A company had an Amazon RDS for MySQL DB instance that was named mysql-db. The DB instance was deleted within the past 90 days. A developer needs to find which 1AM user or role deleted the DB instance in the AWS environment. Which solution will provide this information?
A developer wants to deploy a new version of an AWS Elastic Beanstalk application. During deployment the application must maintain full capacity and avoid service interruption. Additionally, the developer must minimize the cost of additional resources that support the deployment.
Which deployment method should the developer use to meet these requirements?
A developer has created an AWS Lambda function to provide notification through Amazon Simple Notification Service (Amazon SNS) whenever a file is uploaded to Amazon S3 that is larger than 50 MB. The developer has deployed and tested the Lambda function by using the CLI. However, when the event notification is added to the S3 bucket and a 3.000 MB file is uploaded, the Lambda function does not launch.
Which of the following Is a possible reason for the Lambda function's inability to launch?
A developer is working on an application that will store protected health information (PHI) in an Amazon RDS database. The developer applies encryption to the database. The developer must also encrypt the PHI data separately to prevent administrators from accessing the data. Because some of the PHI data files are large, the developer must encrypt the PHI data in the application locally before saving the data to the database.
Which solution will meet these requirements in the MOST secure way?
A developer creates an AWS CloudFormation template that defines one AWS Lambda function, one Amazon S3 bucket, and one IAM role. The developer wants to deploy multiple stacks from the same template across different environments. Each resource must have a unique name per environment.
Which combination of solutions will meet this requirement? (Select TWO.)
A developer is creating an AWS Serverless Application Model (AWS SAM) template. The AWS SAM template contains the definition of multiple AWS Lambda functions, an Amazon S3 bucket, and an Amazon CtoudFront distribution. One of the Lambda functions runs on Lambda@Edge in the CloudFront distribution. The S3 bucket is configured as an origin for the CloudFront distribution.
When the developer deploys the AWS SAM template in the eu-west-1 Region, the creation of the stack fails.
Which of the following could be the reason for this issue?
A company has a multi-node Windows legacy application that runs on premises. The application uses a network shared folder as a centralized configuration repository to store configuration files in .xml format. The company is migrating the application to Amazon EC2 instances. As part of the migration to AWS, a developer must identify a solution that provides high availability for the repository.
Which solution will meet this requirement MOST cost-effectively?
A developer created an AWS Lambda function that performs a series of operations that involve multiple AWS services. The function's duration time is higher than normal. To determine the cause of the issue, the developer must investigate traffic between the services without changing the function code
Which solution will meet these requirements?
A developer is integrating Amazon ElastiCache in an application. The cache will store data from a database. The cached data must populate real-time dashboards. Which caching strategy will meet these requirements?
A company hosts its application on AWS. The application runs on an Amazon Elastic Container Service (Amazon ECS) cluster that uses AWS Fargate. The cluster runs behind an Application Load Balancer The application stores data in an Amazon Aurora database A developer encrypts and manages database credentials inside the application
The company wants to use a more secure credential storage method and implement periodic credential rotation.
Which solution will meet these requirements with the LEAST operational overhead?
A social media application is experiencing high volumes of new user requests after a recent marketing campaign. The application is served by an Amazon RDS for MySQL instance. A solutions architect examines the database performance and notices high CPU usage and many "too many connections" errors that lead to failed requests on the database. The solutions architect needs to address the failed requests.
Which solution will meet this requirement?
A company offers a business-to-business software service that runs on dedicated infrastructure deployed in each customer's AWS account. Before a feature release, the company needs to run integration tests on real AWS test infrastructure. The test infrastructure consists of Amazon EC2 instances and an Amazon RDS database.
A developer must set up a continuous delivery process that will provision the test infrastructure across the different AWS accounts. The developer then must run the integration tests.
Which solution will meet these requirements with the LEAST administrative effort?
A company has built an AWS Lambda function to convert large image files into output files that can be used in a third-party viewer application The company recently added a new module to the function to improve the output of the generated files However, the new module has increased the bundle size and has increased the time that is needed to deploy changes to the function code.
How can a developer increase the speed of the Lambda function deployment?
A developer is working on a serverless application that needs to process any changes to an Amazon DynamoDB table with an AWS Lambda function.
How should the developer configure the Lambda function to detect changes to the DynamoDB table?
A developer wrote an application that uses an AWS Lambda function to asynchronously generate short videos based on requests from customers. This video generation can take up to 10 minutes. After the video is generated, a URL to download the video is pushed to the customer’s web browser. The customer should be able to access these videos for at least 3 hours after generation.
Which solution will meet these requirements?
An ecommerce company is developing a serverless application to track user activities. The company needs to track each type of activity with a timestamp and a unique product ID. The company also must track actions that are associated with each activity, such as product views, shopping cart actions, purchases, and checkout processes.
The company is planning a marketing campaign based on each user's activity. A developer needs to implement a partitioning strategy for an Amazon DynamoDB table to meet the data storage and access requirements for the application. The strategy must maximize provisioned throughput efficiency while minimizing the risk of throttling.
Which solution will meet these requirements?
A developer is using AWS CodeDeploy to automate a company's application deployments to Amazon EC2.
Which application specification file properties are required to ensure the software deployments do not fail? (Select TWO.)
A company requires that all applications running on Amazon EC2 use 1AM roles to gam access to AWS services. A developer is modifying an application that currently relies on 1AM user access keys stored in environment variables to access Amazon DynamoDB tables using boto, the AWS SDK for Python.
The developer associated a role with the same permissions as the 1AM user to the EC2 instance, then deleted the 1AM user. When the application was restarted, the AWS
Access Denied Exception messages started appearing in the application logs. The developer was able to use their personal account on the server to run DynamoDB API commands using the AWS CLI.
What is the MOST likely cause of the exception?
A developer is deploying an application on Amazon EC2 instances that run in Account A. The application needs to read data from an existing Amazon Kinesis data stream in Account B.
