A user downloads an application from a website and intends to modify the application's code. Which of the following license types does the user need for this task?
A user wants to connect to a home's Wi-Fi from the basement but is unable to do so. Which of the following is a potential cause of the issue?
Which of the following can be used to stop an application that is no longer responding?
Which of the following network devices permits and restricts network traffic as its primary function?
A user has concerns about device theft because they are working on a laptop at a local coffee shop. Which of the following physical devices would be best to protect the laptop?
A group wants to store data while collaborating on a project. Which of the following is the best option to enable high availability of the data?
Given the following table:
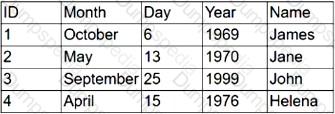
Which of the following fields best represents a primary key?
Given the following pseudocode:
10 FOR Q=1 TO 100
20 PRINT Q
30 NEXT Q
40 EXIT
Which of the following best represents line 10?
A user is typing a document using a keyboard. Which of the following describes this action?
Which of the following concepts is represented by the sale of customer email addresses to potential product vendors?
An employee is working on a database and wants to retrieve specific information. Which of the following should the employee use?
Given the following pseudocode:
This is a paragraph.
Which of the following best represents the type of language used by this code?
All relational databases utilize unique identifiers. Which of the following is the best term for an identifier?
Which of the following internet service types is delivered using an SFP connector?
A programmer wants to write code that will be more efficient when executed at runtime. Which of the following language types should the programmer use?
Which of the following data types would be best for storing data representing a phone number?
A user is testing new speakers on a laptop, but the user does not hear any sounds. The speakers are plugged in and turned on, and the correct driver is updated. Which of the following would most likely cause the issue?
A lab technician removes access from students who do not need to use a fileshare. Which of the following best describes this action?
An employee attempts to install software on a PC. A prompt to enter a username and password appears on-screen. The employee then receives an “access denied” message and cannot install the software. Which of the following types of access would allow the employee to accomplish this task?
A company is using data to provide senior leaders with information to drive company decision-making. Which of the following best describes this process?
A user is trying to view a report via a hyperlink on a website. When the user clicks on the hyperlink, nothing happens. Which of the following must be configured to view the report?
Which of the following best describes a group of computers that are in close proximity to each other on the same network?
Which of the following units of measurement is used when describing a gaming monitor?
A programmer creates a graphical representation of code components and the sequence for code execution. Which of the following has the programmer created?
A programmer needs to create a space in an application code to hold a value. The value will be updated periodically when the code is executed. Which of the following should the programmer use?
Which of the following is used to terminate a Cat 6 cable to an RJ45 connector?
A user wants to graphically depict the steps of a process. Which of the following types of software should the user utilize?
A user wants to download music from a computer to a smartphone. Which of the following cables should the user use to transfer the files?
A technician sets up a small wireless network, but it appears to provide less coverage than expected. Which of the following is the most likely cause of this issue?
Which of the following is commonly used to measure the RAM capacity of a smartphone?
A user needs to reconfigure local storage on an OS. Which of the following should be used?
Which of the following makes a file readable only by select users who possess a key?