A security administrator is advocating for enforcement of a new policy that would require employers with privileged access accounts to undergo periodic inspections and review of certain job performance data. To which of the following policies is the security administrator MOST likely referring?
An organization is moving internal core data-processing functions related to customer data to a global public cloud provider that uses aggregated services from other partner organizations. Which of the following compliance issues will MOST likely be introduced as a result of the migration?
A firewall specialist has been newly assigned to participate in red team exercises and needs to ensure the skills represent real-world threats. Which of the following would be the BEST choice to help the new team member learn bleeding-edge techniques?
A company has completed the implementation of technical and management controls as required by its adopted security, ponies and standards. The implementation took two years and consumed s the budget approved to security projects. The board has denied any further requests for additional budget. Which of the following should the company do to address the residual risk?
A security engineer is assessing a new IoT product. The product interfaces with the ODBII port of a vehicle and uses a Bluetooth connection to relay data to an onboard data logger located in the vehicle. The data logger can only transfer data over a custom USB cable. The engineer suspects a relay attack is possible against the cryptographic implementation used to secure messages between segments of the system. Which of the following tools should the engineer use to confirm the analysis?
A medical device company is implementing a new COTS antivirus solution in its manufacturing plant. All validated machines and instruments must be retested for interoperability with the new software. Which of the following would BEST ensure the software and instruments are working as designed?
A Chief Information Security Officer (CISO is reviewing and revising system configuration and hardening guides that were developed internally and have been used several years to secure the organization’s systems. The CISO knows improvements can be made to the guides.
Which of the following would be the BEST source of reference during the revision process?
The security configuration management policy states that all patches must undergo testing procedures before being moved into production. The sec… analyst notices a single web application server has been downloading and applying patches during non-business hours without testing. There are no apparent adverse reaction, server functionality does not seem to be affected, and no malware was found after a scan. Which of the following action should the analyst take?
A large, public university has recently been experiencing an increase in ransomware attacks against computers connected to its network. Security engineers have discovered various staff members receiving seemingly innocuous files in their email that are being run. Which of the following would BEST mitigate this attack method?
A security researcher is gathering information about a recent spoke in the number of targeted attacks against multinational banks. The spike is on top of already sustained attacks against the banks. Some of the previous attacks have resulted in the loss of sensitive data, but as of yet the attackers have not successfully stolen any funds.
Based on the information available to the researcher, which of the following is the MOST likely threat profile?
While conducting a BIA for a proposed acquisition, the IT integration team found that both companies outsource CRM services to competing and incompatible third-party cloud services. The decision has been made to bring the CRM service in-house, and the IT team has chosen a future solution. With which of the following should the Chief Information Security Officer (CISO) be MOST concerned? (Choose two.)
A security engineer must establish a method to assess compliance with company security policies as they apply to the unique configuration of individual endpoints, as well as to the shared configuration policies of common devices.
Which of the following tools is the security engineer using to produce the above output?
A security engineer is attempting to increase the randomness of numbers used in key generation in a system. The goal of the effort is to strengthen the keys against predictive analysis attacks.
Which of the following is the BEST solution?
A recent assessment identified that several users’ mobile devices are running outdated versions of endpoint security software that do not meet the company’s security policy. Which of the following should be performed to ensure the users can access the network and meet the company’s security requirements?
A company has deployed MFA Some employees, however, report they ate not gelling a notification on their mobile device Other employees report they downloaded a common authenticates application but when they tap the code in the application it just copies the code to memory instead of confirming the authentication attempt Which of the following are the MOST likely explanations for these scenarios? (Select TWO)
A Chief Information Security Officer (CISO) is developing a new BIA for the organization. The CISO wants to gather requirements to determine the appropriate RTO and RPO for the organization’s ERP. Which of the following should the CISO interview as MOST qualified to provide RTO/RPO metrics?
