Common storage networks include direct attached storage (DAS), network attached storage (NAS), and storage area network (SAN). SANs are divided into Fibre Channel storage area networks (FC SANs) and IP storage area networks (IP SANs).
Which of the following statements about FusionAccess for office automation (OA) isfalse?
For a small enterprise with no more than 100 employees, using the FusionAccess gateway and load balancer deployment solution for office scenarios, which of the following plans isrecommended?
Which of the following statements is false about a Virtual Image Management System (VIMS) file system?
Desktop users on the same FusionAccess can be authenticated using different domains.
Which of the following statements are true about system encapsulation and Sysprep (system encapsulation tool) for creating a full copy template on FusionAccess?
FusionCompute integrates physical CPU and memory resources on hosts into a compute resource pool and divides the resources into virtual CPU and memory resources for VMs. The compute resources actually used by a VM cannot exceed the specifications of the hardware resources on the host because the CPU and memory resources used by the VM must be provided by the same host. If this host malfunctions, the system automatically assigns another host to the VM to provide compute resources.
On FusionAccess, when creating afull copy, QuickPrep, or linked clone template, the template must be added to a domain.
The Central Processing Unit (CPU) is the computer's computing and control core. Mainly composed of an arithmetic logic unit (ALU) and a controller, it reads and executes data according to instructions.
In FusionCompute, which of the following isnota prerequisite for VM live migration?
Which of the following parameters are mandatory for quickly provisioning desktops on FusionAccess?
In Huawei FusionCompute, a VM running Linux is created. In this scenario, which of the following does the guest OS run in?
The essence of ___ technology is to convert physical devices into logical ones, thereby decoupling software from hardware.
In virtualization, KVM and Xen are typical hardware-assisted virtualization technologies. They implement virtualization based on kernel modules in the operating system.
The service modes for cloud computing include Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Which of the following statements arefalseabout the IaaS model?
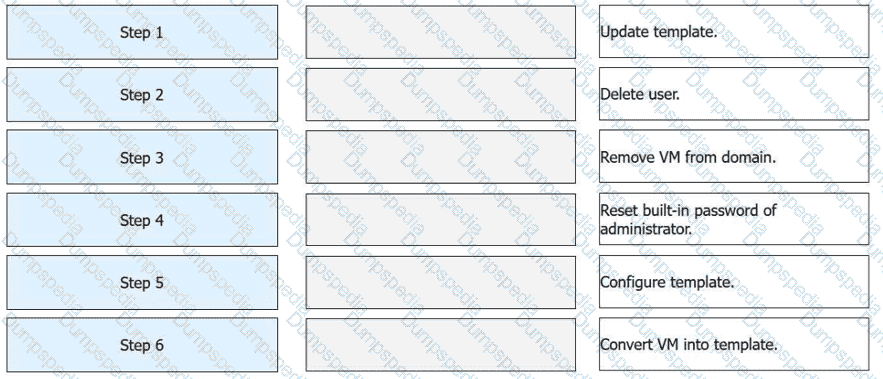
FusionAccess can use a provisioned full copy VM as a full copy VM template. Place the following operations in the correct order.
The kernel is an essential part of the operating system (OS). It is used to manage computer hardware resources and provide a system call interface to run upper-layer application programs.
A switch can learn the source and destination MAC addresses of traffic and add the addresses to a MAC address table. It cannot isolate collision domains.
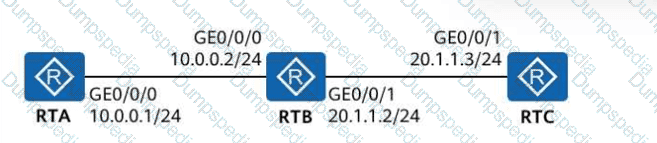
Which of the following statements arefalseabout the network shown in the figure?
FusionCompute supports the storage multipathing function to implement load balancing of storage data flows and improve reliability between storage devices and hosts. Which of the following statements about storage multipathing is true?
When an administrator uses alinked clone templateto quickly provision virtual machines (VMs) on FusionAccess, which of the following are thesteps of the quick provision process?
In FusionCompute, which of the following statements are false about security groups?
After installing infrastructure VMs, you must configure the virtualized environment and vAG/vLB so that FusionAccess can work properly. Which of the following statements aboutFusionAccess initializationaretrue?
FusionCompute supports the following memory overcommitment technologies: memory sharing, memory swapping, and memory ballooning. After host memory overcommitment is enabled in cluster resource control, one of the preceding memory overcommitment technologies needs to be selected.