Which actions should the developer take to provide the application with access to the stream? (Select TWO.)
A developer is migrating some features from a legacy monolithic application to use AWS Lambda functions instead. The application currently stores data in an Amazon Aurora DB cluster that runs in private subnets in a VPC. The AWS account has one VPC deployed. The Lambda functions and the DB cluster are deployed in the same AWS Region in the same AWS account.
The developer needs to ensure that the Lambda functions can securely access the DB cluster without crossing the public internet.
Which solution will meet these requirements?
A company receives food orders from multiple partners. The company has a microservices application that uses Amazon API Gateway APIs with AWS Lambda integration. Each partner sends orders by calling a customized API that is exposed through API Gateway. The API call invokes a shared Lambda function to process the orders.
Partners need to be notified after the Lambda function processes the orders. Each partner must receive updates for only the partner's own orders. The company wants to add new partners in the future with the fewest code changes possible.
Which solution will meet these requirements in the MOST scalable way?
A company developed an API application on AWS by using Amazon CloudFront, Amazon API Gateway, and AWS Lambda. The API has a
minimum of four requests every second. A developer notices that many API users run the same query by using the POST method. The developer
wants to cache the POST request to optimize the API resources.
Which solution will meet these requirements?
A developer has a legacy application that is hosted on-premises. Other applications hosted on AWS depend on the on-premises application for proper functioning. In case of any application errors, the developer wants to be able to use Amazon CloudWatch to monitor and troubleshoot all applications from one place.
How can the developer accomplish this?
A company has a serverless application that uses an Amazon API Gateway API to invoke an AWS Lambda function. A developer creates a fix for a defect in the Lambda function code. The developer wants to deploy this fix to the production environment. To test the changes, the developer needs to send 10% of the live production traffic to the updated Lambda function version.
Options:
A company is running Amazon EC2 instances in multiple AWS accounts. A developer needs to implement an application that collects all the lifecycle events of the EC2 instances. The application needs to store the lifecycle events in a single Amazon Simple Queue Service (Amazon SQS) queue in the company's main AWS account for further processing.
Which solution will meet these requirements?
A developer for a company uses an Amazon S3 bucket to store log files. A bucket policy on the S3 bucket denies all write and delete operations for all principals.
The developer observes that files have been deleted from the S3 bucket despite the bucket policy. The developer must prevent additional deletions from the S3 bucket.
Which solution will meet this requirement?
An online food company provides an Amazon API Gateway HTTP API 1o receive orders for partners. The API is integrated with an AWS Lambda function. The Lambda function stores the orders in an Amazon DynamoDB table.
The company expects to onboard additional partners Some to me panthers require additional Lambda function to receive orders. The company has created an Amazon S3 bucket. The company needs 10 store all orders and updates m the S3 bucket for future analysis
How can the developer ensure that an orders and updates are stored to Amazon S3 with the LEAST development effort?
An application reads data from an Amazon Aurora global database with clusters in two AWS Regions. Database credentials are stored in AWS Secrets Manager in the primary Region and are rotated regularly.
The application must be able to run in both Regions and remain highly available.
Which combination of actions will meet these requirements? (Select TWO.)
A developer is writing an application that will retrieve sensitive data from a third-party system. The application will format the data into a PDF file. The PDF file could be more than 1 MB. The application will encrypt the data to disk by using AWS Key Management Service (AWS KMS). The application will decrypt the file when a user requests to download it. The retrieval and formatting portions of the application are complete.
The developer needs to use the GenerateDataKey API to encrypt the PDF file so that the PDF file can be decrypted later. The developer needs to use an AWS KMS symmetric customer managed key for encryption.
Which solutions will meet these requirements?
A company has an AWS Step Functions state machine named myStateMachine. The company configured a service role for Step Functions. The developer must ensure that only the myStateMachine state machine can assume the service role.
Which statement should the developer add to the trust policy to meet this requirement?
A developer is building a web and mobile application for two types of users: regular users and guest users. Regular users are required to log in, but guest users do not log in. Users should see only their data, regardless of whether they authenticate. Users need AWS credentials before they can access AWS resources.
A developer is modifying a large-scale IoT application that stores device telemetry data in an Amazon DynamoDB table. The telemetry data is valuable only for a limited time, but the application stores the data indefinitely. Data storage is slowing the application down. The developer needs a solution to improve the performance of the application.
Which solution will meet this requirement in the MOST operationally efficient way?
A developer is working on a web application that uses Amazon DynamoDB as its data store The application has two DynamoDB tables one table that is named artists and one table that is named songs The artists table has artistName as the partition key. The songs table has songName as the partition key and artistName as the sort key
The table usage patterns include the retrieval of multiple songs and artists in a single database operation from the webpage. The developer needs a way to retrieve this information with minimal network traffic and optimal application performance.
Which solution will meet these requirements'?
A developer wants the ability to roll back to a previous version of an AWS Lambda function in the event of errors caused by a new deployment. How can the developer achieve this with MINIMAL impact on users?
A developer registered an AWS Lambda function as a target for an Application Load Balancer (ALB) using a CLI command. However, the Lambda function is not being invoked when the client sends requests through the ALB.
Why is the Lambda function not being invoked?
An organization is using Amazon CloudFront to ensure that its users experience low-latency access to its web application. The organization has identified a need to encrypt all traffic between users and CloudFront, and all traffic between CloudFront and the web application.
How can these requirements be met? (Select TWO)
A developer needs to migrate an online retail application to AWS to handle an anticipated increase in traffic. The application currently runs on two servers: one server for the web application and another server for the database. The web server renders webpages and manages session state in memory. The database server hosts a MySQL database that contains order details. When traffic to the application is heavy, the memory usage for the web server approaches 100% and the application slows down considerably.