A software development team has spent the last 18 months developing a new web-based front-end that will allow clients to check the status of their orders as they proceed through manufacturing. The marketing team schedules a launch party to present the new application to the client base in two weeks. Before the launch, the security team discovers numerous flaws that may introduce dangerous vulnerabilities, allowing direct access to a database used by manufacturing. The development team did not plan to remediate these vulnerabilities during development.
Which of the following SDLC best practices should the development team have followed?
Following the successful response to a data-leakage incident, the incident team lead facilitates an exercise that focuses on continuous improvement of the organization’s incident response capabilities. Which of the following activities has the incident team lead executed?
A database administrator is required to adhere to and implement privacy principles when executing daily tasks. A manager directs the administrator to reduce the number of unique instances of PII stored within an organization’s systems to the greatest extent possible. Which of the following principles is being demonstrated?
A pharmacy gives its clients online access to their records and the ability to review bills and make payments. A new SSL vulnerability on a specific platform was discovered, allowing an attacker to capture the data between the end user and the web server providing these services. After the new vulnerability, it was determined that web services provided are being impacted by this new threat. Which of the following data types MOST likely at risk of exposure based on this new threat? (Select Two)
As part of an organization's ongoing vulnerability assessment program, the Chief Information Security Officer (CISO) wants to evaluate the organization's systems, personnel, and facilities for various threats As part of the assessment the CISO plans to engage an independent cybersecurity assessment firm to perform social engineering and physical penetration testing against the organization's corporate offices and remote locations. Which of the following techniques would MOST likely be employed as part of this assessment? (Select THREE).
A Chief Information Security Officer (CISO) is running a test to evaluate the security of the corporate network and attached devices. Which of the following components should be executed by an outside vendor?
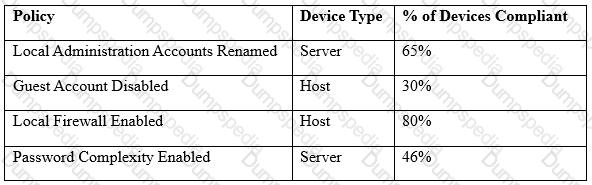
A security analyst is reading the results of a successful exploit that was recently conducted by third-party penetration testers. The testers reverse engineered a privileged executable. In the report, the planning and execution of the exploit is detailed using logs and outputs from the test However, the attack vector of the exploit is missing, making it harder to recommend remediation’s. Given the following output:
The penetration testers MOST likely took advantage of:
A security is testing a server finds the following in the output of a vulnerability scan:

Which of the following will the security analyst most likely use NEXT to explore this further?
A new employee is plugged into the network on a BYOD machine but cannot access the network Which of the following must be configured so the employee can connect to the network?
A company that all mobile devices be encrypted, commensurate with the full disk encryption scheme of assets, such as workstation, servers, and laptops. Which of the following will MOST likely be a limiting factor when selecting mobile device managers for the company?
A cloud architect needs to isolate the most sensitive portion of the network while maintaining hosting in a public cloud Which of the following configurations can be employed to support this effort?
A system administrator at a medical imaging company discovers protected health information (PHI) on a general-purpose file server. Which of the following steps should the administrator take NEXT?
Which of the following may indicate a configuration item has reached end-of-life?
A developer is writing a new mobile application that employees will use to connect to an Internet-facing sensitive system The security team is concerned with MITM attacks against the encrypted application traffic aimed at intercepting and decrypting sensitive information from the server to the mobile client. Which of the following should the developer implement to address the security team's concerns? (Select TWO).
Which of the following is the BEST way for a company to begin understanding product-based solutions to mitigate a known risk?
A company s design team is increasingly concerned about intellectual property theft Members of the team often travel to suppliers' offices where they collaborate and share access to their sensitive data. Which of the following should be implemented?
