The compliance officer requests that all evasive applications need to be blocked on all perimeter firewalls out to the internet The firewall is configured with two zones;
1. trust for internal networks
2. untrust to the internet
Based on the capabilities of the Palo Alto Networks NGFW, what are two ways to configure a security policy using App-ID to comply with this request? (Choose two )
Assume that traffic matches a Security policy rule but the attached Security Profiles is configured to block matching traffic
Which statement accurately describes how the firewall will apply an action to matching traffic?
Place the following steps in the packet processing order of operations from first to last.

You receive notification about a new malware that infects hosts An infection results in the infected host attempting to contact a command-and-control server Which Security Profile when applied to outbound Security policy rules detects and prevents this threat from establishing a command-and-control connection?
Which three types of entries can be excluded from an external dynamic list (EDL)? (Choose three.)
What are three valid source or D=destination conditions available as Security policy qualifiers? (Choose three.)
Recently changes were made to the firewall to optimize the policies and the security team wants to see if those changes are helping.
What is the quickest way to reset the hit counter to zero in all the security policy rules?
Which link in the web interface enables a security administrator to view the security policy rules that match new application signatures?
Your company occupies one floor in a single building you have two active directory domain controllers on a single networks the firewall s management plane is only slightly utilized.
Which user-ID agent sufficient in your network?
A network administrator creates an intrazone security policy rule on a NGFW. The source zones are set to IT. Finance, and HR.
To which two types of traffic will the rule apply? (Choose two.)
When HTTPS for management and GlobalProtect are enabled on the same interface, which TCP port is used for management access?
Within an Anti-Spyware security profile, which tab is used to enable machine learning based engines?
Which two Palo Alto Networks security management tools provide a consolidated creation of policies, centralized management and centralized threat intelligence. (Choose two.)
An administrator is troubleshooting an issue with traffic that matches the intrazone-default rule, which is set to default configuration.
What should the administrator do?
An administrator would like to see the traffic that matches the interzone-default rule in the traffic logs.
What is the correct process to enable this logging1?
Which DNS Query action is recommended for traffic that is allowed by Security policy and matches Palo Alto Networks Content DNS Signatures?
Which action results in the firewall blocking network traffic with out notifying the sender?
In which three places on the PAN-OS interface can the application characteristics be found? (Choose three.)
What must first be created on the firewall for SAML authentication to be configured?
An administrator wants to prevent users from submitting corporate credentials in a phishing attack.
Which Security profile should be applied?
Which two DNS policy actions in the anti-spyware security profile can prevent hacking attacks through DNS queries to malicious domains? (Choose two.)
Which three configuration settings are required on a Palo Alto networks firewall management interface?
An internal host wants to connect to servers of the internet through using source NAT.
Which policy is required to enable source NAT on the firewall?
Which firewall plane provides configuration, logging, and reporting functions on a separate processor?
The administrator profile "SYS01 Admin" is configured with authentication profile "Authentication Sequence SYS01," and the authentication sequence SYS01 has a profile list with four authentication profiles:
• Auth Profile LDAP
• Auth Profile Radius
• Auth Profile Local
• Auth Profile TACACS
After a network outage, the LDAP server is no longer reachable. The RADIUS server is still reachable but has lost the "SYS01 Admin" username and password.
What is the "SYS01 Admin" login capability after the outage?
An administrator is configuring a NAT rule
At a minimum, which three forms of information are required? (Choose three.)
A network administrator is required to use a dynamic routing protocol for network connectivity.
Which three dynamic routing protocols are supported by the NGFW Virtual Router for this purpose? (Choose three.)

