An alert has been distributed throughout the information security community regarding a critical Apache vulnerability. Which of the following courses of action would ONLY identify the known vulnerability?
Several users have reported that when attempting to save documents in team folders, the following message is received:
The File Cannot Be Copied or Moved – Service Unavailable.
Upon further investigation, it is found that the syslog server is not obtaining log events from the file server to which the users are attempting to copy files. Which of the following is the MOST likely scenario causing these issues?
Which of the following is a control that allows a mobile application to access and manipulate information which should only be available by another application on the same mobile device (e.g. a music application posting the name of the current song playing on the device on a social media site)?
During a routine review of firewall logs, an analyst identified that an IP address from the organization’s server subnet had been connecting during nighttime hours to a foreign IP address, and had been sending between 150 and 500 megabytes of data each time. This had been going on for approximately one week, and the affected server was taken offline for forensic review. Which of the following is MOST likely to drive up the incident’s impact assessment?
A technician receives a report that a user’s workstation is experiencing no network connectivity. The technician investigates and notices the patch cable running the back of the user’s VoIP phone is routed directly under the rolling chair and has been smashed flat over time.
Which of the following is the most likely cause of this issue?
Law enforcement has contacted a corporation’s legal counsel because correlated data from a breach shows the organization as the common denominator from all indicators of compromise. An employee overhears the conversation between legal counsel and law enforcement, and then posts a comment about it on social media. The media then starts contacting other employees about the breach. Which of the following steps should be taken to prevent further disclosure of information about the breach?
An analyst has initiated an assessment of an organization’s security posture. As a part of this review, the analyst would like to determine how much information about the organization is exposed externally. Which of the following techniques would BEST help the analyst accomplish this goal? (Select two.)
Company A permits visiting business partners from Company B to utilize Ethernet ports available in Company A’s conference rooms. This access is provided to allow partners the ability to establish VPNs back to Company B’s network. The security architect for Company A wants to ensure partners from Company B are able to gain direct Internet access from available ports only, while Company A employees can gain access to the Company A internal network from those same ports. Which of the following can be employed to allow this?
After running a packet analyzer on the network, a security analyst has noticed the following output:
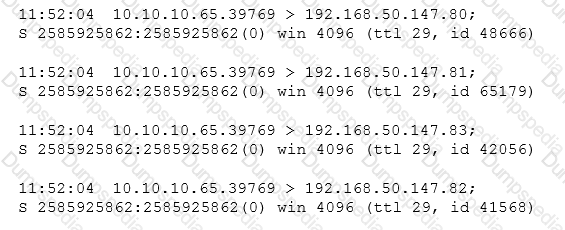
Which of the following is occurring?
A cybersecurity analyst is completing an organization’s vulnerability report and wants it to reflect assets accurately. Which of the following items should be in the report?
A company has recently launched a new billing invoice website for a few key vendors. The cybersecurity analyst is receiving calls that the website is performing slowly and the pages sometimes time out. The analyst notices the website is receiving millions of requests, causing the service to become unavailable. Which of the following can be implemented to maintain the availability of the website?
A cybersecurity analyst has been asked to follow a corporate process that will be used to manage vulnerabilities for an organization. The analyst notices the policy has not been updated in three years. Which of the following should the analyst check to ensure the policy is still accurate?
Which of the following best practices is used to identify areas in the network that may be vulnerable to penetration testing from known external sources?
Which of the following items represents a document that includes detailed information on when an incident was detected, how impactful the incident was, and how it was remediated, in addition to incident response effectiveness and any identified gaps needing improvement?
Using a heuristic system to detect an anomaly in a computer’s baseline, a system administrator was able to detect an attack even though the company signature based IDS and antivirus did not detect it. Further analysis revealed that the attacker had downloaded an executable file onto the company PC from the USB port, and executed it to trigger a privilege escalation flaw. Which of the following attacks has MOST likely occurred?
Which of the following is MOST effective for correlation analysis by log for threat management?
Management is concerned with administrator access from outside the network to a key server in the company. Specifically, firewall rules allow access to the server from anywhere in the company. Which of the following would be an effective solution?