A company recently developed a new mobile application that will be used to access a sensitive system. The application and the system have the following requirements:
• The application contains sensitive encryption material and should not be accessible over the network
• The system should not be exposed to the Internet
• Communication must be encrypted and authenticated by both the server and the client
Which of the following can be used to install the application on the mobile device? (Select TWO).
A company needs to deploy a home assistant that has the following requirement:
1. Revalidate identity when sensitive personal information is accessed and when there is a change m device state. 2 Authenticate every three months and upon registration 3. Support seamless access on all channel
Which of the following actions would be BEST to support the above requirements securely? (Select TWO).
Following a major security modem that resulted in a significant loss of revenue and extended loss of server availability, a new Chief Information Security Officer (CISO) conducts a root cause analysis. Which of the following additional steps should the CISO take to mitigate the chance of a recurrence?
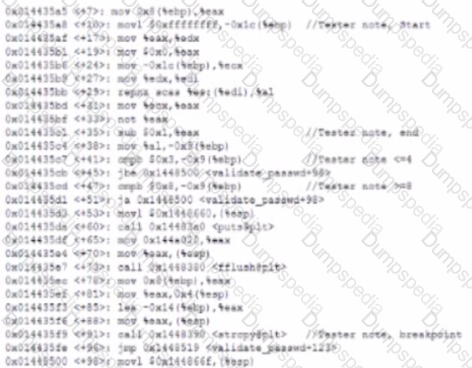
An extensive third-party audit reveals a number of weaknesses m a company's endpoint security posture. The most significant issues are as follows:
Which of the following endpoint security solutions mitigate the GREATEST amount of risk?
A security technician wants to learn about the latest zero-day threats and newly discovered vulnerabilities but does not have the budget to purchase a commercial threat intelligence service. Which of the following would BEST meet the needs of the security technician? (Select TWO)
An administrative control that is put in place to ensure one person cannot carry out a critical task independently is:
The OS on several servers crashed around the same time for an unknown reason. The servers were restored to working condition, and all file integrity was verified. Which of the following should the incident response team perform to understand the crash and prevent it in the future?
A security analyst must carry out the incident response plan for a specific targeted attack that was detected by the security operations center. The director of network security wants to ensure this type of attack cannot be executed again in the environment. Which of the following should the analyst present to the director to BEST meet the director's goal?
A Chief information Security Officer (CISO) has launched to create a rebuts BCP/DR plan for the entire company. As part of the initiative , the security team must gather data supporting s operational importance for the applications used by the business and determine the order in which the application must be back online. Which of the following be the FIRST step taken by the team?
A company is purchasing an application that will be used to manage all IT assets as well as provide an incident and problem management solution for IT activity The company narrows the search to two products. Application A and Application B; which meet all of its requirements. Application A is the most cost-effective product, but it is also the riskiest so the company purchases Application B. Which of the following types of strategies did the company use when determining risk appetite?
A vulnerability was recently announced that allows a malicious user to gain root privileges on other virtual machines running within the same hardware cluster. Customers of which of the following cloud-based solutions should be MOST concerned about this vulnerability?
A penetration tester is trying to gain access to a remote system. The tester is able to see the secure login page and knows one user account and email address, but has not yet discovered a password.
Which of the following would be the EASIEST method of obtaining a password for the known account?
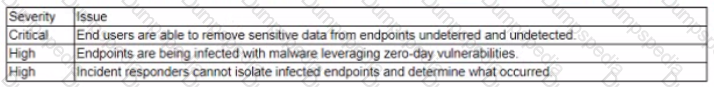
A forensic analyst must image the hard drive of a computer and store the image on a remote server. The analyst boots the computer with a live Linux distribution. Which of the following will allow the analyst to copy and transfer the file securely to the remote server?
A)

B)
C)
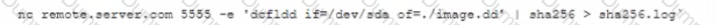
D)

A security engineer is attempting to inventory all network devices Most unknown devices are not responsive to SNMP queries. Which of the following would be the MOST secure configuration?