The developer has found that most of the memory increase and performance decrease is related to the load of managing additional user sessions. For the web server migration, the developer will use Amazon EC2 instances with an Auto Scaling group behind an Application Load Balancer.
Which additional set of changes should the developer make to the application to improve the application's performance?
A company's application runs on a fleet of Amazon EC2 instances in a VPC within private subnets that do not have public internet access. The company uses Amazon CloudWatch to monitor the application.
A developer is troubleshooting an issue with the application. Some performance metrics are not being published to CloudWatch. The developer uses EC2 Instance Connect to access an EC2 instance. The developer verifies that a CloudWatch agent is pre-installed and running.
The developer needs to ensure that the performance metrics are published to CloudWatch.
Which solution will meet this requirement in the MOST secure way?
A developer deploys an AWS Lambda function that writes data to Amazon DynamoDB. Amazon CloudWatch metrics show that some Lambda invocations result in errors. However, no CloudWatch log entries exist for the function. The function source code includes logging statements before the write operation.
What should the developer do to resolve the missing CloudWatch Logs entries?
A developer has created an AWS Lambda function that consumes messages from an Amazon SQS standard queue. The developer notices that the Lambda function processes some messages multiple times.
How should developer resolve this issue MOST cost-effectively?
A developer is building a microservice that uses AWS Lambda to process messages from an Amazon Simple Queue Service (Amazon SQS) standard queue. The Lambda function calls external APIs to enrich the SOS message data before loading the data into an Amazon Redshift data warehouse. The SOS queue must handle a maximum of 1.000 messages per second.
During initial testing, the Lambda function repeatedly inserted duplicate data into the Amazon Redshift table. The duplicate data led to a problem with data analysis. All duplicate messages were submitted to the queue within 1 minute of each other.
How should the developer resolve this issue?
A developer is deploying an application on Amazon EC2 instances that run in Account A. In certain cases, this application needs to read data from a private Amazon S3 bucket in Account B. The developer must provide the application access to the S3 bucket without exposing the S3 bucket to anyone else.
Which combination of actions should the developer take to meet these requirements? (Select TWO.)
A company has a large amount of data in an Amazon DynamoDB table. A large batch of data is appended to the table once each day. The company wants a solution that will make all the existing and future data in DynamoDB available for analytics on a long-term basis.
Which solution meets these requirements with the LEAST operational overhead?
A team of developed is using an AWS CodePipeline pipeline as a continuous integration and continuous delivery (CI/CD) mechanism for a web application. A developer has written unit tests to programmatically test the functionality of the application code. The unit tests produce a test report that shows the results of each individual check. The developer now wants to run these tests automatically during the CI/CD process.
A developer manages an application that stores user objects in an Amazon S3 bucket without versioning enabled. The application has premium users and basic users.
After premium users upload objects, the premium users have unlimited downloads of their objects. Their objects are stored with a premium/ prefix. After basic users upload objects, the basic users can download their objects for 90 days. Their objects are stored with a basic/ prefix.
The developer needs to implement a solution to automatically delete objects for the basic users after 90 days.
Which solution will meet these requirements with the LEAST development effort?
A developer is receiving an intermittent ProvisionedThroughputExceededException error from an application that is based on Amazon DynamoDB. According to the Amazon CloudWatch metrics for the table, the application is not exceeding the provisioned throughput. What could be the cause of the issue?
A developer is creating a stock trading application. The developer needs a solution to send text messages to application users to confirmation when a trade has been completed.
The solution must deliver messages in the order a user makes stock trades. The solution must not send duplicate messages.
Which solution will meet these requirements?
A developer is building a web application that uses Amazon API Gateway to expose an AWS Lambda function to process requests from clients. During testing, the developer notices that the API Gateway times out even though the Lambda function finishes under the set time limit.
Which of the following API Gateway metrics in Amazon CloudWatch can help the developer troubleshoot the issue? (Choose two.)
An ecommerce startup is preparing for an annual sales event. As the traffic to the company's application increases, the development team wants to be notified when the Amazon EC2 instance's CPU utilization exceeds 80%.
Which solution will meet this requirement?
An application that is deployed to Amazon EC2 is using Amazon DynamoDB. The app cation calls the DynamoDB REST API Periodically the application receives a ProvisionedThroughputExceededException error when the application writes to a DynamoDB table.
Which solutions will mitigate this error MOST cost-effectively^ (Select TWO)
A company runs an ecommerce application on AWS. The application stores data in an Amazon Aurora database.
A developer is adding a caching layer to the application. The caching strategy must ensure that the application always uses the most recent value for each data item.
Which caching strategy will meet these requirements?
A company is offering APIs as a service over the internet to provide unauthenticated read access to statistical information that is updated daily. The company uses Amazon API Gateway and AWS Lambda to develop the APIs. The service has become popular, and the company wants to enhance the responsiveness of the APIs.
Which action can help the company achieve this goal?
A developer is running an application on an Amazon EC2 instance. When the application attempts to read from an Amazon S3 bucket, the request fails. The developer determines that the IAM role associated with the EC2 instance is missing the required Amazon S3 read permissions.
The developer must grant the application access to read from the S3 bucket with the LEAST application disruption.
Which solution will meet this requirement?
A developer is writing an application that processes data delivered into an Amazon S3 bucket. The data is delivered approximately 10 times per day, and the developer expects the processing to complete in less than 1 minute on average.
How can the developer deploy and invoke the application with the LOWEST cost and LOWEST latency?
A company had an Amazon RDS for MySQL DB instance that was named mysql-db. The DB instance was deleted within the past 90 days.
A developer needs to find which IAM user or role deleted the DB instance in the AWS environment.
Which solution will provide this information?
A developer is creating a service that uses an Amazon S3 bucket for image uploads. The service will use an AWS Lambda function to create a thumbnail of each image Each time an image is uploaded the service needs to send an email notification and create the thumbnail The developer needs to configure the image processing and email notifications setup.
Which solution will meet these requirements?
