A systems administrator is deploying a new version of a website. The website is deployed in the cloud using a VM cluster. The administrator must then deploy the new version into one VM first. After a period of time, if there are no issues detected, a second VM will be updated. This process must continue until all the VMS are updated. Which of the following upgrade methods is being implemented?
A developer is no longer able to access a public cloud API deployment, which was working ten minutes prior.
Which of the following is MOST likely the cause?
Which of the following cloud deployment models allows a company to have full control over its IT infrastructure?
An organization is deploying development, quality assurance, and production environments with equal numbers of IP addresses to the cloud. The IP address range provided is 10.168.0.0/24, and it needs to be terminated on a firewall. Which of the following IP subnets and firewall IPS should be used for one of the environments?
A web consultancy group currently works in an isolated development environment. The group uses this environment for the creation of the final solution, but also for showcasing it to customers, before commissioning the sites in production. Recently, customers of newly commissioned sites have reported they are not receiving the final product shown by the group, and the website is performing in unexpected ways. Which of the following additional environments should the group adopt and include in its process?
Audit and system logs are being forwarded to a syslog solution. An administrator observes that two application servers have not generated any logs for a period of three days, while others continue to send logs normally. Which of the following BEST explains what is occurring?
A cloud administrator is building a new VM for a network security appliance. The security appliance installer says the CPU clock speed does not meet the requirements.
Which of the following will MOST likely solve the issue?
A cloud administrator is setting up a DR site on a different zone of the same CSP. The application servers are replicated using the VM replication, and the database replication is set up using log shipping. Upon testing the DR site, the application servers are unable to access the database servers. The administrator has verified the systems are running and are accessible from the CSP portal.
Which of the following should the administrator do to fix this issue?
An organization is implementing a new requirement to facilitate users with faster downloads of corporate application content. At the same time, the organization is also expanding cloud regions.
Which of the following would be suitable to optimize the network for this requirement?
A systems administrator would like to reduce the network delay between two servers.
Which of the following will reduce the network delay without taxing other system resources?
An SQL injection vulnerability was reported on a web application, and the cloud platform team needs to mitigate the vulnerability while it is corrected by the development team.
Which of the following controls will BEST mitigate the risk of exploitation?
A systems administrator needs to connect the companys network to a public cloud services provider. Which of the following will BEST ensure encryption in transit for data transfers?
The Chief Information Officer of a financial services company wants to ensure stringent security measures are maintained while migrating customer financial information from a private cloud to the public cloud. The cloud engineer must deploy automated validation and verification checks to prevent unauthorized disclosure of financial information. Which of the following should be configured during the migration?
A global web-hosting company is concerned about the availability of its platform during an upcoming event. Web traffic is forecasted to increase substantially during the next week. The site contains mainly static content.
Which of the following solutions will assist with the increased workload?
An organization is developing a new online product. The product must:
• Minimize organizational infrastructure and comply with security standards.
• Minimize organizational compliance efforts.
• Focus on application development and increase speed to market.
Which of the following should the organization consider, given the requirements listed above?
A company is preparing a hypervisor environment to implement a database cluster. One of the requirements is to share the disks between the nodes of the cluster to access the same LUN. Which of the following protocols Should the company use? (Select TWO)
A company has a web application running in an on-premises environment that needs to be migrated to the cloud. The company wants to implement a solution that maximizes scalability, availability, and security, while requiring no infrastructure administration. Which of the following services would be BEST to meet this goal?
A systems administrator receives a ticket stating the following:
“The programming team received an error during the process deploying applications to the container platform. The error after the containerized applications were created”
Which the following should the administrator Check FIRST?
An organization is hosting a cloud-based web server infrastructure that provides web-hosting solutions. Sudden continuous bursts of traffic have caused the web servers to saturate CPU and network utilizations.
Which of the following should be implemented to prevent such disruptive traffic from reaching the web servers?
A cloud administrator recently deployed an update to the network drivers of several servers. Following the update, one of the servers no longer responds to remote login requests. The cloud administrator investigates the issue and gathers the following information:
Which of the following is the MOST likely cause of the server being unavailable?
