A technician is setting up a backup method on a workstation that only requires two sets of tapes to restore. Which of the following would BEST accomplish this task?
A technician is helping a customer connect to a shared drive. The technician notices some unused drives that have already been mapped and wants to disconnect those drives first. Which of the following commands should the technician use?
Which of the following commands should a technician use to change user permissions?
A suite of security applications was installed a few days ago on a user's home computer. The user reports that the
computer has been running slowly since the installation. The user notices the hard drive activity light is constantly solid. Which of the following should be checked FIRST?
A technician receives a call from a user who is on vacation. The user provides the necessary credentials and asks the technician to log in to the
users account and read a critical email that the user has been expecting. The technician refuses because this is a violation of the:
A call center handles inquiries into billing issues for multiple medical facilities. A security analyst notices that call center agents often walk away from their workstations, leaving patient data visible for anyone to see. Which of the following should a network administrator do to BEST prevent data theft within the call center?
A workstation's hard drive is making loud noises, applications are running slowly, and the workstation is rebooting unexpectedly. Which of the following should the technician do first to begin troubleshooting the issue?
A customer is explaining issues with a workstation to a technician. While the customer is listing the issues, the technician is browsing social media on a smartphone. Which of the following professionalism and communication techniques should the technician be using in this situation? (Select two).
A user sent a large amount of money to a supplier's bank account and claims that the Chief Executive Officer instructed the user to do so. A technician informs the user that the request was fraudulent and contacts the authorities. Which of the following types of attack took place?
An organization's Chief Financial Officer (CFO) is concerned about losing access to very sensitive, legacy unmaintained PII on a workstation if a
ransomware outbreak occurs. The CFO has a regulatory requirement to retain this data for many years. Which of the following backup methods
would BEST meet the requirements?
A technician downloaded software from the Internet that required the technician to scroll through a text box and at the end of the text box, click a
button labeled Accept Which of the following agreements IS MOST likely in use?
A technician is troubleshooting a computer with a suspected short in the power supply. Which of the following is the FIRST step the technician should take?
A small business owner wants to install newly purchased software on all networked PCs. The network is not configured as a domain, and the owner wants to use the easiest method possible. Which of the following is the MOST deficient way lor the owner to install the application?
The web browsing speed on a customer's mobile phone slows down every few weeks and then returns to normal after three or four days. Restarting the device does not usually restore performance. Which of the following should a technician check FIRST to troubleshoot this issue?
A company discovered that numerous computers from multiple geographic locations are sending a very high number of connection requests which is causing the company’s web server to become unavailable to the general public. Which of the following attacks is occurring?
A user installed a new application that automatically starts each time the user logs in to a Windows 10 system. The user does not want this to happen and has asked for this setting to be changed. Which of the following tools would the technician MOST likely use to safely make this change?
A technician is working on a Windows 10 PC that has unwanted applications starting on boot. Which of the following tools should the technician use to disable applications on startup?
A technician needs to provide recommendations about how to upgrade backup solutions for a site in an area that has frequent hurricanes and an unstable power grid. Which of the following should the technician recommend implementing?
A user is no longer able to start the OS on a computer and receives an error message indicating there is no OS found. A technician reviews the audit logs and notes that the user's system posted a S.M.A.R.T. error just days before this issue. Which of the following is the MOST likely cause of this issue?
A systems administrator is monitoring an unusual amount of network traffic from a kiosk machine and needs to Investigate to determine the source of the traffic. Which of the following tools can the administrator use to view which processes on the kiosk machine are connecting to the internet?
A technician has been tasked with troubleshooting audiovisual issues in a conference room. The meeting presenters are unable to play a video with sound. The following error is received:
The Audio Driver is not running.
Which of the following will MOST likely resolve the issue?
The battery life on an employee's new phone seems to be drastically less than expected, and the screen stays on for a very long time after the employee sets the phone down. Which of the following should the technician check first to troubleshoot this issue? (Select two).
A developer's Type 2 hypervisor is performing inadequately when compiling new source code. Which of the following components should the developer upgrade to improve the hypervisor’s performance?
A systems administrator is experiencing Issues connecting from a laptop to the corporate network using PKI. Which to the following tools can the systems administrator use to help remediate the issue?
An IT security team is implementing a new Group Policy that will return a computer to the login after three minutes. Which of the following BEST describes the change in policy?
A company recently outsourced its night-shift cleaning service. A technician is concerned about having unsupervised contractors in the building. Which of the following security measures can be used to prevent the computers from being accessed? (Select two).
A technician is investigating options to secure a small office's wireless network. One requirement is to allow automatic log-ins to the network using certificates instead of passwords. Which of the following should the wireless solution have in order to support this feature?
A user requires a drive to be mapped through a Windows command line. Which of the following command-line tools can be utilized to map the drive?
A technician needs to ensure that USB devices are not suspended by the operating system Which of the following Control Panel utilities should the technician use to configure the setting?
