As shown below,R1 and R2 have established a Level 2 neighbor relationship. The key configuration is as follows. The following statement about the routing entry of R2 is correct

ISIS protocol in broadcast network and P2P network, when router receives LSP, it needs to use PSNP confirms to ensure the synchronization of LSDB.
When the source IAT is allocated and there is a no-pat allocation parameter, which of the following statements is correct?
In the process of using the LACP protocol, which of the following descriptions is correct? (multiple choice)
Eth can be avoided by-Trunk interface frequently flaps interface due to physical link eth-trunk 1
lacp preempt enable
lacp preempt delay delay-time
You can configure the source IP address for load balancing in an enabled link aggregation group through the following commands: interface eth-trunk 1
load-balance src-dst-ip
Member interfaces can be removed from an enabled link aggregation group with the following command: interface GigabitEthermet0/0/1 shutdownwn
Two VTEPs in a VXLAN can determine a VXLAN tunnel, and the VXLAN tunnel between the VTEPs will be shared by all VNIs between the two NVEs.
Which of the following options use tunneling to communicate between IPv6 addresses?
As shown in the figure, there are three switches S1, SW2 and SW3, of which SW1 is the root bridge. The link between S1 and SW2 is congested, and SW2 cannot receive the configuration BPDU sent by the root bridge. What kind of spanning tree does the administrator need to configure? Protection mechanisms to prevent problems caused by link congestion?
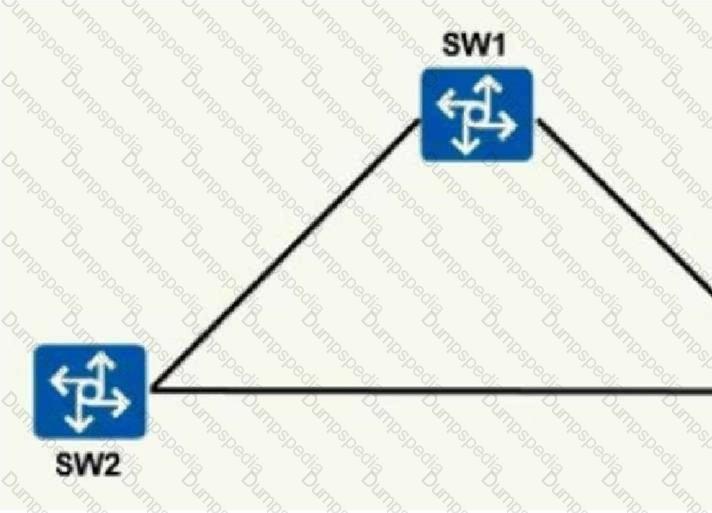
Which of the following descriptions about the process of sending and receiving data frames in switch interface Access mode is correct?
The HW device network administrator plans to migrate the multicast network from IGMPv2 to IGMPv3. What is the improvement of IGMPv3 compared to IGMPv2? .
In BGP4+, what is the content of the next hop network address field carried by the MP REACH NLRI attribute in the Update message?
Which type of address prefix in the following options indicates that the address is globally unique and globally routable among IPv6 unicast addresses, similar to the public address in IPv4?web address?
On a newly deployed routerWRED is configured on HW., which of the following descriptions about WRED features is correct? (multiple choice) ( confirmed)
When configuring ISIS area authentication, which ISIS packet will carry the authentication information?
The RSTP protocol provides a variety of protection functions. For example, when the edge port is configured in the protection state, the processing method after the edge port receives the BPDU message is:
Cross-device link aggregation enables reliable transmission of data traffic and mutual backup of stack member switches. However, due to the limited bandwidth of stack cables between stack devices, which of the following methods can be used to improve forwarding efficiency? (Single Choice)
Which of the following statements about the multicast address used by 0SPFv3 is correct? (Multiple choice)
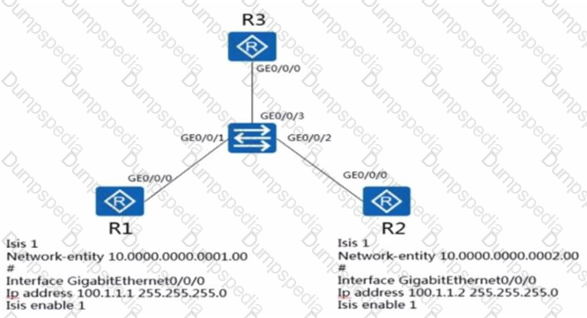
As shown in the figure, the ISIS overload bit is set in the configuration of router R3. Which of the following statements is correct?
the following aboutWhat are the wrong technical claims about URPF, IPSG and DAI?
When running 0SPFv3 on a Huawei router, the OSPFv3 process will automatically select an interface address as the
for the processRouter ID.