A company is planning to undergo a P2V project to improve resource utilisation redundancy, and failover across its two datacenters A consultant has provided a private cloud design that uses a specific Type 1 hypervisor based on Linux. The security manager is concerned about the integrity of the hypervisor Which of the following should the consultant suggest to address the security manager's concerns?
The Chief information Officer (CIO) wants to establish a non-banding agreement with a third party that outlines the objectives of the mutual arrangement dealing with data transfers between both organizations before establishing a format partnership. Which of the follow would MOST likely be used?
An organization wishes to implement cloud computing, but it is not sure which service to choose. The organization wants to be able to share Tiles, collaborate, and use applications that are fully managed on a private network. Which of the following types of cloud computing services should the organization implement based on its needs?
A security researcher at an organization is reviewing potential threats to the VolP phone system infrastructure which uses a gigabit Internet connection. The researcher finds a vulnerability and knows placing an IPS in front of the phone system will mitigate the risk. The researcher gathers the following information about various IPS systems:
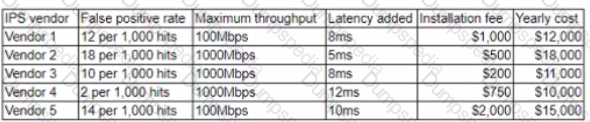
The organization is concerned about cost, but call quality is critical to its operations Which of the foAotmng vendors would be BEST for the organization to choose?
A security administrator wants to stand up a NIPS that is multilayered and can incorporate many security technologies into a single platform The product should have diverse capabilities, such as antivirus, VPN, and firewall services, and be able to be updated in a timely manner to meet evolving threats. Which of the following network prevention system types can be used to satisfy the requirements?
The security administrator of a small firm wants to stay current on the latest security vulnerabilities and attack vectors being used by crime syndicates and nation-states. The information must be actionable and reliable. Which of the following would BEST meet the needs of the security administrator?
While the code is still in the development environment, a security architect is testing the code stored in the code repository to ensure the top ten OWASP secure coding practices are being followed. Which of the following code analyzers will produce the desired results?
A new database application was added to a company’s hosted VM environment. Firewall ACLs were modified to allow database users to access the server remotely. The company’s cloud security broker then identified abnormal from a database user on-site. Upon further investigation, the security team noticed the user ran code on a VM that provided access to the hypervisor directly and access to other sensitive data.
Which of the following should the security do to help mitigate future attacks within the VM environment? (Choose two.)
A Chief Information Security Officer (CISO) implemented MFA for all accounts in parallel with the BYOD policy. After the implementation, employees report the increased authentication method is causing increased time to tasks. This applies both to accessing the email client on the workstation and the online collaboration portal. Which of the following should be the CISO implement to address the employees’ concerns?
The results of an external penetration test for a software development company show a small number of applications account for the largest number of findings. While analyzing the content and purpose of the applications, the following matrix is created.
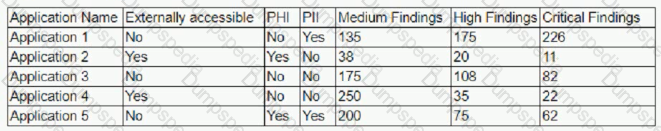
The findings are then categorized according to the following chart:
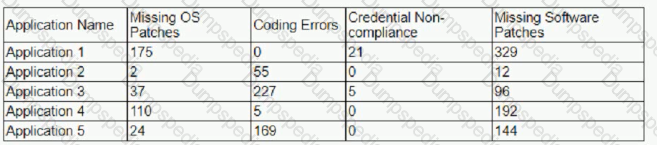
Which of the following would BEST reduce the amount of immediate risk incurred by the organization from a compliance and legal standpoint? (Select TWO)
An application has been through a peer review and regression testing and is prepared for release. A security engineer is asked to analyze an application binary to look for potential vulnerabilities prior to wide release. After thoroughly analyzing the application, the engineer informs the developer it should include additional input sanitation in the application to prevent overflows. Which of the following tools did the security engineer MOST likely use to determine this recommendation?