Creating a lessons learned report following an incident will help an analyst to communicate which of the following information? (Select TWO)
Which of the following represent the reasoning behind careful selection of the timelines and time-of-day boundaries for an authorized penetration test? (Select TWO).
The Chief Executive Officer (CEO) instructed the new Chief Information Security Officer (CISO) to provide a list of enhancement to the company’s cybersecurity operation. As a result, the CISO has identified the need to align security operations with industry best practices. Which of the following industry references is appropriate to accomplish this?
A software development company in the manufacturing sector has just completed the alpha version of its flagship application. The application has been under development for the past three years. The SOC has seen intrusion attempts made by indicators associated with a particular APT. The company has a hot site location for COOP. Which of the following threats would most likely incur the BIGGEST economic impact for the company?
A technician receives the following security alert from the firewall’s automated system:
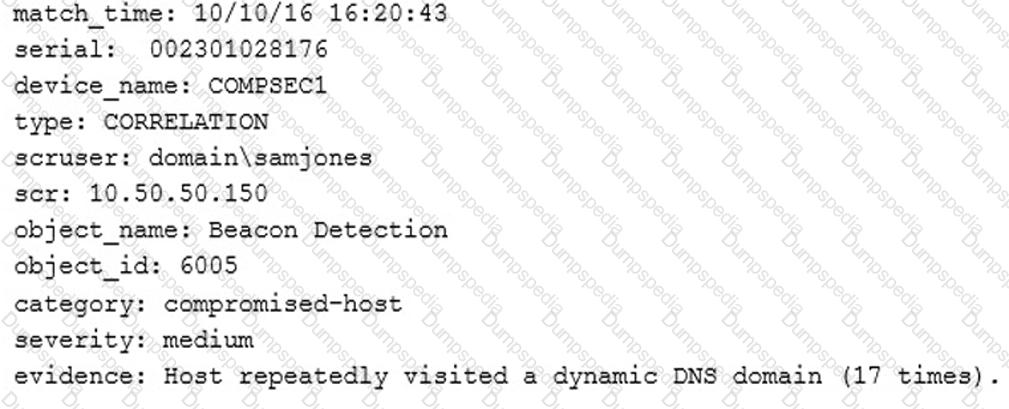
After reviewing the alert, which of the following is the BEST analysis?
After a recent security breach, it was discovered that a developer had promoted code that had been written to the production environment as a hotfix to resolve a user navigation issue that was causing issues for several customers. The code had inadvertently granted administrative privileges to all users, allowing inappropriate access to sensitive data and reports. Which of the following could have prevented this code from being released into the production environment?
A company has been a victim of multiple volumetric DoS attacks. Packet analysis of the offending traffic shows the following:

Which of the following mitigation techniques is MOST effective against the above attack?
Which of the following is a vulnerability when using Windows as a host OS for virtual machines?
Which of the following stakeholders would need to be aware of an e-discovery notice received by the security office about an ongoing case within the manufacturing department?
A security analyst performs various types of vulnerability scans.
Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
Instructions:
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
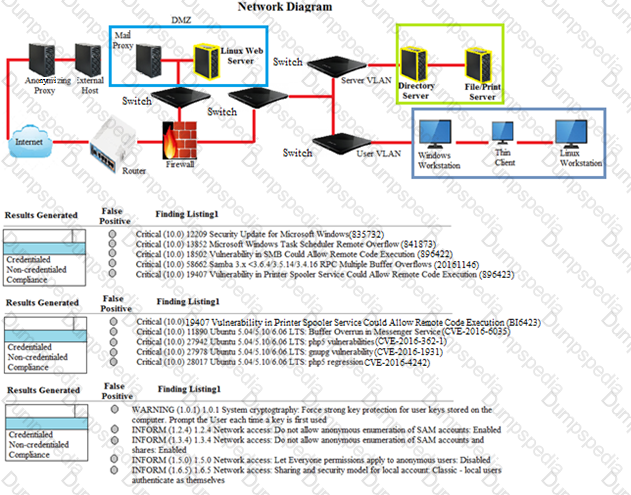
A security analyst is attempting to configure a vulnerability scan for a new segment on the network. Given the requirement to prevent credentials from traversing the network while still conducting a credentialed scan, which of the following is the BEST choice?
