An organization’s security assessment recommended expanding its secure software development framework to include testing Commercial Off-The-Shelf (COTS) products before deploying those products in production. What is the MOST likely reason for this recommendation?
A manufacturing facility uses common wireless technologies to communicate. The head of security is concerned about eavesdropping by attackers outside the perimeter fence. The distance between the facility and fence is at least 300 feet (100 m). Which of the following wireless technologies is MOST likely to be available to an attacker outside the fence?
Which of the following ensures privileges are current and appropriately reflect an individual’s authorized roles and responsibilities?
The primary outcome of frequent replenishments in a distribution requirements planning (DRP) system is that:
Which of the following provides that redundancy and failover capabilities are built into a system to maximize its uptime?
The trade-off of increasing safety stock to improve customer fill rate would be a decrease in:
An information security professional has been tasked with remediating vulnerabilities identified during a recent penetration test. Which of the following sections of the penetration results report would be MOST preferable to remediate hosts one at a time?
A large organization is planning to lay off half of its staff. From an information security point of view, what is the BEST way of approaching affected staff?
Which of the following should be done FIRST when implementing an Identity And Management (IAM) solution?
We have observed the inventory system does not handle plastic parts well." What should be added to the problem statement to make it more useful?
During a threat modeling exercise using the Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege (STRIDE) framework, it was identified that a web server allocates a socket and forks each time it receives a request from a user without limiting the number of connections or requests.
Which of the following security objectives is MOST likely absent in the web server?
Which of the following actions best supports a company's strategic focus on delivery speed to improve competitive advantage?
Under which of the following conditions is excess capacity most likely a good substitute for safety stock?
Which of the following mechanisms should a practitioner focus on for the MOST effective information security continuous monitoring?
For a company that uses first in, first out (FIFO) inventory accounting, the actual use in production of a recently arrived shipment of more expensive components rather than lower-cost components
previously received will have which of the following results?
Which of the following BEST defines whether an organization can consider an alternate location during a contingency?
An executive wants to ensure that risk related to information operations is managed in accordance with the enterprise's risk management thresholds. What is the BEST way to ensure this consistently occurs?
A computer forensic analyst is examining suspected malware from a computer system post-attack. Upon reverse engineering the code, the analyst sees several concerning instructions. One of those concerning instructions is that it installs a Unified Extensible Firmware Interface Basic Input/Output System (BIOS) rootkit, and when the system is then rebooted, the BIOS checks for a certain unknown program to be installed. Which security feature MOST likely would have detected and prevented this type of attack if already on the system?
An organization is preparing to deploy Multi-Factor Authentication (MFA) to its workforce. The primary concerns of the organization are cost and security. The organization realizes that their entire workforce has computers and smartphones. Which of the following is BEST suited to address the organization's concerns?
What is the MOST appropriate action to take when media classification needs to be downgraded to a less sensitive classification?
Following the setting of an organization’s risk appetite by senior management, a risk manager needs to prioritize all identified risks for treatment. Each risk has been scored based on its Annualized Loss Expectancy (ALE). Management has asked for an immediate risk mitigation plan focusing on top risks. Which is the MOST effective approach for the risk manager to quickly present a proposal to management?
To gain entry into a building, individuals are required to use a palm scan. This is an example of which type of control?
A web developer was recently asked to create an organization portal that allows users to retrieve contacts from a popular social media platform using Hypertext Transfer Protocol Secure (HTTPS). Which of the following is BEST suited for authorizing the resource owner to the social media platform?
After reviewing the output of a threat modelling workshop, the development manager decides not to implement the application features where issues were identified. What is the BEST description of how the threats from the workshop are being addressed?
An organization wants to ensure a risk does not occur. The action taken is to eliminate the attack surface by uninstalling vulnerable software. Which risk response strategy did the organization take?
A company can easily change Its workforce, but inventory carrying costs are high. Which of the following strategies would be most appropriate during times of highly fluctuating demand?