A company uses multiple SaaS-based cloud applications. All the applications require authentication upon access. An administrator has been asked to address this issue and enhance security. Which of the following technologies would be the BEST solution?
A company has a large environment with multiple VPCs across three regions in a public cloud. The company is concerned about connectivity within the regions. Which of the following should the cloud administrator implement?
A company that performs passive vulnerability scanning at its transit VPC has detected a vulnerability related to outdated web-server software on one of its public subnets. Which of the following can the use to verify if this is a true positive with the LEAST effort and cost? (Select TWO).
An organization located in Asia connects to a cloud infrastructure hosted in North America and Europe. Sporadic slowness has been observed when using the PaaS and laaS components. A diagnostic using the following commands was run, and the following results were collected:
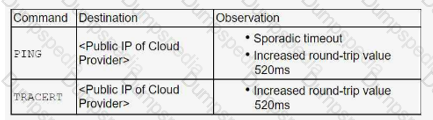
Which of the following is the most likely reason for the latency?
An organization deployed an application using a cloud provider's internal managed certificates. Developers are unable to retrieve data when calling the API from any machine.
The following error message is in the log:
12-04-2023-10:05:25, SSL Negotiation Error
12-04-2023-10:05:28,Invalid Certificate
12-04-2023-10:05:29, TLS Handshake Failed
12-04-2023-10:05:30,Connection Closed
Which of the following is the most likely cause of the error?
A systems administrator is selecting the appropriate RAID level to support a private cloud with the following requirements:
. The storage array must withstand the failure of up to two drives.
. The storage array must maximize the storage capacity of its drives.
Which of the following RAID levels should the administrator implement?
A cloud engineer is migrating a customer's web servers from a hypervisor platform to a CSP environment. The engineer needs to decouple the infrastructure and components during the migration to reduce the single points of failure. Which of the following storage options should the cloud engineer migrate the content to in order to improve availability?
An IT professional is selecting the appropriate cloud storage solution for an application that has the following requirements:
. The owner of the objects should be the object writer.
· The storage system must enforce TLS encryption.
Which of the following should the IT professional configure?
A systems administrator is provisioning VMs in a cloud environment and has been told to select an OS build with the furthest end-of-life date.
Which of the following OS builds would be BEST for the systems administrator to use?
Based on the shared responsibility model, which of the following solutions passes the responsibility of patching the OS to the customer?
A systems administrator is responsible for upgrading operating systems on VMs that are hosted in a cloud environment. The systems administrator wants to ensure the VMs receive updates for as long as possible. Which of the following should the systems administrator choose?
A storage array that is used exclusively for datastores is being decommissioned, and a new array has been installed. Now the private cloud administrator needs to migrate the data.
Which of the following migration methods would be the BEST to use?
Company A has acquired Company B and is in the process of integrating their cloud resources. Company B needs access to Company A’s cloud resources while retaining its IAM solution.
Which of the following should be implemented?
Which of the following provides groups of compute units that can horizontally scale according to a workload?
An enterprise is considering a cost model for a DBaaS. Which of the following is BEST for a cloud solution?
A cloud administrator needs to deploy a security virtual appliance in a private cloud environment, but this appliance will not be part of the standard catalog of items for other users to request. Which of the following is the BEST way to accomplish this task?
A company is using a hybrid cloud environment. The private cloud is hosting the business applications, and the cloud services are being used to replicate for availability purposes.
The cloud services are also being used to accommodate the additional resource requirements to provide continued services. Which of the following scalability models is the company utilizing?
A systems administrator has been notified of possible illegal activities taking place on the network and has been directed to ensure any relevant emails are preserved for court use.
Which of the following is this MOST likely an example of?
A DevOps team needs to provide a solution that offers isolation, portability, and scalability Which of the following would BEST meet these requirements?
A company has applications that need to remain available in the event of the data center being unavailable. The company's cloud architect needs to find a solution to maintain business continuity. Which of following should the company implement?
