In response to an audit finding, a company's Chief information Officer (CIO) instructed the security department to Increase the security posture of the vulnerability management program. Currency, the company's vulnerability management program has the following attributes:
Which of the following would BEST Increase the security posture of the vulnerably management program?
A company notices unknown devices connecting to the internal network and would like to implement a solution to block all non-corporate managed machines. Which of the following solutions would be best to accomplish this goal?
A security analyst at exampte.com receives a SIEM alert for an IDS signature and reviews the associated packet capture and TCP stream:
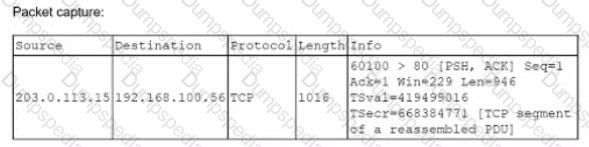
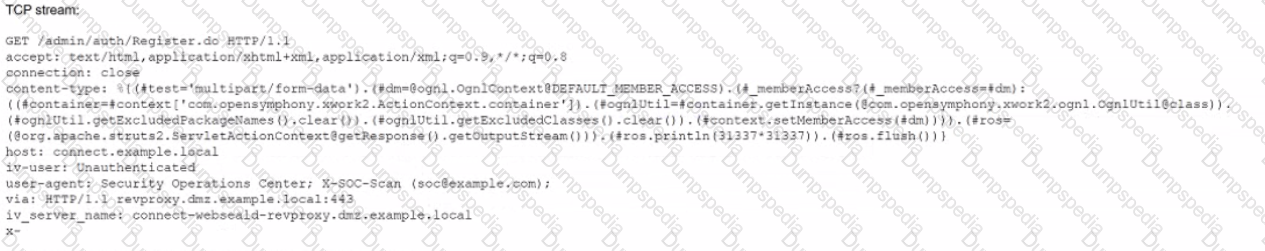
Winch of the following actions should the security analyst lake NEXT?
A new prototype for a company's flagship product was leaked on the internet As a result, the management team has locked out all USB drives Optical drive writers are not present on company computers The sales team has been granted an exception to share sales presentation files with third parties Which of the following would allow the IT team to determine which devices are USB enabled?
Which of the following BEST explains the function of trusted firmware updates as they relate to hardware assurance?
A security technician is testing a solution that will prevent outside entities from spoofing the company's email domain, which is compatia.org. The testing is successful, and the security technician is prepared to fully implement the solution. Which of the following actions should the technician take to accomplish this task?
A digital forensics investigator works from duplicate images to preserve the integrity of the original evidence. Which of the following types of media are most volatile and should be preserved? (Select two).
Which of the following describes the mam difference between supervised and unsupervised machine-learning algorithms that are used in cybersecurity applications?
A security analyst is investigate an no client related to an alert from the threat detection platform on a host (10.0 1.25) in a staging environment that could be running a cryptomining tool because it in sending traffic to an IP address that are related to Bitcoin.
The network rules for the instance are the following:
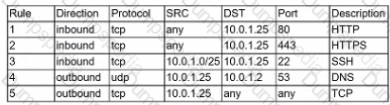
Which of the following is the BEST way to isolate and triage the host?
A security analyst is reviewing malware files without running them. Which of the following analysis types is the security analyst using?
During a routine security review, anomalous traffic from 9.9.9.9 was observed accessing a web server in the corporate perimeter network. The server is mission critical and must remain accessible around the world to serve web content. The Chief Information Security Officer has directed that improper traffic must be restricted. The following output is from the web server:
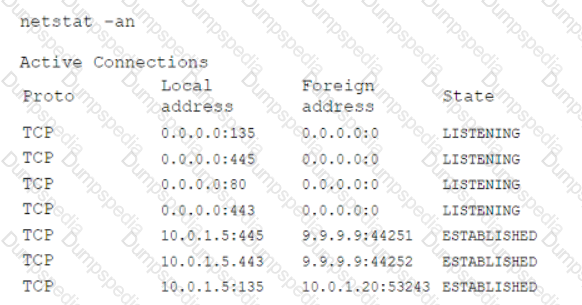
Which of the following is the best method to accomplish this task?