Given the detailed log information above, what was the result of the firewall traffic inspection?
Which built-in IP address EDL would be useful for preventing traffic from IP addresses that are verified as unsafe based on WildFire analysis Unit 42 research and data gathered from telemetry?
Which type of security policy rule will match traffic that flows between the Outside zone and inside zone, but would not match traffic that flows within the zones?
An administrator wants to create a NAT policy to allow multiple source IP addresses to be translated to the same public IP address. What is the most appropriate NAT policy to achieve this?
Prior to a maintenance-window activity, the administrator would like to make a backup of only the running configuration to an external location.
What command in Device > Setup > Operations would provide the most operationally efficient way to achieve this outcome?
What two authentication methods on the Palo Alto Networks firewalls support authentication and authorization for role-based access control? (Choose two.)
Which object would an administrator create to block access to all high-risk applications?
In which stage of the Cyber-Attack Lifecycle would the attacker inject a PDF file within an email?
How can a complete overview of the logs be displayed to an administrator who has permission in the system to view them?
Which two rule types allow the administrator to modify the destination zone? (Choose two )
Which user mapping method could be used to discover user IDs in an environment with multiple Windows domain controllers?
Choose the option that correctly completes this statement. A Security Profile can block or allow traffic ____________.
Which information is included in device state other than the local configuration?
Which User-ID agent would be appropriate in a network with multiple WAN links, limited network bandwidth, and limited firewall management plane resources?
Which Palo Alto Networks firewall security platform provides network security for mobile endpoints by inspecting traffic deployed as internet gateways?
Based on the graphic which statement accurately describes the output shown in the server monitoring panel?

When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?

According to the best practices for mission critical devices, what is the recommended interval for antivirus updates?
An administrator needs to create a Security policy rule that matches DNS traffic within the LAN zone, and also needs to match DNS traffic within the DMZ zone The administrator does not want to allow traffic between the DMZ and LAN zones.
Which Security policy rule type should they use?
Which action can be set in a URL Filtering Security profile to provide users temporary access to all websites in a given category using a provided password?
Which firewall feature do you need to configure to query Palo Alto Networks service updates over a data-plane interface instead of the management interface?
Which path in PAN-OS 11.x would you follow to see how new and modified App-IDs impact a Security policy?
What is considered best practice with regards to committing configuration changes?
What is the default action for the SYN Flood option within the DoS Protection profile?
Which two features can be used to tag a user name so that it is included in a dynamic user group? (Choose two)
What are the two default behaviors for the intrazone-default policy? (Choose two.)
Which three types of authentication services can be used to authenticate user traffic flowing through the firewalls data plane? (Choose three )
Which type of DNS signatures are used by the firewall to identify malicious and command-and-control domains?
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.

Which object would an administrator create to enable access to all applications in the office-programs subcategory?
What are three factors that can be used in domain generation algorithms? (Choose three.)
Which path in PAN-OS 10.2 is used to schedule a content update to managed devices using Panorama?
In a security policy what is the quickest way to rest all policy rule hit counters to zero?
What does an administrator use to validate whether a session is matching an expected NAT policy?
Which option lists the attributes that are selectable when setting up an Application filters?
Which the app-ID application will you need to allow in your security policy to use facebook-chat?
An administrator wants to reference the same address object in Security policies on 100 Panorama managed firewalls, across 10 device groups and five templates.
Which configuration action should the administrator take when creating the address object?
In which two Security Profiles can an action equal to the block IP feature be configured? (Choose two.)
If using group mapping with Active Directory Universal Groups, what must you do when configuring the User-ID?
All users from the internal zone must be allowed only HTTP access to a server in the DMZ zone.
Complete the empty field in the Security policy using an application object to permit only this type of access.
Source Zone: Internal -
Destination Zone: DMZ Zone -
Application: __________
Service: application-default -
Action: allow
By default, what is the maximum number of templates that can be added to a template stack?
Which interface type is part of a Layer 3 zone with a Palo Alto Networks firewall?
You need to allow users to access the office–suite application of their choice. How should you configure the firewall to allow access to any office-suite application?
An administrator configured a Security policy rule with an Antivirus Security profile. The administrator did not change the action (or the profile. If a virus gets detected, how wilt the firewall handle the traffic?
Which action related to App-ID updates will enable a security administrator to view the existing security policy rule that matches new application signatures?
Which three types of Source NAT are available to users inside a NGFW? (Choose three.)
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?