A technician received a call from a user who clicked on a web advertisement Now. every time the user moves the mouse, a pop-up display across the monitor. Which of the following procedures should the technician perform?
A hard drive that previously contained PI I needs to be repurposed for a public access workstation. Which of the following data destruction methods should a technician use to ensure data is completely removed from the hard drive?
A company wants to ensure employees are using strong passwords. Which of the following should the company use to enforce password security?
Which of the following should be enabled on a mobile device to prevent unauthorized access to data in case the device is lost or stolen? (Select two).
A web developer installs and launches a new external web server. Immediately following the launch, the performance of all traffic traversing the firewall degrades substantially. Which of the following considerations was overlooked?
A user is receiving repeated pop-up advertising messages while browsing the internet. A malware scan Is unable to locate the source of an infection. Which of the following should the technician check NEXT?
A user reports a virus is on a PC. The user installs additional real-lime protection antivirus software, and the PC begins performing extremely slow. Which of the following steps should the technician take to resolve the issue?
An administrator responded to an incident where an employee copied financial data to a portable hard drive and then left the company with the data. The administrator documented the movement of the evidence. Which of the following concepts did the administrator demonstrate?
A user calls the help desk to report that Windows installed updates on a laptop and rebooted overnight. When the laptop started up again, the touchpad was no longer working. The technician thinks the software that controls the touchpad might be the issue. Which of the following tools should the technician use to make adjustments?
A homeowner recently moved and requires a new router for the new ISP to function correctly. The internet service has been installed and has been confirmed as functional. Which of the following is the FIRST step the homeowner should take after installation of all relevant cabling and hardware?
A technician is updating the OS on a number of Windows workstations. After successfully updating several workstations, the technician receives an error indicating that the upgrade takes more space than is available on one of the PCs. Which of the following should the technician do to proceed with the upgrade? (Select two).
A technician installs specialized software on a workstation. The technician then attempts to run the software. The workstation displays a message indicating the software is not authorized to run. Which of the following should the technician do to most likely resolve the issue?
A user needs assistance installing software on a Windows PC but will not be in the office. Which of the following solutions would a technician MOST likely use to assist the user without having to install additional software?
A systems administrator receives notification about unauthorized access to company resources outside normal business hours. Which of the following security measures should the systems administrator implement to prevent further unauthorized use?
When a user is in the office, web pages are loading slowly on the user's phone. Which of the following best explains this issue?
Which of the following should be considered when maintaining the environment of a server room?
A user has been unable to receive emails or browse the internet from a smartphone while traveling. However, text messages and phone calls are working without issue. Which of the following should a support technician check FIRST?
A company's assets are scanned annually. Which of the following will most likely help the company gain a holistic view of asset cost?
A user reports an issue when connecting a mobile device to Bluetooth. The user states the mobile device's Bluetooth is turned on. Which of the following steps should the technician take NEXT to resolve the issue?
A remote user is having issues accessing an online share. Which of the following tools would MOST likely be used to troubleshoot the Issue?
Which of the following is used to integrate Linux servers and desktops into Windows Active Directory environments?
A user opened a ticket regarding a corporate-managed mobile device. The assigned technician notices the OS Is several versions out of date. The user Is unaware the OS version is not current because auto-update is turned on. Which of the following is MOST likely the cause of the Issue?
Which of The following refers to the steps to be taken if an Issue occurs during a change Implementation?
Which of the following macOS utilities uses AES-128 to encrypt the startup disk?
A technician is unable to access the internet or named network resources. The technician receives a valid IP address from the DHCP server and can ping the default gateway. Which of the following should the technician check next to resolve the issue?
A user is unable to access a web-based application. A technician verifies the computer cannot access any web pages at all. The computer obtains an IP address from the DHCP server. Then, the technician verifies the user can ping localhost. the gateway, and known IP addresses on the interne! and receive a response. Which of the following Is the MOST likely reason tor the Issue?
A company would like to implement multifactor authentication for all employees at a minimal cost. Which of the following best meets the company's requirements?
A technician removed a virus from a user's device. The user returned the device a week later with the same virus on it. Which of the following should the technician do to prevent future infections?
A user has a computer with Windows 10 Home installed and purchased a Windows 10 Pro license. The user is not sure how to upgrade the OS. Which of the following should the technician do to apply this license?
A technician needs to update the software on several hundred Mac laptops. Which of the following is the best method to complete the task?
A technician needs to recommend a way to keep company devices for field and home-based staff up to date. The users live in various places across the country and the company has several national offices that staff can go to for technical support Which of the following methods is most appropriate for the users?
A user received an alert from a Windows computer indicating low storage space. Which of the following will best resolve this issue?
A user reports being unable to access a sports team's website on an office computer. The administrator tells the user this blocked access is intentional and based on company guidelines. Which of the following is the administrator referring to?
A network administrator is setting up the security for a SOHO wireless network. Which of the following options should the administrator enable to secure the network?