Due to a recent acquisition, the security team must find a way to secure several legacy applications. During a review of the applications, the following issues are documented:
The applications are considered mission-critical.
The applications are written in code languages not currently supported by the development staff.
Security updates and patches will not be made available for the applications.
Username and passwords do not meet corporate standards.
The data contained within the applications includes both PII and PHI.
The applications communicate using TLS 1.0.
Only internal users access the applications.
Which of the following should be utilized to reduce the risk associated with these applications and their current architecture?
A laptop is recovered a few days after it was stolen.
Which of the following should be verified during incident response activities to determine the possible impact of the incident?
A company runs a well –attended, on-premises fitness club for its employees, about 200 of them each day. Employees want to sync center’s login and attendance program with their smartphones. Human resources, which manages the contract for the fitness center, has asked the security architecture to help draft security and privacy requirements. Which of the following would BEST address these privacy concerns?
A security administrator receives reports that several workstations are unable to access resources within one network segment. A packet capture shows the segment is flooded with ICMPv6 traffic from the source fe80::21ae;4571:42ab:1fdd and for the destination ff02::1. Which of the following should the security administrator integrate into the network to help prevent this from occurring?
A company is deploying a DIP solution and scanning workstations and network drives for documents that contain potential Pll and payment card data. The results of the first scan are as follows:
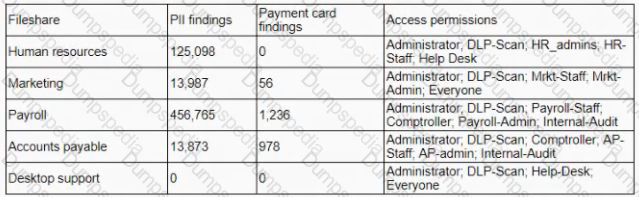
The security learn is unable to identify the data owners for the specific files in a timely manner and does not suspect malicious activity with any of the detected files. Which of the following would address the inherent risk until the data owners can be formally identified?
Joe an application security engineer is performing an audit of an environmental control application He has implemented a robust SDLC process and is reviewing API calls available to the application During the review. Joe finds the following in a log file.
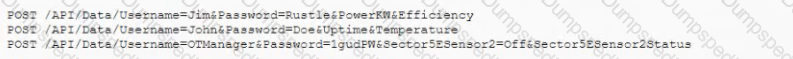
Which of the following would BEST mitigate the issue Joe has found?
Users of a newly deployed VoIP solution report multiple instances of dropped or garbled calls. Thirty users
connect to the primary site via a site-to-site VPN, and the primary site supplies a dial tone to all satellite
locations. The network engineer who installed the equipment copied the configuration from a site that has two
users on a low bandwidth DSL connection. Which of the following is MOST likely to restore telephone
availability at the 30-user site?
Ann, a CIRT member, is conducting incident response activities on a network that consists of several hundred virtual servers and thousands of endpoints and users. The network generates more than 10,000 log messages per second. The enterprise belong to a large, web-based cryptocurrency startup, Ann has distilled the relevant information into an easily digestible report for executive management . However, she still needs to collect evidence of the intrusion that caused the incident. Which of the following should Ann use to gather the required information?
A creative services firm has a limited security budget and staff. Due to its business model, the company sends and receives a high volume of files every day through the preferred method defined by its customers. These include email, secure file transfers, and various cloud service providers. Which of the following would BEST reduce the risk of malware infection while meeting the company's resource requirements and maintaining its current workflow?