A developer is creating an application that must be able to generate API responses without backend integrations. Multiple internal teams need to work with the API while the application is still in development.
Which solution will meet these requirements with the LEAST operational overhead?
A company has developed a new serverless application using AWS Lambda functions that will be deployed using the AWS Serverless Application Model (AWS SAM) CLI.
Which step should the developer complete prior to deploying the application?
A developer is implementing a serverless application by using AWS CloudFormation to provision Amazon S3 web hosting. Amazon API Gateway, and AWS Lambda functions. The Lambda function source code is zipped and uploaded to an S3 bucket. The S3 object key of the zipped source code is specified in the Lambda resource in the CloudFormation template.
The developer notices that there are no changes in the Lambda function every time the CloudFormation stack is updated.
How can the developer resolve this issue?
A developer has a financial application. The application uses AWS Secrets Manager to manage an Amazon RDS for PostgreSQL database's username and password. The developer needs to rotate the password while maintaining the application's high availability. Which solution will meet these requirements with LEAST development effort?
A developer is building two microservices that use an Amazon SQS queue to communicate. The messages that the microservices send to one another contain sensitive information. The developer must ensure the messages are stored and are encrypted at rest.
Which solution will meet these requirements?
A developer is receiving HTTP 400: ThrottlingException errors intermittently when calling the Amazon CloudWatch API. When a call fails, no data is retrieved.
What best practice should first be applied to address this issue?
A developer is troubleshooting an application mat uses Amazon DynamoDB in the uswest-2 Region. The application is deployed to an Amazon EC2 instance. The application requires read-only permissions to a table that is named Cars The EC2 instance has an attached IAM role that contains the following IAM policy.
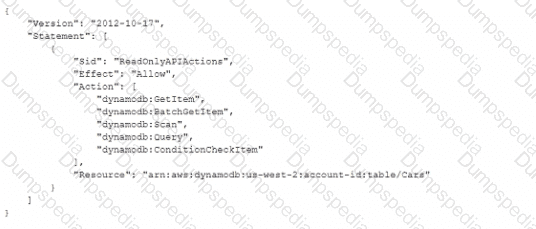
When the application tries to read from the Cars table, an Access Denied error occurs.
How can the developer resolve this error?
A company's application has an AWS Lambda function that processes messages from loT devices. The company wants to monitor the Lambda function to ensure that the Lambda function is meeting its required service level agreement (SLA).
A developer must implement a solution to determine the application's throughput in near real time. The throughput must be based on the number of messages that the Lambda function receives and processes in a given time period. The Lambda function performs initialization and post-processing steps that must not factor into the throughput measurement.
What should the developer do to meet these requirements?
A company is preparing to migrate an application to the company's first AWS environment Before this migration, a developer is creating a proof-of-concept application to validate a model for building and deploying container-based applications on AWS.
Which combination of steps should the developer take to deploy the containerized proof-of-concept application with the LEAST operational effort? (Select TWO.)
A developer is building an application on a fleet of Amazon EC2 Linux instances that run the Apache web server. The application must send API calls that contain sensitive customer data to a second fleet of Linux instances that also run Apache. The two fleets are deployed in peered VPCs within the same AWS account and AWS Region.
All sensitive data must be encrypted in transit.
Which solution will meet these requirements in the MOST operationally efficient way?
A developer is trying to make API calls using the AWS SDK. The IAM user credentials used by the application require multi-factor authentication for all API calls.
Which method should the developer use to access the multi-factor authentication-protected API?
An application that runs on AWS receives messages from an Amazon Simple Queue Service (Amazon SQS) queue and processes the messages in batches. The
application sends the data to another SQS queue to be consumed by another legacy application. The legacy system can take up to 5 minutes to process some transaction data.
A developer wants to ensure that there are no out-of-order updates in the legacy system. The developer cannot alter the behavior of the legacy system.
Which solution will meet these requirements?
A company stores customer credit reports in an Amazon S3 bucket. An analytics service uses standard Amazon S3 GET requests to access the reports.
A developer must implement a solution to redact personally identifiable information (PII) from the reports before the reports reach the analytics service.
Which solution will meet this requirement with the MOST operational efficiency?
A company's developer has deployed an application in AWS by using AWS CloudFormation. The CloudFormation stack includes parameters in AWS Systems Manager Parameter Store that the application uses as configuration settings. The application can modify the parameter values.
When the developer updated the stack to create additional resources with tags, the developer noted that the parameter values were reset and that the values ignored the latest changes made by the application. The developer needs to change the way the company deploys the CloudFormation stack. The developer also needs to avoid resetting the parameter values outside the stack.
Which solution will meet these requirements with the LEAST development effort?
A developer is building an API that uses an Amazon CloudFront distribution to forward requests to an AWS Lambda function URL. The developer must ensure that the function URL can be accessed only through the CloudFront distribution and not directly.
Which solution will meet this requirement?
A developer updates an AWS Lambda function that an Amazon API Gateway API uses. The API is the backend for a web application.
The developer needs to test the updated Lambda function before deploying the Lambda function to production. The testing must not affect any production users of the web application.
Which solution will meet these requirements in the MOST operationally efficient way?
A developer is investigating recent performance bottlenecks within a company's distributed web application that runs on various AWS services, including Amazon EC2 and Amazon DynamoDB.
How can the developer determine the length of time of the application's calls to the various downstream AWS services?
An Amazon Simple Queue Service (Amazon SQS) queue serves as an event source for an AWS Lambda function In the SQS queue, each item corresponds to a video file that the Lambda function must convert to a smaller resolution The Lambda function is timing out on longer video files, but the Lambda function's timeout is already configured to its maximum value
What should a developer do to avoid the timeouts without additional code changes'?
An developer is building a serverless application by using the AWS Serverless Application Model (AWS SAM). The developer is currently testing the application in a development environment. When the application is nearly finsihed, the developer will need to set up additional testing and staging environments for a quality assurance team.
