You need to deploy IntroSpect Analyzer in your existing network. You are planning to configure logs from
multiple systems around your network. Can this 3rd-party tool collect the logs and push them to Analyzer?
(Splunk Enterprise will allow push notifications.)
You deploy IntroSpect Analyzer in your existing network. You want to monitor email for suspect malware
activity. Would this action be supported by IntroSpect? (Deploy a supported DNP like Proofpoint Email Protection, and integrate with The IntroSpect Analyzer.)
You are one of the system administrators in your company, and you are assigned to monitor the IntroSpect
system for alarms. Is this a correct statement about alarms? (You must navigate to the IntroSpect Analyzer
Menu>Alerts page to see if there are any alarms.)
Refer to the exhibit.
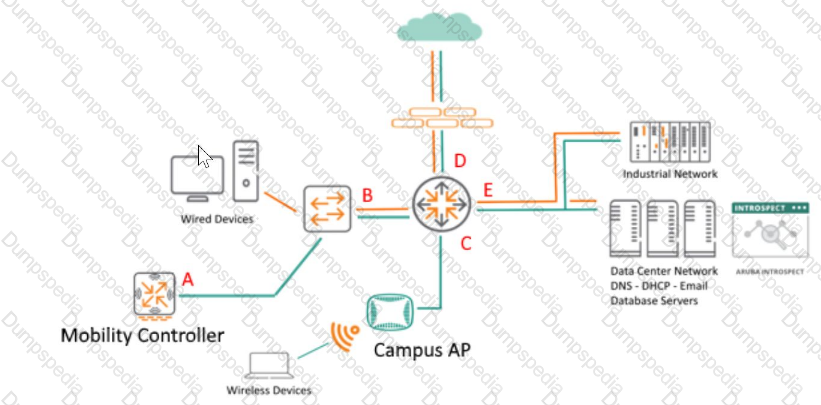
You are monitoring network traffic and considering DNS flow patterns. Where is a good location to place the Network Tap or Taps? (Location C.)
You are planning to configure ClearPass to send endpoint context to IntroSpect. You need to create a checklist of functions that must be enabled in ClearPass to support this. Is this an option that is required? (Ingress Event Processing.)
You are an administrator who made a few configuration changes in the IntroSpect Packet Processor, and arestart is required after those changes. Is this a valid method to restart the Packet Processor? (Issue thecommand #>shutdown –r now from the CLI of the Packet Processor.)
While investigating alerts you notice an entity has triggered a peer alert for visiting recruiting websites. Two days later the same user accessed the office for the first time in the late evening. You also noticed that they downloaded more data than their peers through the VPN session. Based on these conditions, is this a possible cause? (This user has just become a flight risk, and is now sending data off the network to use in their next job.)
While reviving the logs at a customer site you notice that one particular device is accessing multiple servers in the environment, using a number of different user accounts. When you QUESTION NO: the IT admin, they tell you that the computer is a JumpBox and running software used to monitor all of the servers in the environment.
Would this be a logical next step? (You can safely ignore this activity as this is normal behavior for a
JumpBox.)
Refer to the exhibit.
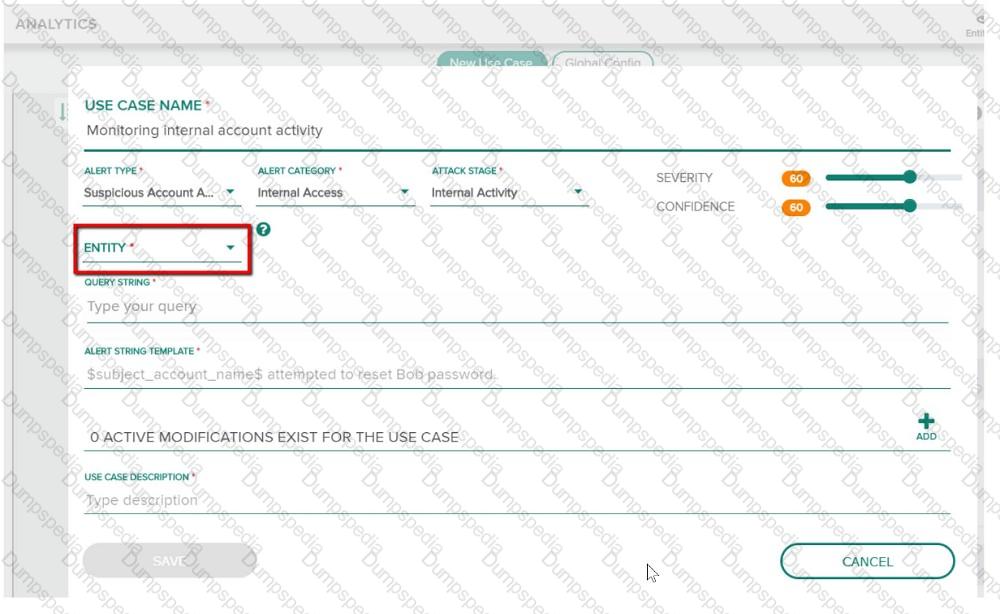
You have been assigned a task to monitor, analyze, and find those entities who are trying to access internal resources without having valid user credentials. You are creating an AD-based use case to look for this activity. Could you use this entity type to accomplish this? (Host name.)
A security analyst is monitoring the traffic which is accessing internal and external resources. They find
abnormal activity, indicating communication between a compromised internal user(host) and internal
infrastructure, and found a suspicious malware activity. Is this a correct attack stage classification for this
activity? (Infection.)
Refer to the exhibit.
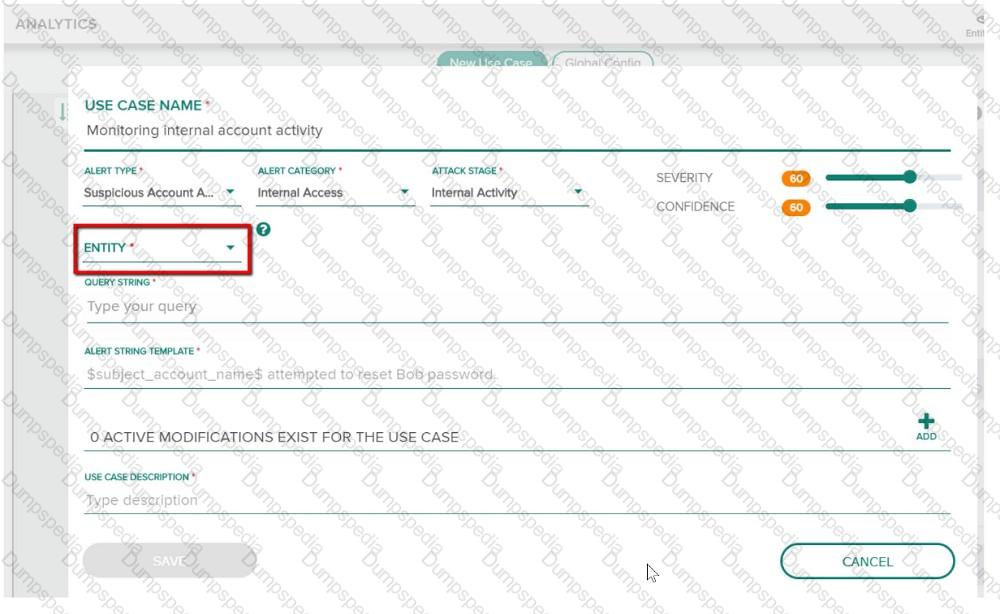
You have been assigned a task to monitor, analyze, and find those entities who are trying to access internal resources without having valid user credentials. You are creating an AD-based use case to look for this activity. Could you use this entity type to accomplish this? (Dest Host.)
Refer to the exhibit.
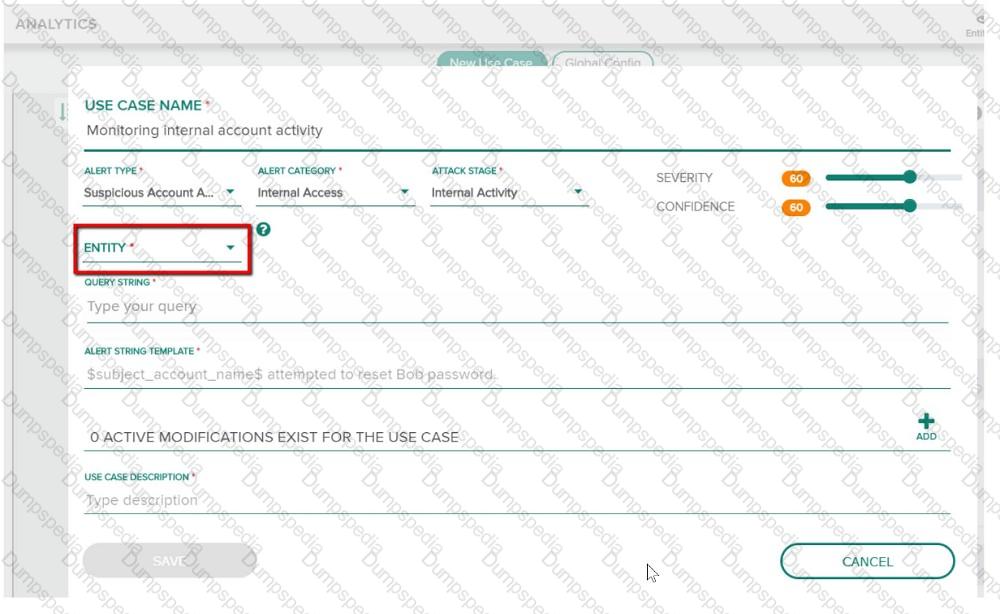
You have been assigned a task to monitor, analyze, and find those entities who are trying to access internal resources without having valid user credentials. You are creating an AD-based use case to look for this activity. Could you use this entity type to accomplish this? (Source Host.)
Would this be a proper correlation between entity and attack stage? (There is an alert for port scans by anentity, and you correlate that to a malware doing recon.)
Your company has found some suspicious conversations for some internal users. The security team suspects those users are communicating with entities in other countries. You have been assigned the task of identifying those users who are either uploading or downloading files from servers in other countries. Is this the best way to visualize conversations of suspected users in this scenario? (Visualizing Applications and Ports.)