A developer has written an Amazon kinesis Data streams application. As usage grows and traffic over time, the application is regularly receiving provisionedThroughputExceededException error messages.
Which steps should the Developer take to resolve the error? (Select Two.)
An AWS Lambda function must access an external site by using a regularly rotated user name and password. These items must be kept securely and cannot be stored in the function code.
What combination of AWS services can be used to accomplish this? (Choose two.)
While developing an application that runs on Amazon EC2 in an Amazon VPC, a Developer identifies the need for centralized storage of application-level logs.
Which AWS service can be used to securely store these logs?
A software engineer developed an AWS Lambda function in Node.js to do some CPU-intensive data processing. With the default settings, the Lambda function takes about 5 minutes to complete.
Which approach should a developer take to increase the speed of completion''
A developer is migrating code to an AWS Lambda function that will access an Amazon Aurora MySQL database.
What is the MOST secure way to authenticate the function to the database?
A company is creating a REST service using an Amazon API Gateway with AWS Lambda integration. The service must run different versions for testing purposes.
What would be the BEST way to accomplish this?
A development team is creating a new application designed to run on AWS. While the test and production environments will run on Amazon EC2 instances, developers will each run their own environment on their laptops.
Which of the following is the simplest and MOST secure way to access AWS services from the local development machines?
An advertising company has a dynamic website with heavy traffic. The company wants to migrate the website infrastructure to AWS to handle everything except website development.
Which solution BEST meets these requirements?
An application is running on a cluster of Amazon EC2 instance. While trying to read objects stored within a single Amazon S3 bucket that are encrypted with server-side encryption with AWS KMS managed keys (SSE-KMS), the application receives the following error:
Service : AWSKMS: Status Code: 400: Code : ThrottlingException
Which combination of steps should be taken to prevent this failure? (Select TWO.)
A Developer is storing sensitive documents in Amazon S3 that will require encryption at rest. The encryption keys must be rotated annually, at least.
What is the easiest way to achieve this?
A developer is writing an AWS Lambda function. The Lambda function needs to access items that are stored in an Amazon DynamoDB table.
What is the MOST secure way to configure this access for the Lambda function?
A developer is designing a serverless application that customers use to select seats for a concert venue. Customers send the ticket requests to an Amazon API Gateway API with an AWS Lambda function that acknowledges the order and generates an order ID. The application includes two additional Lambda functions: one for inventory management and one for payment processing. These two Lambda functions run in parallel and write the order to an Amazon Dynamo DB table.
The application must provide seats to customers according to the following requirements. If a seat is accidently sold more than once, the first order that the application received must get the seat. In these cases, the application must process the payment for only the first order. However, if the first order is rejected during payment processing, the second order must get the seat. In these cases, the application must process the payment for the second order.
Which solution will meet these requirements?
A developer deploys an ecommerce application on Amazon EC2 instances behind an Application Load Balancer (ALB). The instances run in an Amazon EC2 Auto Scaling group. The EC2 instances are based on an Amazon Machine Image (AMI) that uses an Amazon Elastic Block Store (Amazon EBS) root volume. After deployment, the developer notices that a third of the instances seem to be idle. These instances are not receiving requests from the load balancer. The developer verifies that all the instances are registered with the load balancer. The developer must implement a solution to allow the EC2 instances to receive requests from the load balancer.
Which action will meet this requirement?
A company is running an application on AWS Elastic Beanstalk in a single-instance environment. The company's deployments must avoid any downtime. Which deployment option will meet these requirements?
A developer deployed an application to an Amazon EC2 instance. The application needs to know the public IPv4 address of the instance. How can the application find this information?
A company is using Amazon Cognito user pools for sign-up and login functionality for a web application. The company is using Amazon RDS for the application's data persistence and is using Amazon API Gateway and AWS Lambda for the application's API functionality. Users must provide their first name, last name, email address, and phone number to sign up. All API endpoints have a Cognito user pool authorizer to guard against unauthenticated requests.
A developer wants to show a personalized welcome screen to users after they log in. The welcome screen needs to show the user's first name and the user's previous login date. According to company policy. developers who work on the web application cannot store any personally identifiable information in RDS instances.
Which solution should the developer implement to meet these requirements?
