Refer to the exhibit which shows the output of an email transmission using a telnet session.

What are two correct observations about this SMTP session? (Choose two.)
A FortiMail is configured with the protected domain example.com.
On this FortiMail, which two envelope addresses are considered incoming? (Choose two.)
An organization has different groups of users with different needs in email functionality, such as address book access, mobile device access, email retention periods, and disk quotas.
Which FortiMail feature specific to server mode can be used to accomplish this?
Refer to the exhibit, which shows an inbound recipient policy.
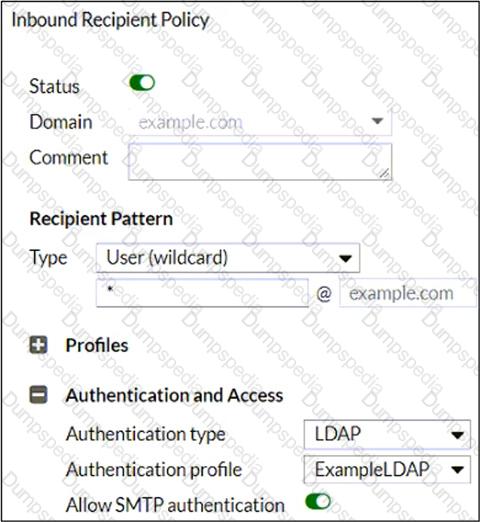
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
Refer to the exhibits which show a topology diagram (Topology), and a configuration element (Access Control Rule).
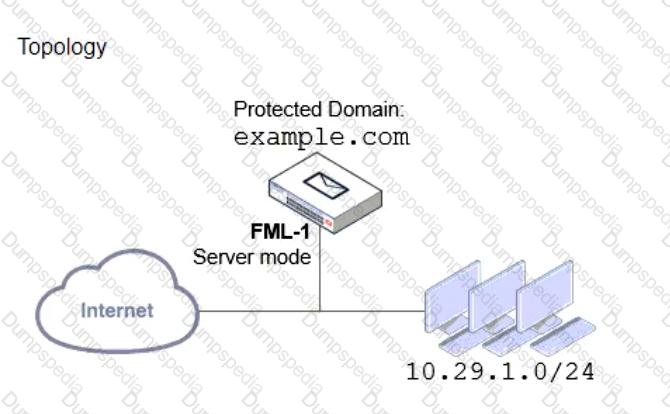
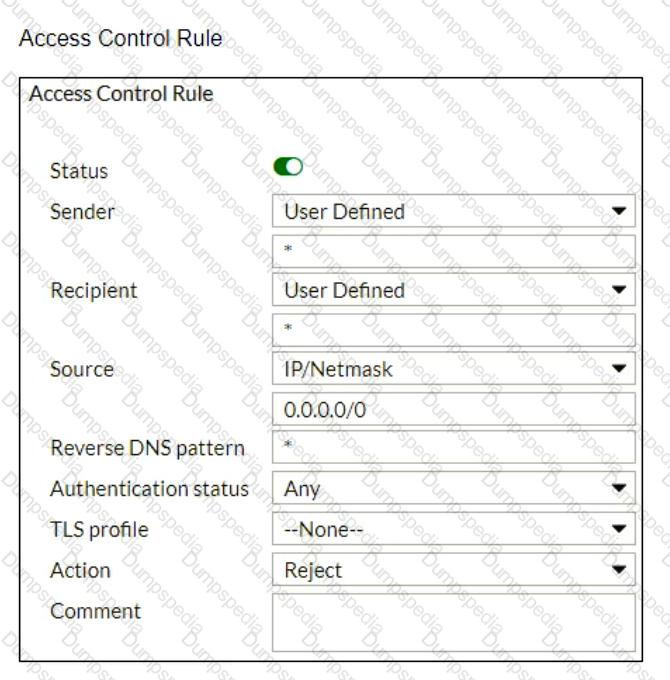
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain.
Which two settings should be used to configure the access receive rule? (Choose two.)