What is the minimum time a newly created Deduplication storage policy takes to apply to the VMs in the container?
Upon logging into Prism Central, an administrator notices high cluster latency.
How can the administrator analyze data with the least number of steps or actions?
When configuring Prism Central, which two log modules are able to forward messages to an external syslog server? (Choose two.
A recently configured cluster is leveraging NearSync with a recovery schedule of 15 minutes. It is noticed that the cluster is consistently transitioning in an Out of NearSyne.
What action should be taken to potentially address this issue?
Refer to exhibit:
 An administrator needs to update some images that were previously uploaded to their Nutanix cluster, while logged into Prism Element when trying to update the images, the update icon is not enabled.
An administrator needs to update some images that were previously uploaded to their Nutanix cluster, while logged into Prism Element when trying to update the images, the update icon is not enabled.
What could be the cause for this behavior?
A guest VM should be able to tolerate simultaneous failure of two nodes or drives.
What are the minimum requirements for the Nutanix cluster?
What is the proper sequence to perform a one-click upgrade to a Nutanix cluster?
Item instructions: For each procedure, indicate the order in which that procedure must take place to meet the item requirements. Not all procedures are valid. Identify any invalid procedures using the drop-down option.

Which three upgrades should an administrator be able to perform using Lifecycle Management? (Choose Three)
An administrator needs to provide access for a user to view real-time performance metric for all VMs on all clusters across the datacenter.
Which method accomplishes this with the least effort and ongoing maintenance?
An administrator has been notified by a user that a Microsoft SQL Server instance is not performing well.
When reviewing the utilization metrics, the following concerns are noted:
Memory consumption has been above 95% for several months
Memory consumption has been spiking to 100% for the last five days
Storage latency is 2ms.
When logging into Prism Central, how could the administrator quickly verify if this VM has performance bottlenecks?
Refer to Exhibit:
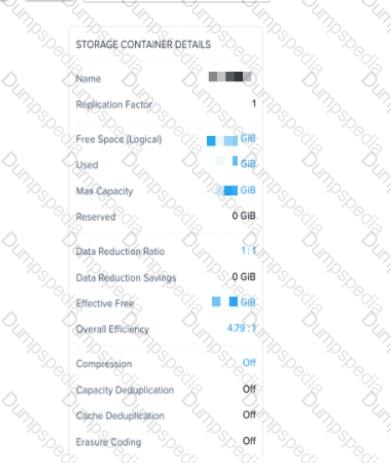
An administrator needs to enable inline deduplication for a pre-existing storage container. When trying to enable deduplication on the storage container. this feature is grayed-out.
What is the reason for this behavior?
Which best practice should be followed when creating a bond in a Nutanix cluster?
A cluster has RF2. The cluster loses two drives on different nodes in the same storage tier.
What is the effect on the replicas of the VMs?
When a VM is connected to a Nutanix managed network, when is the IP addressed assigned?
An administrator needs to ensure logs, alerts and information is consistent across clusters that are located in different countries.
Which service needs to be configured?
Refer to the exhibit.
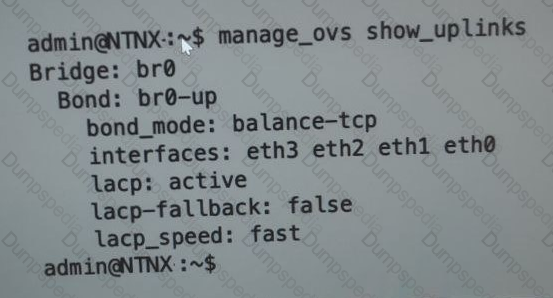
An administrator is adding a new node to a cluster. The node has been imaged to the same versions of AHV and AOS that the cluster running, configured with appropriate IP addresses, and br0-up has been configured the same the existing uplink bonds
When attempting to add the node to the cluster with the Expand Cluster function in Prism , the cluster is unable to find the new node.
Based on the above output from the new node, what is most likely the cause of this issue?
An administrator recently added new SSDs to a Nutanix cluster and knows the firmware will be out of date, Due to security constraints, the cluster does not have access to the Internet.
Which two steps must be completed to update the firmware? (Choose two.)
An administrator is concerned about the amount of data that a VM reading and writing to the storage fabric.
Which metric will provide that data?
Refer to the exhibit.

