Refer to the exhibit.
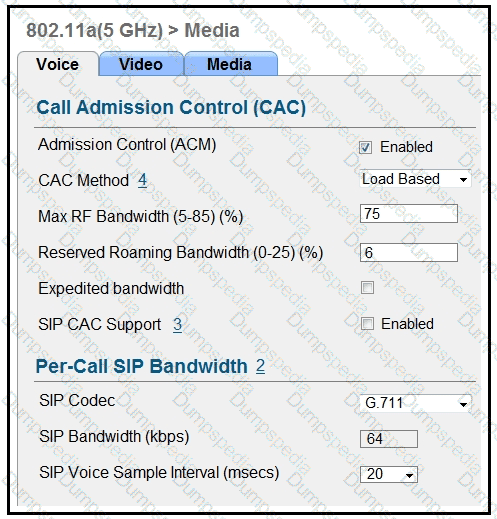
Which two items must be supported on the VoWLAN phones to take full advantage of this WLAN configuration? (Choose two.)
An engineer is configuring location services within Cisco Spaces (formerly Cisco DNA Spaces). The solution must track interfering devices. Which component of Cisco Spaces must be configured?
A network engineer must get an autonomous AP to authenticate to the upstream switch via IEEE 802.1 X. Drag and drop the commands from the left onto the right to complete the configuration.
An engineer is in the process of implementing Fastiane on a wireless network with a Mobility Express AP installed and Apple end-user devices. Due to a security concern, the IT department has updated all the iPads to version 14.5.423551943. Which QoS profile must the engineer configure on the user WLAN?
An engineer must configure a Cisco WLC to support Cisco Aironet 600 Series OfficeExtend APs. Which two Layer 2 security options are supported in this environment? (Choose two.)
An engineer is deploying a virtual MSE. The network has 3000 APs and needs 7000 IPS licenses.
To which size server does the engineer scale it?
WPA2 Enterprise with 802.1X is being used for clients to authenticate to a wireless network through a Cisco ISE server. For security reasons, the network engineer wants to ensure that only PEAP authentication is used. The engineer sent instructions to clients on how to configure the supplicants, but the ISE logs still show users authenticating using EAP-FAST. Which action ensures that access to the network is restricted for these users unless the correct authentication mechanism is configured?
An engineer must configure MSE to provide guests access using social media authentication. Which service does the engineer configure so that guests use Facebook credentials to authenticate?
After looking in the logs, an engineer notices that RRM keeps changing the channels for non-IEEE 802.11 interferers. After surveying the area, it has been decided that RRM should not change the channel. Which feature must be enabled to ignore non-802.11 interference?
A network engineer must segregate all IPads on the guest WLAN to a separate VLAN. How does the engineer accomplish this task without using Cisco
ISE?
An engineer just added a new MSE to Cisco Prime Infrastructure and wants to synchronize the MSE with the Cisco 5520 WLC, located behind a firewall in a DMZ. It is noticed that NMSP messages are failing between the two devices. Which traffic must be allowed on the firewall to ensure that the MSE and WLC are able to communicate using NMSP?
A multitenant building contains known wireless networks in most of the suites. Rogues must be classified in the WLC. How are the competing wireless APs classified?
A wireless network has two RF groups where Cisco WLCs are joined. APs are associated with different controllers using the round-robin approach. Rogue containment must be deployed v\ all controllers, but the network must not be affected by any RRM neighbor packets sent by friendly APs. Which AP authentication protection type must be enabled?
A company is collecting the requirements for an on-premises event. During the event, a wireless client connected to a dedicated WLAN will run a video application that will need on average 391595179 bits per second to function properly. What is the QoS marking that needs to be applied to that WLAN?
A wireless network engineer must present a list of all rogue APs with a high severity score to senior management. Which report must be created in Cisco Prime Infrastructure to provide this information?
A Cisco WLC has been added to the network and Cisco ISE as a network device, but authentication is failing. Which configuration within the network device configuration should be verified?
An engineer must use Cisco AVC on a Cisco WLC to prioritize Cisco IP cameras that use the wireless network. Which element do you configure in a rule?
A customer wants to allow employees to easily onboard their personal devices to the wireless network. The visitors also must be able to connect to the same network without the need to engage with anyone from the reception desk. Which process must be configured on Cisco ISE to support this requirement?