Which of the following are important reasons for performing proactive threat-hunting activities7 (Select two).
A product security analyst has been assigned to evaluate and validate a new products security capabilities Part of the evaluation involves reviewing design changes at specific intervals tor security deficiencies recommending changes and checking for changes at the next checkpoint Which of the following BEST defines the activity being conducted?
As part of the senior leadership team's ongoing nsk management activities the Chief Information Security Officer has tasked a security analyst with coordinating the right training and testing methodology to respond to new business initiatives or significant changes to existing ones The management team wants to examine a new business process that would use existing infrastructure to process and store sensitive data Which of the following would be appropnate for the security analyst to coordinate?
A security analyst is deploying a new application in the environment. The application needs to be integrated with several existing applications that contain SPI Pnor to the deployment, the analyst should conduct:
A security administrator needs to provide access from partners to an Isolated laboratory network inside an organization that meets the following requirements:
• The partners' PCs must not connect directly to the laboratory network.
• The tools the partners need to access while on the laboratory network must be available to all partners
• The partners must be able to run analyses on the laboratory network, which may take hours to complete
Which of the following capabilities will MOST likely meet the security objectives of the request?
A company employee downloads an application from the internet. After the installation, the employee begins experiencing noticeable performance issues, and files are appearing on the desktop.
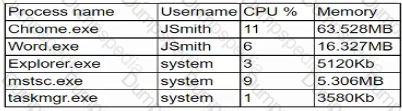
Which of the following processes will the security analyst Identify as the MOST likely indicator of system compromise given the processes running in Task Manager?
An IT security analyst has received an email alert regarding vulnerability within the new fleet of vehicles the company recently purchased. Which of the following attack vectors is the vulnerability MOST likely targeting?
After a remote command execution incident occurred on a web server, a security analyst found the following piece of code in an XML file:

Which of the following it the BEST solution to mitigate this type of attack?
After examining a header and footer file, a security analyst begins reconstructing files by scanning the raw data bytes of a hard disk and rebuilding them. Which of the following techniques is the analyst using?
White reviewing incident reports from the previous night, a security analyst notices the corporate websites were defaced with po mcai propaganda. Which of the following BEST Describes this type of actor?
During an incident investigation, a security analyst discovers the web server is generating an unusually high volume of logs The analyst observes the following response codes:
• 20% of the logs are 403
• 20% of the logs are 404
• 50% of the logs are 200
• 10% of the logs are other codes
The server generates 2MB of logs on a daily basis, and the current day log is over 200MB. Which of the following commands should the analyst use to identify the source of the activity?
A company is required to monitor for unauthorized changes to baselines on all assets to comply with industry regulations. Two of the remote units did not recover after scans were performed on the assets. An analyst needs to recommend a solution to prevent recurrence. Which of the following is the best way to satisfy the regulatory requirement without impacting the availability to similar assets and creating an unsustainable process?
While conducting a cloud assessment, a security analyst performs a Prowler scan, which generates the following within the report:
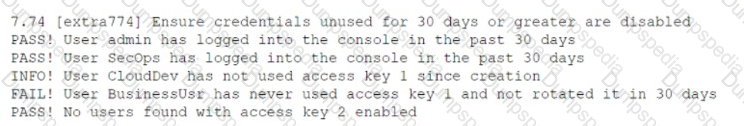
Based on the Prowler report, which of the following is the BEST recommendation?
A routine vulnerability scan detected a known vulnerability in a critical enterprise web application. Which of the following would be the BEST next step?
A SIEM analyst receives an alert containing the following URL:
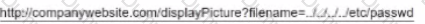
Which of the following BEST describes the attack?
During the onboarding process for a new vendor, a security analyst obtains a copy of the vendor's latest penetration test summary:
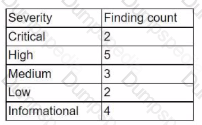
Performed by: Vendor Red Team Last performed: 14 days ago
Which of the following recommendations should the analyst make first?
A company wants to ensure a third party does not take intellectual property and build a competing product. Which of the following is a non-technical data and privacy control that would best protect the company?