A large retail organization will be creating new Application Programming Interfaces (API) as part of a customer-facing shopping solution. The solution will accept information from users both inside and outside of the organization. What is the safest software development practice the team can follow to protect the APIs against Structured Query Language Injection (SQLi) attacks?
Which of the following planes directs the flow of data within a Software-Defined Networking (SDN) architecture?
Which of the following production activity control (PAC) techniques focuses on optimizing output?
An organization wants to ensure the security of communications across its environment. What is the BEST way to provide confidentiality of data from handheld wireless devices to the internal network?
Which of the following is a document that will be obtained at the end of an asset’s lifecycle?
A security practitioner has been asked to investigate the presence of customer Personally Identifiable Information (PII) on a social media website. Where does the practitioner begin?
Capacity requirements planning (CRP) is applicable primarily In companies operating In an environment where:
A security engineer must address resource sharing between various applications without adding physical hardware to the environment. Which secure design principle is used to BEST segregate applications?
Why would a network administrator monitor Internet of Things (IoT) security differently than the security of standards network devices?
What is the FIRST element that must be evaluated in a security governance program?
Price negotiation is most appropriate when purchasing which of the following product categories?
Which of the following strategies is most appropriate for a business unit with a low relative market share in a high-growth market?
What is a strategic process that is aimed at considering possible attack scenarios and vulnerabilities within a proposed or existing application environment for the purpose of clearly identifying risk and impact levels?
Which of the common vulnerabilities below can be mitigated by using indexes rather than actual portions of file names?
If organizational leadership determines that its required continuous monitoring plan is too costly for the organization, what action should be taken by leadership and the Authorizing Official (AO)?
An organization requires all passwords to include two uppercase characters, two numbers, and two special characters. After a security professional has successfully retrieved the hashed password file from a server, what would be the fastest attack to conduct on the file?
A cybersecurity professional has been tasked with instituting a risk management function at a new organization. Which of the following is the MOST important step the professional should take in this endeavor?
Endpoint security needs to be established after an organization procured 1,000 industrial Internet Of Things (IoT) sensors. Which of the following challenges are the security engineers MOST likely to face?
An organization's penetration test engineer noticed that traffic is being modified between 2 nodes and suspects an eavesdropping attack. On which networking plane is this attack occurring?
In preparing for a facility location decision, proximity to suppliers would be classified as which kind of criteria?
Substituting capital equipment in place of direct labor can be economically Justified for which of the following scenarios?
Which of the following methods would be appropriate for forecasting the demand for a product family when there is a significant trend and seasonality in the demand history?
A company decided not to pursue a business opportunity In a foreign market due to political Instability and currency fluctuations. Which risk control strategy did this business utilize?
An organization is restructuring its network architecture in which system administrators from the corporate office need to be able to connect to the branch office to perform various system maintenance activities. What network architecture would be MOST secure?
In which of the following circumstances is an organization MOST likely to report the accidental release of personal data to the European Union (EU) General Data Protection Regulation (GDPR) supervisory authority and affected users?
An organization has received the results of their network security risk assessment. What is the BEST course of action for the organization to take in response to the analyzed report findings?
Which security concept applies if an architecture diagram illustrates a particular user/role combination with access to an asset or applicaton?
An organization wants to control access at a high-traffic entrance using magnetic-stripe cards for identification. Which of the following is the BEST for the organization to utilize?
A part is sold as a service part, and It is also used as a component In another part. Which of the following statements about the planning for this part is true?
A company uses planning bills of material (BOMs) in its planning process extensively. Which of the following scenarios would present the biggest challenge to this planning process?
Which of the following roles is the BEST choice for classifying sensitive data?
In restoring the entire corporate email system after a major outage and data loss, an email administrator reads a few email message exchanges between the human resources manager and a candidate for an open position. Which of the following BEST describes the behavior of the email administrator, and why?
Which of the following states of data becomes MOST important to protect as organizations continue to transition toward Application Programming Interface (API)-based solutions?
A security engineer developing software for a professional services organization has a requirement that users cannot have concurrent access to data of clients that are competitors. Which security model should the security engineer implement to meet this requirement?