The developer wants to use a feature of the AWS SAM to set up deployments to multiple environments.
Which solution will meet these requirements with the LEAST development effort?
A company uses a custom root certificate authority certificate chain (Root CA Cert) that is 10 KB in size generate SSL certificates for its on-premises HTTPS endpoints. One of the company’s cloud based applications has hundreds of AWS Lambda functions that pull date from these endpoints. A developer updated the trust store of the Lambda execution environment to use the Root CA Cert when the Lambda execution environment is initialized. The developer bundled the Root CA Cert as a text file in the Lambdas deployment bundle.
After 3 months of development the root CA Cert is no longer valid and must be updated. The developer needs a more efficient solution to update the Root CA Cert for all deployed Lambda functions. The solution must not include rebuilding or updating all Lambda functions that use the Root CA Cert. The solution must also work for all development, testing and production environment. Each environment is managed in a separate AWS account.
When combination of steps Would the developer take to meet these environments MOST cost-effectively? (Select TWO)
A developer at a company needs to create a small application mat makes the same API call once each flay at a designated time. The company does not have infrastructure in the AWS Cloud yet, but the company wants to implement this functionality on AWS.
Which solution meets these requirements in the MOST operationally efficient manner?
A developer needs to deploy an application running on AWS Fargate using Amazon ECS The application has environment variables that must be passed to a container for the application to initialize.
How should the environment variables be passed to the container?
A developer maintains an Amazon API Gateway REST API. Customers use the API through a frontend UI and Amazon Cognito authentication.
The developer has a new version of the API that contains new endpoints and backward-incompatible interface changes. The developer needs to provide beta access to other developers on the team without affecting customers.
Which solution will meet these requirements with the LEAST operational overhead?
A developer is making changes to a custom application that uses AWS Elastic Beanstalk.
Which solutions will update the Elastic Beanstalk environment with the new application version after the developer completes the changes? (Select TWO.)
A developer has designed an application to store incoming data as JSON files in Amazon S3 objects. Custom business logic in an AWS Lambda function then transforms the objects, and the Lambda function loads the data into an Amazon DynamoDB table. Recently, the workload has experienced sudden and significant changes in traffic. The flow of data to the DynamoDB table is becoming throttled.
The developer needs to implement a solution to eliminate the throttling and load the data into the DynamoDB table more consistently.
Which solution will meet these requirements?
A company is building a serverless application composed of multiple AWS Lambda functions. The company wants to accelerate feature development without adding staff or reducing quality. The solution must improve unit tests and code reviews, integrate with the existing IDE, and require no new infrastructure.
Which solution will meet these requirements?
A company hosts its application in the us-west-1 Region. The company wants to add redundancy in the us-east-1 Region. The application secrets are stored in AWS Secrets Manager in us-west-1. A developer needs to replicate the secrets to us-east-1.
Which solution will meet this requirement?
A developer is designing a full-stack serverless application. Files for the website are stored in an Amazon S3 bucket. AWS Lambda functions that use Amazon API Gateway endpoints return results from an Amazon DynamoDB table.
The developer must create a solution that securely provides registration and authentication for the application while minimizing the amount of configuration.
Which solution meets these requirements?
A company has a social media application that receives large amounts of traffic User posts and interactions are continuously updated in an Amazon RDS database The data changes frequently, and the data types can be complex The application must serve read requests with minimal latency
The application's current architecture struggles to deliver these rapid data updates efficiently The company needs a solution to improve the application's performance.
Which solution will meet these requirements'?
A developer manages a website that distributes its content by using Amazon CloudFront. The website's static artifacts are stored in an Amazon S3 bucket.
The developer deploys some changes and can see the new artifacts in the S3 bucket. However, the changes do not appear on the webpage that the CloudFront distribution delivers.
How should the developer resolve this issue?
A developer is building an application that processes a stream of user-supplied data. The data stream must be consumed by multiple Amazon EC2-based processing applications in parallel and in real time. Each processor must be able to resume without losing data if there is a service interruption. The application architect plans to add other processors in the near future and wants to minimize the amount of data duplication involved.
Which solution will satisfy these requirements?
A company has point-of-sale devices across thousands of retail shops that synchronize sales transactions with a centralized system. The system includes an Amazon API Gateway API that exposes an AWS Lambda function. The Lambda function processes the transactions and stores the transactions in Amazon RDS for MySQL. The number of transactions increases rapidly during the day and is near zero at night.
How can a developer increase the elasticity of the system MOST cost-effectively?
A company is developing a serverless application by using AWS Lambda functions. One of the Lambda functions needs to access an Amazon RDS DB instance. The DB instance is in a private subnet inside a VPC.
The company creates a role that includes the necessary permissions to access the DB instance. The company then assigns the role to the Lambda function. A developer must take additional action to give the Lambda function access to the DB instance.
What should the developer do to meet these requirements?
An 1AM role is attached to an Amazon EC2 instance that explicitly denies access to all Amazon S3 API actions. The EC2 instance credentials file specifies the 1AM access key and secret access key, which allow full administrative access.
Given that multiple modes of 1AM access are present for this EC2 instance, which of the following is correct?
A developer received the following error message during an AWS CloudFormation deployment:
Which action should the developer take to resolve this error?
A developer is designing a fault-tolerant environment where client sessions will be saved.
How can the developer ensure that no sessions are lost if an Amazon EC2 instance fails?
A company is running a custom web application on Amazon EC2 instances behind an Application Load Balancer. The instances run in an Auto Scaling group. The company's development team is using AWS CloudFormation to deploy all the services. The application is time-consuming to install and configure when the development team launches a new instance.
Which combination of steps should a developer take to optimize the performance when a new instance is launched? (Select TWO.)
A developer is working on an ecommerce website The developer wants to review server logs without logging in to each of the application servers individually. The website runs on multiple Amazon EC2 instances, is written in Python, and needs to be highly available
How can the developer update the application to meet these requirements with MINIMUM changes?