A company has developed a cloud-ready application. Before deployment, an administrator needs to select a deployment technology that provides a high level of portability and is lightweight in terms of footprint and resource requirements.
Which of the following solutions will be BEST to help the administrator achieve the requirements?
A cloud administrator is designing a multiregion network within an IaaS provider. The business requirements for configuring the network are as follows:
Which of the following solutions should the network administrator use within the IaaS provider to connect multiregions?
An organization will be deploying a web application in a public cloud with two web servers, two database servers, and a load balancer that is accessible over a single public IP.
Taking into account the gateway for this subnet and the potential to add two more web servers, which of the following will meet the minimum IP requirement?
A cloud administrator checked out the deployment scripts used to deploy the sandbox environment to a public cloud provider. The administrator modified the script to add an application load balancer in front of the web- based front-end application. The administrator next used the script to recreate a new sandbox environment successfully, and the application was then using the new load balancer.
The following week, a new update was required to add more front-end servers to the sandbox environment. A second administrator made the necessary changes and checked out the deployment scripts. The second administrator then ran the script, but the application load balancer was missing from the new deployment.
Which of the following is the MOST likely reason for this issue?
During a security incident on an laaS platform, which of the following actions will a systems administrator most likely take as part of the containment procedure?
A systems administrator audits a cloud application and discovers one of the key regulatory requirements has not been addressed. The requirement states that if
a physical breach occurs and hard drives are stolen, the contents of the drives should not be readable. Which of the following should be used to address the requirement?
A company has entered into a business relationship with another organization and needs to provide access to internal resources through directory services. Which of the following should a systems administrator implement?
An administrator is performing an in-place upgrade on a quest VM operating system.
Which of the following can be performed as a quick method to roll back to an earlier state, if necessary?
A systems administrator needs to deploy a solution to automate new application releases that come from the development team. The administrator is responsible for provisioning resources at the infrastructure layer without modifying any configurations in the application code. Which of the following would BEST accomplish this task?
A company has hired a security firm to perform a vulnerability assessment of its environment. In the first phase, an engineer needs to scan the network services exposed by the hosts. Which of the following will help achieve this with the LEAST privileges?
A cloud administrator is responsible for managing a VDI environment that provides end users with access to limited applications. Which of the following should the administrator make changes to when a new application needs to be provided?
Users currently access SaaS email with five-character passwords that use only letters and numbers. An administrator needs to make access more secure without changing the password policy. Which of the following will provide a more secure way of accessing email at the lowest cost?
In an IaaS platform, which of the following actions would a systems administrator take FIRST to identify the scope of an incident?
A cloud engineer has deployed a virtual storage appliance into a public cloud environment. The storage appliance has a NAT to a public IP address. An administrator later notices there are some strange files on the storage appliance and a large spike in network traffic on the machine. Which of the following is the MOST likely cause?
A cloud administrator needs to coordinate and automate the management of a company's secrets and keys for all its cloud services with minimal effort and low cost. Which of the following is the BEST option to achieve the goal?
An administrator manages a file server that has a lot of users accessing and creating many files. As a result, the storage consumption is growing quickly. Which of the following would BEST control storage usage?
A cloud engineer, who manages workloads in a public cloud environment, uses autoscaling to maintain availability of a critical application. During a recent burst in demands, the engineer received the following error alert:
LimitedlnstanceCapacity
Which of the following is MOST likely cause of the error?
A local bank has all of its infrastructure in the cloud. An update was applied to the main database server at 5:00 a.m. on Monday morning, and the database was then corrupted and unusable. It had to be restored from backup. The last backup was taken the night before at 10:00 p.m. The database was then restored successfully, but seven hours' worth of data was lost, which is deemed unacceptable. Which of the following needs to be updated in the DR plan?
A systems administrator must ensure confidential company information is not leaked to competitors. Which of the following services will BEST accomplish this goal?
A VDI provider suspects users are installing prohibited software on the instances. Which of the following must be implemented to prevent the issue?
A cloud administrator would like to maintain file integrity checks through hashing on a cloud object store. Which of the following is MOST suitable from a performance perspective?
