Refer to the exhibit.
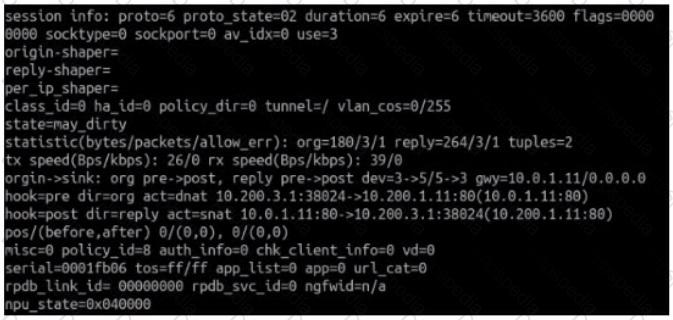
Which contains a session diagnostic output. Which statement is true about the session diagnostic output?
In an explicit proxy setup, where is the authentication method and database configured?
Which three criteria can a FortiGate use to look for a matching firewall policy to process traffic? (Choose three.)
Refer to the FortiGuard connection debug output.

Based on the output shown in the exhibit, which two statements are correct? (Choose two.)
Refer to the exhibits.
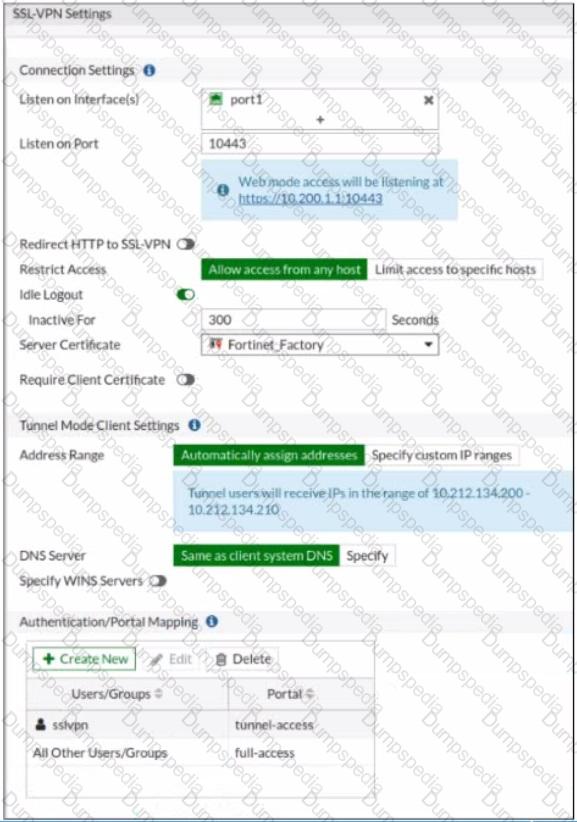

The SSL VPN connection fails when a user attempts to connect to it. What should the user do to successfully connect to SSL VPN?
7
Which two settings can be separately configured per VDOM on a FortiGate device? (Choose two.)
Refer to the exhibits.
Exhibit A shows the application sensor configuration. Exhibit B shows the Excessive-Bandwidth and Apple filter details.
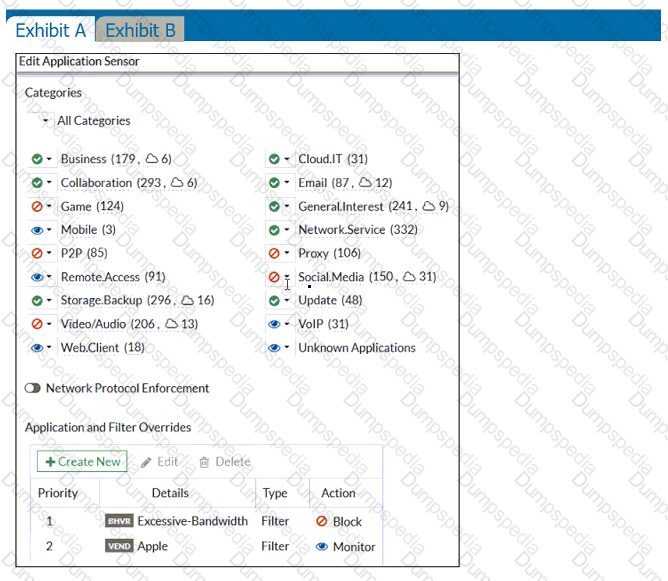
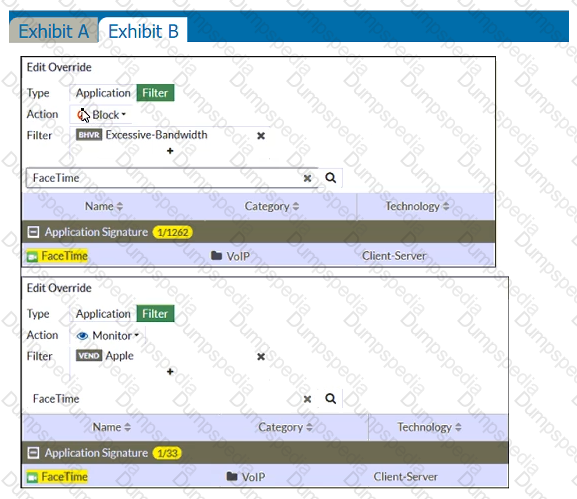
Based on the configuration, what will happen to Apple FaceTime if there are only a few calls originating or incoming?