A technician is configuring a SOHO router and wants to only allow specific computers on the network. Which of the following should the technician do?
A technician receives a high-priority ticket about sensitive information collected from an end user’s workstation. Which of the following steps should a technician take to preserve the chain of custody for a forensic investigation?
A company was recently attacked by ransomware. The IT department has remediated the threat and determined that the attack method used was email. Which of the following is the most effective way to prevent this issue from reoccurring?
A user opened an infected email. A security administrator responded to the malicious event, successfully mitigated the situation, and returned the machine to service Which of the following needs to be completed before this event is considered closed?
A user takes a work-issued laptop home for the first time. When the user attempts to browse any website on the home internet, the user receives the following error:
"This site cannot be reached."
A technician from work confirms that the static IP that was set up on the machine was changed back to DHCP. Which of the following needs to be corrected?
Which of the following operating systems were designed for smartphones? (Select two).
A user is trying to limit the amount of time their children spend on the internet. Which of the following Windows 10 settings should be enabled to accomplish this objective?
A technician is troubleshooting a Windows system that is having issues with the OS loading at startup. Which of the following should the technician do to diagnose the issue?
A company uses shared drives as part of a workforce collaboration process. To ensure the correct access permissions, inheritance at the top-level folder is assigned to each department. A manager's team is working on confidential material and wants to ensure only the immediate team can view a specific folder and its subsequent files and subfolders. Which of the following actions should the technician most likely take?
Which of the following operating systems was the app file type designed to run under as an application file bundle?
Which of the following is used to generate passcodes necessary to access applications or systems that require an extra layer of security?
A technician downloaded an OS installation file but is unable to run it. When the technician tries to open the file, a message indicates no software is installed to run this file. Which of the following should the technician do next to attempt to access the OS file?
A technician is setting up a printer on a Linux workstation. Which of the following commands should the technician use to set the default printer?
A user clicked a link in an email, and now the cursor is moving around on its own. A technician notices that File Explorer is open and data is being copied from the local drive to an unknown cloud storage location. Which of the following should the technician do first?
A customer service representative is unable to send jobs to a printer at a remote branch office. However, the representative can print successfully to a local network printer. Which of the following commands should a technician use to view the path of the network traffic from the PC?
Which of the following languages is used for scripting the creation of Active Directory accounts?
A technician is troubleshooting a user’s PC that is running slowly and displaying frequent pop-ups. The technician thinks malware may be causing the issues, but before the issues began the user installed anti-malware software in response to a pop-up window Which of the following is the most likely cause of these issues'?
An organization wants to deploy a customizable operating system. Which of the following should the organization choose?
A technician is troubleshooting a PC that is unable to perform DNS lookups. Utilizing the following firewall output:
Protocol/PortActionDirection
1 AllowOut
445 BlockOut
53 BlockOut
123 BlockOut
80 BlockOut
Which of the following ports should be opened to allow for DNS recursion?
A malicious user was able to export an entire website's user database by entering specific commands into a field on the company's website. Which of the following did the malicious user most likely exploit to extract the data?
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users' audio issues are
resolved using best practice procedures.
Multiple devices may be selected for quarantine.
Click on a host or server to configure services.



An employee has been using the same password for multiple applications and websites for the past several years. Which of the following would be best to prevent security issues?
A company installed WAPs and deployed new laptops and docking stations to all employees. The docking stations are connected via LAN cables. Users are now reporting degraded network service. The IT department has determined that the WAP mesh network is experiencing a higher than anticipated amount of traffic. Which of the following would be the most efficient way to ensure the wireless network can support the expected number of wireless users?
A technician is following the ticketing system’s best practices when handling user support requests. Which of the following should the technician do first when responding to a user support request that contains insufficient information?
Multiple users routinely record log-in information in readily accessible areas. Which of the following is the best way to mitigate this issue?
Which of the following features can be used to ensure a user can access multiple versions of files?
A user’s Windows 10 workstation with an HDD is running really slowly. The user has opened, closed, and saved many large files over the past week. Which of the following tools should a technician use to remediate the issue?
A technician is doing a bare-metal installation of the Windows 10 operating system. Which of the following prerequisites must be in place before the technician can start the installation process?
A customer, whose smartphone's screen was recently repaired, reports that the device has no internet access through Wi-Fi. The device shows that it is connected to Wi-Fi, has an address of 192.168.1.42. and has no subnet mask. Which of the following should the technician check next?
An administrator needs to select a method to dispose of SSDs containing sensitive data. Which of the following are the most appropriate methods? (Select two).
Users report having difficulty using the Windows Hello facial recognition feature. Which of the following is a secondary feature of Windows Hello that can be used to log in?
A mobile phone user has downloaded a new payment application that allows payments to be made with a mobile device. The user attempts to use the device at a payment terminal but is unable to do so successfully. The user contacts a help desk technician to report the issue. Which of the following should the technician confirm NEXT as part of the troubleshooting process?