System Non-Root Partition Usage shows a warning or critical alert The administrator needs to change the frequency of checks and alerts to respond more quickly.
Where in Prism Element should the administrator change the frequency of checks and alerts?
An administrator initially performed a cluster Foundation using a flat switch without any VLAN configuration. After the Foundation, the administrator moved the dual 25Gb data ports and single 1Gb IPMI port to the actual switches with the below network configurations:
. All VLANs are tagged
. VLAN 1000 for CVM\Hypervisor traffic
· VLAN 1001 for User VM traffic
. VLAN 100 for IPMI traffic
After moving the IPMI network links, the administrator can no longer ping the IPMI IPs.
Which two changes does the administrator need to make? (Choose two.)
An administrator is not able to log into Prism Central by using a new Active Directory user account. After Logging with the local user, the administrator verified that Directory Services and Role Mapping setting are valid.
What is the most likely cause of this issue?
An administrator needs to periodically send information about cluster efficiency via email to a set of users.
What should be configured to accomplish this task?
In which two scenarios is an automated live migration likely to occur? (Choose two)
Which two capabilities does IPAM provide in a Nutanix networking configuration? (Choose two.)
Which component ensures uniform distribution of data throughout the cluster to eliminate hot spots and speed up rebuilds?
An administrator is working with Nutanix Support and needs to provide logs for troubleshooting an issue. The cluster is located in a secure environment. Data such as IP addresses and VM names cannot be shared.
Which method should be used to anonymize the log data sent to Nutanix Support?
A)

B)
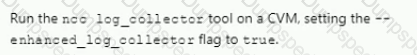
C)

D)

