An agreement between a cloud service provider and a customer based on cloud-specific terms is called:
During an ISC2 CC exam, you observe another candidate cheating. What should you do?
An employee launched a privilege escalation attack to gain root access on one of the organization’s database servers. The employee has an authorized user account on the server. What log file would MOST likely contain relevant information?
What is the primary goal of Identity and Access Management (IAM) in cybersecurity?
Exhibit.
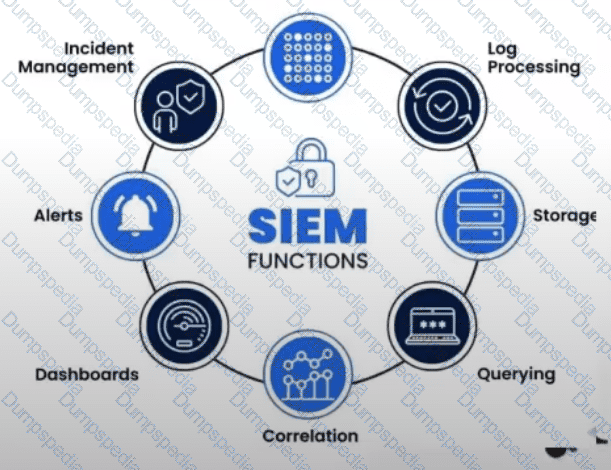
What is the purpose of a Security Information and Event Management (SIEM) system?
What kind of control is it when we add a backup firewall that takes over if the main one stops working?
A structured way to align IT with business goals while managing risk and regulations:
Which provides confidentiality by hiding or obscuring a message so it cannot be understood by unauthorized parties?
A measure of the degree to which an organization depends on information or systems to achieve its mission is called:
The evaluation of security controls to determine whether they are implemented correctly and operating as intended is known as:
After an earthquake disrupts business operations, which document contains the reactive procedures required to return business to normal operations?
The harmonization of automated computing tasks into reusable workflows is called:
Which term describes a communication tunnel that provides point-to-point transmission of authentication and data traffic over an untrusted network?
Exhibit.
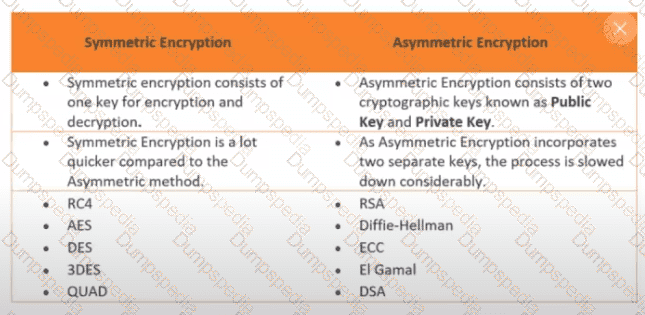
How many keys would be required to support 50 users in an asymmetric cryptography system?
To avoid bodily injury claims, a company decides not to offer high-risk services. This is an example of:
Which of these components is very likely to be instrumental to any disaster recovery (DR) effort?
Which logical control best protects confidential data from unauthorized access?
A weighted factor based on the probability that a threat will exploit a vulnerability is called:
A collection of actions that must be followed to complete a task or process in accordance with a set of rules is known as:
Which of the following is NOT an element of system security configuration management?
Networks that are heavily microsegmented with firewalls at connection points are characteristic of:
Exhibit.