A field technician applied a Group Policy setting to all the workstations in the network. This setting forced the workstations to use a specific SNTP server. Users are unable to log in now. Which of the following is the MOST likely cause of this issue?
Each time a user tries to go to the selected web search provider, a different website opens. Which of the following should the technician check FIRST?
A technician is troubleshooting a customer's PC and receives a phone call. The technician does not take the call and sets the phone to silent. Which of the following BEST describes the technician's actions?
A user is having issues with document-processing software on a Windows workstation. Other users that log in to the same device do not have the same issue.
Which of the following should a technician do to remediate the issue?
A user created a file on a shared drive and wants to prevent its data from being accidentally deleted by others. Which of the following applications should the technician use to assist the user with hiding the file?
A user calls the help desk and reports a workstation is infected with malicious software. Which of the following tools should the help desk technician use to remove the malicious software? (Select TWO).
A technician is tasked with configuring a computer for a visually impaired user. Which of the following utilities should the technician use?
A user has a license for an application that is in use on a personal home laptop. The user approaches a systems administrator about using the same license on
multiple computers on the corporate network. Which of the following BEST describes what the systems administrator should tell the user?
A company is deploying mobile phones on a one-to-one basis, but the IT manager is concerned that users will root/jailbreak their phones. Which of the following technologies can be implemented to prevent this issue?
A technician connects an additional monitor to a PC using a USB port. The original HDMI monitor is mounted to the left of the new monitor. When moving the mouse to the right from the original monitor to the new monitor, the mouse stops at the end of the screen on the original monitor. Which
of the following will allow the mouse to correctly move to the new monitor?
A user connected a laptop to a wireless network and was tricked into providing login credentials for a website. Which of the following threats was used to carry out the attack?
The findings from a security audit indicate the risk of data loss from lost or stolen laptops is high. The company wants to reduce this risk with minimal impact to users who want to use their laptops when not on the network. Which of the following would BEST reduce this risk for Windows laptop users?
A desktop support technician is tasked with migrating several PCs from Windows 7 Pro to Windows 10 Pro, The technician must ensure files and user preferences are retained, must perform the operation locally, and should migrate one station at a time. Which of the following methods would be MOST efficient?
A user in a corporate office reports the inability to connect to any network drives. No other users have reported this issue. Which of the following is the MOST likely reason the user is having this issue?
A user received the following error upon visiting a banking website:
The security presented by website was issued a different website' s address .
A technician should instruct the user to:
A technician has been asked to set up a new wireless router with the best possible security. Which of the following should the technician implement?
A Windows user reported that a pop-up indicated a security issue. During inspection, an antivirus system identified malware from a recent download, but it was unable to remove the malware. Which of the following actions would be BEST to remove the malware while also preserving the user's files?
A macOS user needs to create another virtual desktop space. Which of the following applications will allow the user to accomplish this task?
A technician needs to manually set an IP address on a computer that is running macOS. Which of the following commands should the technician use?
Following the latest Windows update PDF files are opening in Microsoft Edge instead of Adobe Reader. Which of the following utilities should be used to ensure all PDF files open in Adobe Reader?
A Windows administrator is creating user profiles that will include home directories and network printers for several new users. Which of the following is the most efficient way for the technician to complete this task?
A user reports that after a recent software deployment to upgrade applications, the user can no longer use the Testing program.
However, other employees can successfully use the Testing program.
INSTRUCTIONS
Review the information in each tab to verify the results of the deployment and resolve any issues discovered by selecting the:
Index number of the Event Viewer issue
First command to resolve the issue
Second command to resolve the issue
BSOD
Commands:
Event Viewer:

System Error:
A technician is working to resolve a Wi-Fi network issue at a doctor's office that is located next to an apartment complex. The technician discovers that employees and patients are not the only people on the network. Which of the following should the technician do to BEST minimize this issue?
While assisting a customer with an issue, a support representative realizes the appointment is taking longer than expected and will cause the next customer meeting to be delayed by five minutes. Which of the following should the support representative do NEXT?
A user is unable to access a website, which is widely used across the organization, and receives the following error message:
The security certificate presented by this website has expired or is not yet valid.
The technician confirms the website works when accessing it from another computer but not from the user's computer. Which of the following should the technician perform NEXT to troubleshoot the issue?
A technician is troubleshooting a PC that has been performing poorly. Looking at the Task Manager, the technician sees that CPU and memory resources seem fine, but disk throughput is at 100%.
Which of the following types of malware is the system MOST likely infected with?
A user receives an error message from an online banking site that states the following:
Your connection is not private. Authority invalid.
Which of the following actions should the user take NEXT?
A technician is upgrading the backup system for documents at a high-volume law firm. The current backup system can retain no more than three versions of full backups before failing. The law firm is not concerned about restore times but asks the technician to retain more versions when possible. Which of the following backup methods should the technician MOST likely implement?