A pharmacy gives its clients online access to their records and the ability to review bills and make payments. A new SSL vulnerability on a special platform was discovered, allowing an attacker to capture the data between the end user and the web server providing these services. After investigating the platform vulnerability, it was determined that the web services provided are being impacted by this new threat.
Which of the following data types are MOST likely at risk of exposure based on this new threat? (Choose two.)
During a review of security controls, an analyst was able to connect to an external, unsecured FTP server from a workstation. The analyst was troubleshooting and reviewed the ACLs of the segment firewall the workstation is connected to:
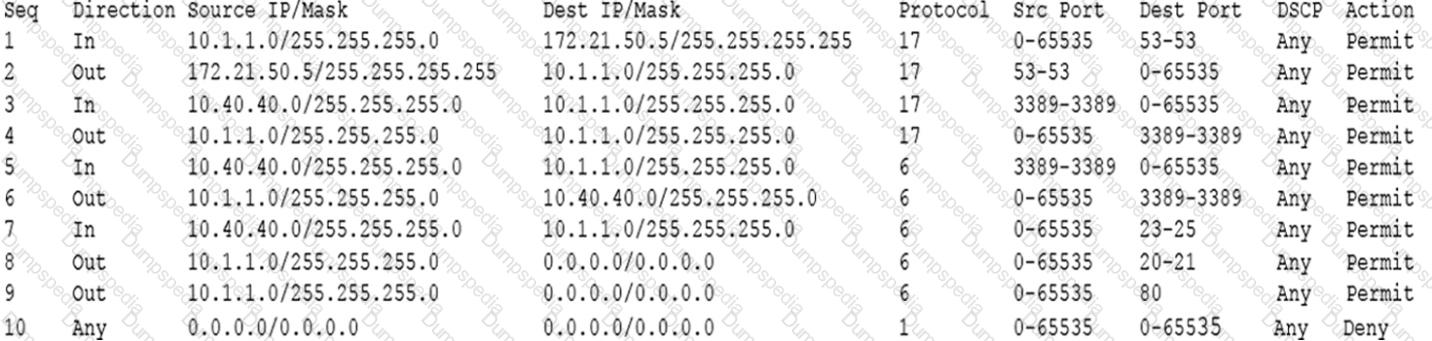
Based on the ACLs above, which of the following explains why the analyst was able to connect to the FTP server?
There have been several exploits to critical devices within the network. However, there is currently no process to perform vulnerability analysis.
Which of the following should the security analyst implement during production hours to identify critical threats and vulnerabilities?
A penetration tester is preparing for an audit of critical systems that may impact the security of the environment. This includes the external perimeter and the internal perimeter of the environment. During which of the following processes is this type of information normally gathered?
Scan results identify critical Apache vulnerabilities on a company’s web servers. A security analyst believes many of these results are false positives because the web environment mostly consists of Windows servers.
Which of the following is the BEST method of verifying the scan results?
The business has been informed of a suspected breach of customer data. The internal audit team, in conjunction with the legal department, has begun working with the cybersecurity team to validate the report. To which of the following response processes should the business adhere during the investigation?
A SIEM analyst noticed a spike in activities from the guest wireless network to several electronic health record (EHR) systems. After further analysis, the analyst discovered that a large volume of data has been uploaded to a cloud provider in the last six months. Which of the following actions should the analyst do FIRST?
During which of the following NIST risk management framework steps would an information system security engineer identify inherited security controls and tailor those controls to the system?
Which of the following countermeasures should the security administrator apply to MOST effectively mitigate Bootkit-level infections of the organization's workstation devices?
The Chief Information Security Officer (CISO) has asked the security staff to identify a framework on which to base the security program. The CISO would like to achieve a certification showing the security program meets all required best practices. Which of the following would be the BEST choice?
Nmap scan results on a set of IP addresses returned one or more lines beginning with “cpe:/o:” followed by a company name, product name, and version. Which of the following would this string help an administrator to identify?
Three similar production servers underwent a vulnerability scan. The scan results revealed that the three servers had two different vulnerabilities rated “Critical”.