Due to continued support of legacy applications, an organization's enterprise password complexity rules are inadequate for its required security posture. Which of the following is the BEST compensating control to help reduce authentication compromises?
An analyst determines a security incident has occurred Which of the following is the most appropnate NEXT step in an incident response plan?
A company's Chief Information Security Officer [CISO) is concerned about the integrity of some highly confidential files. Any changes to these files must be tied back to a specific authorized user's activity session. Which of the following is the best technique to address the ClSO's concerns?
A security analyst is researching ways to improve the security of a company's email system to mitigate emails that are impersonating company executives. Which of the following would be BEST for the analyst to configure to achieve this objective?
An organization completed an internal assessment of its policies and procedures. The audit team identified a deficiency in the policies and procedures for PH. Which of the following should be the first step to secure the organization's Pll?
A security analyst responds to a series of events surrounding sporadic bandwidth consumption from an endpoint device. The security analyst then identifies the following additional details:
• Bursts of network utilization occur approximately every seven days.
• The content being transferred appears to be encrypted or obfuscated.
• A separate but persistent outbound TCP connection from the host to infrastructure in a third-party cloud is in place.
• The HDD utilization on the device grows by 10GB to 12GB over the course of every seven days.
• Single file sizes are 10GB.
Which of the following describes the most likely cause of the issue?
A security analyst is scanning the network to determine if a critical security patch was applied to all systems in an enterprise. The Organization has a very low tolerance for risk when it comes to resource availability. Which of the following is the BEST approach for configuring and scheduling the scan?
A company frequently expenences issues with credential stuffing attacks Which of the following is the BEST control to help prevent these attacks from being successful?
An employee contacts the SOC to report a high-severity bug that was identified in a new, internally developed web application, which went live in production last week. The SOC staff did not receive contact details or escalation procedures to follow. Which of the following stages of the SDLC
process was overlooked?
A company's application development has been outsourced to a third-party development team. Based on the SLA. The development team must follow industry best practices for secure coding. Which of the following is the BEST way to verify this agreement?
During the threat modeling process for a new application that a company is launching, a security analyst needs to define methods and items to take into consideralion Wtiich of the following are part of a known threat modeling method?
When investigating a report of a system compromise, a security analyst views the following /var/log/secure log file:
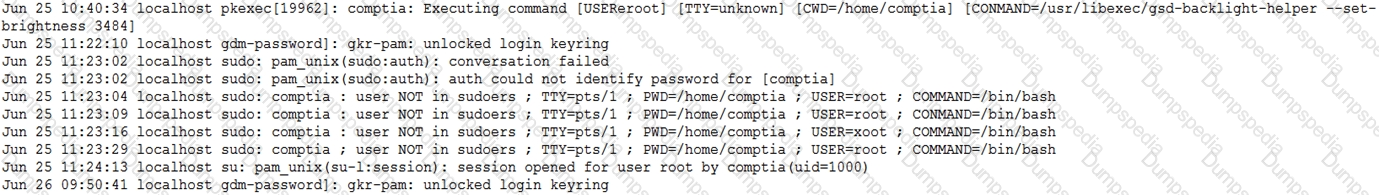
Which of the following can the analyst conclude from viewing the log file?
A security analyst is reviewing the network security monitoring logs listed below:
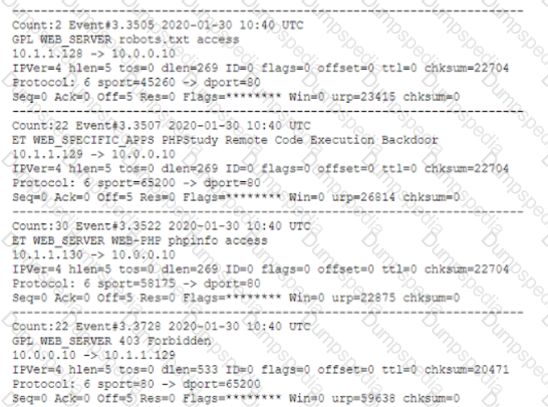
Which of the following is the analyst most likely observing? (Select two).