16
FortiGate is configured as a policy-based next-generation firewall (NGFW) and is applying web filtering and application control directly on the security policy. Which two other security profiles can you apply to the security policy? (Choose two.)
94
An administrator observes that the port1 interface cannot be configured with an IP address. What can be the reasons for that? (Choose three.)
Refer to the exhibit.
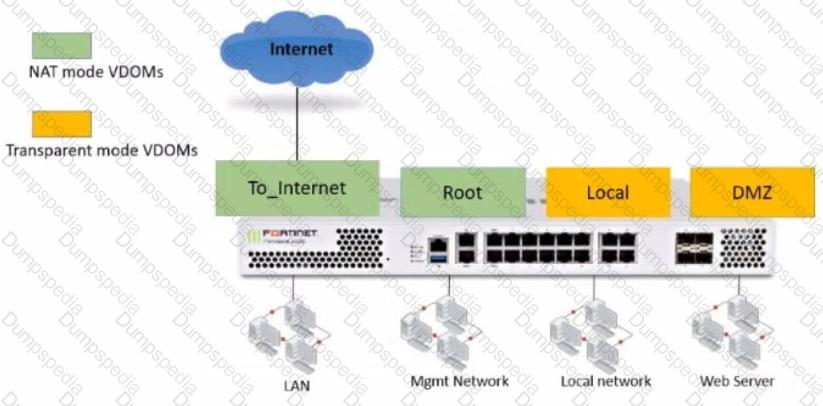
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are configured in transparent mode.
The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access the internet. The To_Internet VDOM is the only VDOM with internet access and is directly connected to ISP modem .
With this configuration, which statement is true?
49
A network administrator is configuring a new IPsec VPN tunnel on FortiGate. The remote peer IP address is dynamic. In addition, the remote peer does not support a dynamic DNS update service.
What type of remote gateway should the administrator configure on FortiGate for the new IPsec VPN tunnel to work?
Refer to the exhibit.
The exhibit shows the FortiGuard Category Based Filter section of a corporate web filter profile.
An administrator must block access to download.com, which belongs to the Freeware and Software Downloads category. The administrator must also allow other websites in the same category.
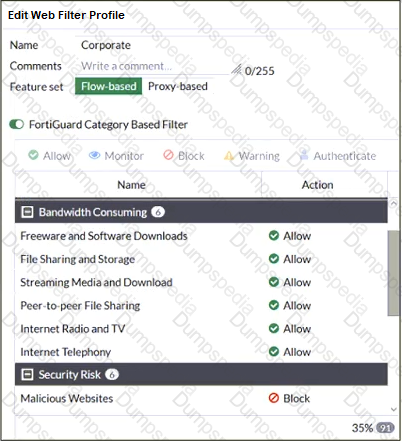
What are two solutions for satisfying the requirement? (Choose two.)
108
Which statement about the IP authentication header (AH) used by IPsec is true?
Which engine handles application control traffic on the next-generation firewall (NGFW) FortiGate?
FortiGate is operating in NAT mode and is configured with two virtual LAN (VLAN) subinterfaces added to the same physical interface.
In this scenario, what are two requirements for the VLAN ID? (Choose two.)
18
If the Issuer and Subject values are the same in a digital certificate, which type of entity was the certificate issued to?
