Your monitoring team reports performance issues with a web application hosted in Azure. You suspect that the bottleneck might be due to unexpected inbound traffic spikes.
Which method should you use to identify and analyze the traffic pattern?
You are experiencing intermittent connectivity issues in a FortiGate HA cluster deployed with Azure gateway load balancer. Traffic is being dropped when it passes through the cluster. What is the cause of the issue? (Choose one answer)1
Refer to the exhibit.

You deployed a FortiGate HA active-passive cluster in Microsoft Azure.
Which two statements regarding this particular deployment are true? (Choose two.)
Refer to the exhibit.
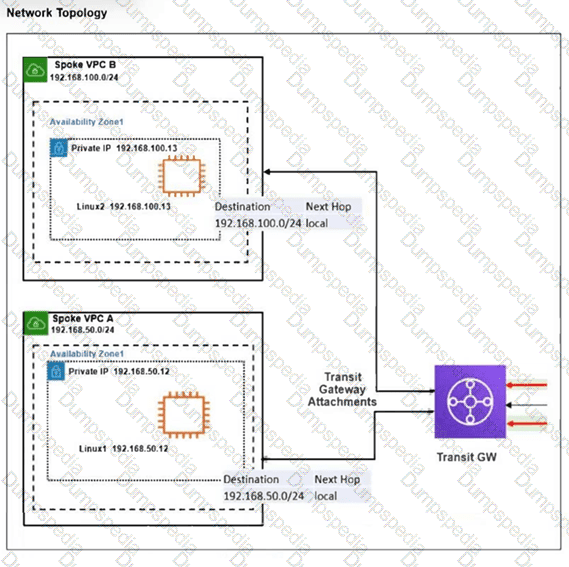
The exhibit shows a customer deployment of two Linux instances and their main routing table in Amazon Web Services (AWS). The customer also created a Transit Gateway (TGW) and two attachments. Which two steps are required to route traffic from Linux instances to the TGW? (Choose two answers)
Refer to the exhibit.
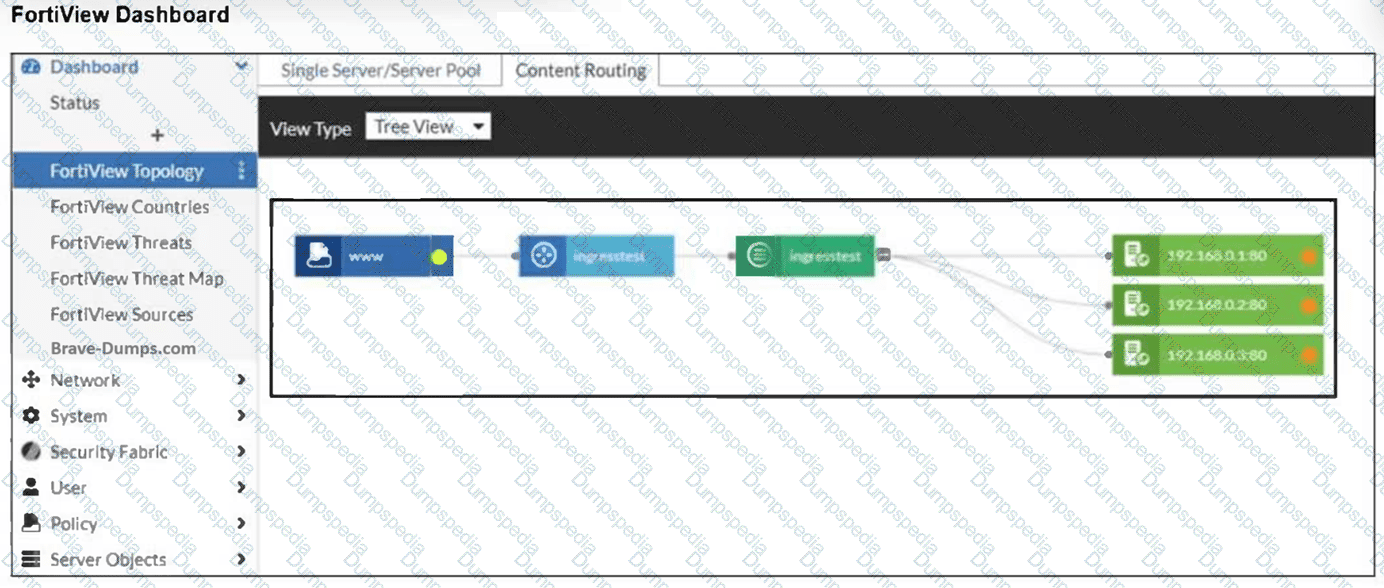
An administrator installed a FortiWeb ingress controller to protect a containerized web application. What is the reason for the status shown in FortiView? (Choose one answer)
Refer to the exhibit.