A developer is working on an application that is deployed on an Amazon EC2 instance. The application needs to transfer a file to an Amazon S3 bucket. What should the developer do to authenticate the application's access to the S3 bucket in the MOST secure way?
A developer is running an application on an Amazon EC2 instance. When the application tries to read an Amazon S3 bucket, the application fails. The developer notices that the associated IAM role is missing the S3 read permission. The developer needs to give the application the ability to read the S3 bucket.
Which solution will meet this requirement with the LEAST application disruption?
A company uses AWS CloudFormation to deploy an application that uses an Amazon API Gateway REST API with AWS Lambda function integration. The application uses Amazon DynamoDB for data persistence. The application has three stages, development, testing, and production. Each stage uses its own DynamoDB table.
The company has encountered unexpected issues when promoting changes to the production stage. The changes were successful in the development and testing stages. A developer needs to route 20% of the traffic to the new production stage API with the next production release. The developer needs to route the remaining 80% of the traffic to the existing production stage. The solution must minimize the number of errors that any single customer experiences.
Which approach should the developer take to meet these requirements?
A developer is building varKHJS microservices for an application that will run on Amazon EC2 instances. The developer needs to monitor the end-to-end view of the requests between the microservices and debug any issues in the various microservices.
What should the developer do to accomplish these tasks?
An open-source map application gathers data from several geolocation APIs. The application's source code repository is public and can be used by anyone, but the geolocation APIs must not be directly accessible.
A developer must implement a solution to prevent the credentials that are used to access the APIs from becoming public. The solution also must ensure that the application still functions properly.
Which solution will meet these requirements MOST cost-effectively?
A developer is writing an application that will run on Amazon EC2 instances in an Auto Scaling group. The developer wants to externalize the session state to support the application. Miich AWS services or resources can the developer use to meet these requirements? (Select TWO.)
A company has an application that provides blog hosting services to its customers. The application includes an Amazon DynamoDB table with a primary key The primary key consists of the customers' UserName as a partition key and the NumberOIBIogs as a sort key. The application stores the TotalReactionsOnBlogs as an attribute on the same DynamoDB table.
A developer needs to implement an operation to retrieve the top 10 customers based on the greatest number of reactions on their blogs This operation must not consume the DynamoDB table's existing read capacity.
What should the developer do to meet these requirements in the MOST operationally efficient manner?
A developer is writing a web application that allows users to sign in. The application will run on Amazon EC2 instances behind an Application Load Balancer (ALB). The instances will run in an Auto Scaling group across multiple Availability Zones.
How can the developer ensure that users stay signed in when the Auto Scaling group is scaled down?
A business intelligence application runs on Amazon Elastic Container Service (Amazon ECS) on AWS Fargate. Application-level audits require a searchable log of all API calls from users to the application. The application’s developers must store the logs centrally on AWS.
Which solution will meet these requirements?
A distributed application includes an AWS Lambda function that runs successfully in the DEV environment with 128 MB of memory assigned. The same function is failing in the TEST environment. The developer is monitoring the application using AWS X-Ray, but the Lambda function cannot be seen on the X-Ray service graph. The Lambda execution role has AWS X-Ray permissions
What is the MOST LIKELY cause for AWS X-Ray not showing any data for the Lambda function?