During a routine review of service restarts a security analyst observes the following in a server log:
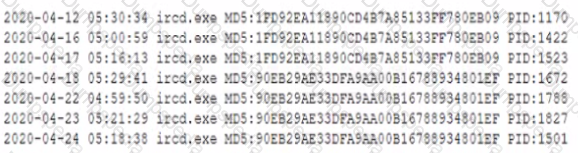
Which of the following is the GREATEST security concern?
As part of an Intelligence feed, a security analyst receives a report from a third-party trusted source. Within the report are several detrains and reputational information that suggest the company's employees may be targeted for a phishing campaign. Which of the following configuration changes would be the MOST appropriate for Mergence gathering?
An analyst received an alert regarding an application spawning a suspicious command shell process Upon further investigation, the analyst observes the following registry change occurring immediately after the suspicious event:

Which of the following was the suspicious event able to accomplish?
During a review of the vulnerability scan results on a server, an information security analyst notices the following:
The MOST appropriate action for the analyst to recommend to developers is to change the web server so:
Which of the following organizational initiatives would be MOST impacted by data severighty issues?
A vulnerability scanner has identified an out-of-support database software version running on a server. The software update will take six to nine months to complete. The management team has agreed to a one-year extended support contract with the software vendor. Which of the following BEST describes the risk treatment in this scenario?
According to a static analysis report for a web application, a dynamic code evaluation script injection vulnerability was found. Which of the following actions is the BEST option to fix the vulnerability in the source code?
A security analyst notices the following proxy log entries:
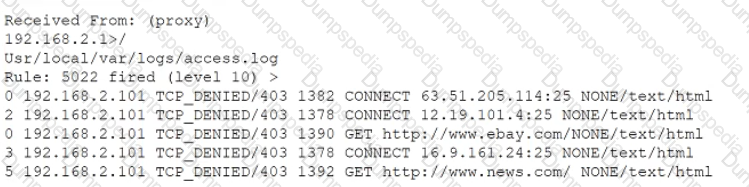
Which of the following is the user attempting to do based on the log entries?
A Chief Information Security Officer (CISO) is concerned about new privacy regulations that apply to the company. The CISO has tasked a security analyst with finding the proper control functions to verify that a user's data is not altered without the user's consent. Which of the following would be an appropriate course of action?
The IT department is concerned about the possibility of a guest device infecting machines on the corporate network or taking down the company's singe internet connection. Which of the following should a security analyst recommend to BEST meet the requirements outlined by the IT Department?
A security analyst performs various types of vulnerability scans. Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
Instructions:
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

A security analyst is reviewing the following server statistics:
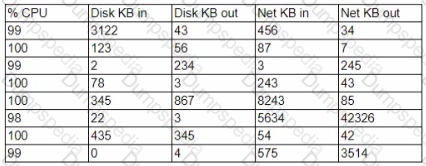
Which of the following is MOST likely occurring?
A consultant evaluating multiple threat intelligence leads to assess potential risks for a client. Which of the following is the BEST approach for the consultant to consider when modeling the client's attack surface?
Which of the following attack techniques has the GREATEST likelihood of quick success against Modbus assets?
A company's security team recently discovered a number of workstations that are at the end of life. The workstation vendor informs the team that the product is no longer supported and patches are no longer available The company is not prepared to cease its use of these workstations Which of the following would be the BEST method to protect these workstations from threats?
Which of the following incident response components can identify who is the llaison between multiple lines of business and the pubic?
During a review of SIEM alerts, a securrty analyst discovers the SIEM is receiving many alerts per day from the file-integrity monitoring toot about files from a newly deployed application that should not change. Which of the following steps should the analyst complete FIRST to respond to the issue7
An analyst is responding to an incident within a cloud infrastructure Based on the logs and traffic analysis, the analyst thinks a container has been compromised Which of the following should Ihe analyst do FIRST?
A security analyst is running a tool against an executable of an unknown source. The Input supplied by the tool to the executable program and the output from the executable are shown below:
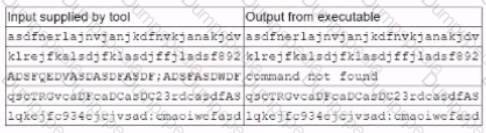
Which of the following should the analyst report after viewing this Information?