Which algorithm do snapshots and clones leverage to maximize efficiency and effectiveness?
An administrator is configuring data protection and DR for a multi-tier application. All VMs must be protected at the same time.
What must the administrator do to meet this requirement?
The Stargate service becomes unavailable on a single CVM on an AHV node. What is used to maintain I/O operations in the cluster?
An administrator is adding a node with a higher AOS release to an existing cluster.
What is the most efficient action an administrator should take to ensure it is in a supported state?
How should an administrator configure a custom alert for a specific VM in Prism?
An administrator logs into the Nutanix Support Portal and notices there is a new version of the LCM Framework available. In an effort ensure LCM is providing the latest features, the administrator would like to upgrade LCM.
How can the LCM Framework be upgraded?
Refer to Exhibit:
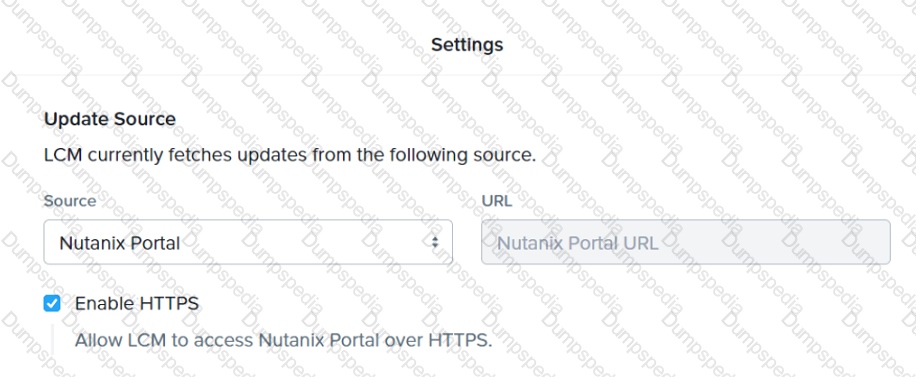
The Update Source for LCM has been configured as shown in the exhibit. Inventory is failing consistently.
What is the likely cause of this issue?
Refer to Exhibit:
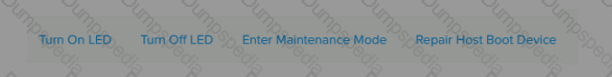
An administrator wants to replace and old node with a node of newer generation in a 3-node cluster. The administrator has already chosen the appropriate node. But unable to remove it from the cluster.
Why is the Remove Host option not shown in the exhibit?
An administrator needs to bring down a host in a Nutanix Cluster for maintenance reasons. The administrator puts the host in maintenance mode.
What should the administrator do to perform an orderly shutdown of the CVM?
Prism Central will be installed manually on an AHV cluster.
Which three disk images must be downloaded from the portal for the Prism Central VM? (Choose three.)
An administrator is reviewing performance of a core banking system that routinely has 20,000 concurrent users. During, business hours, the CPU on the applications servers runs at close to 100%. The administrator needs to determine if there is a performance issue specific to the app servers, the database servers, or all servers on the cluster.
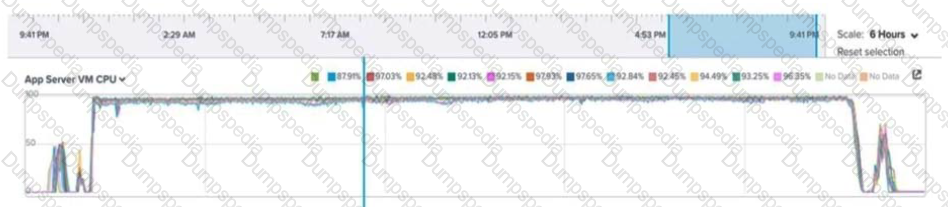
Which metrics should the administrator review in Prism Analysis Graphs?
A two-node ROBO cluster is configured with a witness VM.
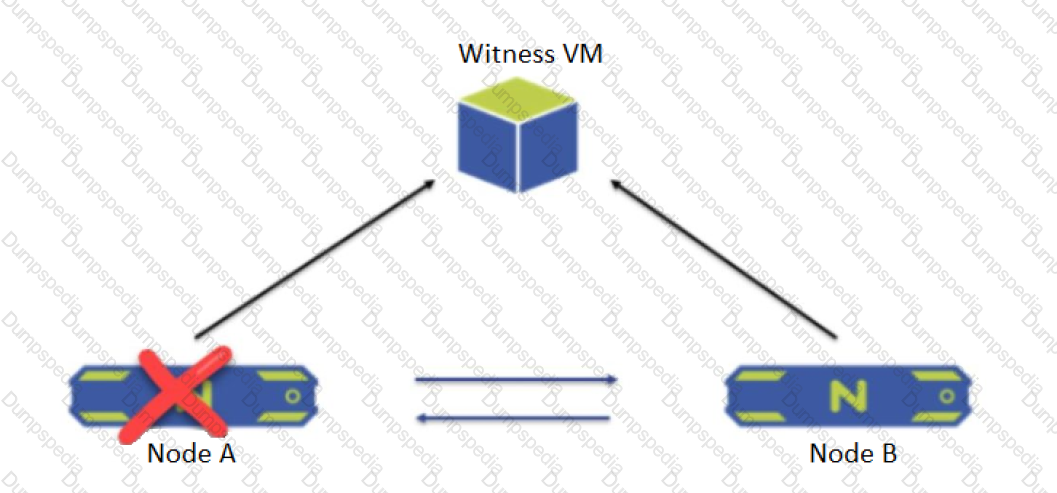
What happens when Node A goes down?
An administrator needs to relocate an AHV cluster to a new datacenter during a maintenance window. The cluster will use the same IPs in the new datacenter.
Which two steps should be taken to prepare for this task? (Choose two.)
Which two permission assignment tasks can be accomplished via Prism Element? (Choose two.)
When installing Nutanix Guest Tools (NGT) on an ESXi-hosted VM, which port should be enabled on the VM to allow communication with the NGT-Controller VM service?
An administrator needs to limit the amount of storage space that data stored in single container can consume.
Which action should the administrator take?
After logging into Prism Element, an administrator presses the letter A on the Keyboard.
What is the expected outcome of this input?
An administrator is setting up a Nutanix cluster and needs to configure the default VLAN.
Which configuration should the administrator choose?