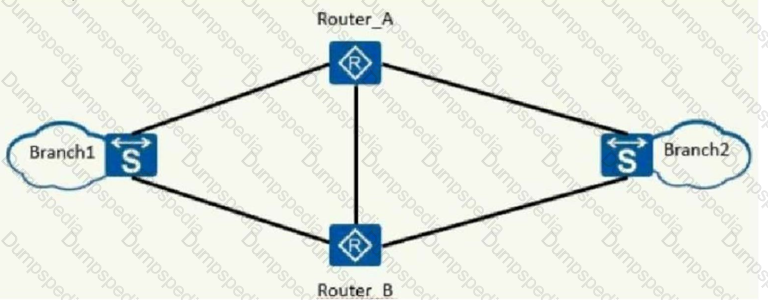
As shown in the figure, the router load shares the communication traffic between branch network 1 and branch network 2. In this case, configure the configuration on the physical interface of the router.
URPF must use loose mode to prevent source IP address spoofing attacks.
The MAC address table of the switch with default configuration is empty at this time, and the host A connected to the switch sends the first unicast data frame, then what operation will the switch perform after receiving the instruction?
RD is used to distinguish the same IP address in different VPNs. How many bits does RD contain?
Which properties meet the following two conditions:
BGP router A can choose toWhether the Update packet carries this attribute.
If Router B receives aAfter the Update message, Router B does not recognize the attribute, but also advertises the Update message containing this attribute to Router C. Router C may recognize and use this attribute. (multiple choice) ( confirmed)
OSPF fast convergence is an extended feature to improve the convergence speed of routing. The working principle of PRC (Partial Route Calculation) is that when the network topology changes, only the affected nodes are calculated. , so as to speed up the routing calculation
man-in-the-middle attack or IP/MAC SpoofingAttacks can lead to information leakage and other hazards, and are more common in intranets. To prevent man-in-the-middle attacks or IP/MAC SpoofingAttack, the configuration methods that can be taken are:
The following are about 802.1x authentication. What are the correct statements about RADIUS authentication and HWTACACS authentication?
When the ACL in the RP has multiple matching rules (rules) , which of the following statements is true about the matching order? ( confirmed)
In the intra-domain MPLS VPNI network, when the data packet enters the public network and is forwarded, it will be encapsulated with two layers of MPLS labels. The description of the two layers of labels in the following options is wrong?
BGP4+ is running between the two routers, and the neighbor relationship is normal, but the BGP routing table of the local router does not have any neighbor routing entries. The following possible reasons are:
A medium-sized campus network manages the network through the SNMP protocol. The campus has high network security. Which version of SMMP is recommended for management?
In an operator's MPLS VPN network, there are two devices PE1 and PE2 for MPLS VPN data forwarding. PE1 receives a private network route of 172.16.1.0/24 from the client, converts it to a VPNv4 route on PE1 and converts it to a VPNv4 route. Assign label 1027 to publish to PE2. The outgoing label of the MPLS LSR-ID from PE2 to PE1 is 1025. When the client on PE2 accesses back to 172.16.1.0/24, the frame sent by PE2, the inner and outer labels should be the combination of which of the following options?
Which of the following functions will affect the establishment of BGP neighbors?
Which of the following statements about the tail of ISIS protocol LSP packets is correct?
If the PIM-SM protocol is run in the multicast network, RP needs to be configured. The configuration methods of RP are divided into dynamic RP and static RP. The following description of RP configuration is correct:
In an intra-domain MPLS BGP VPN network, when a data packet enters the public network for forwarding, it will be encapsulated with two layers of MPLS labels. Which of the following descriptions about the two layers of labels is wrong? (single choice)
The host HW1 in the HW device network wants to join a video conference, what will the host do?
What is the multicast protocol that can generate a multicast distribution tree?
