One user has reported connectivity issues; no other users have reported problems. Which tool can the administrator use to identify the problem? (Choose one answer)
What can be configured on FortiSASE as an additional layer of security for FortiClient registration? (Choose one answer)
Which secure internet access (SIA) use case minimizes individual workstation or device setup, because you do not need to install FortiClient on endpoints or configure explicit web proxy settings on web browser-based end points?
Which three traffic flows are supported by FortiSASE Secure Private Access (SPA)? (Choose three answers)
To complete their day-to-day operations, remote users require access to a TCP-based application that is hosted on a private web server. Which FortiSASE deployment use case provides the most efficient and secure method for meeting the remote users' requirements?
Which two components are part of onboarding a secure web gateway (SWG) endpoint? (Choose two)
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
Refer to the exhibits.
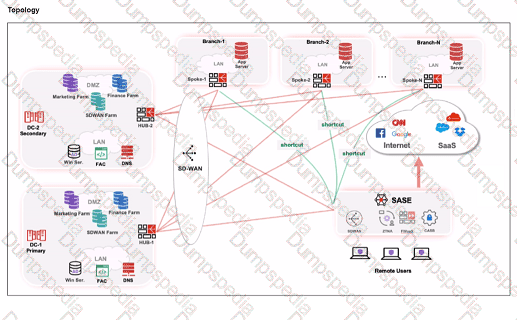
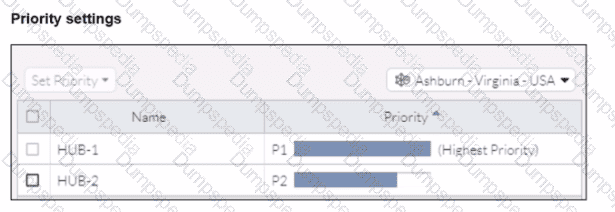
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
When viewing the daily summary report generated by FortiSASE. the administrator notices that the report contains very little data. What is a possible explanation for this almost empty report?
Refer to the exhibit.
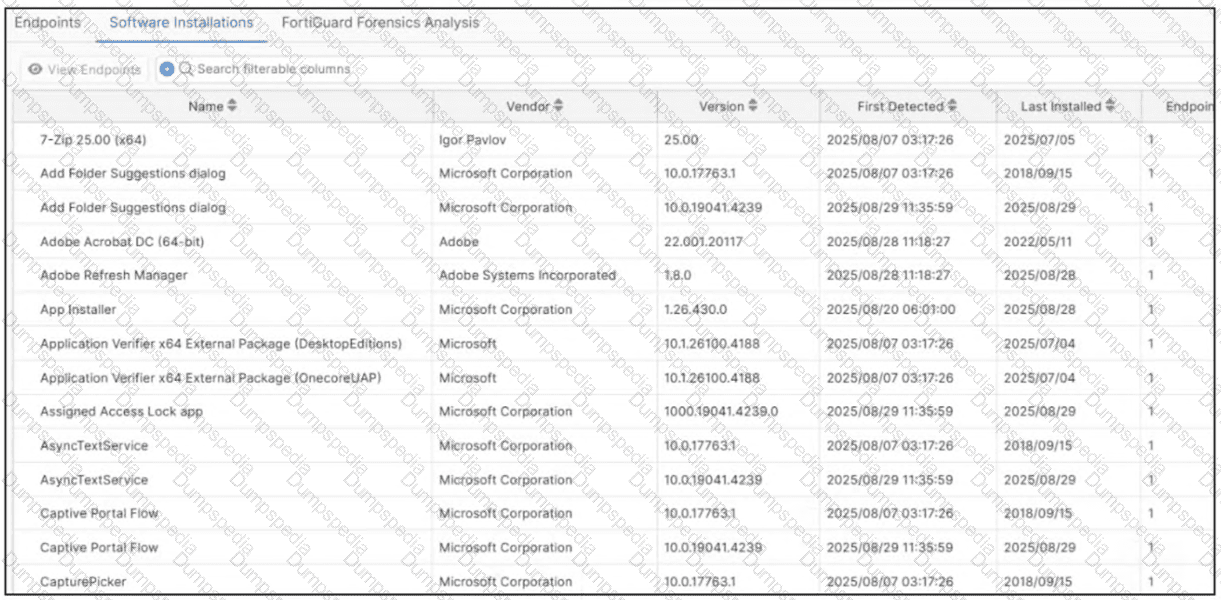
Which type of information or actions are available to a FortiSASE administrator from the following output? (Choose one answer)
A company must provide access to a web server through FortiSASE secure private access for contractors. What is the recommended method to provide access? (Choose one answer)
An organization needs to resolve internal hostnames using its internal rather than public DNS servers for remotely connected endpoints. Which two components must be configured on FortiSASE to achieve this? (Choose two.)
