Which certificate is needed during profile configuration when configuring an iOS Mobile SSO profile within VMware Workspace ONE UEM?
Which service on the connector server must be able to access the RADIUS server when configuring RADIUS (cloud deployment) authentication?
Which combination of authentication challenges does an integration of RSA SecurID in Workspace ONE Access provide to protect resources?
What is the primary benefit of utilizing Verify (Intelligent Hub) authentication m VMware Workspace ONE Access?
Which two Workspace ONE UEM services require persistence on the load balancers to support an environment of 25,000 devices? (Choose two.)
An administrator has been tasked with building and enabling Secure Email Gateway (SEG) V2 n the Unified Access Gateway (UAG).
How should the SSL certificate be added to the UAG?
What is the primary purpose of VMware Workspace ONE Trust Network in VMware Workspace ONE Intelligence?
Which three resources can be deployed to users through Workspace ONE Access? (Choose three.)
An organization wants to prevent users from connecting to VMware Horizon desktop or application pools from a Horizon Pod deployed on their internal network unless the user selects the Horizon pool from the Unified Catalog of their Workspace ONE Access shared SaaS tenant.
Which additional setting must the organization administrator configure?
Which two options are valid when managing directories m VMware Workspace ONE Access through the Manage > Directories page? (Choose two.)
Which two solutions needs to be integrated for an administrator to have conditional access with User Risk Score? (Choose two.)
An administrator is creating a REST API call to the following Workspace ONE Access URL:
https://access.company.com/api/token/auth/state
The HTTP method of the request is POST, and the body of the request is as follows:
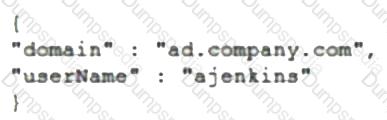
Consider the URL, HTTP method, and request body.
Which goal is the administrator attempting to meet?
A VMware Workspace ONE environment has been setup with Roles Based Access Control (RBAC), and the directory-based administrators who managed in Workspace ONE UEM have limited permissions to access the console.
The administrator has enabled VMware Workspace ONE Intelligence in the environment and must now enable the correct configuration setting that will allow administrators to access VMware Workspace ONE Intelligence from VMware Workspace ONE UEM.
Which configuration setting must be enabled?
Which step is required to set up Hub Digital Badge Service in VMware Workspace ONE Hub Services?