An engineer is responsible for a wireless network for an enterprise. The enterprise has distributed offices around the globe, and all APs are configured in FlexConnect mode. The network must be configured to support 802.11r and CCKM. What needs to be implemented to accomplish this goal?
An engineer has implemented advanced location services for a retail wireless deployment. The marketing department wants to collect user demographic information in exchange for guest WLAN access and to have a customized portal per location hosted by the provider. Which social connector must be tied into Cisco CMX to provide this service?
A wireless engineer is configuring LWA using ISE. The customer is a startup company and requested the wireless users to authenticate against a directory, but LDAP is unavailable. Which solution should be proposed in order to have the same security and user experience?
Which two configurations are applied on the WLC to enable multicast, check multicast stream subscriptions, and stream content only to subscribed clients? (Choose two)
An engineer must run a Client Traffic Stream Metrics report in Cisco Prime Infrastructure. Which task must be run before the report?
What is characteristic of Multicast mode that affects the wireless network when configured on a Cisco WLC?
Which two steps are needed to complete integration of the MSE to Cisco Prime Infrastructure to track the location of clients/rogues on maps? (Choose two.)
An engineer is following the proper upgrade path to upgrade a Cisco AireOS WLC from version 7.3 to 8.9. Which two ACLs for Cisco CWA must be configured when upgrading from the specified codes? (Choose two.)
An engineer has configured Media Stream on the WLC and must guarantee at least 2 Mbps stream per user. Which RRC template should the engineer use?
Refer to the exhibit.
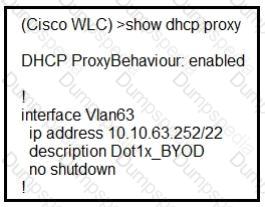
A network administrator deploys the DHCP profiler service in two ISE servers: 10.3.10.101 and 10.3.10.102. All BYOD devices connecting to WLAN on VLAN63 have been incorrectly profiled and are assigned as unknown profiled endpoints. Which action efficiently rectifies the issue according to Cisco recommendations?
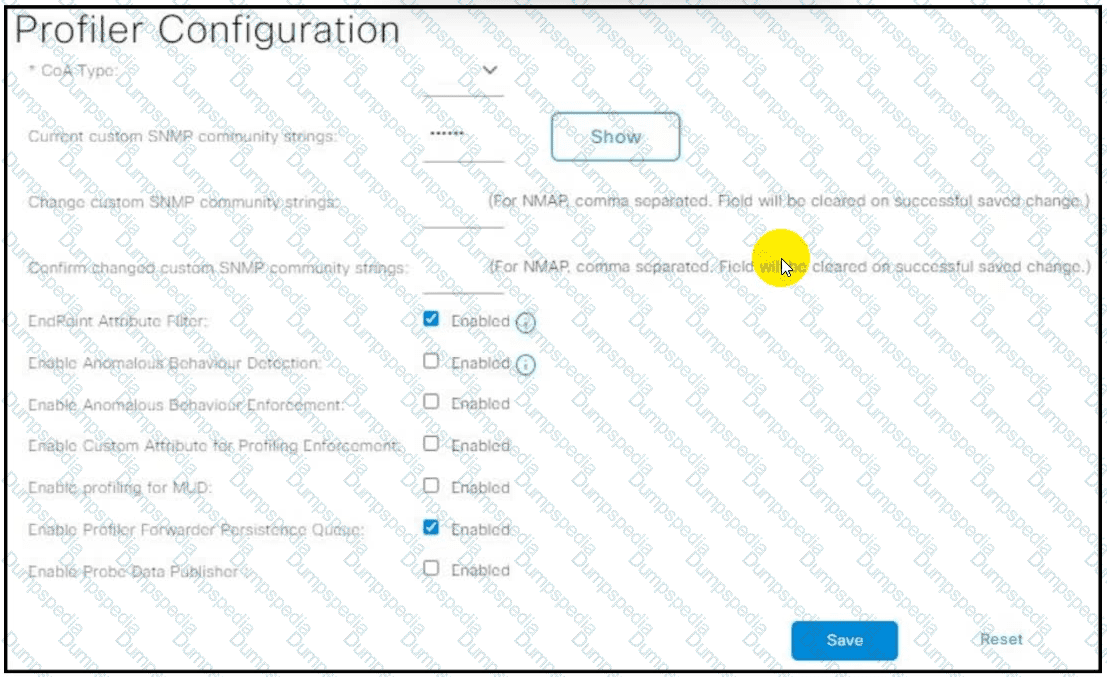
Refer to the exhibit. A network administrator must migrate a Cisco Catalyst 9800 WLC from local client profiling to RADIUS profiling through Cisco ISE. The engineer must enable RADIUS CoA based on detecting the client type as Windows to update the access policy based on profile detection immediately. Which CoA type configuration must the engineer apply on Cisco ISE?
