The classification of cyber-attacks includes traffic-based attacks, scanning and snooping attacks, malformed packet attacks, and special packet attacks.
Using the virtual firewall technology, users on the two VPNs can log in to their private VPNs through the Root VFW on the public network to directly access private network resources. What are the following statements about the characteristics of the VPN multi-instance service provided by the firewall?
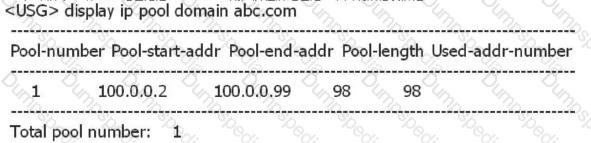
As shown below, the domain abc address pool is the address pool where the L2TP VPN user is located. What is wrong with the following statement?
Defense against the cache server The main method of DNS request flood is to use the DNS source authentication technology:
Which of the following states indicates that a BFD session has been successfully established?
Static fingerprint filtering function, different processing methods for different messages, the following statement is correct?
An enterprise network is as follows. At this time, server A cannot access server B. The administrator performs troubleshooting. It finds that server A can access firewall A, but cannot access firewall B. What is the method for administrators to use to troubleshoot problems?

The hot standby and IPSec functions are combined. Which of the following statements is correct?
The traffic limiting policy feature only supports the number of connections initiated by the specified IP or the number of connections received.
When the user logs in to the virtual gateway web page and prompts “Cannot display web page”, what is the possible cause of the failure?
The following figure shows the L2TP over IPSec application scenario. The client uses the pre-shared-key command to perform IPSec authentication. How should the IPSec security policy be configured on the LNS?
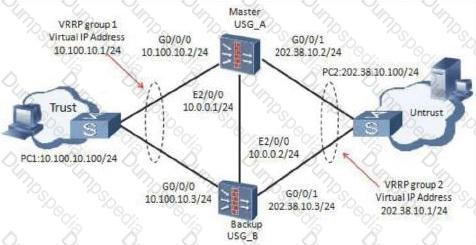
The enterprise network is as shown in the figure. On the USG_A and USG_B, hot standby is configured, and USG_A is the master device. The administrator wants to configure SSL VPN on the firewall so that branch employees can access the headquarters through SSL VPN. Which virtual gateway address should the SSL VPN be?
The default interval for sending VGMP hello packets is 1 second. That is, when the hello packet sent by the peer is not received within the range of three hello packets, the peer is considered to be faulty. Master status.
When there are a large number of BFD sessions in a system, what mode can be used to prevent BFD detection when the cost of sending BFD control packets periodically affects the normal operation of the system?
The IP address of the USG firewall GE0/0/0 is 192.168.0.1/24, and the firewall functions as the FTP server. The IP address of the PC host is 192.168.0.2/24. The GE0/0/0 interface of the firewall and the PC host are connected through the network cable. Connected, as shown below: PC (192.168.0.2/24)--GE0/0/0 USG. Which of the following commands can be used to complete the backup of the system configuration file vrpcfg.cfg?
The main function of URPF is to prevent network attack behavior based on destination address spoofing.
Avoid DHCP server spoofing attacks. DHCP snooping is usually enabled. What is the correct statement?
Which of the following does the virtual firewall technical feature not include?
Accessing the headquarters server through the IPSec VPN from the branch computer. The IPSec tunnel can be established normally, but the service is unreachable. What are the possible reasons?
On an Eth-Trunk interface, traffic load balancing can be implemented by configuring different weights on member links.
In the networking environment of dual-system hot backup and ip-link, which of the following configurations is the key configuration for ip-link and dual-system hot backup?
On the USG, you need to delete sslconfig.cfg in the hda1:/ directory. Which of the following commands can complete the operation?
The virtual firewall forwards multiple instances. The firewall has multiple routing tables and forwarding tables. The addresses are overlapped and are implemented on the same configuration interface. Users with configuration rights can configure and view all data.
According to the capture of the victim host, what kind of attack is this attack?
With regard to the Radius agreement, what are the following statements correct?
Configure the remote packet capture function on the USG to download the device to the device. You can use the FTP server to analyze the packet.
Which of the following configurations is mandatory when the IKE peer needs to be referenced to the IPSec policy template in the divquarters-branch-based IPSec VPN network (pre-shared key + traversal NAT)?
USG dual-machine hot standby must meet certain conditions and can be used below. What are the following statements correct?
An intranet has made a network, the old equipment is offline, the new network equipment is brought online, and after the service test, it is found that most of the original service traffic cannot work normally. What is the quickest way to restore the business?
The network of an enterprise is as follows. At this time, server A cannot access the web service of server B. The administrator performs troubleshooting and finds that there is no problem in the routing mode of firewall A. The corresponding routing table has been established, but the firewall mode of firewall A is set. error. What is the method used by the administrator to troubleshoot the problem?

In the DDoS attack defense, if the service learning function is used to find that there is no service or traffic of a certain service in normal traffic, you can use the blocking or traffic limiting method to defend against attacks on the Anti-DDoS device. .
Two USG firewalls failed to establish an IPSec VPN tunnel through the NAT traversal mode. Run the display ike sa command to view the session without any UDP 500 session. What are the possible reasons?
A user dials to the LNS of the company through L2TP over IPSec using the VPN client, and the final dialup fails. However, the debug ike all and debug l2tp all did not see any information on the LNS. The two stages of establishing ike failed. What are the reasons for the failure?