A neighbor successfully connected to a user's Wi-Fi network. Which of the following should the user do after changing the network configuration to prevent the neighbor from being able to connect again?
A technician is working on a way to register all employee badges and associated computer IDs. Which of the following options should the technician use in order to achieve this objective?
A user contacts a technician about an issue with a laptop. The user states applications open without being launched and the browser redirects when trying to go to certain websites. Which of the following is MOST likely the cause of the user's issue?
A user connects a laptop that is running Windows 10 to a docking station with external monitors when working at a desk. The user would like to close the laptop when it is docked, but the user reports it goes to sleep when it is closed. Which of the following is the best solution to prevent the laptop from going to sleep when it is closed and on the docking station?
A technician thinks that a computer on the network has been infected with malware. The technician attempts several times to use a malware removal tool, but the issue persists. Which of the following should the technician do next?
While accessing a website, a user clicks on a menu option and nothing happens. Which of the following actions should the user take to most likely resolve this issue?
A technician needs to configure laptops so that only administrators can enable virtualization technology if needed. Which of the following should the technician configure?
A user in a SOHO asks an off-site, remote technician to connect securely to the user’s laptop. The technician is able to connect to the VPN but is unable to connect to the user’s laptop. Which of the following settings should the technician review?
A user is unable to open personal files on a PC on a home network. An on-screen message indicates the files are encrypted and demands payment to access the files. Which of the following should a technician recommend the user do first?
Which of the following commands should be used to display current processor activity on a Linux workstation?
A user is unable to log in to a workstation. The user reports an error message about the date being incorrect. A technician reviews the date and verifies it is correct, but the system clock is an hour behind. The technician also determines this workstation is the only one affected. Which of the following is the most likely issue?
An employee utilizes a personal smartphone to work remotely. The employee is unable to reach the portal using the company-provided VPN service. Which of the following describes the cause of the issue?
A user reports that antivirus software indicates a computer is infected with viruses. The user thinks this happened white browsing the internet. The technician does not recognize the interface with which the antivirus message is presented. Which of the following is the NEXT step the technician should take?
Which of the following provide the BEST way to secure physical access to a data cento server room? (Select TWO).
A technician is working with a company to determine the best way to transfer sensitive personal information between offices when conducting business. The company currently uses USB drives and is resistant to change. The company's compliance officer states that all media at rest must be encrypted. Which of the following would be the BEST way to secure the current workflow?
A user calls the help desk to report potential malware on a computer. The anomalous activity began after the user clicked a link to a free gift card in a recent email The technician asks the user to describe any unusual activity, such as slow performance, excessive pop-ups, and browser redirections. Which of the following should the technician do NEXT?
A technician has been tasked with using the fastest and most secure method of logging in to laptops. Which of the following log-in options meets these requirements?
A technician is configuring a new Windows laptop Corporate policy requires that mobile devices make use of full disk encryption at all limes Which of the following encryption solutions should the technician choose?
A technician is asked to resize a partition on the internal storage drive of a computer running macOS. Which of the followings tools should the technician use to accomplish this task?
A company needs to securely dispose of data stored on optical discs. Which of the following is the MOST effective method to accomplish this task?
Someone who is fraudulently claiming to be from a reputable bank calls a company employee. Which of the following describes this incident?
A user reports that the hard drive activity light on a Windows 10 desktop computer has been steadily lit for more than an hour, and performance is severely degraded. Which of the following tabs in Task Manager would contain the information a technician would use to identify the cause of this issue?
A technician has spent hours trying to resolve a computer issue for the company's Chief Executive Officer (CEO). The CEO needs the device returned as soon as possible. Which of the following steps should the technician take NEXT?
A technician suspects a rootkit has been installed and needs to be removed. Which of the following would BEST resolve the issue?
After a failed update, an application no longer launches and generates the following error message: Application needs to be repaired. Which of the following Windows 10 utilities should a technician use to address this concern?
A manager called the help desk to ask for assistance with creating a more secure environment for the finance department- which resides in a non-domain environment. Which of the following would be the BEST method to protect against unauthorized use?
A desktop engineer is deploying a master image. Which of the following should the desktop engineer consider when building the master image? (Select TWO).
A kiosk, which is running Microsoft Windows 10, relies exclusively on a numeric keypad to allow customers to enter their ticket numbers but no other information. If the kiosk is idle for four hours, the login screen locks. Which of the following sign-on options would allow any employee the ability to unlock the kiosk?
A user added a second monitor and wants to extend the display to it. In which of the following Windows settings will the user MOST likely be able to make this change?
A technician is troubleshooting boot times for a user. The technician attempts to use MSConfig to see which programs are starting with the OS but receives a message that it can no longer be used to view startup items. Which of the following programs can the technician use to view startup items?
A technician installed Windows 10 on a workstation. The workstation only has 3.5GB of usable RAM, even though the technician installed 8GB. Which of the following is the MOST likely reason this system is not utilizing all the
available RAM?