Which of the following statements is an assumption on which the economic order quantity (EOQ) model is based?
The time spent In queue by a specific manufacturing job is determined by which of the following factors related to the order?
During the initiation phase of a project to acquire a customer relation management system, what is the FIRST step a project team will take for early integration of security?
An organization has a requirement that all documents must be auditable and that the original is never modified once created. When designing the system, what security model MUST be implemented in order to meet this requirement?
A cybersecurity analyst is reviewing a recent incident in which the adversaries were able to move vertically within the network. Which attack phase MOST clearly represents this scenario?
An organization wishes to utilize a managed Domain Name System (DNS) provider to reduce the risk of users accessing known malicious sites when web browsing. The organization operates DNS forwarders that forward queries for all external domains to the DNS provider. Which of the following techniques could enable the organization to identify client systems that have attempted to access known malicious domains?
Which of the following BEST characterizes the operational benefit of using immutable workloads when working on a cloud-based project?
Which specification enables organizations to ensure penetration test results are documented using open, machine-readable standards?
A security practitioner notices that workforce members retain access to information systems after transferring to new roles within the organization, which could lead to unauthorized changes to the information systems.
This is a direct violation of which common security model?
The primary reason for tracing a component with scheduling problems to Its master production schedule (MPS) item is to:
When resolving conflicts, which canon within the ISC2 Code of Ethics requires members to consider duties to principals and Individuals?
An executive is approved to travel to a high-risk country. What is the BEST action the organization can take to ensure the executive’s safety and security?
The cost accountant has discovered a consistent overage in actual run time for one operation. This information should be sent first to the:
A logistics manager Is faced with delivering an order via rail or truck. Shipping via rail costs S300 and takes 14 days. Shipping via truck costs $600 and takes 3 days. If the holding cost is $40 per day, what is the cost to deliver the order?
Which of the following is the MOST effective approach to reduce the threat of rogue devices being introduced to the internal network?
A company confirms a customer order based on available capacity and inventory, even though the current production plan does not cover the entire order quantity. This situation is an example of what type of order fulfillment policy?
Which of the following is the BEST option for a security director to use in order to mitigate the risk of inappropriate use of credentials by individuals with administrative rights?
Bad actors with little expense can easily make calls. Which social engineer strategy is a telecommunications ONLY risk concept?
Which of the following is the GREATEST threat for a Border Gateway Protocol (BGP) deployment on the internet?
An organization’s external auditors have issued a management letter identifying significant deficiencies related to the effectiveness of the previous year’s global access certification. The organization wants to move from a department-based access control system to a Role-Based Access Control (RBAC) system. In addition to quickly and securely provisioning users by granting membership into predefined and approved roles, which of these presents the BEST reason to do so?
Which approach will BEST mitigate risks associated with root user access while maintaining system functionality?
An independent risk assessment determined that a hospital's existing policies did not have a formal process in place to address system misuse, abuse, or fraudulent activity by internal users. Which of the following would BEST address this deficiency in the Corrective Action Plan?
A lengthy power outage led to unavailability of time critical services resulting in considerable losses. It was determined that a backup electrical generator did not work as intended at the time of the incident due to lack of fuel. What should the security consultant FIRST Investigate?
Which of the following environments is most suitable for the use of kanban systems?
Which of the below represent the GREATEST cloud-specific policy and organizational risk?
An organization is attempting to address the security risk introduced by employees writing down door entry passcodes. Which of the following security measures BEST mitigates this risk?
An organization recently created a new accounting department, and that department is critical in the event of a disaster for the operations to continue. Which steps should the organization take to create a Business Continuity Plan (BCP)?
An external audit is conducted on an organization's cloud Information Technology (IT) infrastructure. This organization has been using cloud IT services for several years, but its use is not regulated in any way by the organization and security audits have never been conducted in the past. Which task will be the MOST challenging to conduct an effective security audit?
Which of the following statements is an advantage of a fourth-party logistics (4PL) provider?
During a security incident investigation, a security analyst discovered an unauthorized module was compiled into an application package as part of the application assembly phase. This incident occurred immediately prior to being digitally signed and deployed using a deployment pipeline.
