What is a key use case for FortiSASE Secure Internet Access (SIA) in an agentless deployment? (Choose one answer)
Which two statements correctly describe what happens when traffic matches the implicit SD-WAN rule? (Choose two answers)
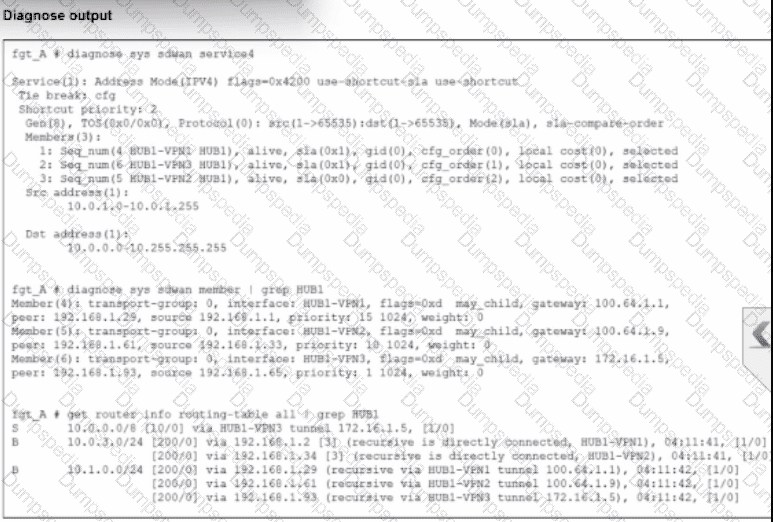
An administrator is troubleshooting SD-WAN on FortiGate. A device behind branch1_fgt generates traffic to the 10.0.0.0/8 network. The administrator expects the traffic to match SD-WAN rule ID 1 and be routed over HUB1-VPN1. However, the traffic is routed over HUB1-VPN3.
Based on the output shown in the exhibit, which two reasons, individually or together, could explain the observed behavior? (Choose two.)
Refer to the exhibit.

Which two statements about the Vulnerability summary dashboard in FortiSASE are correct? (Choose two.)
The IT team is wondering whether they will need to continue using MDM tools for future FortiClient upgrades.
What options are available for handling future FortiClient upgrades?