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
Refer to the exhibits.
The exhibits show a network diagram and firewall configurations.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2. Remote-User1 must be able to access the Webserver. Remote-User2 must not be able to access the Webserver.


In this scenario, which two changes can the administrator make to deny Webserver access for Remote-User2? (Choose two.)
Refer to the exhibit showing a debug flow output.
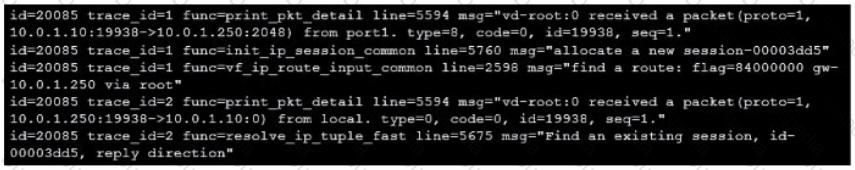
Which two statements about the debug flow output are correct? (Choose two.)
Refer to the exhibit.
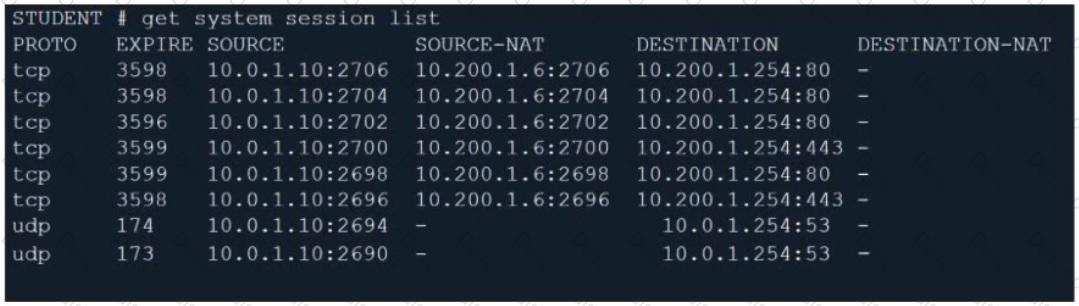
Which contains a session list output. Based on the information shown in the exhibit, which statement is true?
68
If the Services field is configured in a Virtual IP (VIP), which statement is true when central NAT is used?
Refer to the exhibit.
An administrator added a configuration for a new RADIUS server. While configuring, the administrator selected the Include in every user group option.

What is the impact of using the Include in every user group option in a RADIUS configuration?
104
Which three statements are true regarding session-based authentication? (Choose three.)
Refer to the exhibit.
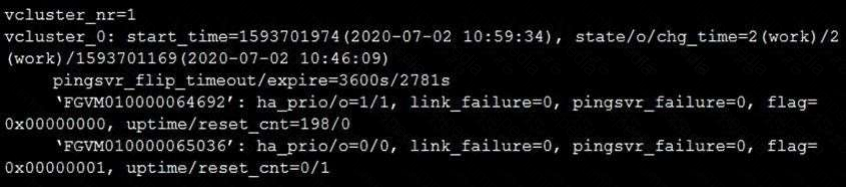
The exhibit displays the output of the CLI command: diagnose sys ha dump-by vcluster.
Which two statements are true? (Choose two.)
106
Which two actions can you perform only from the root FortiGate in a Security Fabric? (Choose two.)
109
Why does FortiGate keep TCP sessions in the session table for some seconds even after both sides
(client and server) have terminated the session?
Examine this FortiGate configuration:
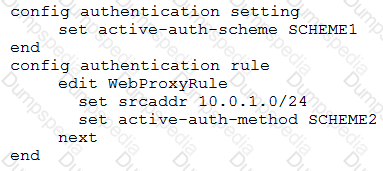
How does the FortiGate handle web proxy traffic coming from the IP address 10.2.1.200 that requires authorization?
What are two characteristics of FortiGate HA cluster virtual IP addresses? (Choose two.)
An administrator is configuring an Ipsec between site A and siteB. The Remotes Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192. 16. 1.0/24 and the remote quick mode selector is 192. 16.2.0/24. How must the administrator configure the local quick mode selector for site B?
Refer to the exhibit.