While investigating network traffic, a cloud administrator discovers the monthly billing has increased substantially. Upon further review, it appears the servers have been compromised, and sensitive files have been exfiltrated. Which of the following can be implemented to maintain data confidentiality?
A new development team requires workstations hosted in a PaaS to develop a new website. Members of the team also require remote access to the workstations using their corporate email addresses. Which of the following solutions will BEST meet these requirements? (Select TWO).
A cloud administrator needs to implement a mechanism to monitor the expense of the company’s cloud resources.
Which of the following is the BEST option to execute this task with minimal effort?
A systems administrator is creating a playbook to run tasks against a server on a set schedule.
Which of the following authentication techniques should the systems administrator use within the playbook?
A systems administrator recently upgraded the processors in a web application host. Upon the next login, the administrator sees a new alert regarding the license being out of compliance.
Which of the following licensing models is the application MOST likely using?
Lateral-moving malware has infected the server infrastructure.
Which of the following network changes would MOST effectively prevent lateral movement in the future?
A web server has been deployed in a public IaaS provider and has been assigned the public IP address of 72.135.10.100. Users are now reporting that when they browse to the website, they receive a message indicating the service is unavailable. The cloud administrator logs into the server, runs a netstat command,
and notices the following relevant output:

Which of the following actions should the cloud administrator take to resolve the issue?
A cloud architect wants to minimize the risk of having systems administrators in an IaaS compute instance perform application code changes. The development group should be the only group allowed to modify files in the directory.
Which of the following will accomplish the desired objective?
An organization’s web server farm, which is hosted in the cloud with DNS load balancing, is experiencing a spike in network traffic. This has caused an outage of the organization’s web server infrastructure.
Which of the following should be implemented to prevent this in the future as a mitigation method?
A cloud administrator is planning to migrate a globally accessed application to the cloud.
Which of the following should the cloud administrator implement to BEST reduce latency for all users?
A systems administrator in a large enterprise needs to alter the configuration of one of the finance department’s database servers.
Which of the following should the administrator perform FIRST?
A company recently subscribed to a SaaS collaboration service for its business users. The company also has an on-premises collaboration solution and would like users to have a seamless experience regardless of the collaboration solution being used.
Which of the following should the administrator implement?
A technician deployed a VM with NL-SAS storage to host a critical application. Two weeks later, users have begun to report high application latency. Which of the following is the BEST action to correct the latency issue?
A company is migrating workloads from on premises to the cloud and would like to establish a connection between the entire data center and the cloud environment. Which of the following VPN configurations would accomplish this task?
A security audit related to confidentiality controls found the following transactions occurring in the system:
GET http://gateway.securetransaction.com/privileged/api/v1/changeResource?id=123 &user=277
Which of the following solutions will solve the audit finding?
An organization recently deployed a private cloud on a cluster of systems that delivers compute, network, and storage resources in a single hardware, managed by an intelligent software. Which of the following BEST describes this type of deployment?
A cloud administrator has created a new asynchronous workflow lo deploy VMs to the cloud in bulk. When the workflow is tested for a single VM, it completes successfully. However, if the workflow is used to create 50 VMs at once, the job fails. Which of the following is the MOST likely cause of the issue? (Choose two.)
A cloud engineer is performing updates to an application and needs to gracefully stop any new transactions from processing before the updates can be applied. Which of the following steps should the engineer take?
A company is using an laaS environment. Which of the following licensing models would BEST suit the organization from a financial perspective to implement scaling?
A systems administrator is securing a new email system for a large corporation. The administrator wants to ensure private corporate information is not emailed to external users. Which of the following would be MOST useful to accomplish this task?
A systems administrator is planning a penetration test for company resources that are hosted in a public cloud. Which of the following must the systems administrator do FIRST?
A company wants to utilize its private cloud for a new application. The private cloud resources can meet 75% of the application's resource requirements. Which of the following
scaling techniques can the cloud administrator implement to accommodate 100% of the application's requirements?
A production engineer is configuring a new application, which is running in containers, that requires access to a database. Which of the following methods will allow the application to authenticate to the database in the MOST secure way?