A developer needs to store configuration variables for an application. The developer needs to set an expiration date and time for me configuration. The developer wants to receive notifications. Before the configuration expires. Which solution will meet these requirements with the LEAST operational overhead?
A company has a serverless application that uses Amazon API Gateway backed by AWS Lambda proxy integration. The company is developing several backend APIs. The company needs a landing page to provide an overview of navigation to the APIs.
A developer creates a new /LandingPage resource and a new GET method that uses mock integration.
What should the developer do next to meet these requirements?
A developer is building two microservices that communicate by using an Amazon SQS queue. The messages exchanged between the microservices contain sensitive information. The developer must ensure that the messages are encrypted at rest.
Which solution will meet these requirements?
A company needs to rapidly prototype a web application. However, the company has not yet designed the complete architecture.
A developer uses AWS Lambda functions to build three endpoints. A frontend team wants to test the endpoints while the team prototypes the frontend.
Which solution will meet these requirements with the LEAST operational overhead?
A developer is creating an AWS Lambda function in VPC mode An Amazon S3 event will invoke the Lambda function when an object is uploaded into an S3 bucket The Lambda function will process the object and produce some analytic results that will be recorded into a file Each processed object will also generate a log entry that will be recorded into a file.
Other Lambda functions. AWS services, and on-premises resources must have access to the result files and log file. Each log entry must also be appended to the same shared log file. The developer needs a solution that can share files and append results into an existing file.
Which solution should the developer use to meet these requirements?
A developer wants to add request validation to a production environment Amazon API Gateway API. The developer needs to test the changes
before the API is deployed to the production environment. For the test, the developer will send test requests to the API through a testing tool.
Which solution will meet these requirements with the LEAST operational overhead?
A developer wants to reduce risk when deploying a new version of an existing AWS Lambda function. To test the Lambda function, the developer needs to split the traffic between the existing version and the new version of the Lambda function.
Which solution will meet these requirements?
A company is planning to securely manage one-time fixed license keys in AWS. The company's development team needs to access the license keys in automaton scripts that run in Amazon EC2 instances and in AWS CloudFormation stacks.
Which solution will meet these requirements MOST cost-effectively?
A developer is creating an AWS Lambda function that needs network access to private resources in a VPC.
An application writes transactions to an Amazon DynamoDB table by using the PutItem operation. Each transaction has a unique transactionId. Sometimes duplicate transactions are received. The developer wants to ensure that a duplicate PutItem does not overwrite an existing item. Duplicate transactions are rare.
What is the MOST cost-effective solution?
A developer wants to store information about movies. Each movie has a title, release year, and genre. The movie information also can include additional properties about the cast and production crew. This additional information is inconsistent across movies. For example, one movie might have an assistant director, and another movie might have an animal trainer.
The developer needs to implement a solution to support the following use cases:
For a given title and release year, get all details about the movie that has that title and release year.
For a given title, get all details about all movies that have that title.
For a given genre, get all details about all movies in that genre.
Which data store configuration will meet these requirements?
A social media application stores millions of video clips in Amazon S3 and serves them to users worldwide. Traffic is highly variable and can spike to more than 10,000 PUT and GET requests per second. Users report poor video streaming quality.
Which solution will provide the LARGEST improvement in performance?
For a deployment using AWS Code Deploy, what is the run order of the hooks for in-place deployments?
A company uses Amazon API Gateway to expose a set of APIs to customers. The APIs have caching enabled in API Gateway. Customers need a way to invalidate the cache for each API when they test the API.
What should a developer do to give customers the ability to invalidate the API cache?
A developer has written the following IAM policy to provide access to an Amazon S3 bucket:
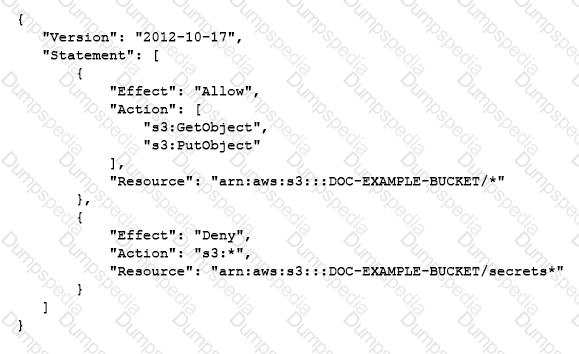
Which access does the policy allow regarding the s3:GetObject and s3:PutObject actions?
A developer is creating an AWS Lambda function that consumes messages from an Amazon Simple Queue Service (Amazon SQS) standard queue. The developer notices that the Lambda function processes some messages multiple times.
How should developer resolve this issue MOST cost-effectively?
A company is planning to use AWS CodeDeploy to deploy an application to Amazon Elastic Container Service (Amazon ECS) During the deployment of a new version of the application, the company initially must expose only 10% of live traffic to the new version of the deployed application. Then, after 15 minutes elapse, the company must route all the remaining live traffic to the new version of the deployed application.
Which CodeDeploy predefined configuration will meet these requirements?
A development team uses an Amazon DynamoDB table as a database for an application. The team notices errors and slowdowns in the application during peak usage hours. The slowdowns and errors occur during a surge of user logins. The application receives frequent write requests. Application logs indicate that write requests are being throttled.
The development team needs to reduce the application latency and resolve the throttling errors.
Which solutions will meet these requirements? (Select TWO.)
A healthcare company uses AWS Amplify to host a patient management system. The system uses Amazon API Gateway to expose RESTful APIs. The backend logic of the system is handled by AWS Lambda functions.
One of the Lambda functions receives patient data that includes personally identifiable information (PII). The Lambda function sends the patient data to an Amazon DynamoDB table. The company must encrypt all patient data at rest and in transit before the data is stored in DynamoDB.