An e-commerce company that provides payment gateways is concerned about the growing expense and time associated with PCI audits of its payment gateways and external audits by customers for their own compliance reasons The Chief Information Officer (CIO) asks the security team to provide a list of options that will:
1. Reduce the overall cost of these audits
2. Leverage existing infrastructure where possible
3. Keep infrastructure costs to a minimum
4. Provide some level of attestation of compliance
Which of the following will BEST address the CIO"s concerns? (Select TWO)
Confidential information related to Application A. Application B and Project X appears to have been leaked to a competitor. After consulting with the legal team, the IR team is advised to take immediate action to preserve evidence for possible litigation and criminal charges.
While reviewing the rights and group ownership of the data involved in the breach, the IR team inspects the following distribution group access lists:
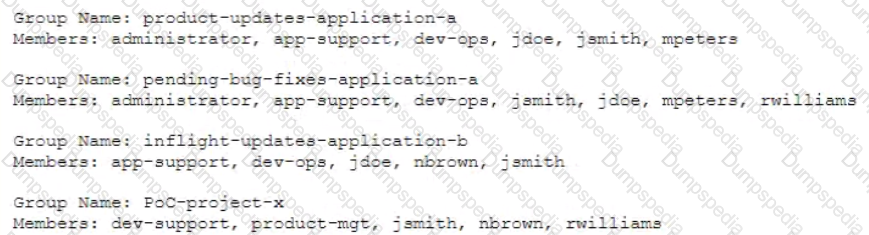
Which of the following actions should the IR team take FIRST?
The Chief Information Security Officer (CISO) is preparing a requirements matrix scorecard for a new security tool the company plans to purchase Feedback from which of the following documents will provide input for the requirements matrix scorecard during the vendor selection process?
A large industrial system’s smart generator monitors the system status and sends alerts to third-party
maintenance personnel when critical failures occur. While reviewing the network logs, the company’s security manager notices the generator’s IP is sending packets to an internal file server’s IP. Which of the following mitigations would be BEST for the security manager to implement while maintaining alerting capabilities?
A financial institution has several that currently employ the following controls:
* The severs follow a monthly patching cycle.
* All changes must go through a change management process.
* Developers and systems administrators must log into a jumpbox to access the servers hosting the data using two-factor authentication.
* The servers are on an isolated VLAN and cannot be directly accessed from the internal production network.
An outage recently occurred and lasted several days due to an upgrade that circumvented the approval process. Once the security team discovered an unauthorized patch was installed, they were able to resume operations within an hour. Which of the following should the security administrator recommend to reduce the time to resolution if a similar incident occurs in the future?
Engineers at a company believe a certain type of data should be protected from competitors, but the data owner insists the information is not sensitive. An information security engineer is implementing controls to secure the corporate SAN. The controls require dividing data into four groups: non-sensitive, sensitive but accessible, sensitive but export-controlled, and extremely sensitive. Which of the following actions should the engineer take regarding the data?
An electric car company hires an IT consulting company to improve the cybersecurity of us vehicles. Which of the following should achieve the BEST long-term result for the company?
A security engineer is investigating a compromise that occurred between two internal computers. The engineer has determined during the investigation that one computer infected another. While reviewing the IDS logs, the engineer can view the outbound callback traffic but sees no traffic between the two computers. Which of the following would BEST address the IDS visibility gap?
Historical information shows that a small aerospace R&D company has a lack of user security awareness and is susceptible to nation-state social-engineering attacks and zero-day exploits. A network engineer advises the Chief Information Security Officer (CISO) to invest m a next-generation firewall to guard against incoming traffic and allow for the development of ACLs for new sessions Which of the following is the FIRST course of action for the CISO to take?
An organization is a subsidiary of a larger firm that provides managed IT and human resources controls to the subsidiary. The subsidiary determines the contract in place between the two firms does not define and apply terms appropriate relating to the controls provided by the larger firm. Which of the following would be MOST appropriate for both firms to formally document the controls to be provided? (Select TWO.)
A company decides to procure only laptops that use permanent, solid-stale storage. Which of the following risk mitigation strategies BEST meets the company's requirement to ensure all company data is destroyed before disposing of the laptops?