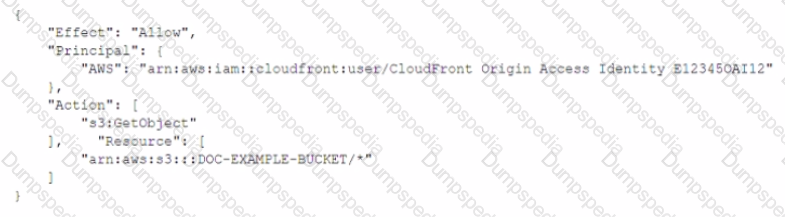
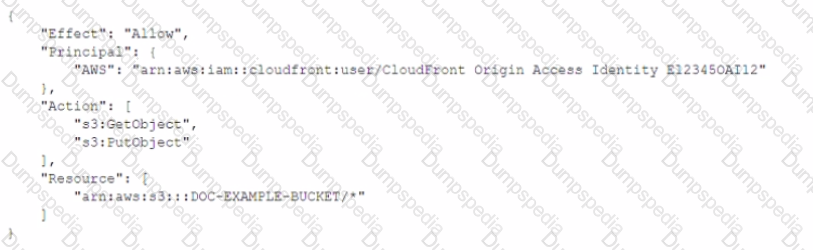
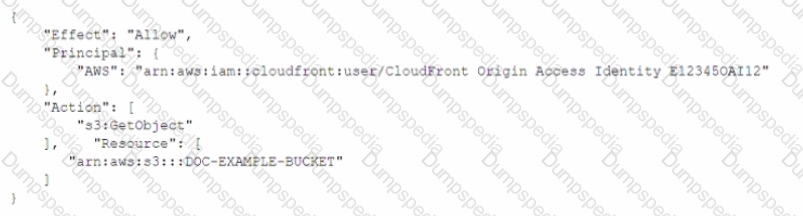
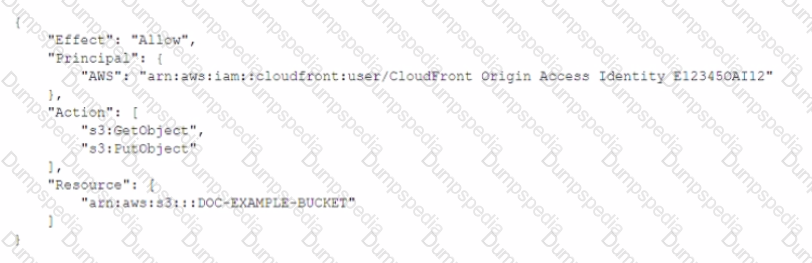
A developer needs to secure the static assets in a company's Amazon S3 bucket that is named DOC-EXAMPLE-BUCKET. The company has an Amazon CtoudFront distribution that serves the S3 bucket's assets to the public. The developer has already created the origin access identity (OAI) and has associated the OAI with the distribution. The developer must write a bucket policy that allows only the CloudFront distribution to access the S3 bucket
Which policy will meet this requirement MOST securely?
A)
B)
C)
D)
A development team set up a pipeline to launch a test environment. The developers want to automate tests for their application. The team created an AWS CodePipeline stage to deploy the application to a test environment in batches using AWS Elastic Beanstalk. A later CodePipeline stage contains a single action that uses AWS CodeBuild to run numerous automated Selenium-based tests on the deployed application. The team must speed up the pipeline without removing any of the individual tests.
Which set of actions will MOST effectively speed up application deployment and testing?
\ developer is designing a serverless application for a game in which users register and log in through a web browser. The application makes requests on behalf of users to a set of AWS Lambda functions that un behind an Amazon API Gateway HTTP API.
rhe developer needs to implement a solution to register and log in users on the application's sign-in page. The solution must minimize operational overhead and must minimize ongoing management of user identities.
Which solution will meet these requirements?
A developer is building an application using an Amazon API Gateway REST API backed by an AWS Lambda function that interacts with an Amazon DynamoDB table During testing, the developer observes high latency when making requests to the API
How can the developer evaluate the end-to-end latency and identify performance bottlenecks?
A company is using an AWS Lambda function to process records from an Amazon Kinesis data stream The company recently observed slow processing of the records. A developer notices that the iterator age metric for the function is Increasing and that the Lambda run duration is constantly above normal.
Which actions should the developer take to increase the processing speed? (Select TWO.)
A developer has launched an application that calls an API by way of Amazon API Gateway. It offers information that changes several times a day, but is not updated in real time. The application has become so popular that the API endpoint is overloaded and that traffic to the endpoint must be reduced.
What can the developer do to address the performance issues?
A team deployed an AWS CloudFormaiion template to update a stack that already included an Amazon RDS DB instance However, before the deployment of the update the team changed the name of the DB instance on the template by mistake The DeletionPoIicy attribute for all resources was not changed from the default values
What will be the result of this mistake?
A company is launching a new web application in the AWS Cloud. The company's development team is using AWS Elastic Beanstalk for deployment and maintenance. According to the company's change management process, the development team must evaluate changes for a specific time period before completing the rollout.
Which deployment policy meets this requirement?
A developer is changing the configuration for a CPU-intensive AWS Lambda function that runs once an hour. The function usually takes 45 seconds to run, but sometimes the run time is up to 1 minute. The timeout parameter is set to 3 minutes, and all other parameters are set to default.