A FortiSASE administrator is configuring a Secure Private Access (SPA) solution to share endpoint information with a corporate FortiGate.
Which three configuration actions will achieve this solution? (Choose three.)
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for which three FortiSASE components? (Choose three.)
Your organization is currently using FortiSASE for its cybersecurity. They have recently hired a contractor who will work from the HQ office and who needs temporary internet access in order to set up a web-based point of sale (POS) system. How can you provide secure internet access to the contractor using FortiSASE? (Choose one answer)
Refer to the exhibit.
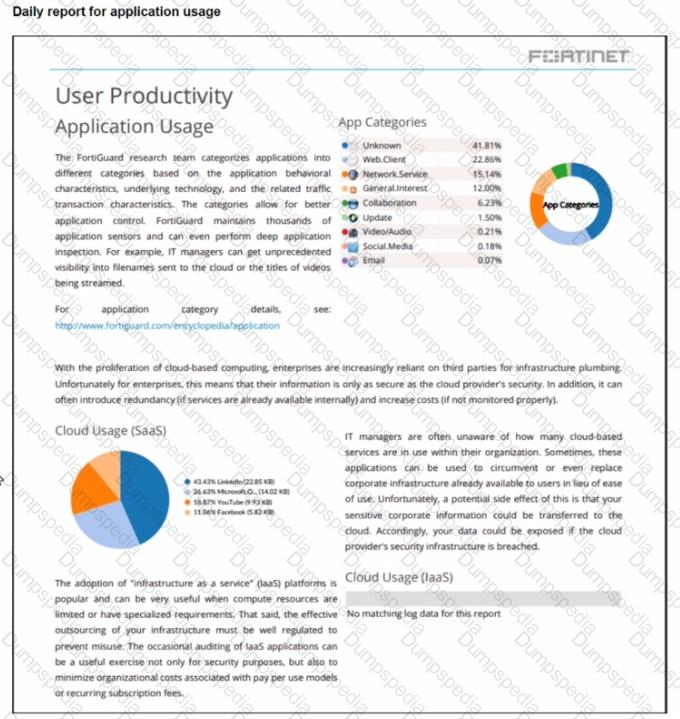
The daily report for application usage shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
You have configured FortiSASE Secure Private Access (SPA) deployment. Which statement is true about traffic flows? (Choose two answers)
Refer to the exhibits.
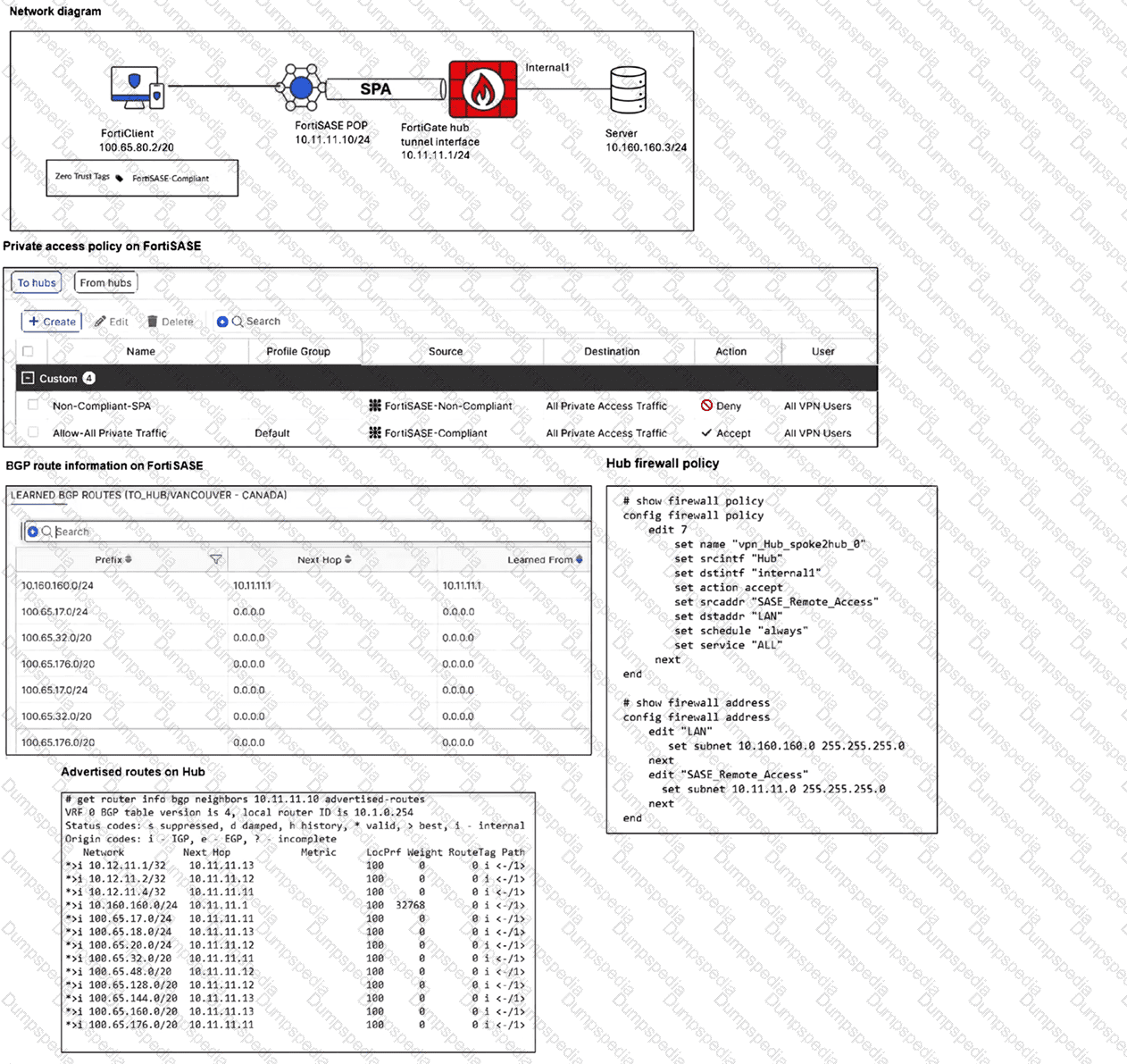
