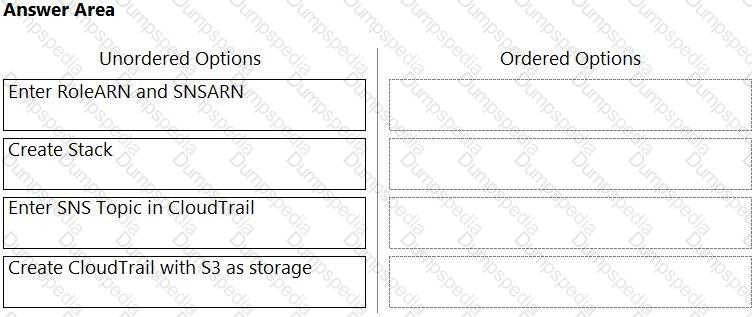
Order the steps involved in onboarding an AWS Account for use with Data Security feature.
You are tasked with configuring a Prisma Cloud build policy for Terraform. What type of query is necessary to complete this policy?
Which resource and policy type are used to calculate AWS Net Effective Permissions? (Choose two.)
A Prisma Cloud Administrator onboarded an AWS cloud account with agentless scanning enabled successfully to Prisma Cloud. Which item requires deploying defenders to be able to inspect the risk on the onboarded AWS account?
In Azure, what permissions need to be added to Management Groups to allow Prisma Cloud to calculate net effective permissions?
A customer wants to harden its environment from misconfiguration.
Prisma Cloud Compute Compliance enforcement for hosts covers which three options? (Choose three.)
A manager informs the SOC that one or more RDS instances have been compromised and the SOC needs to make sure production RDS instances are NOT publicly accessible.
Which action should the SOC take to follow security best practices?
During an initial deployment of Prisma Cloud Compute, the customer sees vulnerabilities in their environment.
Which statement correctly describes the default vulnerability policy?
Prisma Cloud supports which three external systems that allow the import of vulnerabilities and provide additional context on risks in the cloud? (Choose three.)
What is the most reliable and extensive source for documentation on Prisma Cloud APIs?
Which two options may be used to upgrade the Defenders with a Console v20.04 and Kubernetes deployment? (Choose two.)
Which two statements explain differences between build and run config policies? (Choose two.)
Which three serverless runtimes are supported by Prisma Cloud for vulnerability and compliance scans? (Choose three.)
An administrator needs to detect and alert on any activities performed by a root account.
Which policy type should be used?
Which three incident types will be reflected in the Incident Explorer section of Runtime Defense? (Choose three.)
Which policy type should be used to detect and alert on cryptominer network activity?
Per security requirements, an administrator needs to provide a list of people who are receiving e-mails for Prisma Cloud alerts.
Where can the administrator locate this list of e-mail recipients?
Which action would be applicable after enabling anomalous compute provisioning?
Which two processes ensure that builds can function after a Console upgrade? (Choose two.)
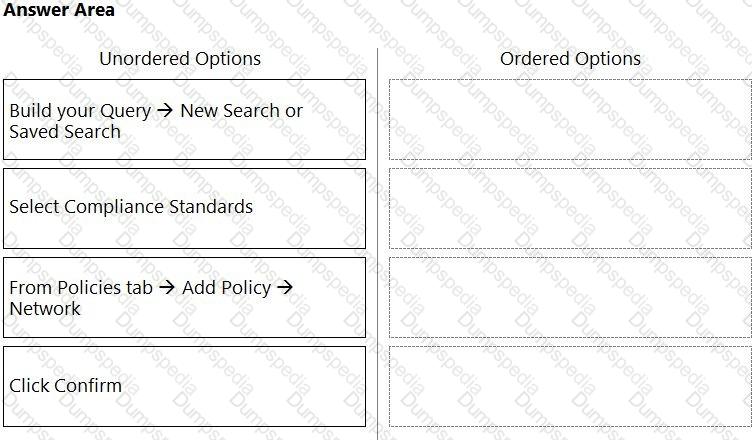
The Prisma Cloud administrator has configured a new policy.
Which steps should be used to assign this policy to a compliance standard?
Which three options are selectable in a CI policy for image scanning with Jenkins or twistcli? (Choose three.)
A Prisma Cloud administrator is onboarding a single GCP project to Prisma Cloud. Which two steps can be performed by the Terraform script? (Choose two.)
A customer has Prisma Cloud Enterprise and host Defenders deployed.
What are two options that allow an administrator to upgrade Defenders? (Choose two.)
Which two statements are true about the differences between build and run config policies? (Choose two.)
Based on the following information, which RQL query will satisfy the requirement to identify VM hosts deployed to organization public cloud environments exposed to network traffic from the internet and affected by Text4Shell RCE (CVE-2022-42889) vulnerability?
• Network flow logs from all virtual private cloud (VPC) subnets are ingested to the Prisma Cloud Enterprise Edition tenant.
• All virtual machines (VMs) have Prisma Cloud Defender deployed.
A)
B)
C)
D)
Which of the below actions would indicate – “The timestamp on the compliance dashboard?
Which three options for hardening a customer environment against misconfiguration are included in Prisma Cloud Compute compliance enforcement for hosts? (Choose three.)
Which two bot categories belong to unknown bots under Web-Application and API Security (WAAS) bot protection? (Choose two.)