A technician is preparing to remediate a Trojan virus that was found on a workstation. Which of the following steps should the technician complete BEFORE removing the virus?
Which of the following options should MOST likely be considered when preserving data from a hard drive for forensic analysis? (Select TWO).
A technician needs to access a Windows 10 desktop on the network in a SOHO using RDP. Although the connection is unsuccessful, the technician is able to ping the computer successfully. Which of the following is MOST likely preventing the connection?
A user lost a company tablet that was used for customer intake at a doctor's office. Which of the following actions would BEST protect against unauthorized access of the data?
A user receives the following error while attempting to boot a computer.
BOOTMGR is missing
press Ctrl+Alt+Del to restart
Which of the following should a desktop engineer attempt FIRST to address this issue?
Which of the following would MOST likely be used to change the security settings on a user's device in a domain environment?
A user requires local administrative access to a workstation. Which of the following Control Panel utilities allows the technician to grant access to the user?
A systems administrator is creating a new document with a list of the websites that users are allowed to access. Which of the following types of documents is the administrator MOST likely creating?
A technician is securing a new Windows 10 workstation and wants to enable a Screensaver lock. Which of the following options in the Windows settings should the technician use?
A large company is selecting a new Windows operating system and needs to ensure it has built-in encryption and endpoint protection. Which of the following Windows versions will MOST likely be selected?
Which of the following macOS features provides the user with a high-level view of all open windows?
Which of the following is used to explain issues that may occur during a change implementation?
A technician is troubleshooting an issue with a computer that contains sensitive information. The technician determines the computer needs to be taken off site for repair. Which of the following should the technician do NEXT?
A company acquired a local office, and a technician is attempting to join the machines at the office to the local domain. The technician notes that the domain join option appears to be missing. Which of the following editions of Windows is MOST likely installed on the machines?
A hard drive that previously contained PII needs to be repurposed for a public access workstation. Which of the following data destruction methods should a technician use to ensure data is completely removed from the hard drive?
A technician needs to join a Windows client to a domain. Which of the following is required?
Which of the following is protected by government policy for end-user information?
While testing a new computer, a technician hears a loud buzzing sound, smells smoke, and sees a flame inside the power supply. Which of the following actions should the technician take first?
Which of the following will automatically map network drives based on Group Policy configuration?
A technician is on-site dealing with an angry customer. The customer thinks the issues have not been addressed, while the technician thinks that the issue has been correctly resolved. Which of the following should the technician do to handle the situation?
A home office user wants to ensure a PC is backed up and protected against local natural disasters and hardware failures. Which of the following would meet the user's requirements?
A technician, who is completing hardware upgrades at a company, is approached by a user who submitted a computer upgrade request. After checking the list of offices to upgrade, the technician finds that the user's office is not listed for an upgrade. Which of the following actions should the technician take next?
A customer's workstation cannot connect to the internet. A technician runs a command on the workstation to view the network settings. The following is a partial readout of the response:

Which of the following is the most likely cause of the issue?
A client’s device was recently used by multiple other users. The client reports their device is now running slower than usual. Which of the following steps should a technician take first? (Select two.)
A company has experienced a ransomware attack. Which of the following is the best way to recover from ransomware?
A user reports a PC is running slowly. The technician suspects it has a badly fragmented hard drive. Which of the following tools should the technician use?
A technician needs to configure a computer for a user to work from home so the user can still securely access the user's shared files and corporate email. Which of the following tools would best accomplish this task?
Security software was accidentally uninstalled from all servers in the environment. After requesting the same version of the software be reinstalled, the security analyst learns that a change request will need to be filled out. Which of the following is the BEST reason to follow the change management process in this scenario?
An incident handler needs to preserve evidence for possible litigation. Which of the following will the incident handler MOST likely do to preserve the evidence?
A user receives a notification indicating the antivirus protection on a company laptop is out of date. A technician is able to ping the user's laptop. The technician checks the antivirus parent servers and sees the latest signatures have been installed. The technician then checks the user's laptop and finds the antivirus engine and definitions are current. Which of the following has MOST likely occurred?
A technician is installing new network equipment in a SOHO and wants to ensure the equipment is secured against external threats on the Internet. Which of the following actions should the technician do FIRST?
A user attempts to open some files, but a message appears stating that the files are encrypted. The user was able to access these files before without receiving this message and no changes have been made within the company. Which of the following has infected the computer?
A company is Issuing smartphones to employees and needs to ensure data is secure if the devices are lost or stolen. Which of the following provides the BEST solution?
The command cac cor.ptia. txt was issued on a Linux terminal. Which of the following results should be expected?
An executive has contacted you through the help-desk chat support about an issue with a mobile device.
Assist the executive to help resolve the issue.