DDoS is an abnormal packet that an attacker sends a small amount of non-traffic traffic to the attack target (usually a server, such as DNS or WEB) through the network, so that the attacked server resolves the packet when the system crashes or the system is busy.
Virtual firewall virtualizes multiple logical firewalls on a physical firewall device and implements multiple instances?
The NAT/ASPF log in the session log and the DPI traffic monitoring log provide a “binary” output technology for this type of log. The use of binary input output can greatly reduce the impact on system performance, but The binary form output needs to be configured with the elog log management system.
If the IPSec policy is configured in the policy template and sub-policy mode, the firewall applies the policy template first and then applies the sub-policy.
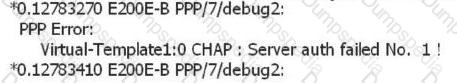
The IPSec establishment of a device is unsuccessful. The debug print information is as follows. What are the possible causes of the fault?
? %%01IKE/4/WARING(1):phase2:proposal mismatch,please check ipsec proposal configuration 0 34476900 %%01IKE/7/DEBUG(d) dropped message from 3.3.3.1 due to notification type NO_PROPOSAL_CHOSEN
In the dual-system hot backup, when the slave does not receive the hello packet of the HRP sent in the HRP hello packet period, the slave device is considered to be faulty.
The method of defending a FIN/RST flood attack is to perform a session check. The workflow is to discard the packet and then start the session check when the FIN/RST packet rate exceeds the threshold.
In the hot standby scenario, what is the correct statement about the primary and backup backups?
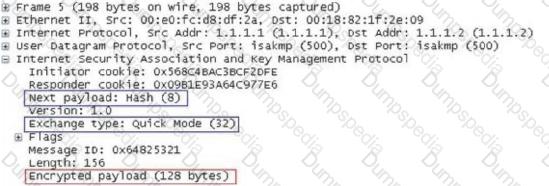
In the IKE V1 pre-shared key mode, what is the main role of the data captured in the following figure?
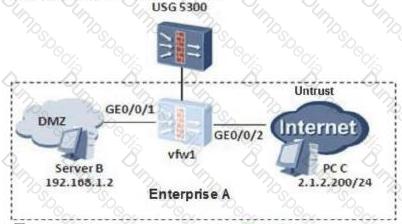
On the following virtual firewall network, the USG unified security gateway provides leased services to the enterprise. The VPN instance vfw1 is leased to enterprise A. The networking diagram is as follows. The PC C of the enterprise A external network user needs to access the intranet DMZ area server B through NAT. To achieve this requirement, what are the following key configurations?
In the client-initial mode, the L2TP dialup fails. From the debug information below, it can be seen that the most likely cause is the dialup failure.
The DHCP snooping function needs to maintain the binding table. What are the contents of the binding table?
The administrator can create vfw1 and vfw2 on the root firewall to provide secure multi-instance services for enterprise A and enterprise B, and configure secure forwarding policies between security zones of vfw1 and vfw2.
IPSec VPN uses digital certificates for authentication. It has the following steps: 1. verify the certificate signature; 2. find the certificate serial number in the CRL; 3. share the entity certificate between the two devices; 4. verify the validity period of the certificate; . Establish a VPN tunnel. Which of the following is correct?
In the active/standby mode of the USG dual-system hot standby, the service interface works at Layer 3, and the upstream and downstream routers are connected to the router. The administrator can view: USG_A status is HRP_M[USG_A], USG_B status is HRP_S[USG_B], current 15000+ session Table, every time a switchover occurs, all traffic is interrupted for a period of time, and seamless switching is impossible.
Site to Site IPSec VPN negotiation failed. Which of the following should be checked? 1. Network connectivity issues; 2. View the establishment of IKE phase 1 security associations and related configurations; 3. View the establishment of IKE phase 2 security associations and related configurations; 4. See if the security ACLs at both ends mirror each other.
In dual-system hot backup, the backup channel must be the primary interface on the interface board. Which type is not supported?
What are the scenarios in which the USG series firewall service port sends gratuitous ARPs when the following configurations are performed?
Which of the following protocol messages cannot be propagated in an IPSec tunnel by default?
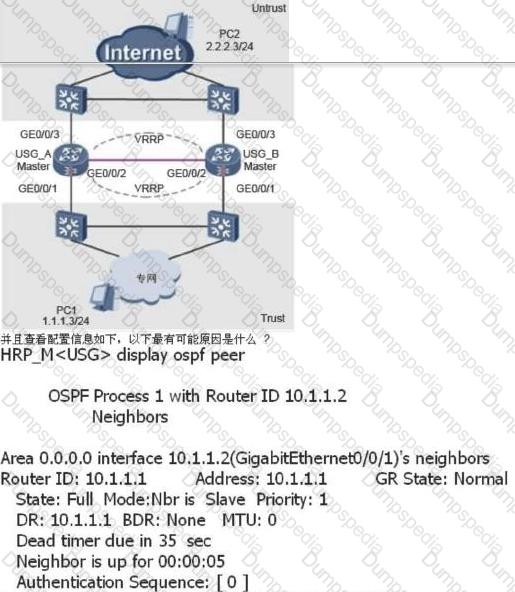
The dual-system hot standby networking environment is as shown in the following figure: VRRP group 1 and 2 are added to the VGMP management group, USG_A is the master device, and USG_B is the standby device. When the USG_A has a fault Status, such as power failure, the USG_B status is switched from Slave to Master. After the USG_A is faulty, its status is switched back to Master and the USG_B status is still Master. What is the reason for this now?
In the firewall DDoS attack defense technology, the Anti-DDoS device adopts seven layers of defense technology, and the description based on session defense is correct?