Does this command create a swarm service that only listens on port 53 using the UDP protocol?
Solution: ‘docker service create -name dns-cache -p 53:53 -service udp dns-cache'
Is this a type of Linux kernel namespace that provides container isolation?
Solution. Process ID
Does this command create a swarm service that only listens on port 53 using the UDP protocol?
Solution. ‘docker service create -name dns-cache -p 53:53 -udp dns-cache’
Is this a type of Linux kernel namespace that provides container isolation?
Solution: Authentication
A company's security policy specifies that development and production containers must run on separate nodes in a given Swarm cluster.
Can this be used to schedule containers to meet the security policy requirements?
Solution: node affinities
A company's security policy specifies that development and production containers must run on separate nodes in a given Swarm cluster. Can this be used to schedule containers to meet the security policy requirements?
Solution. environment variables
The following Docker Compose file is deployed as a stack:
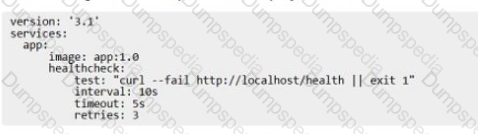
Is this statement correct about this health check definition?
Solution: Health checks test for app health five seconds apart. If the test fails, the container will be restarted three times before it gets rescheduled.
Is this an advantage of multi-stage builds?
Solution: simultaneously creates and tags multiple images
Will this command mount the host's '/data1 directory to the ubuntu container in read-only mode?
Solution. ‘docker run -v /data:/mydata -mode readonly ubuntu'
Will a DTR security scan detect this?
Solution: licenses for known third party binary components
In Docker Trusted Registry, is this how a user can prevent an image, such as 'nginx:latest’, from being overwritten by another user with push access to the repository?
Solution: Use the DTR web Ul to make all tags in the repository immutable.
Does this command create a swarm service that only listens on port 53 using the UDP protocol?
Solution. ‘docker service create -name dns-cache -p 53:53 -constraint networking.protocol.udp=true dns-cache"
Will a DTR security scan detect this?
Solution. private keys copied to the image
Is this a function of UCP?
Solution: scans images to detect any security vulnerability
One of several containers in a pod is marked as unhealthy after failing its livenessProbe many times. Is this the action taken by the orchestrator to fix the unhealthy container?
Solution: Kubernetes automatically triggers a user-defined script to attempt to fix the unhealthy container.
A company's security policy specifies that development and production containers must run on separate nodes in a given Swarm cluster.
Can this be used to schedule containers to meet the security policy requirements?
Solution: resource reservation
Does this describe the role of Control Groups (cgroups) when used with a Docker container?
Solution: accounting and limiting of resources
You configure a local Docker engine to enforce content trust by setting the environment variable
DOCKER_CONTENT_TRUST=1.
If myorg/myimage: 1.0 is unsigned, does Docker block this command?
Solution: docker service create myorg/myimage:1.0
Will this command ensure that overlay traffic between service tasks is encrypted?
Solution: docker service create --network --secure
Will this command ensure that overlay traffic between service tasks is encrypted?
Solution. docker network create -d overlay --secure
An application image runs in multiple environments, with each environment using different certificates and ports.
Is this a way to provision configuration to containers at runtime?
Solution: Create images that contain the specific configuration for every environment.
You are troubleshooting a Kubernetes deployment called api, and want to see the events table for this object. Does this command display it?
Solution: kubectl describe deployment api
You created a new service named 'http' and discover it is not registering as healthy. Will this command enable you to view the list of historical tasks for this service?
Solution: 'docker inspect http'
Can this set of commands identify the published port(s) for a container?
Solution. ‘docker port inspect", docker container inspect"
Will this command list all nodes in a swarm cluster from the command line?
Solution. ‘docker inspect nodes
Is this statement correct?
Solution. A Dockerfile stores persistent data between deployments of a container
You add a new user to the engineering organization in DTR.
Will this action grant them read/write access to the engineering/api repository?