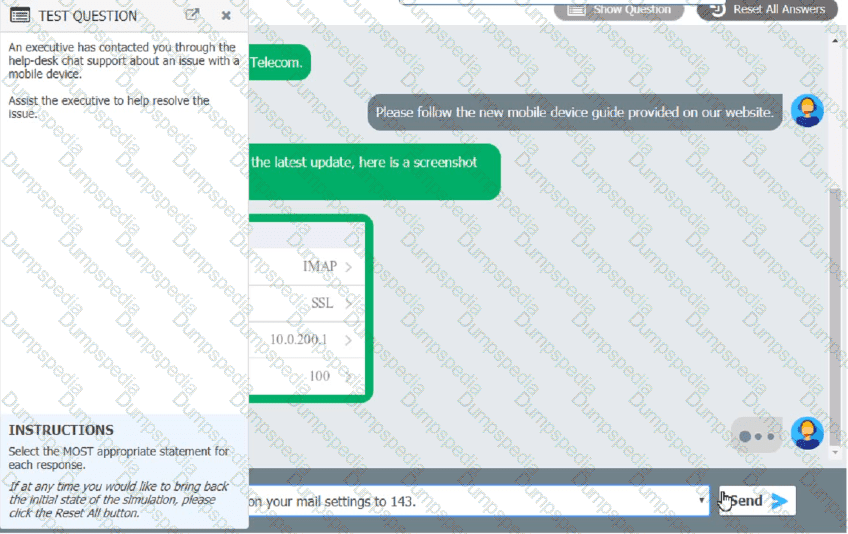
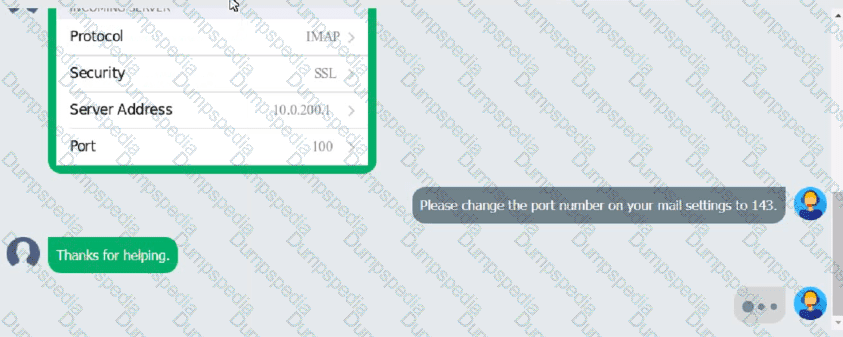
Which of the following should be done NEXT?
A network administrator is deploying a client certificate lo be used for Wi-Fi access for all devices m an organization The certificate will be used in conjunction with the user's existing username and password Which of the following BEST describes the security benefits realized after this deployment?
A call center technician receives a call from a user asking how to update Windows Which of the following describes what the technician should do?
A technician is replacing the processor in a desktop computer prior to opening the computer, the technician wants to ensure the internal components are protected. Which of the following safety procedures would BEST protect the components in the PC? (Select TWO).
A user corrects a laptop that is running Windows 10 to a docking station with external monitors when working at a desk. The user would like to close the laptop when it is docked, but the user reports it goes to sleep when it is closed. Which of the following is the BEST solution to prevent the laptop from going to sleep when it is closed and on the docking station?
Which of the following Linux commands would be used to install an application?
Which of the following could be used to implement secure physical access to a data center?
A user reports a computer is running slow. Which of the following tools will help a technician identify the issue?
During a recent flight an executive unexpectedly received several dog and cat pictures while trying to watch a movie via in-flight Wi-Fi on an iPhone. The executive has no records of any contacts sending pictures like these and has not seen these pictures before. To BEST resolve this issue, the executive should:
A technician needs to interconnect two offices to the main branch while complying with good practices and security standards. Which of the following should the technician implement?
A user's smartphone data usage is well above average. The user suspects an installed application is transmitting data in the background. The user would like to be alerted when an application attempts to communicate with the internet. Which of the following BEST addresses the user's concern?
A technician is configuring a SOHO device Company policy dictates that static IP addresses cannot be used. The company wants the server to maintain the same IP address at all times. Which of the following should the technician use?
A technician receives a ticket indicating the user cannot resolve external web pages However, specific IP addresses are working. Which of the following does the technician MOST likely need to change on the workstation to resolve the issue?
Which of the following must be maintained throughout the forensic evidence life cycle when dealing with a piece of evidence?
A user enabled a mobile device's screen lock function with pattern unlock. The user is concerned someone could access the mobile device by repeatedly attempting random patterns to unlock the device. Which of the following features BEST addresses the user's concern?
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
Click on individual tickers to see the ticket details. View attachments to determine the problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.

A laptop that was in the evidence room of a police station is missing. Which of the following is the best reason to refer to chain of custody documentation?
A network technician is deploying a new machine in a small branch office that does not have a DHCP server. The new machine automatically receives the IP address of 169.254.0.2 and is unable to communicate with the rest of the network. Which of the following would restore communication?