CMX Facebook Wi-Fi allows access to the network before authentication. Which two elements are available? (Choose two.)
An engineer needs to provision certificates on a Cisco Catalyst 9800 Series Wireless Controller. The customer uses a third-party CA server. Which protocol must be used between the controller and CA server to request and install certificates?
An engineer set up a VoWLAN with QoS on the WLC and a class map on the switch, but the markings are not being preserved correctly in the end-to- end traffic flow. Which two configurations on the wired network ensure end-to-end QoS? (Choose two.)
Which three characteristics of a rogue AP pose a high security risk? (Choose three.)
A healthcare organization notices many rogue APs and is concerned about a honeypot attack. Which configuration must a wireless network engineer perform in Cisco Prime Infrastructure to prevent these attacks most efficiently upon detection?
An IT team is growing quickly and needs a solution for management device access. The solution must authenticate users from an external repository instead of the current local on the WLC, and it must also identify the user and determine what level of access users should have. Which protocol do you recommend to achieve these goals?
The security policy mandates that only controller web management traffic is allowed from the IT subnet. In testing, an engineer is trying to connect to a WLAN with Web Authentication for guest users, but the page is timing out on the wireless client browser. What is the cause of the issue?
A customer is experiencing performance issues with its wireless network and asks a wireless engineer to provide information about all sources of interference and their impacts to the wireless network over the past few days. Where can the requested information be accessed?
You enter the command or a Cisco Catalyst 3850 Series Switch that runs Cisco ISO XE. What does the command do?
An engineer is adding APs to an existing VolMLAN to allow for location based services. Which option will the primary change be to the network?
An engineer must control administrative access to the WLC using their Active Directory without being concerned about RBAC after the admin user is authenticated. Which two features does the engineer configure to accomplish this task? (Choose two.)
On a branch office deployment, it has been noted that if the FlexConnect AP is in standalone mode and loses connection to the WLC, all clients are disconnected, and the SSID is no longer advertised. Considering that FlexConnect local switching is enabled, which setting is causing this behavior?
An engineer must implement a BYOD policy with these requirements:
Onboarding unknown machines
Easily scalable
Low overhead on the wireless network
Which method satisfies these requirements?
Refer to the exhibit.
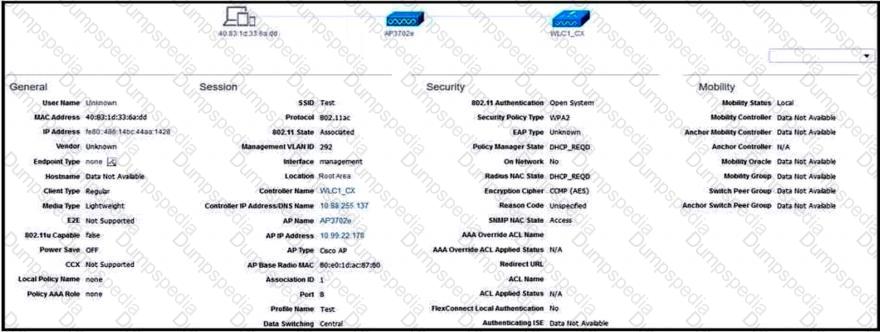
What is the reason that the wireless client cannot get the RUN state?
An enterprise started using WebEx as a virtual meeting solution. There is a concern that the existing wireless network will not be able to support the increased amount of traffic as a result of using WebEx. An engineer needs to remark the QoS value for this application to ensure high quality in meetings. What must be implemented to accomplish this task?
The CTO of an organization wants to ensure that all Android devices are placed into a separate VLAN on their wireless network. However, the CTO does not want to deploy ISE. Which feature must be implemented on the Cisco WLC?
After installing and configuring Cisco CMX, an administrator must change the NTP server on the Cisco CMX server. Which action accomplishes this task?
An engineer must implement Cisco Identity-Based Networking Services at a remote site using ISE to dynamically assign groups of users to specific IP subnets. If the subnet assigned to a client is available at the remote site, then traffic must be offloaded locally, and subnets are unavailable at the remote site must be tunneled back to the WLC. Which feature meets these requirements?