A systems administrator wants to restrict access to a set of sensitive files to a specific group of users. Which of the following will achieve the objective?
A company that requires full administrative control at the OS level is considering the use of public cloud services. Which of the following service models would BEST fit the company's requirements?
A cloud administrator is upgrading a cloud environment and needs to update the automation script to use a new feature from the cloud provider. After executing the script, the deployment fails. Which of the following is the MOST likely cause?
An engineer is responsible for configuring a new firewall solution that will be deployed in a new public cloud environment. All traffic must pass through the firewall. The SLA for the firewall is 99.999%. Which of the following should be deployed?
A user reports a poor-quality remote VDI session. Which of the following should the help desk technician do FIRST to troubleshoot the issue?
A VDI administrator has received reports from the drafting department that rendering is slower than normal. Which of the following should the administrator check FIRST to optimize the performance of the VDI infrastructure?
A cloud administrator wants to have a central repository for all the logs in the company’s private cloud. Which of the following should be implemented to BEST meet this requirement?
A company is planning to migrate applications to a public cloud, and the Chief Information Officer (CIO) would like to know the cost per business unit for the applications in the cloud. Before the migration, which of the following should the administrator implement FIRST to assist with reporting the cost for each business unit?
A company has an in-house-developed application. The administrator wants to utilize cloud services for additional peak usage workloads. The application has a very unique stack of dependencies.
Which of the following cloud service subscription types would BEST meet these requirements?
An organization is currently deploying a private cloud model. All devices should receive the time from the local environment with the least administrative effort. Which of the following ports needs to be opened to fulfill this requirement?
A systems administrator wants to be notified every time an application's configuration files are updated. Which of the following should the administrator implement to achieve the objective?
A company has two primary offices, one in the United States and one in Europe. The company uses a public laaS service that has a global data center presence to host its marketing materials. The marketing team, which is primarily based in Europe, has reported latency issues when retrieving these materials. Which of the following is the BEST option to reduce the latency issues?
A systems administrator deployed a new application release to the green stack of a blue-green infrastructure model and made the green stack primary. Immediately afterward, users began reporting application issues. The systems administrator must take action to bring the service online as quickly as possible. Which of the following is the FASTEST way to restore the service?
A company needs to migrate the storage system and batch jobs from the local storage system to a public cloud provider. Which of the following accounts will MOST likely be created to run the batch processes?
A resource pool in a cloud tenant has 90 GB of memory and 120 cores. The cloud administrator needs to maintain a 30% buffer for resources for optimal performance of the hypervisor. Which of the following would all ow for the maximum number of two-core machines with equal memory?
An administrator is securing a private cloud environment and wants to ensure only approved systems can connect to switches. Which of the following would be MOST useful to accomplish this task?
A systems administrator has migrated a web application to the cloud with a synchronous uplink speed of 100Mbps. After the migration, the administrator receives reports of slow connectivity to the web application. The administrator logs into the firewall and notices the WAN port is transmitting at a constant 12.5MBps. Which of the following BEST explains the reason for the issue?
Which of the following would be the BEST option for discussion of what individuals should do in an incident response or disaster recovery scenario?
A systems administrator is performing upgrades to all the hypervisors in the environment. Which of the following components of the hypervisors should be upgraded? (Choose two.)
A cloud security analyst needs to ensure the web servers in the public subnet allow only secure communications and must remediate any possible issue. The stateful configuration for the public web servers is as follows:
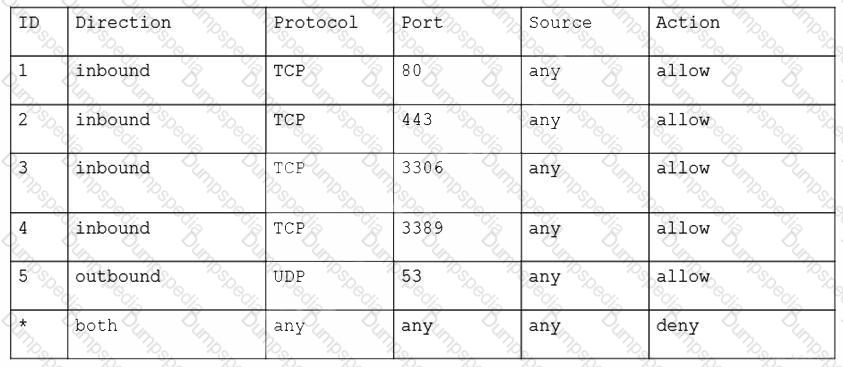
Which of the following actions should the analyst take to accomplish the objective?