A vendor develops a mobile application for global customers. The mobile application supports advanced encryption of data between the source (the mobile device) and the destination (the organization’s ERP system).
As part of the vendor’s compliance program, which of the following would be important to take into account?
During a sprint, developers are responsible for ensuring the expected outcome of a change is thoroughly evaluated for any security impacts. Any impacts must be reported to the team lead. Before changes are made to the source code, which of the following MUST be performed to provide the required information to the team lead?
A penetration testing manager is contributing to an RFP for the purchase of a new platform. The manager has provided the following requirements:
Which of the following types of testing should be included in the testing platform? (Choose two.)
A hospital is deploying new imaging softwares that requires a web server for access to image for both local and remote users. The web server allows user authentication via secure LDAP. The information security officer wants to ensure the server does not allow unencrypted access to the imaging server by using Nmap to gather additional information. Given the following.
* The imaging server IP is 192.168.101.24
* The domain controller IP is 192.168.100.1
* The client machine IP is 192.168.200.37
Which of the following should be used to confirm this is the only open post on the web server?
A legal services company wants to ensure emails to clients maintain integrity in transit Which of the following would BEST meet this requirement? (Select TWO)
A company has decided to move an ERP application to a public cloud vendor. The company wants to replicate some of its global policies from on premises to cloud. The policies include data encryption, token management, and limited user access to the ERP application. The Chief Information Officer (CIO) is mainly concerned about privileged accounts that might be compromised and used to alter data in the ERP application. Which of the following is the BEST option to meet the requirements?
A legacy SCADA system is m place in a manufacturing facility to ensure proper facility operations Recent industry reports made available to the security team state similar legacy systems are being used as part of an attack chain in the same industry market Due to the age of these devices security control options are limned Which of the following would BEST provide continuous monitoring for these threats'
A company has launched a phishing awareness campaign that includes serving customized phishing email to employees Employees are encouraged to report all phishing attempts and/or delete the email without clicking on them The first phishing email asks employees to dick on a link that takes them to a website where they are asked to enter their credentials The management team wants metrics to determine the emails effectiveness Following is the initial report:
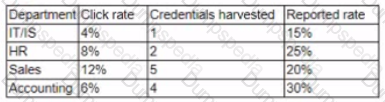
The management team wants to know how these results compare to those of other companies. They also want to improve the consistency of how the information is displayed Which of the following changes should be made to this report?
A smart switch has the ability to monitor electrical levels and shut off power to a building in the event of power surge or other fault situation. The switch was installed on a wired network in a hospital and is monitored by the facilities department via a cloud application. The security administrator isolated the switch on a separate VLAN and set up a patching routine. Which of the following steps should also be taken to harden the smart switch?
A financial services company has proprietary trading algorithms, which were created and are maintained by a team of developers on their private source code repository. If the details of this operation became known to competitors, the company's ability to profit from its trading would disappear immediately. Which of the following would the company MOST likely use to protect its trading algorithms?
A PaaS provider deployed a new product using a DevOps methodology Because DevOps is used to support both development and production assets inherent separation of duties is limited To ensure compliance with security frameworks that require a specific set of controls relating to separation of duties the organization must design and implement an appropriate compensating control Which of the following would be MOST suitable in this scenario?
A security engineer is helping the web developers assess a new corporate web application The application will be Internet facing so the engineer makes the following recommendation:
In an htaccess file or the site config add:
or add to the location block:
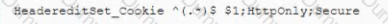
Which of the following is the security engineer trying to accomplish via cookies? (Select TWO)
Which of the following is an external pressure that causes companies to hire security assessors and penetration testers?
A consulting firm was hired to conduct assessment for a company. During the first stage, a penetration tester used a tool that provided the following output:
TCP 80 open
TCP 443 open
TCP 1434 filtered
The penetration tester then used a different tool to make the following requests:
GET / script/login.php?token=45$MHT000MND876
GET / script/login.php?token=@#984DCSPQ%091DF
Which of the following tools did the penetration tester use?