Solution: Add the user directly to the list of users with read/write access under the repository's Permissions tab.
You created a new service named 'http* and discover it is not registering as healthy. Will this command enable you to view the list of historical tasks for this service?
Solution. ‘docker inspect http"
Will this command mount the host's '/data' directory to the ubuntu container in read-only mode?
Solution: 'docker run --add-volume /data /mydata -read-only ubuntu'
Seven managers are in a swarm cluster.
Is this how should they be distributed across three datacenters or availability zones?
Solution: 5-1-1
You configure a local Docker engine to enforce content trust by setting the environment variable DOCKER_C0NTENT_TRUST=l. If myorg/myimage: 1.0 is unsigned, does Docker block this command?
Solution. docker image build, from a Dockeflle that begins FROM myorg/myimage: l1.0
You created a new service named 'http' and discover it is not registering as healthy. Will this command enable you to view the list of historical tasks for this service?
Solution: 'docker ps http'
Is this a function of UCP?
Solution: enforces the deployment of signed images to the cluster
The Kubernetes yaml shown below describes a networkPolicy.
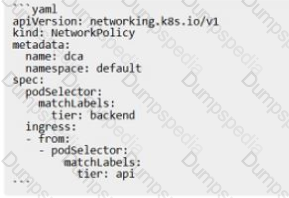
Will the networkPolicy BLOCK this trafftc?
Solution. a request issued from a pod bearing the tier: api label, to a pod bearing the tier: backend label
One of several containers in a pod is marked as unhealthy after failing its livenessProbe many times. Is this the action taken by the orchestrator to fix the unhealthy container?
Solution: The unhealthy container is restarted.
You want to create a container that is reachable from its host's network. Does this action accomplish this?
Solution: Use either EXPOSE or --publish to access the containers on the bridge network
You are pulling images from a Docker Trusted Registry installation
configured to use self-signed certificates, and this error appears:
`x509: certificate signed by unknown authority.
You already downloaded the Docker Trusted Registry certificate authority
certificate from https://dtr.example.com/ca.
How do you trust it? (Select two.)
Will this command mount the host's '/data' directory to the ubuntu container in read-only mode?
Solution: 'docker run --volume /data:/mydata:ro ubuntu'
Is this a type of Linux kernel namespace that provides container isolation?
Solution. Host
The following Docker Compose file is deployed as a stack:
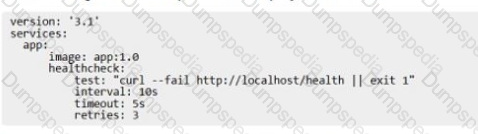
Is this statement correct about this health check definition?
Solution. Health checks lest for app health ten seconds apart. Three failed health checks transition the container into "unhealthy" status.
You want to create a container that is reachable from its host's network.
Does this action accomplish this?
Solution: Use network attach to access the container on the bridge network.
Two development teams in your organization use Kubernetes and want to deploy their applications while ensuring that Kubernetes-specific resources, such as secrets, are grouped together for each application.
Is this a way to accomplish this?
Solution: Create one namespace for each application and add all the resources to it.
Your organization has a centralized logging solution, such as Splunk.
Will this configure a Docker container to export container logs to the logging solution?
Solution. Set the log-driver-and log-opt keys to values for the logging solution (Splunk) in the daemon.json file.
Two development teams in your organization use Kubernetes and want to deploy their applications while ensuring that Kubernetes-specific resources, such as secrets, are grouped together for each application.
Is this a way to accomplish this?
Solution. Create a collection for for each application.
Is this an advantage of multi-stage builds?
Solution: faster image builds by allowing parallel execution of Docker builds
Will This command list all nodes in a swarm cluster from the command line?
Solution. ‘docker swarm nodes'
You want to create a container that is reachable from its host's network. Does this action accomplish this?
Solution: Use --link to access the container on the bridge network.
Will this action upgrade Docker Engine CE to Docker Engine EE?
Solution: Delete '/var/lib/docker' directory.