Which of the following security controls would BEST prevent this type of incident in the future?
A firm that currently produces all items to stock is implementing the concept of postponement in all new product designs. Which of the following outcomes is most likely to result?
While doing a penetration test, auditors found an old credential hash for a privileged user. To prevent a privileged user's hash from being cached, what is the MOST appropriate policy to mandate?
Employees at an organization use web based services provided by an affiliate. Which of the following risks is unique to this situation?
What is the BEST reason to include a Hardware Security Module (HSM) in the key management system when securing cloud storage?
According to best practice, at which step in the system lifecycle shall a security professional begin involvement?
In a make-to-stock (MTS) environment, the master production schedule (MPS) Is usually a schedule of which of the following types of items?
The horizon for forecasts that are input to the sales and operations planning (S&OP) process should be long enough that:
Which of the following procedures should be defined when establishing information and asset handling requirements?
A company’s Marketing and Sales departments have identified an opportunity to develop a new market for a product family and requested an increase in the production plan. Which of the following actions would be most appropriate to account for the new market opportunity?
Which of the following BEST effective when protecting against insider threats?
What is the MAIN reason security is considered as part of the system design phase instead of deferring to later phases?
A security officer has been tasked with performing security assessments on the organization’s in the current calendar year. While collecting data, the officer realizes that more than one business until will be engaged in the assessment. What activity MUST be included in the data collection phase?
An advantage of applying ABC classification to a firm's replenishment items is that:
When a third-party needs to receive privileged information, which of the following would be the BEST to
transport the data?
Which of the following should recommendations from a Plan Of Action And Milestones (POA&M) be based on?
An organization has implemented a control that requires users to change their passwords every 30 days. Which setting of the password policy will prevent users from reusing passwords?
A hot Disaster Recovery (DR) data center is the victim of a data breach. The hackers are able to access and copy 10GB of clear text confidential information. Which of the following could have decreased the amount of exposure from this data breach?
A security professional is accessing an organization-issued laptop using biometrics to remotely log into a network resource. Which type of authentication method is described in this scenario?
An organization intends to host an application on a multi-tenant Infrastructure as a Service (IaaS) platform. Which of the following measures are MOST important to ensure proper protection of sensitive information?
An information system security manager is tasked with properly applying risk management principle to their cloud information system as outlined by the National Institute of Standards and Technology (NIST).
Which of the following is the INITIAL step?
Which of the following design considerations would offer the BEST protection against unauthorized access to the facility?
In the sales and operations planning (S&OP) process, the demand management function provides:
Which of the physiological biometric scanning methods is considered the MOST invasive?
Exhibit:
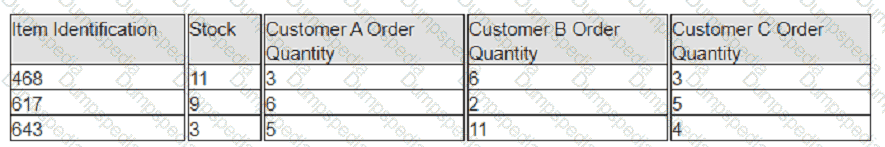
A company has prioritized customers A, B, and C, filling orders in that sequence. What are the impacts to customer service levels for customers B and C?
An information security auditor is creating an audit program to assess endpoint security controls for portable storage media movement. Which type of control will MOST likely be part of the program?
Which protocol is the BEST option to provide authentication, confidentiality, and data integrity between two applications?
Improvements in an Input/output control (I/O control) system will most likely lead to:
Company A has acquired Company B. Company A has decided to start a project to convert Company B's enterprise resource planning (ERP) software to the same ERP software that Company A uses. What is a likely reason for this decision?
Which of the following concepts MOST accurately refers to an organization's ability to fully understand the health of the data in its system at every stage of the lifecycle?