Company A is m the process of merging with Company B As part of the merger, connectivity between the ERP systems must be established so portent financial information can be shared between the two entitles. Which of the following will establish a more automated approach to secure data transfers between the two entities?
A company is setting up a small, remote office to support five to ten employees. The company's home office is in a different city, where the company uses a cloud service provider for its business applications and a local server to host its data. To provide shared access from the remote office to the local server and the business applications, which of the following would be the easiest and most secure solution?
Which of the following describes the difference between intentional and unintentional insider threats'?
A forensic analyst is conducting an investigation on a compromised server Which of the following should the analyst do first to preserve evidence''
While investigating reports or issues with a web server, a security analyst attempts to log in remotely and recedes the following message:
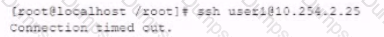
The analyst accesses the server console, and the following console messages are displayed:
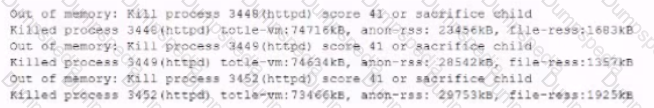
The analyst is also unable to log in on the console. While reviewing network captures for the server, the analyst sees many packets with the following signature:
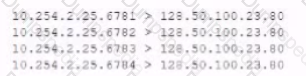
Which of the following is the BEST step for the analyst to lake next in this situation?
While reviewing a vulnerability assessment, an analyst notices the following issue is identified in the report:
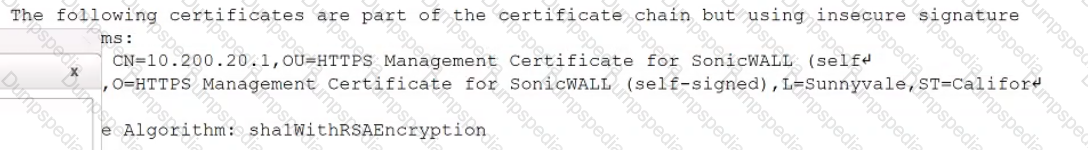 this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
A company has a cluster of web servers that is critical to the business. A systems administrator installed a utility to troubleshoot an issue, and the utility caused the entire cluster to 90 offline. Which of the following solutions would work BEST prevent to this from happening again?
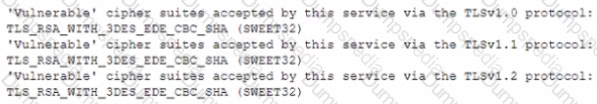
A security analyst is reviewing vulnerability scans from an organization's internet-facing web services. The following is from an output file called ssl-test_webapps.comptia.org:
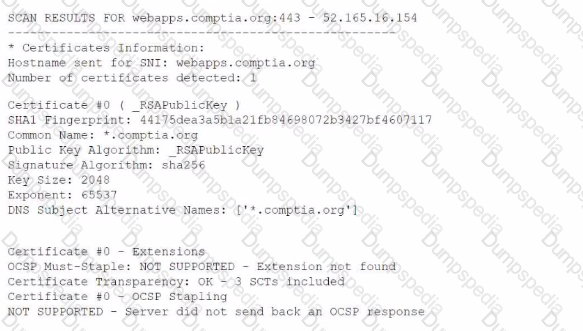
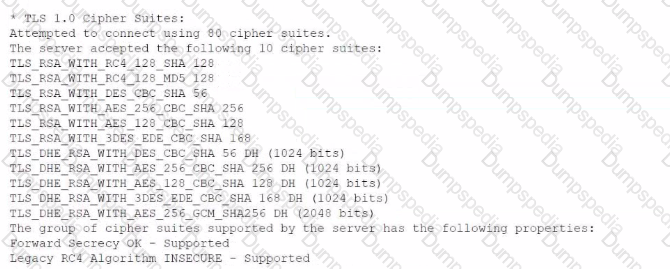
Which of the following lines from this output most likely indicates that attackers could quickly use brute force and determine the negotiated secret session key?
A software developer is correcting the error-handling capabilities of an application following the initial coding of the fix. Which of the following would the software developer MOST likely performed to validate the code poor to pushing it to production?