A company wants to confirm sufficient executable space protection is in place for scenarios in which malware may be attempting buffer overflow attacks. Which of the following should the security engineer check?
When reviewing KRIs of the email security appliance with the Chief Information Security Officer (CISO) of an insurance company, the security engineer notices the following:
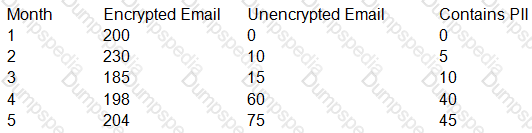
Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?
Given the following code snippet:
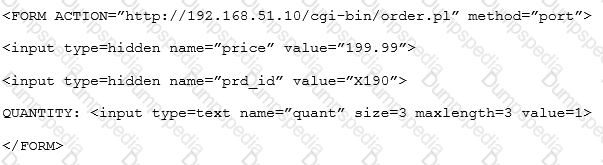
Of which of the following is this snippet an example?
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website.
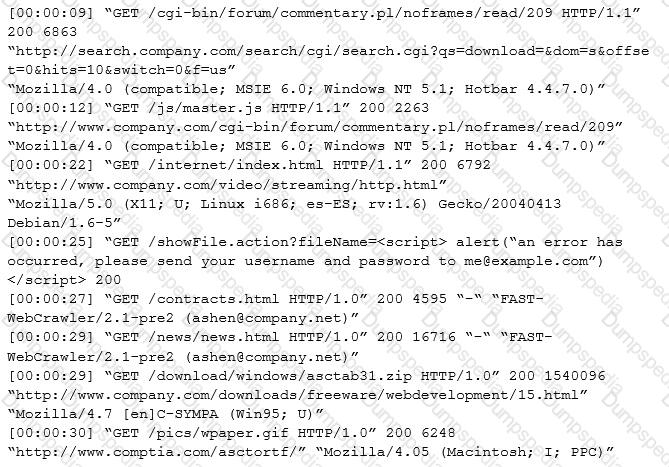
Which of the following types of attack vector did the penetration tester use?
A security analyst has been asked to create a list of external IT security concerns, which are applicable to the organization. The intent is to show the different types of external actors, their attack vectors, and the types of vulnerabilities that would cause business impact. The Chief Information Security Officer (CISO) will then present this list to the board to request funding for controls in areas that have insufficient coverage.
Which of the following exercise types should the analyst perform?
A security technician receives a copy of a report that was originally sent to the board of directors by the Chief Information Security Officer (CISO).
The report outlines the following KPVKRI data for the last 12 months:
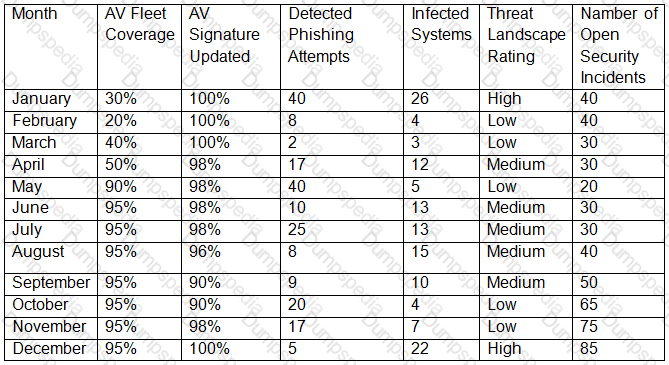
Which of the following BEST describes what could be interpreted from the above data?
A Chief Information Security Officer (CISO) requests the following external hosted services be scanned for malware, unsecured PII, and healthcare data:
Security policy also is updated to allow the security team to scan and detect any bulk downloads of corporate data from the company’s intranet and online storage site. Which of the following is needed to comply with the corporate security policy and the CISO’s request?