A DevOps lead reviewed some system logs and notices some odd behavior that could be a data exfiltration attempt. The DevOps lead only has access to vulnerability data in Prisma Cloud Compute, so the DevOps lead passes this information to SecOps.
Which pages in Prisma Cloud Compute can the SecOps lead use to investigate the runtime aspects of this attack?
Which ban for DoS protection will enforce a rate limit for users who are unable to post five (5) “. tar.gz" files within five (5) seconds?
Which three OWASP protections are part of Prisma Cloud Web-Application and API Security (WAAS) rule? (Choose three.)
What is an automatically correlated set of individual events generated by the firewall and runtime sensors to identify unfolding attacks?
Which policy type provides information about connections from suspicious IPs in a customer database?
How does assigning an account group to an administrative user on Prisma Cloud help restrict access to resources?
The development team wants to fail CI jobs where a specific CVE is contained within the image. How should the development team configure the pipeline or policy to produce this outcome?
What improves product operationalization by adding visibility into feature utilization and missed opportunities?
An administrator has added a Cloud account on Prisma Cloud and then deleted it.
What will happen if the deleted account is added back on Prisma Cloud within a 24-hour period?
Which serverless cloud provider is covered by the "overly permissive service access" compliance check?
A customer has a requirement to restrict any container from resolving the name www.evil-url.com.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
The compliance team needs to associate Prisma Cloud policies with compliance frameworks. Which option should the team select to perform this task?
What factor is not used in calculating the net effective permissions for a resource in AWS?
The Compute Console has recently been upgraded, and the administrator plans to delay upgrading the Defenders and the Twistcli tool until some of the team’s resources have been rescaled. The Console is currently one major release ahead.
What will happen as a result of the Console upgrade?
Which two frequency options are available to create a compliance report within the console? (Choose two.)
Given the following audit event activity snippet:
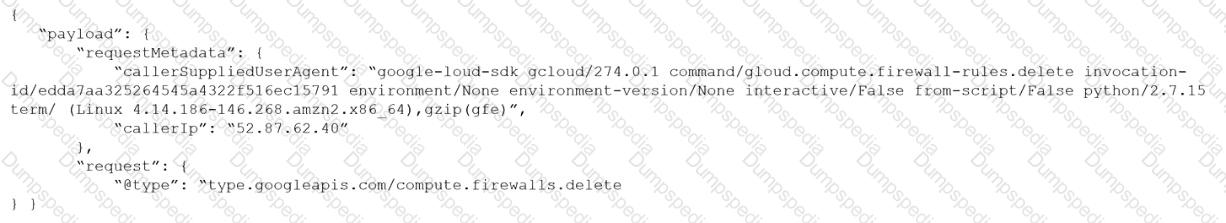
Which RQL will be triggered by the audit event?
A)
B)
C)
D)
A customer has multiple violations in the environment including:
User namespace is enabled
An LDAP server is enabled
SSH root is enabled
Which section of Console should the administrator use to review these findings?
You are an existing customer of Prisma Cloud Enterprise. You want to onboard a public cloud account and immediately see all of the alerts associated with this account based off ALL of your tenant’s existing enabled policies. There is no requirement to send alerts from this account to a downstream application at this time.
Which option shows the steps required during the alert rule creation process to achieve this objective?
What is the order of steps to create a custom network policy?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
A business unit has acquired a company that has a very large AWS account footprint. The plan is to immediately start onboarding the new company’s AWS accounts into Prisma Cloud Enterprise tenant immediately. The current company is currently not using AWS Organizations and will require each account to be onboarded individually.
The business unit has decided to cover the scope of this action and determined that a script should be written to onboard each of these accounts with general settings to gain immediate posture visibility across the accounts.
Which API endpoint will specifically add these accounts into the Prisma Cloud Enterprise tenant?
A Prisma Cloud Administrator needs to enable a Registry Scanning for a registry that stores Windows images. Which of the following statement is correct regarding this process?
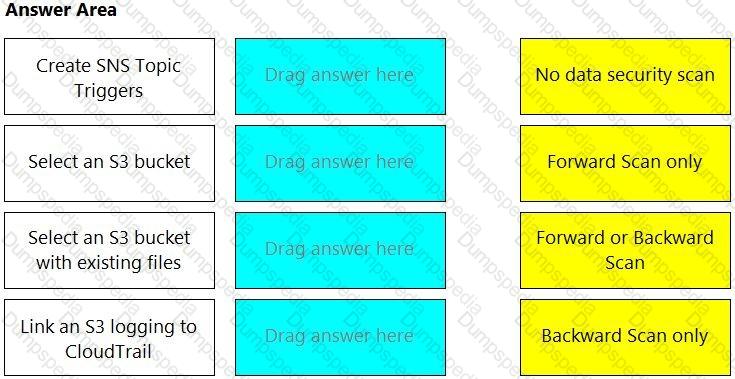
Match the correct scanning mode for each given operation.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
What are two key requirements for integrating Okta with Prisma Cloud when multiple Amazon Web Services (AWS) cloud accounts are being used? (Choose two.)
Which file extension type is supported for Malware scanning in Prisma Cloud Data Security (PCDS)?
Which resources can be added in scope while creating a vulnerability policy for continuous integration?
On which cloud service providers can new API release information for Prisma Cloud be received?
In which Console menu would an administrator verify whether a custom compliance check is failing or passing?