A FortiSASE administrator has configured FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGate hub. However, the remote FortiClient is not able to access the web server hosted behind the FortiGate hub. What is the reason for the access failure? (Choose one answer)
When you configure FortiSASE Secure Private Access (SPA) with SD-WAN integration, you must establish a routing adjacency between FortiSASE and the FortiGate SD-WAN hub. Which routing protocol must you use?
Refer to the exhibit.
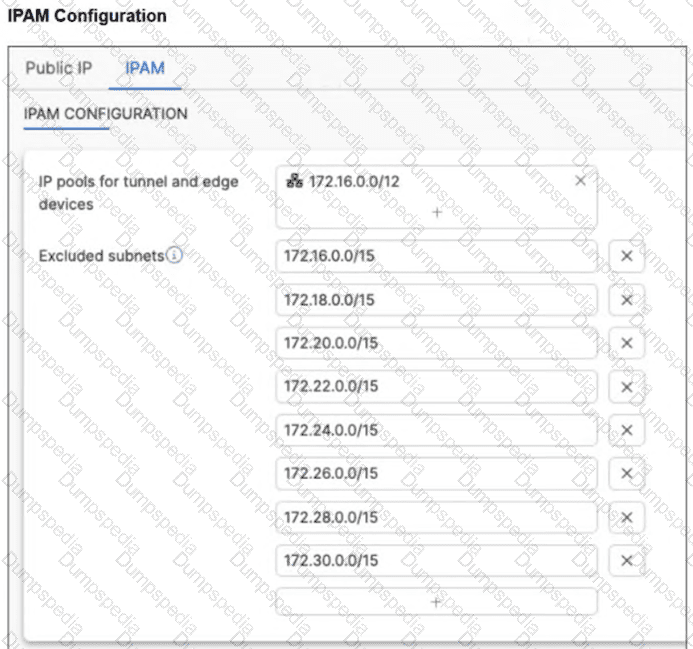
A customer wants to fine-tune network assignments on FortiSASE, so they modified the IPAM configuration as shown in the exhibit. After this configuration, the customer started having connectivity problems and noticed that devices are using excluded ranges. What could be causing the unexpected behavior and connectivity problems? (Choose two answers)
Which information does FortiSASE use to bring network lockdown into effect on an endpoint? (Choose one answer)