The administrator observed the following about the three servers:
Which of the following assessments is valid and what is the most appropriate NEXT step? (Select TWO).
A nuclear facility manager determined the need to monitor utilization of water within the facility. A startup company just announced a state-of-the-art solution to address the need for integrating the business and ICS network. The solution requires a very small agent to be installed on the ICS equipment. Which of the following is the MOST important security control for the manager to invest in to protect the facility?
A security analyst begins to notice the CPU utilization from a sinkhole has begun to spike. Which of the following describes what may be occurring?
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has already identified active hosts in the network and is now scanning individual hosts to determine if any are running a web server. The output from the latest scan is shown below:
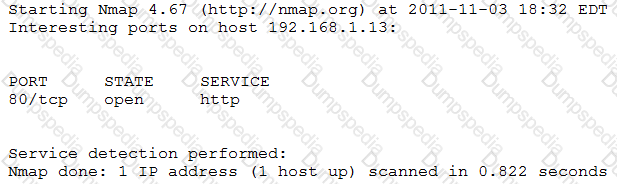
Which of the following commands would have generated the output above?
The software development team pushed a new web application into production for the accounting department. Shortly after the application was published, the head of the accounting department informed IT operations that the application was not performing as intended. Which of the following SDLC best practices was missed?
A security analyst must perform quarterly vulnerability scans to keep the organization In compliance with PCI regulations. The analyst has scheduled the scans to occur early on Monday mornings and uses Nexpose on 192.168.65.32 to run scans on the entire network. The morning after the scan was run. the analyst received the following alert from the network-based IDS system:
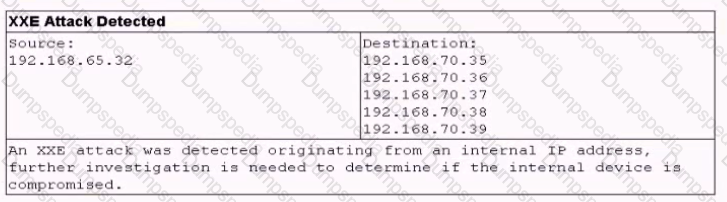
Which of the following would be the BEST way to address this alert while remaining in compliance with PCI regulations?
A manufacturing company has decided to participate in direct sales of its products to consumers. The company decides to use a subdomain of its main site with its existing cloud service provider as the portal for e-commerce. After launch, the site is stable and functions properly, but after a robust day of sales, the site begins to redirect to a competitor’s landing page. Which of the following actions should the company’s security team take to determine the cause of the issue and minimize the scope of impact?
Which of the following is a security concern found PRIMARILY in virtual infrastructure?
The development team currently consists of three developers who each specialize in a specific programming language:
Developer 1 – C++/C#
Developer 2 – Python
Developer 3 – Assembly
Which of the following SDLC best practices would be challenging to implement with the current available staff?
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has received the following output from the latest scan:
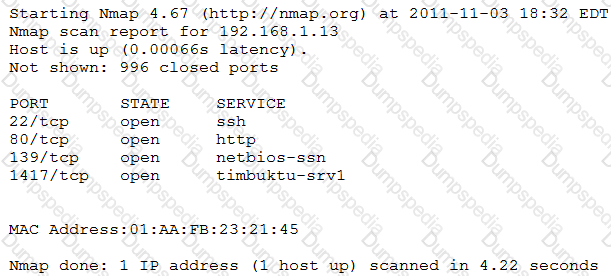
The penetration tester knows the organization does not use Timbuktu servers and wants to have Nmap interrogate the ports on the target in more detail. Which of the following commands should the penetration tester use NEXT?
A SIEM alert occurs with the following output:
Which of the following BEST describes this alert?
The following IDS log was discovered by a company’s cybersecurity analyst:

Which of the following was launched against the company based on the IDS log?
During an investigation, a computer is being seized. Which of the following is the FIRST step the analyst should take?
Now regulations have come out that require a company to conduct regular vulnerability scans. Not wanting to be found with a vulnerability during an audit, the company wants the most accurate and complete vulnerability scan. Which of the following BEST meets this objective?