A technician needs to deploy two virtual machines in preparation for the configuration of a financial application next week. Which of the following cloud deployment models should the technician use?
A systems administrator has been asked to restore a VM from backup without changing the current VM's operating state. Which of the following restoration methods would BEST fit this scenario?
Which of the following actions should a systems administrator perform during the containment phase of a security incident in the cloud?
A systems administrator is troubleshooting a performance issue with a virtual database server. The administrator has identified the issue as being disk related and believes the cause is a lack of IOPS on the existing spinning disk storage. Which of the following should the administrator do NEXT to resolve this issue?
Users of a public website that is hosted on a cloud platform are receiving a message indicating the connection is not secure when landing on the website. The administrator has found that only a single protocol is opened to the service and accessed through the URL https://www.comptiasite.com. Which of the following would MOST likely resolve the issue?
A company is concerned about the security of its data repository that contains customer PII. A systems administrator is asked to deploy a security control that will prevent the exfiltration of such data. Which of the following should the systems administrator implement?
A systems administrator is deploying a VM and would like to minimize storage utilization by ensuring the VM uses only the storage if needs. Which of the following will BEST achieve this goal?
A systems administrator adds servers to a round-robin, load-balanced pool, and then starts receiving reports of the website being intermittently unavailable. Which of the following is the MOST likely cause of the issue?
A cloud security analyst is implementing a vulnerability scan of the web server in the DMZ, which is running in an IaaS compute instance. The default inbound firewall settings are as follows:
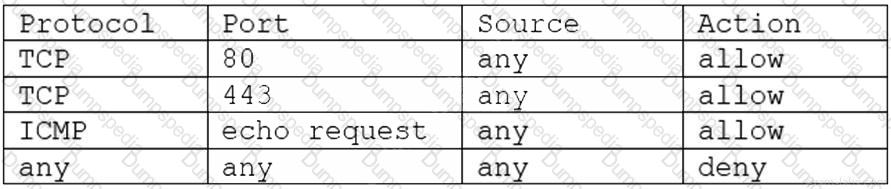
Which of the following will provide the analyst with the MOST accurate report?
An administrator recently provisioned a file server in the cloud. Based on financial considerations, the administrator has a limited amount of disk space. Which of the following will help control the amount of space that is being used?
Users of an enterprise application, which is configured to use SSO, are experiencing slow connection times. Which of the following should be done to troubleshoot the issue?
A cloud administrator is reviewing the annual contracts for all hosted solutions. Upon review of the contract for the hosted mail solution, the administrator notes the monthly subscription rate has increased every year. The provider has been in place for ten years, and there is a large amount of data being hosted. Which of the following is a barrier to switching providers?
An organization is using multiple SaaS-based business applications, and the systems administrator is unable to monitor and control the use of these subscriptions. The administrator needs to implement a solution that will help the organization apply security policies and monitor each individual SaaS subscription. Which of the following should be deployed to achieve these requirements?
A systems administrator is about to deploy a new VM to a cloud environment. Which of the following will the administrator MOST likely use to select an address for the VM?
Some VMs that are hosted on a dedicated host server have each been allocated with 32GB of memory. Some of VMs are not utilizing more than 30% of the allocation. Which of the following should be enabled to optimize the memory utilization?
A systems administrator is troubleshooting performance issues with a VDI environment. The administrator determines the issue is GPU related and then increases the frame buffer on the virtual machines. Testing confirms the issue is solved, and everything is now working correctly. Which of the following should the administrator do NEXT?