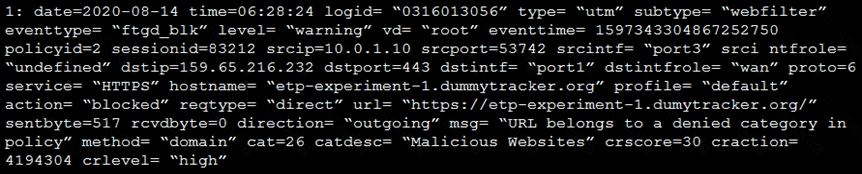
Based on the raw log, which two statements are correct? (Choose two.)
An employee needs to connect to the office through a high-latency internet connection.
Which SSL VPN setting should the administrator adjust to prevent SSL VPN negotiation failure?
Which statements about the firmware upgrade process on an active-active HA cluster are true? (Choose two.)
46
Which two types of traffic are managed only by the management VDOM? (Choose two.)
17
Refer to the exhibit.
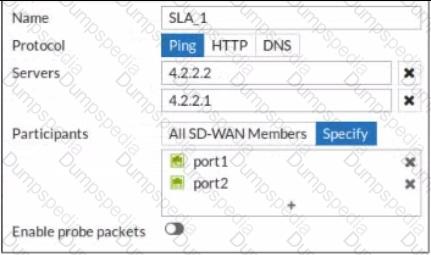
An administrator has configured a performance SLA on FortiGate, which failed to generate any traffic.
Why is FortiGate not sending probes to 4.2.2.2 and 4.2.2.1 servers? (Choose two.)
40
Which CLI command will display sessions both from client to the proxy and from the proxy to the servers?
When a firewall policy is created, which attribute is added to the policy to support recording logs to a FortiAnalyzer or a FortiManager and improves functionality when a FortiGate is integrated with these devices?
2
Which two statements are true when FortiGate is in transparent mode? (Choose two.)
31
Which CLI command allows administrators to troubleshoot Layer 2 issues, such as an IP address conflict?
Refer to the exhibits.
Exhibit A shows a topology for a FortiGate HA cluster that performs proxy-based inspection on traffic. Exhibit B shows the HA configuration and the partial output of the get system ha status command.
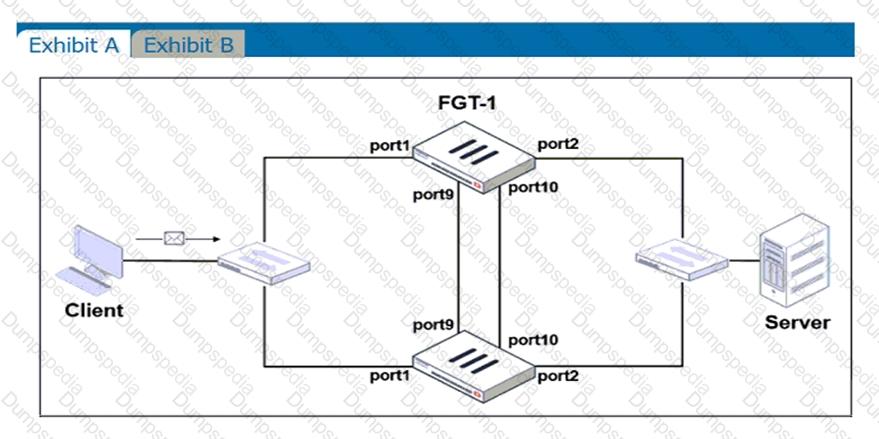
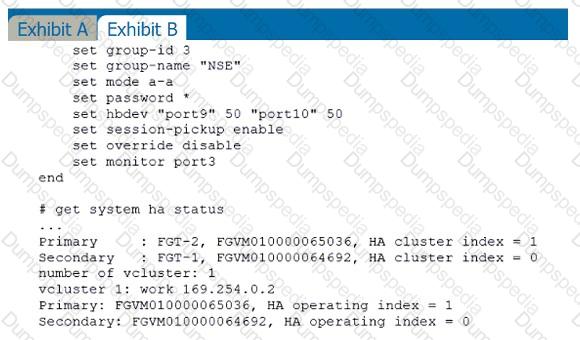
Based on the exhibits, which two statements about the traffic passing through the cluster are true? (Choose two.)
An administrator wants to simplify remote access without asking users to provide user credentials.
Which access control method provides this solution?
30
A team manager has decided that, while some members of the team need access to a particular website, the majority of the team does not Which configuration option is the most effective way to support this request?
On FortiGate, which type of logs record information about traffic directly to and from the FortiGate management IP addresses?