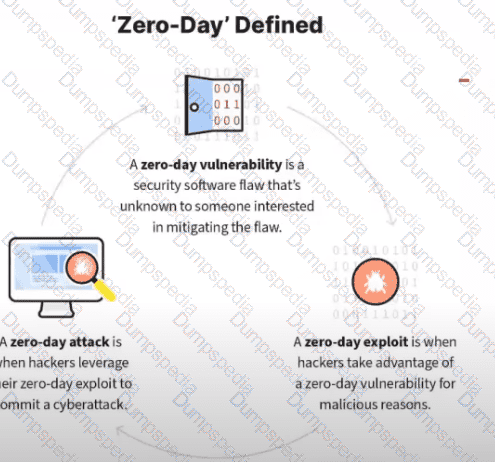
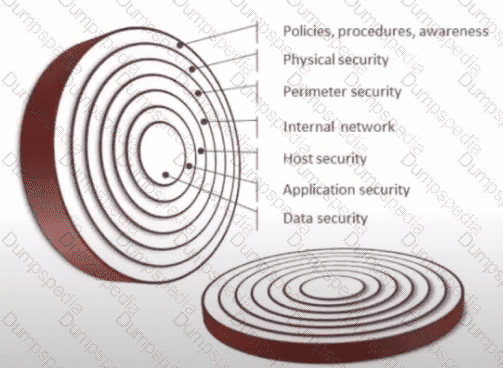
What kind of vulnerability is typically not identifiable through a standard vulnerability assessment?
Which addresses are reserved for internal network use and are not routable on the Internet?
What is the main challenge in achieving non-repudiation in electronic transactions?
Information should be consistently and readily accessible for authorized parties.
An attack in which an attacker listens passively to the authentication protocol to capture information that can be used in a subsequent active attack to masquerade as the claimant is known as:
Which document identifies the principles and rules governing an organization’s protection of information systems and data?
The DevOps team has updated the application source code. Tom discovered that many unauthorized changes have been made. What is the BEST control Tom can implement to prevent a recurrence of this problem?
A company wants to ensure that its employees can evacuate the building in case of an emergency. Which physical control is best suited?
A DLP solution should be deployed so it can inspect all forms of data leaving the organization, including:
Natalia is concerned that users on her network may be storing sensitive information, such as Social Security numbers, on their hard drives without proper authorization or security controls. What third-party security service can she implement to best detect this activity?
The magnitude of harm expected from unauthorized disclosure, modification, destruction, or loss of information is known as:
Which cloud service model provides the most suitable environment for customers to build and operate their own software?
Which attack attempts to gain information by observing a device’s power consumption?
When operating in a cloud environment, which cloud deployment model provides security teams with the greatest access to forensic information?
Which one of the following groups is NOT normally part of an organization's cybersecurity incident response team?
A method for risk analysis that is based on the assignment of a descriptor such as low, medium, or high.
Which approach involves a continuous cycle of identifying, assessing, prioritizing, and mitigating cybersecurity risks?
Often offered by third-party organizations and covering advisory or compliance objectives:
Which security control is designed to prevent unauthorized access to sensitive information by ensuring it is accessible only to authorized users?
What is the difference between Business Continuity Planning (BCP) and Disaster Recovery Planning (DRP)?
Which aspect of cybersecurity is MOST impacted by Distributed Denial of Service (DDoS) attacks?
An attack in which a user authenticated to a server unknowingly invokes unwanted actions after visiting a malicious website is known as:
Natalia wants to ensure the authenticity of her organization’s domain name records using digital signatures. What technology should she use?
Which phase of the access control process (AAA) does a user prove his/her identity?
A one-way spinning door or barrier that allows only one person at a time to enter a building or area.
The amount of risk an organization is willing to accept in pursuit of objectives is called:
Which type of software testing focuses on examining the source code for vulnerabilities and security issues?
Finance Server and Transaction Server have restored their original facility after a disaster. What should be moved in FIRST?
An analysis of system requirements and interdependencies used to prioritize recovery is known as:
An external entity attempts unauthorized access to your IT environment. This is a(n):
Mark’s proposed configuration change must be approved and tested by a Change Control Board. This is an example of:
Duke would like to restrict users from accessing a list of prohibited websites while connected to his network. Which control would BEST achieve his objective?
A company wants to prevent employees from bringing unauthorized electronic devices into the workspace. Which physical control is best?
A company network experiences a sudden flood of network packets that causes major slowdown in Internet traffic. What type of event is this?
A security event in which an intruder gains or attempts unauthorized access to a system is called: