Your IPsec VPN configuration uses two CoS forwarding classes to separate voice and data traffic. How many IKE security associations are required between the IPsec peers in this scenario?
SRX Series device enrollment with Policy Enforcer fails To debug further, the user issues the following command show configuration services security—intelligence url
https : //cloudfeeds . argon . juniperaecurity . net/api/manifeat. xml
and receives the following output:
What is the problem in this scenario?
Exhibit:
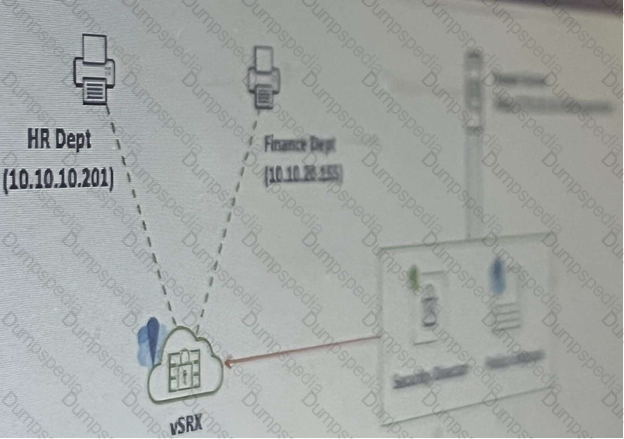
Referring to the exhibit, your company’s infrastructure team implemented new printers
To make sure that the policy enforcer pushes the updated Ip address list to the SRX.
Which three actions are required to complete the requirement? (Choose three )
You are asked to allocate security profile resources to the interconnect logical system for it to work properly.
In this scenario, which statement is correct?
You are asked to deploy Juniper atp appliance in your network. You must ensure that incidents and
alerts are sent to your SIEM.
In this scenario, which logging output format is supported?
Which two additional configuration actions are necessary for the third-party feed shown in the exhibit to work properly? (Choose two.)
You want traffic to avoid the flow daemon for administrative task.
In this scenario which two stateless service are available with selective stateless packet based service. (Choose Two)
You want to configure a threat prevention policy.
Which three profiles are configurable in this scenario? (Choose three.)
Which two features would be used for DNS doctoring on an SRX Series firewall? (Choose two.)
You have a webserver and a DNS server residing in the same internal DMZ subnet. The public Static NAT addresses for
the servers are in the same subnet as the SRX Series devices internet-facing interface. You implement DNS doctoring to
ensure remote users can access the webserver.Which two statements are true in this scenario? (Choose two.)
You are asked to determine if the 203.0.113.5 IP address has been added to the third-party security feed, DS hield, from Juniper Seclnte1. You have an SRX Series device that is using Seclnte1 feeds from Juniper ATP Cloud
Which command will return this information?
Exhibit
Which two statements are correct about the output shown in the exhibit? (Choose two.)
you configured a security policy permitting traffic from the trust zone to the untrust zone but your
traffic not hitting the policy.
In this scenario, which cli command allows you to troubleshoot traffic problem using the match criteria?
You want to enable inter-tenant communica????on with tenant system.
In this Scenario, Which two solutions will accomplish this task?
You are asked to download and install the IPS signature database to a device operating in chassis cluster mode. Which statement is correct in this scenario?
you must create a secure fabric in your company’s network
In this Scenario, Which three statements are correct? (Choose Three)
You are required to deploy a security policy on an SRX Series device that blocks all known Tor network IP addresses. Which two steps will fulfill this requirement? (Choose two.)
Click the Exhibit button.

Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)
You are asked to configure a security policy on the SRX Series device. After committing the policy, you receive the “Policy is out of sync between RE and PFE
Which command would be used to solve the problem?
Exhibit

An administrator wants to configure an SRX Series device to log binary security events for tenant systems.
Referring to the exhibit, which statement would complete the configuration?
You want to use selective stateless packet-based forwarding based on the source address.
In this scenario, which command will allow traffic to bypass the SRX Series device flow daemon?
Which two types of source NAT translations are supported in this scenario? (Choose two.)
Your Source NAT implementation uses an address pool that contains multiple IPv4 addresses Your users report that when they establish more than one session with an external application, they are prompted to authenticate multiple times External hosts must not be able to establish sessions with internal network hosts
What will solve this problem?
You are requested to enroll an SRX Series device with Juniper ATP Cloud.
Which statement is correct in this scenario?
You are deploying a virtualization solution with the security devices in your network Each SRX Series device must support at least 100 virtualized instances and each virtualized instance must have its own discrete administrative domain.
In this scenario, which solution would you choose?
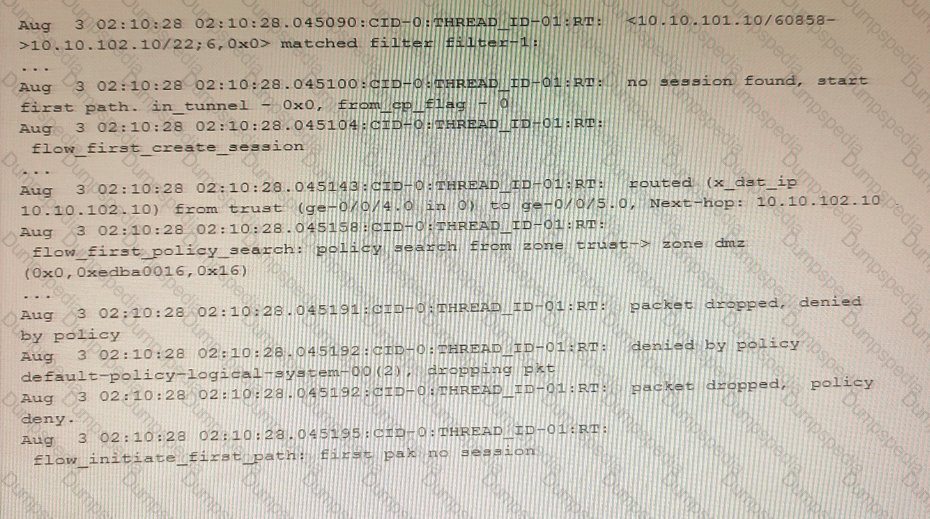
Exhibit

You are using traceoptions to verify NAT session information on your SRX Series device. Referring to the exhibit, which two statements are correct? (Choose two.)
Your company wants to use the Juniper Seclntel feeds to block access to known command and control servers, but they do not want to use Security Director to manage the feeds.
Which two Juniper devices work in this situation? (Choose two)