prioritized, based on the customer’s requirements?
Scenario: The Workspacelab team has implemented a Citrix ADC high availability pair and Citrix ADC Management and Analytics (Citrix Application Delivery Management). The Citrix Application Delivery Management was configured by a Citrix Architect to monitor and manage these devices. The Workspacelab team wants to load balance their Microsoft SharePoint servers on the Citrix ADC and needs the process to be streamlined and administered using Citrix Application Delivery Management. The following requirements were discussed during the meeting.
• The Microsoft SharePoint server should be optimized. Load balanced, and secured in the network and should be deployed using Citrix Application Delivery Management.
• All the configurations should be verified before getting pushed to the Citrix Application Delivery Management.
What is a prerequisite for installing Microsoft SharePoint using Citrix Application Delivery Management?
Scenario: A Citrix Architect needs to assess an existing Citrix ADC configuration. The customer recently found that members of certain administrator groups were receiving permissions on the production Citrix ADC appliances that do NOT align with the designed security requirements. Click the Exhibit button to view the configured command policies for the production Citrix ADC deployment.

To align the command policy configuration with the security requirements of the organization, the__________for________________should change. (Choose the correct option to complete the sentence.)
Scenario: A Citrix Architect needs to design a hybrid Citrix Virtual App and Citrix Virtual Desktop environment which will include as well as resource locations in an on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
Click the Exhibit button to view the conceptual environment architecture.

The architect should use___________ in Location A, and should use _______________ in Location B. (Choose the correct option to complete the sentence.)
Scenario: A Citrix Architect has configured two MPX devices in high availability mode with version 12.0.53.13 nc. After a discussion with the security team, the architect enabled the Application Firewall feature for additional protection.
In the initial deployment phase, the following security features were enabled:

What should the architect do to meet these requirements?
Scenario: A Citrix Architect needs to deploy Single Sign-on form-based authentication through Citrix ADC for Outlook Web Access (OWA) 2013 for the users of the domain workspacelab com The Single Sign-on (SSO) must be performed based on sAMAccountName.
Which SSO action can the architect use to meet this requirement?
Which three steps should a Citrix Architect complete to configure session settings for different user accounts or groups? (Choose three.)
Scenario: Based on a discussion between a Citrix Architect and a team of Workspacelab members, the MPX Logical layout for Workspacelab has been created across three (3) sites.
The requirements captured during the design discussion held for a NetScaler design project are as follows:
How many NetScaler MPX appliances should the architect deploy at each site to meet the design requirements above?
Which response is returned by the Citrix ADC, if a negative response is present in the local cache?
Scenario: A Citrix Architect has deployed two MPX devices, 12.0.53.13 nc and MPX 11500 models, in high availability (HA) pair for the Workspace labs team. The deployment method is two-arm and the devices are installed behind a CISCO ASA 5585 Firewall. The architect enabled the following features on the NetScaler devices. Content Switching, SSL Offloading, Load Balancing, NetScaler Gateway, Application Firewall in hybrid security and Appflow. All are enabled to send monitoring information to NMAS 12.0.53.13 nc build. The architect is preparing to configure load balancing for Microsoft Exchange 2016 server.
The following requirements were discussed during the implementation:
Which monitor will meet these requirements?
Scenario: A Citrix Architect needs to design a new multi-datacenter NetScaler deployment. The customer wants NetScaler to provide access to various backend resources by using Global Server Load Balancing (GSLB) in an Active-Active deployment.
Click the Exhibit button to view additional requirements identified by the architect.
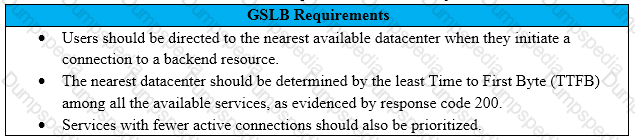
Which GSLB algorithm or method should the architect use for the deployment, based on the stated requirements?
Which two methods can a Citrix Architect use to create a Heat Orchestration template? (Choose two)
Scenario: A Citrix Architect has deployed two MPX devices. 12.0.53.13 nc and MPX 11500 models, in a high availability (HA) pair for the Workspace labs team. The deployment method is two-arm and the devices are installed behind a CISCO ASA 5585 Firewall. The architect enabled the following features on the Citrix ADC devices. Content Switching. SSL Offloading, Load Balancing, Citrix Gateway. Application Firewall in hybrid security and Appflow. All are enabled to send monitoring information to Citrix Application Delivery Management 12.0.53.13 nc build. The architect is preparing to configure load balancing for Microsoft Exchange 2016 server.
The following requirements were discussed during the implementation:
Which monitor will meet these requirements?
Scenario: A Citrix Architect needs to design a hybrid XenApp and XenApp and XenDesktop environment which will include Citrix Cloud as well as resource locations in on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
Click the Exhibit button to view the conceptual environment architecture.
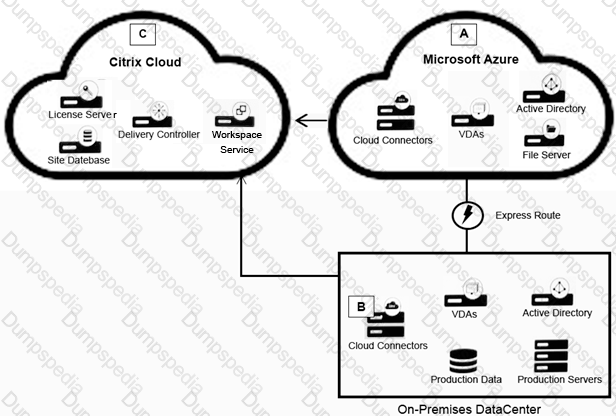
The architect should use ________ in Location A, and should use _________ in Location B. (Choose the correct option to complete the sentence.)
Scenario: The Workspacelab team has implemented Citrix ADC high availability pair and Citrix ADC Management and Analytics System (Citrix Application Delivery Management). The Citrix Application Delivery Management was configured by a Citrix Architect to monitor and manage these devices. The Workspacelab team wants to load balance their Microsoft SharePoint servers on the Citrix ADC and needs the process to be streamlined and administered using Citrix Application Delivery Management.
The following requirements were discussed during the meeting:
Which feature should the architect use to configure the Microsoft SharePoint server using Citrix Application Delivery Management?
Scenario: A Citrix Architect has set up NetScaler MPX devices in high availability mode with version 12.0. 53.13 nc. These are placed behind a Cisco ASA 5505 Firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall.
The following requirements were captured by the architect during the discussion held as part of the NetScaler security implementation project with the customer’s security team:
The NetScaler device:
Which two security features should the architect configure to meet these requirements? (Choose two.)
Scenario: Based on a discussion between a Citrix Architect and a team of Workspacelab members, the MPX Logical layout for Workspacelab has been created across three (3) sites.
They captured the following requirements during the design discussion held for a Citrix ADC design project:
Which design decision must the architect make the design requirements above?