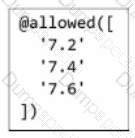
What is the purpose of this section of an Azure Bicep file?
You are using Ansible to modify the configuration of several FortiGate VMs. What is the minimum number of files you need to create, and in which file should you configure the target FortiGate IP addresses?
Refer to the exhibit.
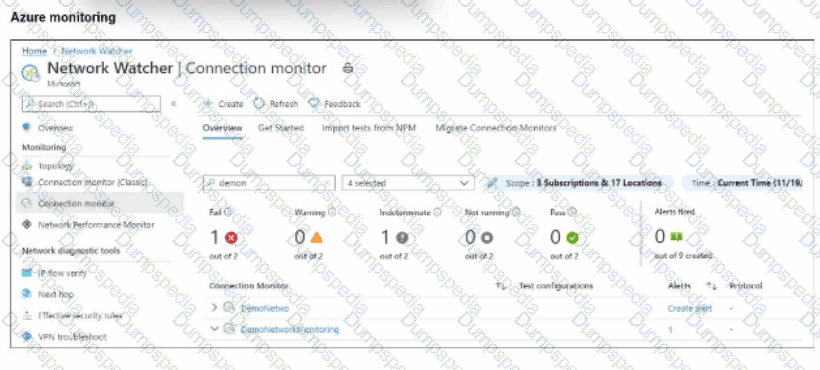
After analyzing the native monitoring tools available in Azure, an administrator decides to use the tool displayed in the exhibit.
Why would an administrator choose this tool?
A customer would like to use FortiGate fabric integration with FortiCNP. When adding a FortiGate VM to FortiCNP, which three mandatory configuration steps must you follow on FortiGate? (Choose three answers)
Refer to the exhibit.
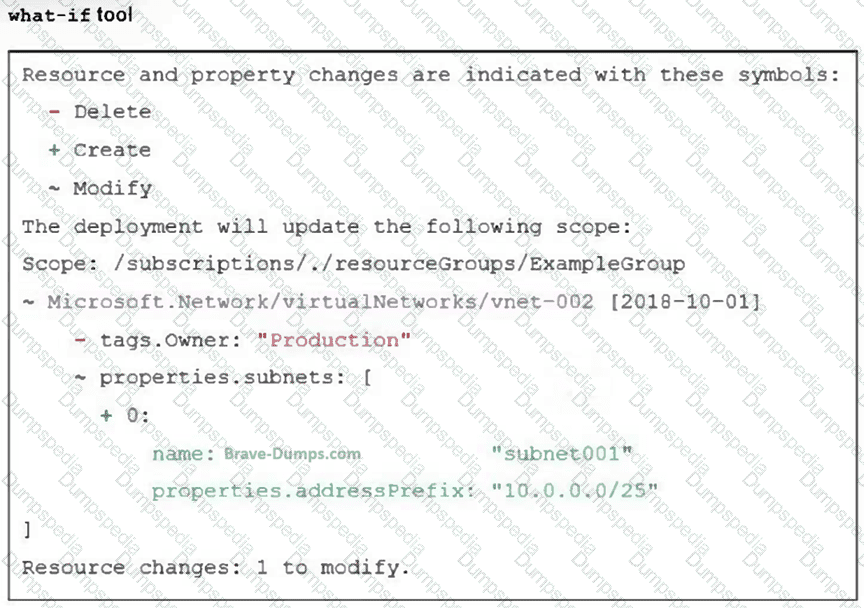
An administrator used the what-if tool to preview the changes to an Azure Bicep file. What will happen if the administrator applies these changes in Azure? (Choose one answer)
You are investigating an attack path for a top risky host. You notice that the Common Vulnerability Scoring System (CVSS) and the vulnerability impact scores are very high. However, the attack path severity for the top risky host itself is low. Which two pieces of contextualized information can help you understand why? (Choose two answers)
You must add an Amazon Web Services (AWS) network access list (NACL) rule to allow SSH traffic to a subnet for temporary testing purposes. When you review the current inbound and outbound NACL rules, you notice that the rules with number 5 deny SSH and telnet traffic to the subnet.
What can you do to allow SSH traffic?
What are two main features in Amazon Web Services (AWS) network access control lists (NACLs)? (Choose two answers)