A security analyst is reviewing the following log entries to identify anomalous activity:
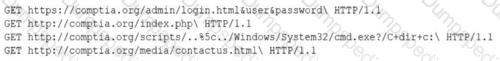
Which of the following attack types is occurring?
A company is experiencing a malware attack within its network. A security engineer notices many of the impacted assets are connecting outbound to a number of remote destinations and exfiltrating data. The security engineer also see that deployed, up-to-date antivirus signatures are ineffective. Which of the following is the BEST approach to prevent any impact to the company from similar attacks in the future?
The Chief Information Security Officer (CISO) of a large financial institution is seeking a solution that will block a predetermined set of data points from being transferred or downloaded by employees. The CISO also wants to track the data assets by name, type, content, or data profile.
Which of the following BEST describes what the CIS wants to purchase?
A Chief Information Security Officer has requested a security measure be put in place to redirect certain traffic on the network. Which of the following would best resolve this issue?
A company wants to configure the environment to allow passive network monitonng. To avoid disrupting the sensitive network, which of the following must be supported by the scanner's NIC to assist with the company's request?
Due to a rise m cyberattackers seeking PHI, a healthcare company that collects highly sensitive data from millions of customers is deploying a solution that will ensure the customers' data is protected by the organization internally and externally Which of the following countermeasures can BEST prevent the loss of customers' sensitive data?
An organization recently discovered that spreadsheet files containing sensitive financial data were improperly stored on a web server. The management team wants to find out if any of these files were downloaded by pubic users accessing the server. The results should be written to a text file and should induce the date. time, and IP address associated with any spreadsheet downloads. The web server's log file Is named webserver log, and the report We name should be accessreport.txt. Following is a sample of the web servefs.log file:
2017-0-12 21:01:12 GET /index.htlm - @4..102.33.7 - return=200 1622
Which of the following commands should be run if an analyst only wants to include entries in which spreadsheet was successfully downloaded?
A Chief Information Officer wants to implement a BYOD strategy for all company laptops and mobile phones. The Chief Information Security Officer is concerned with ensuring all devices are patched and running some sort of protection against malicious software. Which of the following existing technical controls should a security analyst recommend to best meet all the requirements?
A user reports a malware alert to the help desk. A technician verities the alert, determines the workstation is classified as a low-severity device, and uses network controls to block access. The technician then assigns the ticket to a security analyst who will complete the eradication and recovery processes. Which of the following should the security analyst do next?
Members of the sales team are using email to send sensitive client lists with contact information to their personal accounts The company's AUP and code of conduct prohibits this practice. Which of the following configuration changes would improve security and help prevent this from occurring?
An organization is required to be able to consume multiple threat feeds simultaneously and to provide actionable intelligence to various teams. The organization would also like to be able to leverage the intelligence to enrich security event data. Which of the following functions would most likely help the security analyst meet the organization's requirements?
During an incident response procedure, a security analyst acquired the needed evidence from the hard drive of a compromised machine. Which of the following actions should the analyst perform next to ensure the data integrity of the evidence?
A company's blocklist has outgrown the current technologies in place. The ACLs are at maximum, and the IPS signatures only allow a certain amount of space for domains to be added, creating the need for multiple signatures. Which of the following configuration changes to the existing controls would be the MOST appropriate to improve performance?
A Chief Executive Officer (CEO) is concerned about the company’s intellectual property being leaked to competitors. The security team performed an extensive review but did not find any indication of an outside breach. The data sets are currently encrypted using the Triple Data Encryption Algorithm. Which of the following courses of action is appropriate?
A security team has begun updating the risk management plan, incident response plan, and system security plan to ensure compliance with security review guidelines. Which of the following can be executed by internal managers to simulate and validate the proposed changes?
An organization has specific technical nsk mitigation configurations that must be implemented before a new server can be approved for production Several critical servers were recently deployed with the antivirus missing unnecessary ports disabled and insufficient password complexity Which of the following should the analyst recommend to prevent a recurrence of this risk exposure?
An organization is focused on restructuring its data governance programs and an analyst has been Tasked with surveying sensitive data within the organization. Which of the following is the MOST accurate method for the security analyst to complete this assignment?