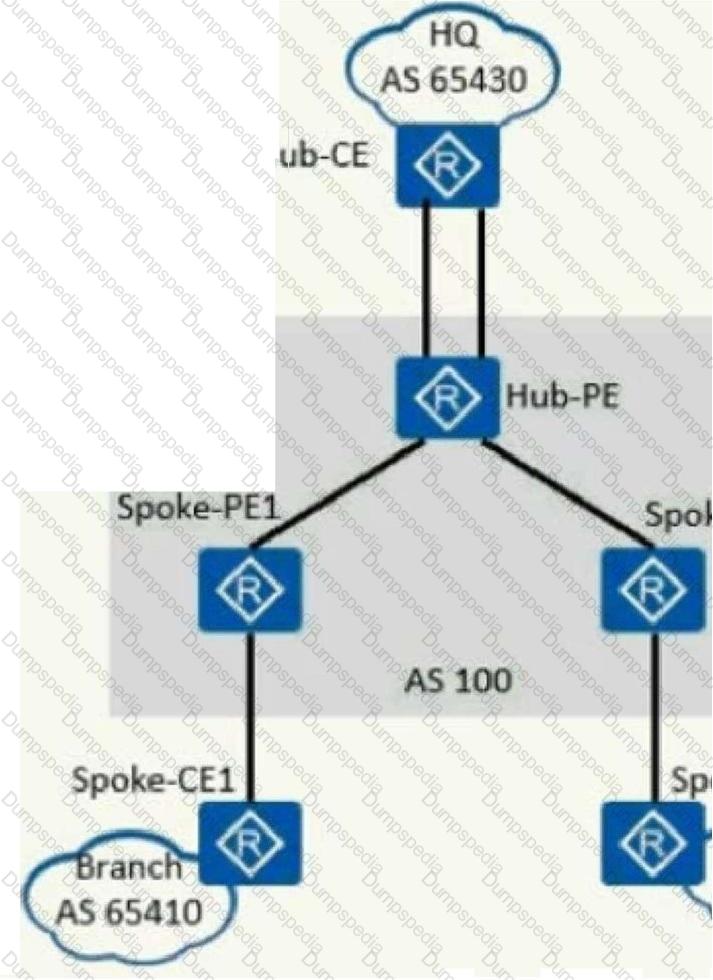
As shown in the figure, an enterprise hopes to realize the secure mutual access between the head office and each branch through MPLS/VPN, and requires that the VPN traffic of the branches must be forwarded through the head office to monitor the traffic. Which of the options described in this solution is wrong?
Which of the following statements about the format of OSPFv3 packets is correct?? (multiple choice)
run SNMS for NMPv1 ( Network Managementt What messages will Station) send to the Agent?
TION NO: 3
BGP EVPNWhich of the following types of packets are required to implement virtual machine migration in a distributed gateway scenario?
The OSPFv3 protocol is a separately developed protocol. It is somewhat different from OSPFv2. Regarding OSPFv3 is based on links rather than network segments, which of the following statements is wrong?
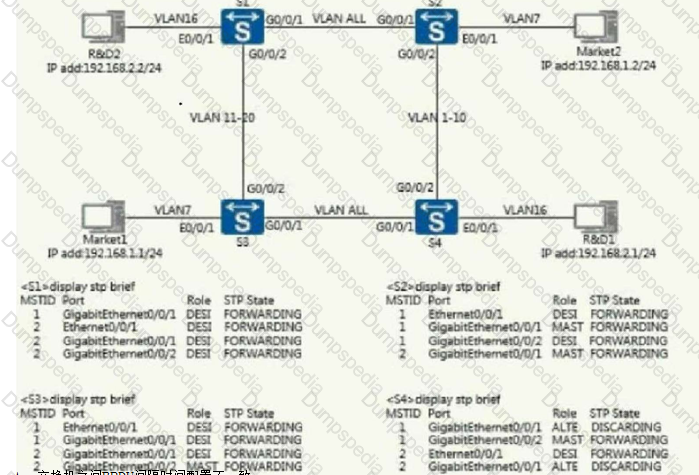
A company's two-layer phase network signature is shown in the figure. After the engineer has completed the configuration, it is found that the business between departments cannot communicate. The device status can be checked through the command as follows. Please determine the possible causes?
Subnets under different VPNs of VXLAN need to be accessed in the same way. The information of one of the subnets is as follows, RT 10:10 both under EVPN, RT 1000:1000 export, and RT 100:100 under VPN. Another subnet can be configured as ?
Which of the following descriptions is wrong about the address resolution function of NDP?
VLAN L3 Gateway is used to implement different V?The three-layer logical interface of ANW virtual network communication is?
NO: 236
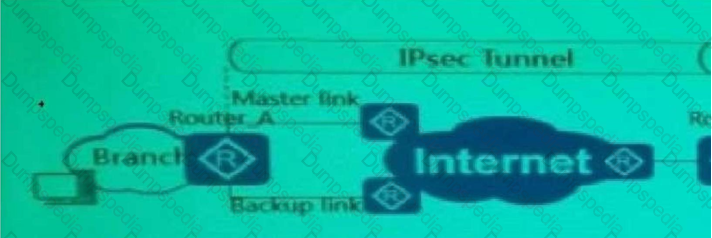
As shown in the figure, redundant links are used to establish IPse between the branch and the headquartersc VPN, and enable traffic from branch 1 on Router_B at the same time URPF, which of the following statements is true?
Use dual-bucket and dual-speed in traffic monitoring, the number of tokens in bucket C is TC,The number of tokens in the P bucket is TP. When a packet of length B comes in, which of the following statements is true?
[R1]ospf 1
[R1-ospf-1]area 2
[R1-ospf-1-area-0.0.0 2] network 10.0.13.1 0.0.0.0
As shown in the configuration, the administrator has configured OSPF on R1, but R1 cannot learn the routes of other routers, so the possible reason is ().
In Huawei equipment, when ISIS imports external routes and sets the external route label of the routing information, the ISIS MetThe ric type does not need to be modified, keep silentAccept it. ( confirmed)