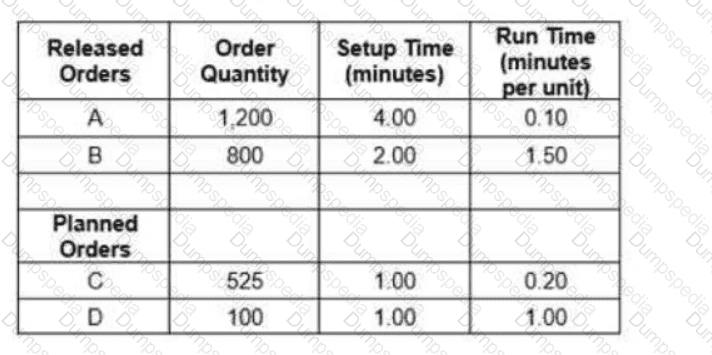
What is the total load requirement for this work center based on the following data?
Which of the following security techniques can be used to ensure the integrity of software as well as determine who developed the software?
A security analyst has been asked to build a data retention policy for a hospital. What is the FIRST action that needs to be performed in building this policy?
An information security professional is enhancing the organization's existing information security awareness program through educational posters. Which of the following is the MOST effective location for poster placement?
To mitigate risk related to natural disasters, an organization has a separate location with systems and communications in place. Data must be restored on the remote systems before they are ready for use. What type of remote site is this?
Which of the following situations is most likely to occur when using a push system?
An organization has identified that an individual has failed to adhere to a given standard set by the organization. Based on the needs of the organization, it was decided that an exception process will be created. What is the PRIMARY benefit of establishing an exception process?
Which burden of proof has been applied when a workplace investigation has a 51 percent or greater certainty that allegations are true?
Which of the following is the workflow of the identity and access provisioning lifecycle?
An Information Technology (IT) professional is seeking a control objective framework that is widely accepted around the world and focuses specifically on information security controls. Which of the following frameworks BEST meets this need?
Which of the following product design approaches are likely to reduce time to market for a global supply chain?
In conducting a new corporate payroll system security review, which of the following individuals should answer questions regarding the data classification?
Which of the following security features is utilized to validate both user credentials and the health of the client device on a network?
An organization has been struggling to improve their security posture after a recent breach.
Where should the organization focus their efforts?
An organization undergoing acquisition merged IT departments and infrastructure. During server decommissioning, some servers still in use by customers were mistakenly removed, causing order processing failures. Which type of review would have BEST avoided this scenario?
An audit of antivirus server reports shows a number of workstations do not have current signatures installed. The organization security standard requires all systems to have current antivirus signatures. What distinct part of the audit finding did the auditor fail to include?
Cloud computing introduces the concept of the shared responsibility model. This model can MOST accurately be described as defining shared responsibility between which of the following?
A traffic analysis on an organization's network identifies a significant degree of inefficient resource use as a result of broadcast traffic. The organization wants to reduce the scope of the broadcasts without impeding the flow of traffic. Which of the following devices is the BEST choice to implement to achieve this goal?
Which of the following is the BEST activity to mitigate risk from ransomware on mobile devices and removable media in a corporate environment?
Which of the following is a core subset of The Open Group Architecture Framework (TOGAF) enterprise architecture model?
Which of the following statements correctly describes the relationship between the strategic plan and the business plan?
Before securing a email system using OpenPGP in an organization, Which of the following actions MUST be performed?
What General Data Protection Regulation (GDPR) principle says that data should be collected lawfully and with the person’s consent?
Which assessing whether real-world threats to the security of an application have been mitigated, what is MOST effective source to confirm that sufficient security controls are in place for both end users and customers?
Which of the following stock location systems would you use in a repetitive manufacturing, lean environment?
Following the go-live of a new financial software, an organization allowed the Information Technology (IT) officer to maintain all rights and access permissions to help the organization staff should they have challenges in their day-to-day work. What is the BEST way to categorize the situation?
An organization has deployed an Identity And Access Management (IAM) tool and is expanding their information governance program. Which of the following would BEST be included in the governance for IAM?
Which of the following is the MAIN element in achieving a successful security strategy?
A third-party vendor is procured to conduct a non-financial audit. Which report evaluates the effectiveness of the controls?