Given the screenshot what two types of route is the administrator configuring? (Choose two )
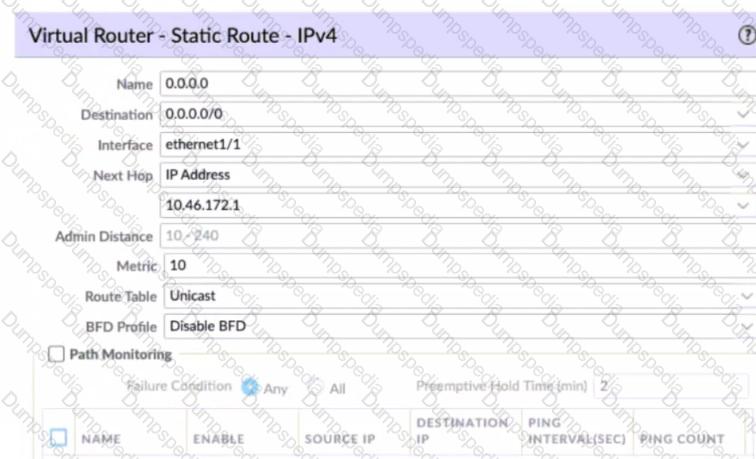
Which administrator type utilizes predefined roles for a local administrator account?
In which two Security Profiles can an action equal to the block IP feature be configured? (Choose two.)
A company moved its old port-based firewall to a new Palo Alto Networks NGFW 60 days ago. Which utility should the company use to identify out-of-date or unused rules on the firewall?
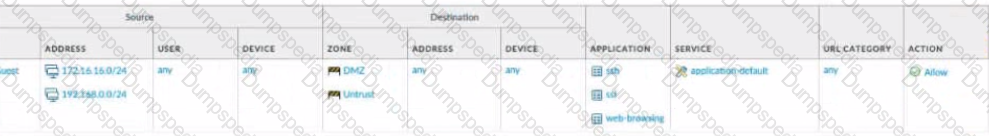
View the diagram.
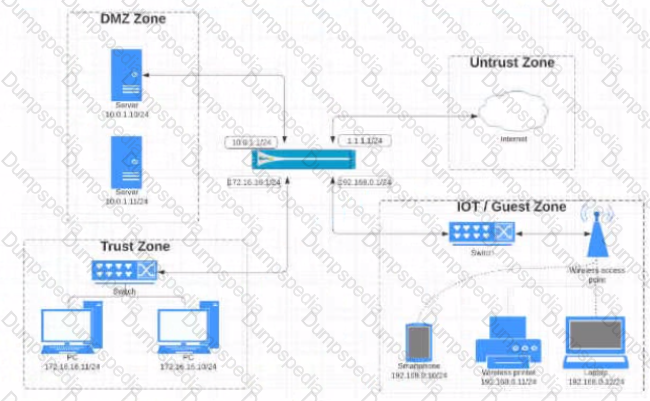
What is the most restrictive yet fully functional rule to allow general Internet and SSH traffic into both the DMZ and Untrust/lnternet zones from each of the lOT/Guest and Trust Zones?
A)
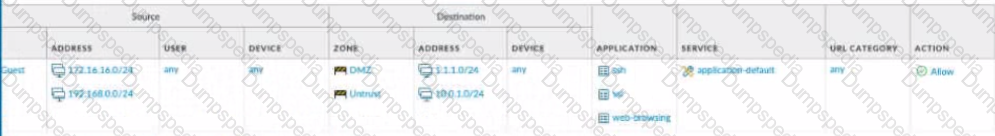
B)
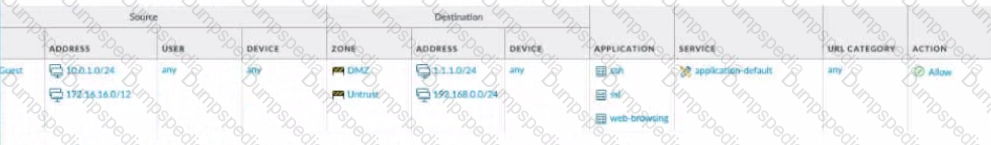
C)

D)
A network administrator created an intrazone Security policy rule on the firewall. The source zones were set to IT. Finance, and HR.
Which two types of traffic will the rule apply to? (Choose two)
An administrator wants to enable access to www.paloaltonetworks.com while denying access to all other sites in the same category.
Which object should the administrator create to use as a match condition for the security policy rule that allows access to www.paloaltonetworks.com?
Which administrative management services can be configured to access a management interface?
Refer to the exhibit. A web server in the DMZ is being mapped to a public address through DNAT.

Which Security policy rule will allow traffic to flow to the web server?
Which administrator type provides more granular options to determine what the administrator can view and modify when creating an administrator account?
Assume a custom URL Category Object of "NO-FILES" has been created to identify a specific website
How can file uploading/downloading be restricted for the website while permitting general browsing access to that website?