An IT team is growing quickly and needs a solution for management device access. The solution must authenticate users from an external repository instead of the current local on the WLC, and it must also identify the user and determine what level of access users should have. Which protocol do you recommend to achieve these goals?
An IT administrator is managing a wireless network in which most devices are Apple iOS. A QoS issue must be addressed on the WLANs. Which configuration must be performed?
An engineer is setting up a new unique NAD on a Cisco ISE.
Which two parameters must be configured? (Choose two.)
Refer to the exhibit.
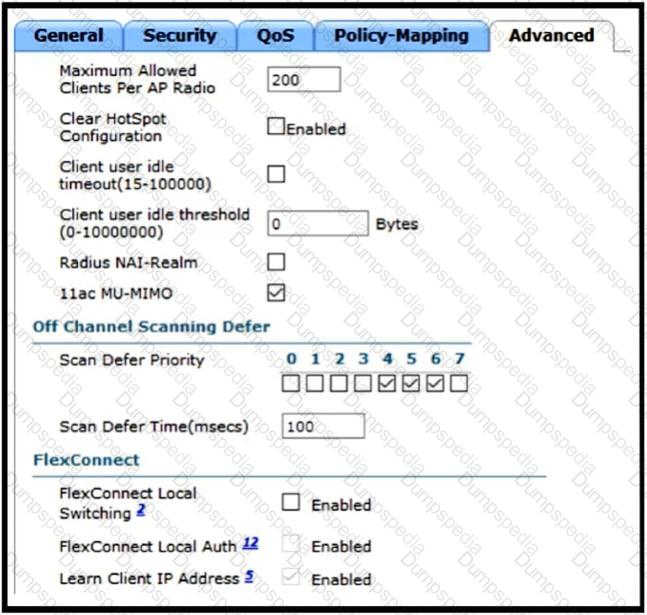
A customer has implemented Cisco FlexConnect deployments with different WLANs around the globe and is opening a new branch in a different location. The engineer’s task is to execute all the wireless configuration and to suggest how to configure the switch ports for new APs. Which configuration must the switching team use on the switch port?
An engineer is configuring an autonomous AP to allow 802.1X authentication for users. The policy on the RADIUS server only allows for EAP-TLS authentication. Which authentication method must the engineer select under the Client Authentication Settings for the SSID on the AP?
Refer to the exhibit.
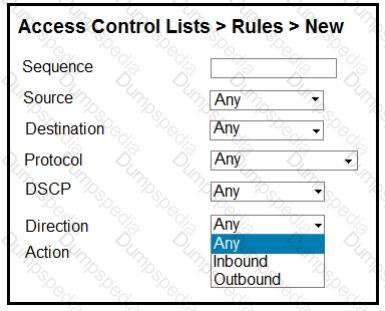
An engineer is creating an ACL to restrict some traffic to the WLC CPU. Which selection must be made from the direction drop- down list?
Refer to the exhibit.
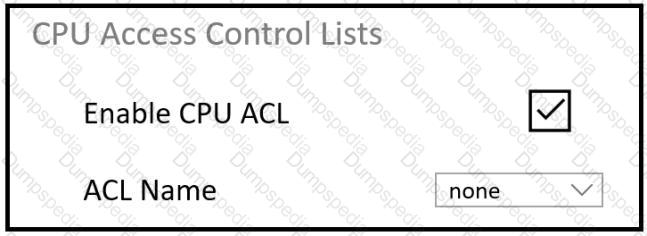
An engineer must restrict some subnets to have access to the WLC. When the CPU ACL function is enabled, no ACLs in the drop-down list are seen. What is the cause of the problem?
What must be configured on the Global Configuration page of the WLC for an AP to use 802.1x to authenticate to the wired infrastructure?
Refer to the exhibit.
