Which type of system collects data and uses correlation rules to trigger alarms?
Which tool's analysis data gives security operations teams insight into their environment's risks from exposed services?
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
A doctor receives an email about her upcoming holiday in France. When she clicks the URL website link in the email, the connection is blocked by her office firewall because it's a known malware website. Which type of attack includes a link to a malware website in an email?
Which network firewall primarily filters traffic based on source and destination IP address?
A user is given access to a service that gives them access to cloud-hosted physical and virtual servers, storage, and networking.
Which NIST cloud service model is this?
Based on how much is managed by the vendor, where can CaaS be situated in the spread of cloud computing services?
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
Which technology secures software-as-a-service (SaaS) applications and network data, and also enforces compliance policies for application access?
Which type of firewall should be implemented when a company headquarters is required to have redundant power and high processing power?
Which technique uses file sharing or an instant messenger client such as Meebo running over Hypertext Transfer Protocol (HTTP)?
Which type of malware replicates itself to spread rapidly through a computer network?
Which term describes data packets that move in and out of the virtualized environment from the host network or a corresponding traditional data center?
Which two pieces of information are considered personally identifiable information (PII)? (Choose two.)
What is a characteristic of the National Institute Standards and Technology (NIST) defined cloud computing model?
In which situation would a dynamic routing protocol be the quickest way to configure routes on a router?
What is the recommended method for collecting security logs from multiple endpoints?
What role do containers play in cloud migration and application management strategies?
An administrator finds multiple gambling websites in the network traffic log.
What can be created to dynamically block these websites?
In which phase of the cyberattack lifecycle do attackers establish encrypted communication channels back to servers across the internet so that they can modify their attack objectives and methods?
A high-profile company executive receives an urgent email containing a malicious link. The sender appears to be from the IT department of the company, and the email requests an update of the executive's login credentials for a system update.
Which type of phishing attack does this represent?
On an endpoint, which method should you use to secure applications against exploits?
Which feature of cloud-native security platforms (CNSPs) focuses on protecting virtual machine (VM), container, and serverless deployments against application-level attacks during runtime?
Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) fall under which Prisma access service layer?
Which two network resources does a directory service database contain? (Choose two.)
Layer 4 of the TCP/IP Model corresponds to which three Layer(s) of the OSI Model? (Choose three.)
Which of the following is a service that allows you to control permissions assigned to users in order for them to access and utilize cloud resources?
In which two cloud computing service models are the vendors responsible for vulnerability and patch management of the underlying operating system? (Choose two.)
Which VM-Series virtual firewall cloud deployment use case reduces your environment's attack surface?
Which security function enables a firewall to validate the operating system version of a device before granting it network access?
Which NGFW feature is used to provide continuous identification, categorization, and control of known and previously unknown SaaS applications?
Which security tool provides policy enforcement for mobile users and remote networks?
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering intelligence?
In an IDS/IPS, which type of alarm occurs when legitimate traffic is improperly identified as malicious traffic?
What protocol requires all routers in the same domain to maintain a map of the network?
With regard to cloud-native security in layers, what is the correct order of the four C's from the top (surface) layer to the bottom (base) layer?
Which next-generation firewall (NGFW) deployment option provides full application visibility into Kubernetes environments?
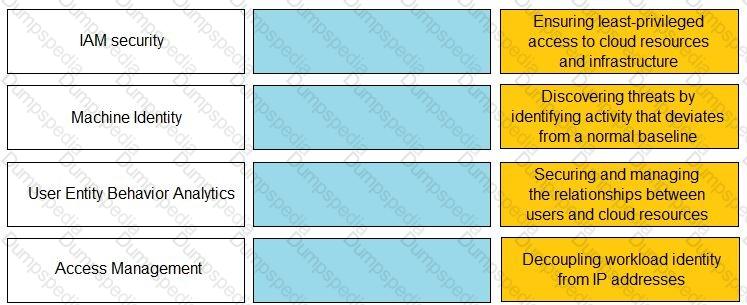
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Which component of the AAA framework regulates user access and permissions to resources?
Which feature of the VM-Series firewalls allows them to fully integrate into the DevOps workflows and CI/CD pipelines without slowing the pace of business?