Forming a hypothesis, looking for indicators of compromise, and using the findings to proactively improve detection capabilities are examples of the value of:
An organization wants to implement controls for protecting private information at rest. Which of the following would meet the organization's need?
A Chief Executive Officer (CEO) is concerned the company will be exposed to data sovereignty issues as a result of some new privacy regulations to help mitigate this risk. The Chief Information Security Officer (CISO) wants to implement an appropriate technical control. Which of the following would meet the requirement?
A company’s Chief Information Security Officer (CISO) published an Internet usage policy that prohibits employees from accessing unauthorized websites. The IT department whitelisted websites used for business needs. The CISO wants the security analyst to recommend a solution that would improve security and support employee morale. Which of the following security recommendations would allow employees to browse non-business-related websites?
An employee observes degraded system performance on a Windows workstation. While attempting to access documents, the employee notices the file icons appear abnormal and the file extensions have been changed. The employee instantly shuts down the machine and alerts a supervisor.
Which of the following forensic evidence will be lost as a result of these actions?
A manufacturing company uses a third-party service provider for Tier 1 security support. One of the requirements is that the provider must only source talent from its own country due to geopolitical and national security interests. Which of the following can the manufacturing company implement to ensure the third-party service provider meets this requirement?
A security officer needs to find the most cost-effective solution to the current data privacy and protection gap found in the last security assessment. Which of the following is the BEST recommendation?
A Chief Information Security Officer has asked for a list of hosts that have critical and high-severity findings as referenced in the CVE database. Which of the following tools would produce the assessment output needed to satisfy this request?
A security analyst is reviewing the output of tcpdump to analyze the type of activity on a packet capture:
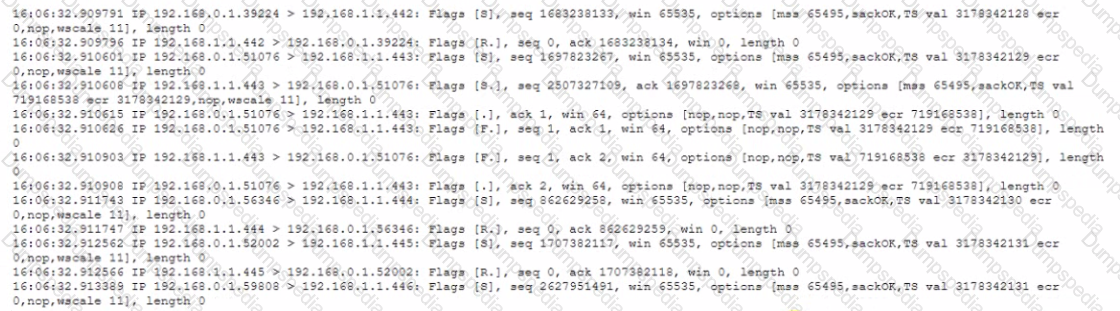
Which of the following generated the above output?
Which of the following activities is designed to handle a control
failure that leads to a breach?
Which of the following is the BEST way to gather patch information on a specific server?
An analyst reviews the most recent vulnerability management report and notices a firewall with 99.98% required uptime is reporting different firmware versions on scans than were reported in previous scans. The vendor released new firewall firmware a few months ago. Which of the following will the analyst most likely do next given the requirements?
A threat intelligence group issued a warning to its members regarding an observed increase in attacks performed by a specific threat actor and the related loCs. Which is of the following is (he best method to operationalize these loCs to detect future attacks?
A social media company is planning an acquisition. Prior to the purchase, the Chief Security Officer (CSO) would like a full report to gain a better understanding of the prospective company's cybersecurity posture and to identify risks in the supply chain. Which of the following will best support the CSO's objective?
During an audit several customer order forms were found to contain inconsistencies between the actual price of an item and the amount charged to the customer Further investigation narrowed the cause of the issue to manipulation of the public-facing web form used by customers to order products Which of the following would be the BEST way to locate this issue?
At which of the following phases of the SDLC shoukJ security FIRST be involved?
A security analyst discovers the accounting department is hosting an accounts receivable form on a public document service. Anyone with the link can access it. Which of the following threats applies to this situation?