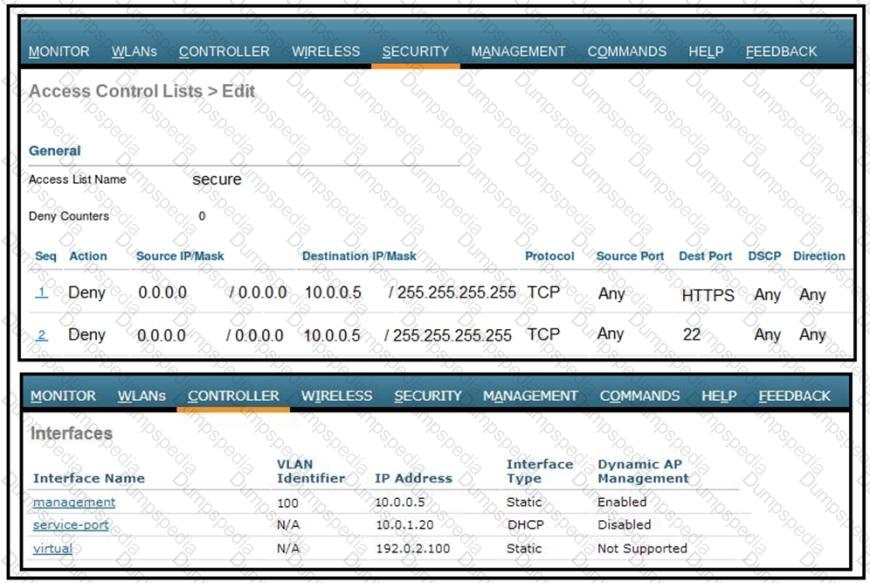
An engineer implemented the CPU ACL on your Cisco 5520 Series Wireless LAN Controller, and the controller is no longer manageable via the network. What must be changes on this CPU ACL to enable it to manage the controller again?
A company is concerned about unauthorized APs on their wired and wireless networks. The company implements a Cisco Catalyst Center (formerly DNA Center) solution. Which feature must be enabled?
An engineer is implementing profiling for BYOD devices using Cisco ISE. When using a distributed model, which persona must the engineer configure with the profiling service?
An engineer configured a Cisco AireOS controller with two TACACS+ servers. The engineer notices that when the primary TACACS+ server fails, the WLC starts using the secondary server as expected, but the WLC does not use the primary server again until the secondary server fails or the controller is rebooted. Which cause of this issue is true?
An engineer is in the process of implementing Fastlane on a wireless network with a Mobility Express AP installed. The network must support voice and video applications for Apple devices. Due to a security concern, all iPhones are updated to version 14.5.432302546. Which QoS profile must the engineer configure on the user WLAN?
A corporation has a wireless network where all access points are configured in FlexConnect. The WLC has a Data WLAN and a VoWiFi WLAN implemented where centrally-switched SSID is configured for the APs. Which QoS configuration must be implemented for the wireless packets to maintain the marking across the wired and wireless network?
An engineer must achieve the highest level of location accuracy possible for a new mobile application. Which technology must be implemented for this use case?
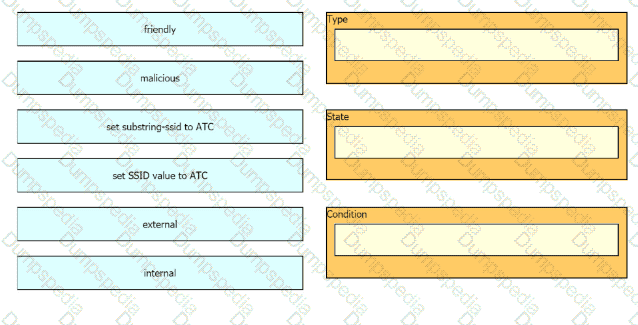
The network management team in a large shopping center has detected numerous rogue APs from local coffee shops that are broadcasting SSIDs. All of these SSIDs have names starting with ATC (for example, ATC302, ATC011, and ATC566). A wireless network engineer must appropriately classify these SSIDs using the Rogue Rules feature. Drag and drop the options from the left onto the categories in which they must be used on the right. Not all options are used.
Refer to the exhibit.
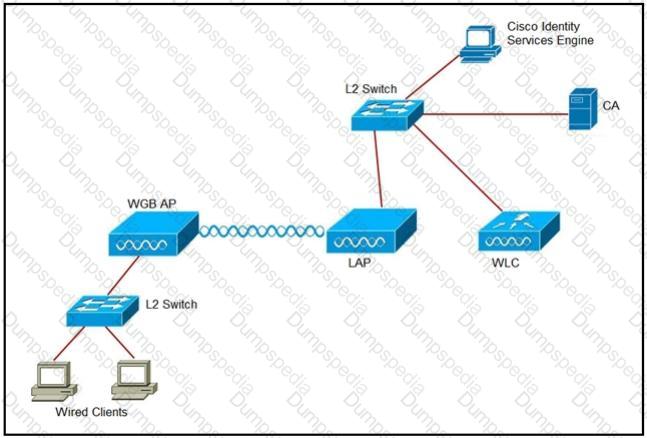
An engineer must connect a fork lift via a WGB to a wireless network and must authenticate the WGB certificate against the RADIUS server. Which three steps are required for this configuration? (Choose three.)