A team has an Amazon API Gateway REST API that consists of a single resource and a GET method that is backed by an AWS Lambda integration.
A developer makes a change to the Lambda function and deploys the function as a new version. The developer needs to set up a process to test the new version of the function before using the new version in production. The tests must not affect the production REST API.
Which solution will meet these requirements with the LEAST operational overhead?
A developer is storing JSON files in an Amazon S3 bucket. The developer wants to securely share an object with a specific group of people.
How can the developer securely provide temporary access to the objects that are stored in the S3 bucket?
An application runs on multiple EC2 instances behind an ELB.
Where is the session data best written so that it can be served reliably across multiple requests?
An application is using Amazon Cognito user pools and identity pools for secure access. A developer wants to integrate the user-specific file upload and download features in the application with Amazon S3. The developer must ensure that the files are saved and retrieved in a secure manner and that users can access only their own files. The file sizes range from 3 KB to 300 MB.
Which option will meet these requirements with the HIGHEST level of security?
A developer created an AWS Lambda function to process data in an application. The function pulls large objects from an Amazon S3 bucket, processes the data, and loads the processed data into a second S3 bucket. Application users have reported slow response times. The developer checks the logs and finds that Lambda function invocations run much slower than expected. The function itself is simple and has a small deployment package. The function initializes quickly. The developer needs to improve the performance of the application. Which solution will meet this requirement with the LEAST operational overhead?
A developer writes an AWS Lambda function that processes new object uploads to an Amazon S3 bucket. The Lambda function runs for approximately 30 seconds. The function runs as expected under normal load conditions. Other Lambda functions in the AWS account also run as expected.
Occasionally, up to 500 new objects are written to the bucket every minute. Each new object write invokes the processing Lambda function during the high-volume periods through an event notification.
The developer must ensure that the processing function continues to run as expected during the high-volume periods.
Which solution will meet this requirement?
A company is developing a serverless application that requires storage of sensitive API keys as environment variables for various services. The application requires the automatic rotation of the encryption keys every year.
Which solution will meet these requirements with no development effort?
A developer is configuring an applications deployment environment in AWS CodePipeine. The application code is stored in a GitHub repository. The developer wants to ensure that the repository package's unit tests run in the new deployment environment. The deployment has already set the pipeline's source provider to GitHub and has specified the repository and branch to use in the deployment.
When combination of steps should the developer take next to meet these requirements with the least the LEAST overhead' (Select TWO).
A developer is troubleshooting an Amazon API Gateway API Clients are receiving HTTP 400 response errors when the clients try to access an endpoint of the API.
How can the developer determine the cause of these errors?
A developer manages an AWS Lambda function written in the latest version of .NET. The function processes data from an Amazon S3 bucket sporadically throughout the day. The function experiences cold start times of up to 10 seconds, negatively affecting latency-sensitive downstream workloads.
The developer needs to improve the function’s performance.
Which solution will meet this requirement?
A developer is setting up AWS CodePipeline for a new application. During each build, the developer must generate a test report.
Which solution will meet this requirement?
A developer has observed an increase in bugs in the AWS Lambda functions that a development team has deployed in its Node is application. To minimize these bugs, the developer wants to impendent automated testing of Lambda functions in an environment that Closely simulates the Lambda environment.
The developer needs to give other developers the ability to run the tests locally. The developer also needs to integrate the tests into the team's continuous integration and continuous delivery (Ct/CO) pipeline before the AWS Cloud Development Kit (AWS COK) deployment.
Which solution will meet these requirements?
A developer is creating AWS CloudFormation templates to manage an application's deployment in Amazon Elastic Container Service (Amazon ECS) through AWS CodeDeploy. The developer wants to automatically deploy new versions of the application to a percentage of users before the new version becomes available for all users.
How should the developer manage the deployment of the new version?
A company has three AWS Lambda functions written in Node.js. The Lambda functions include a mix of custom code and open source modules. When bugs are occasionally detected in the open source modules, all three Lambda functions must be patched.
What is the MOST operationally efficient solution to deploy a patched open source library for all three Lambda functions?
A company runs a batch processing application by using AWS Lambda functions and Amazon API Gateway APIs with deployment stages for development, user acceptance testing and production A development team needs to configure the APIs in the deployment stages to connect to third-party service endpoints.
Which solution will meet this requirement?
A company wants to migrate applications from its on-premises servers to AWS. As a first step, the company is modifying and migrating a non-critical application to a single Amazon EC2 instance. The application will store information in an Amazon S3 bucket. The company needs to follow security best practices when deploying the application on AWS.
Which approach should the company take to allow the application to interact with Amazon S3?
A company has an application that is based on Amazon EC2. The company provides API access to the application through Amazon API Gateway and uses Amazon DynamoDB to store the application's data. A developer is investigating performance issues that are affecting the application. During peak usage, the application is overwhelmed by a large number of identical data read requests that come through APIs. What is the MOST operationally efficient way for the developer to improve the application's performance?
A developer is building an application that includes an AWS Lambda function that is written in .NET Core. The Lambda function's code needs to interact with Amazon DynamoDB tables and Amazon S3 buckets. The developer must minimize the Lambda function's deployment time and invocation duration.
Which solution will meet these requirements?
A developer at a company needs to create a small application that makes the same API call once each day at a designated time. The company does not have infrastructure in the AWS Cloud yet, but the company wants to implement this functionality on AWS.
Which solution meets these requirements in the MOST operationally efficient manner?
A company wants to share information with a third party. The third party has an HTTP API endpoint that the company can use to share the information. The company has the required API key to access the HTTP API.
The company needs a way to manage the API key by using code. The integration of the API key with the application code cannot affect application performance.
Which solution will meet these requirements MOST securely?
A company is creating a new application that gives users the ability to upload and share short video files. The average size of the video files is 10 MB. After a user uploads a file, a message needs to be placed into an Amazon Simple Queue Service (Amazon SQS) queue so the file can be processed. The files need to be accessible for processing within 5 minutes.