Static entry
A user's application is unresponsive. Which of the following Task Manager tabs will allow the user to address the situation?
A technician needs to track evidence for a forensic investigation on a Windows computer. Which of the following describes this process?
A technician is troubleshooting a Windows 10 PC that is unable to start the GUI. A new SSD and a new copy of Windows were recently installed on the PC. Which of the following is the most appropriate command to use to fix the issue?
msconfig
A user is unable to access a remote server from a corporate desktop computer using the appropriate terminal emulation program. The user contacts the help desk to report the issue. Which of the following clarifying questions would be most effective for the help desk technician to ask the user in order to understand the issue?
A user reports that an air-gapped computer may have been infected with a virus after the user transferred files from a USB drive. The technician runs a computer scan with Windows Defender but does not find an infection. Which of the following actions should the technician take next? (Select two).
Which of the following languages is used for scripting the creation of Active Directory accounts?
A user receives a call from someone claiming to be a technical support agent. The caller asks the user to log in to the computer.
Which of the following security measures should the user take to ensure security and privacy?
A user's company phone was stolen. Which of the following should a technician do next?
A large company is changing its password length requirements. The Chief Information Officer is mandating that passwords now be at least 12 characters long, instead of 10. Which of the following should be used to adjust this setting?
Group Policy
A systems administrator received a request to limit the amount of cellular data a user's Windows 10 tablet can utilize when traveling. Which of the following can the administrator do to best solve the user's issue?
An office is experiencing constant connection attempts to the corporate Wi-Fi. Which of the following should be disabled to mitigate connection attempts?
SSID
A client wants a technician to set up a proxy server in a branch office to manage internet access. This involves configuring the workstations to use the new proxy server. Which of the following Internet Options tabs in Control Panel would be most appropriate for the technician to use to configure the settings?
A technician needs to reimage a desktop in an area without network access. Which of the following should the technician use? (Select two).
A technician is building a new desktop machine for a user who will be using the workstation to render 3-D promotional movies. Which of the following is the most important component?
Which of the following environments allows for the testing of critical systems without the risk of them being negatively impacted by changes?
A technician is partitioning a hard disk. The five primary partitions should contain 4TB of free space. Which of the following partition styles should the technician use to partition the device?
A hotel's Wi-Fi was used to steal information on a corporate laptop. A technician notes the following security log:
SRC: 192.168.1.1/secrets.zip Protocol SMB >> DST: 192.168.1.50/capture
The technician analyses the following Windows firewall information:
Which of the following protocols most likely allowed the data theft to occur?
A student is setting up a new Windows 10 laptop for the upcoming semester. The student is interested in customizing the wallpaper. Which of the following should the student use to change the wallpaper?
A user recently purchased a second monitor and wants to extend the Windows desktop to the new screen. Which of the following Control Panel options should a technician adjust to help the user?
Color Management
A computer technician is investigating a computer that is not booting. The user reports that the computer was working prior to shutting it down last night. The technician notices a removable USB device is inserted, and the user explains the device is a prize the user received in the mail yesterday. Which of the following types of attacks does this describe?
A technician is troubleshooting a PC because the user has reported strange pop-up windows and computer performance issues. Which of the following actions should the technician take next?
When trying to access a secure internal network, the user receives an error messaging stating, "There is a problem with this website's security certificate." The user reboots the desktop and tries to access the website again, but the issue persists. Which of the following should the user do to prevent this error from reoccurring?
Which of the following would allow physical access to a restricted area while maintaining a record of events?
A technician is moving a Windows workstation from the accounting department to the sales department and needs to update the IP and gateway settings. Which of the following Control Panel utilities should the technician use?
Which of the following is also known as something you know, something you have, and something you are?
ACL
A user wants to acquire antivirus software for a SOHO PC. A technician recommends a licensed software product, but the user does not want to pay for a license. Which of the following license types should the technician recommend?
Antivirus software indicates that a workstation is infected with ransomware that cannot be quarantined. Which of the following should be performed first to prevent further damage to the host and other systems?
Turn off the machine.
Which of the following file extensions should a technician use for a PowerShell script?
Which of the following environmental factors are most important to consider when planning the configuration of a data center? (Select two).
Which of the following should be documented to ensure that the change management plan is followed?
A technician is modifying the default home page of all the workstations in a company. Which of the following will help to implement this change?
The calendar application on an employee's smartphone is experiencing frequent crashes, and the smartphone has become unresponsive. Which of the following should a technician do first to resolve the issue?
An organization is creating guidelines for the incorporation of generative Al solutions. In which of the following would these guidelines be published?
Standard operating procedure
A customer installed a new web browser from an unsolicited USB drive that the customer received in the mail. The browser is not working as expected, and internet searches are redirected to another site. Which of the following should the user do next after uninstalling the browser?
A user is setting up backups on a workstation. The user wants to ensure that the restore process is as simple as possible. Which of the following backup types should the user select?