A healthcare organization notices many rogue APs and is concerned about a honeypot attack. Which configuration must a wireless network engineer perform in Cisco Prime Infrastructure to prevent these attacks most efficiently upon detection?
An engineer wants the wireless voice traffic class of service to be used to determine the queue order for packets received, and then have the differentiated services code point set to match when it is resent to another port on the switch. Which configuration is required in the network?
Company XYZ recently migrated from AireOS to IOS XE 9800 WLCs. The Internet bandwidth must be limited to 5 Mbps for each guest client as per the global standard. In which configuration on the Cisco Catalyst 9800 WLC must the QoS requirement be added?
A company wants to utilize the wireless network to push videos to wireless clients. An engineer has been hired to configure a Cisco WLC to notify users when it cannot provide a video stream while using the Multicast Direct Feature. Which settings must be enabled for this functionality?
An engineer completes the setup of a two-node Cisco ISE deployment for a guest portal. When testing the portal, the engineer notices that sometimes there is a certificate CN mismatch. Which certificate type helps resolve this issue?
Refer to the exhibit.
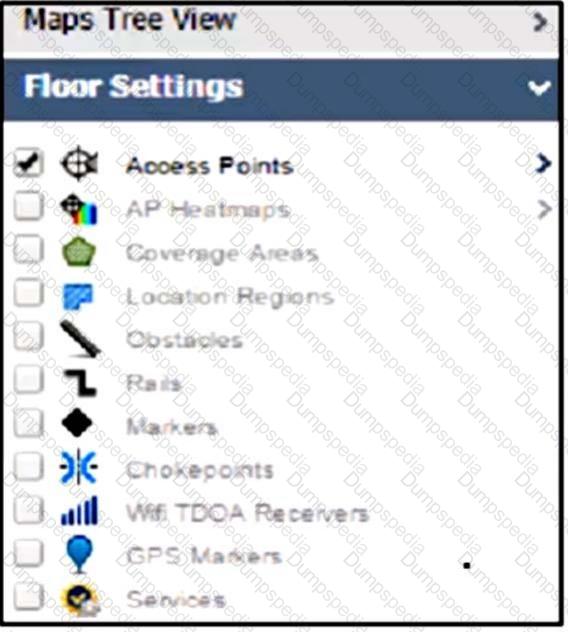
An engineer must provide a position of rogue APs on a floor map using Cisco PI 3.0, but no rogue AP options are showing on the left-hand navigation menu under Maps. What is the reason for this omission?
When implementing self-registration for guest/BYOD devices, what happens when an employee tries to connect four devices to the network at the same time?
A customer managing a large network has implemented location services. Due to heavy load, it is needed to load balance the data coming through NMSP from the WLCs. Load must be spread between multiple CMX servers to help optimize the data flow for APs. Which configuration in CMX meets this requirement?
An engineer is troubleshooting a Cisco CMX high-availability deployment and notices that the primary and backup Cisco CMX servers are both considered primary. Which command must the engineer run on the backup server?
An engineer is troubleshooting rogue access points that are showing up in Cisco Prime Infrastructure.
What is maximum number of APS the engineer can use to contain an identified rogue access point in the WLC?
Refer to the exhibit.

An engineer is creating an ACL to restrict some traffic to the WLC CPU. Which selection must be made from the direction drop- down list?
A company is deploying wireless PCs on forklifts within its new 10,000-square-foot(3048-square-rneter) facility.
The clients are configured for PEAP-MS-CHAPv2 with WPA TKIP. Users report that applications frequently drop when the clients roam between access points on the floor. A professional site survey was completed.
Which configuration change is recommended to improve the speed of client roaming?
A network engineer created a new wireless network that will be used for guest access. The corporate network must utilize all rates. The guest network must use only lower rates instead of 802.11n data rates. To what must the WMM policy of the WLAN be set to accomplish this task?
Which configuration is applied to prevent the network from a Layer 2 flooding of multicast frames with a seamless transfer of multicast data to the client when roaming from one controller to another?