Which solution will meet these requirements MOST cost-effectively?
A developer is creating an AWS Lambda function that searches for items from an Amazon DynamoDB table that contains customer contact information. The DynamoDB table items have the customer's email_address as the partition key and additional properties such as customer_type, name, and job_title.
The Lambda function runs whenever a user types a new character into the customer_type text input. The developer wants the search to return partial matches of the email_address property for a particular customer_type value. The developer does not want to recreate the DynamoDB table.
What should the developer do to meet these requirements?
A developer is creating an application that will give users the ability to store photos from their cellphones in the cloud. The application needs to support tens of thousands of users. The application uses an Amazon API Gateway REST API that is integrated with AWS Lambda functions to process the photos. The application stores details about the photos in Amazon DynamoDB.
Users need to create an account to access the application. In the application, users must be able to upload photos and retrieve previously uploaded photos. The photos will range in size from 300 KB to 5 MB.
Which solution will meet these requirements with the LEAST operational overhead?
A company has an application that uses Amazon Cognito user pools as an identity provider. The company must secure access to user records. The company has set up multi-factor authentication (MFA). The company also wants to send a login activity notification by email every time a user logs in.
What is the MOST operationally efficient solution that meets this requirement?
A company notices that credentials that the company uses to connect to an external software as a service (SaaS) vendor are stored in a configuration file as plaintext.
The developer needs to secure the API credentials and enforce automatic credentials rotation on a quarterly basis.
Which solution will meet these requirements MOST securely?
A developer is building various microservices for an application that will run on Amazon EC2 instances. The developer needs to monitor the end-to-end view of the requests between the microservices and debug any issues in the various microservices.
What should the developer do to accomplish these tasks?
A company is building a compute-intensive application that will run on a fleet of Amazon EC2 instances. The application uses attached Amazon
Elastic Block Store (Amazon EBS) volumes for storing data. The Amazon EBS volumes will be created at time of initial deployment. The
application will process sensitive information. All of the data must be encrypted. The solution should not impact the application's performance.
Which solution will meet these requirements?
A company with multiple branch locations has an analytics and reporting application. Each branch office pushes a sales report to a shared Amazon S3 bucket at a predefined time each day. The company has developed an AWS Lambda function that analyzes the reports from all branch offices in a single pass. The Lambda function stores the results in a database.
The company needs to start the analysis once each day at a specific time.
Which solution will meet these requirements MOST cost-effectively?
A company is creating an application that processes csv files from Amazon S3 A developer has created an S3 bucket The developer has also created an AWS Lambda function to process the csv files from the S3 bucket
Which combination of steps will invoke the Lambda function when a csv file is uploaded to Amazon S3? (Select TWO.)
A developer needs to set up an API to provide access to an application and its resources. The developer has a TLS certificate. The developer must have the ability to change the default base URL of the API to a custom domain name. The API users are distributed globally. The solution must minimize API latency.
An application uses an Amazon DynamoDB table to manage user profiles. A UserID attribute is the primary key of the table. The table also includes columns named Username, EmailAddress, RegistrationDate, Location, and Status.
The application needs to display a list of users from a specific location who registered after a specific date. Queries on the table must be optimized for efficiency.
Which solution will meet these requirements?
A cloud-based video surveillance company is developing an application that analyzes video files. After the application analyzes the files, the company can discard the files.
The company stores the files in an Amazon S3 bucket. The files are 1 GB in size on average. No file is larger than 2 GB. An AWS Lambda function will run one time for each video file that is processed. The processing is very I/O intensive, and the application must read each file multiple times.
Which solution will meet these requirements in the MOST performance-optimized way?
A developer is creating an application that will be deployed on IoT devices. The application will send data to a RESTful API that is deployed as an AWS Lambda function. The application will assign each API request a unique identifier. The volume of API requests from the application can randomly increase at any given time of day.
During periods of request throttling, the application might need to retry requests. The API must be able to handle duplicate requests without inconsistencies or data loss.
Which solution will meet these requirements?
A software company is launching a multimedia application. The application will allow guest users to access sample content before the users decide if they want to create an account to gain full access. The company wants to implement an authentication process that can identify users who have already created an account. The company also needs to keep track of the number of guest users who eventually create an account.
Which combination of steps will meet these requirements? {Select TWO.)
A developer is planning to migrate on-premises company data to Amazon S3. The data must be encrypted, and the encryption Keys must support automate annual rotation. The company must use AWS Key Management Service (AWS KMS) to encrypt the data.
When type of keys should the developer use to meet these requirements?
A company has an application that consists of different microservices that run inside an AWS account. The microservices are running in containers inside a single VPC. The number of microservices is constantly increasing. A developer must create a central logging solution for application logs.
Which solution will meet these requirements?
A developer is deploying a company's application to Amazon EC2 instances The application generates gigabytes of data files each day The files are rarely accessed but the files must be available to the application's users within minutes of a request during the first year of storage The company must retain the files for 7 years.
How can the developer implement the application to meet these requirements MOST cost-effectively?
A banking company is building an application for users to create accounts, view balances, and review recent transactions. The company integrated an Amazon API Gateway REST API with AWS Lambda functions. The company wants to deploy a new version of a Lambda function that gives customers the ability to view their balances. The new version of the function displays customer transaction insights. The company wants to test the new version with a small group of users before deciding whether to make the feature available for all users. Which solution will meet these requirements with the LEAST disruption to users?
A developer created an AWS Lambda function that accesses resources in a VPC. The Lambda function polls an Amazon Simple Queue Service (Amazon SOS) queue for new messages through a VPC endpoint. Then the function calculates a rolling average of the numeric values that are contained in the messages. After initial tests of the Lambda function, the developer found that the value of the rolling average that the function returned was not accurate.
How can the developer ensure that the function calculates an accurate rolling average?