In order to the leverage the power of data correlation with Nessus, a cybersecurity analyst must first be able to create a table for the scan results.
Given the following snippet of code:

Which of the following output items would be correct?
Risk management wants IT to implement a solution that will permit an analyst to intercept, execute, and analyze potentially malicious files that are downloaded from the Internet.
Which of the following would BEST provide this solution?
A corporation employs a number of small-form-factor workstations and mobile devices, and an incident response team is therefore required to build a forensics kit with tools to support chip-off analysis. Which of the following tools would BEST meet this requirement?
A computer at a company was used to commit a crime. The system was seized and removed for further analysis. Which of the following is the purpose of labeling cables and connections when seizing the computer system?
A security administrator has uncovered a covert channel used to exfiltrate confidential data from an internal database server through a compromised corporate web server. Ongoing exfiltration is accomplished by embedding a small amount of data extracted from the database into the metadata of images served by the web server. File timestamps suggest that the server was initially compromised six months ago using a common server misconfiguration. Which of the following BEST describes the type of threat being used?
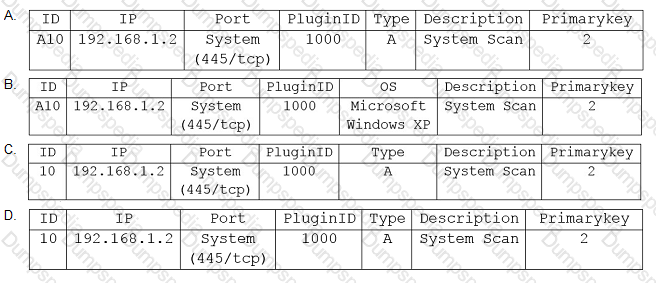
A security analyst is preparing for the company’s upcoming audit. Upon review of the company’s latest vulnerability scan, the security analyst finds the following open issues:
Which of the following vulnerabilities should be prioritized for remediation FIRST?
A security administrator uses FTK to take an image of a hard drive that is under investigation. Which of the following processes are used to ensure the image is the same as the original disk? (Choose two.)
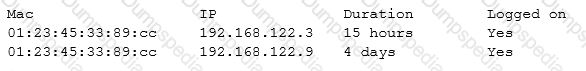
An organization has recently found some of its sensitive information posted to a social media site. An investigation has identified large volumes of data leaving the network with the source traced back to host 192.168.1.13. An analyst performed a targeted Nmap scan of this host with the results shown below:
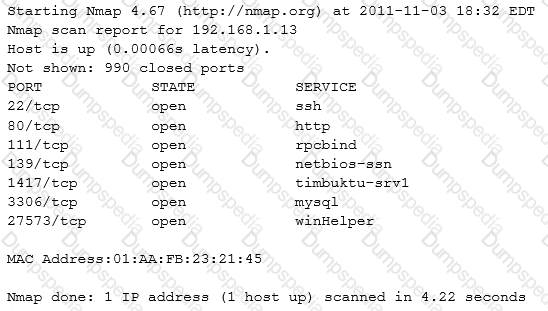
Subsequent investigation has allowed the organization to conclude that all of the well-known, standard ports are secure. Which of the following services is the problem?
A cybersecurity analyst was asked to review several results of web vulnerability scan logs.
Given the following snippet of code:

Which of the following BEST describes the situation and recommendations to be made?
A hacker issued a command and received the following response:
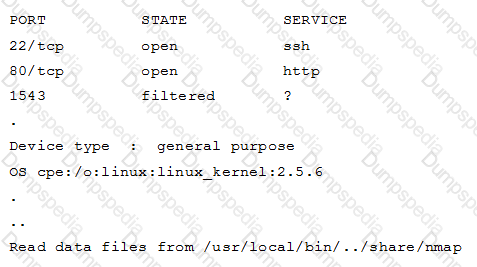
Which of the following describes what the hacker is attempting?
A company uses a managed IDS system, and a security analyst has noticed a large volume of brute force password attacks originating from a single IP address. The analyst put in a ticket with the IDS provider, but no action was taken for 24 hours, and the attacks continued. Which of the following would be the BEST approach for the scenario described?