The developer needs to optimize the run time of this function.
Which solution will meet this requirement?
A company is running a custom application on a set of on-premises Linux servers that are accessed using Amazon API Gateway. AWS X-Ray tracing has been enabled on the API test stage
How can a developer enable X-Ray tracing on the on-premises servers with the LEAST amount of configuration''
A company runs its APIs using Amazon API Gateway in front of AWS Lambda functions The company wants to add logging at the API level Each API must have production and development environments The developer wants to enable different logging levels in both environments.
How can these requirements be met?
A developer is working on a serverless application. The application uses Amazon API Gateway. AWS Lambda functions that are written in Python, and Amazon DynamoDB.
Which combination of steps should the developer take so that the Lambda functions can be debugged in the event of application failures? (Select TWO )
A developer is leveraging a Border Gateway Protocol (BGP)-based AWS VPN connection to connect from on-premises to Amazon EC2 instances in the developer's account The developer is able to access an EC2 instance in subnet A, but is unable to access an EC2 instance in subnet B in the same VPC
Which logs can the developer use to verify whether the traffic is reaching subnet B?
A company hosts a microservices application that uses Amazon API Gateway, AWS Lambda, Amazon Simple Queue Service (Amazon SOS), and Amazon DynamoDB, One of the Lambda functions adds messages to an SOS FIFO queue.
When a developer checks the application logs, the developer finds a few duplicated items in a DynamoDB table. The items were inserted by another polling function that processes messages from the queue.
What is the MOST likely cause of this issue?
A developer wants to modify the following AWS Cloud Formation template to embed another CloudFormation stack:
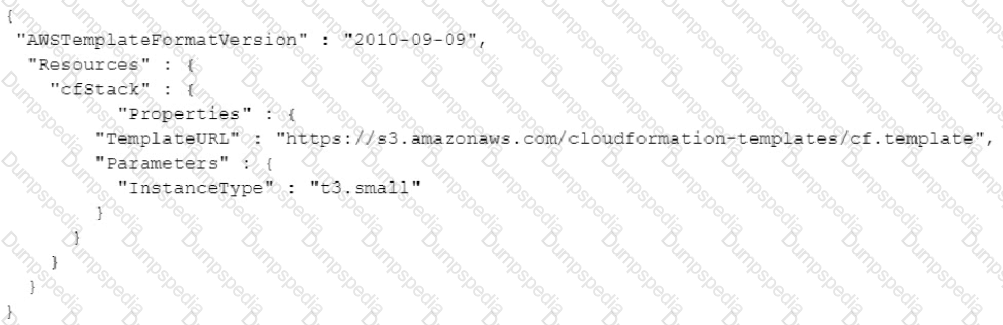
Which syntax should the developer add to the blank line of the CloudFormation template to meet this requirement?
A developer works in an environment with multiple AWS accounts that have AWS Lambda functions processing the same 100 KB payloads. The developer wants to centralize the point of origin of the payloads to one account and have all the Lambda functions be invoked whenever the initiating event occurs in the parent account.
How can the developer design the workflow in the MOST efficient way, so all the multi-account Lambda functions get invoked when the event occurs?
A legacy service has an XML-based SOAP interface. The Developer wants to expose the functionality of the service to external clients with the Amazon API Gateway. Which technique will accomplish this?
A movie fan club hosts a serverless web application in an Amazon S3 bucket. The application uses an AWS Lambda function that is exposed by an Amazon API Gateway API. The function queries an Amazon DynamoDB table to list actors sorted by movie. In the DynamoDB table. Actor is the primary key, Movie is the sort key, and Role and Year are attributes.
In the web application, a developer wants to add a page that is named Phase 1 that lists only the movies that were released between 2008 and 2012. The developer needs to fetch the Phase 1 items in a way that minimizes the impact on the DynamoDB table.
Which solution will meet these requirements?
An application that is running on Amazon EC2 instances stores data in an Amazon S3 bucket. All the data must be encrypted in transit. How can a developer ensure that all traffic to the S3 bucket is encrypted?
A developer is monitoring an application that runs on an Amazon EC2 instance. The developer has configured a custom Amazon CloudWatch metric with d#ta granularity of 1 second. If any issues occur, the developer wants to be notified within 30 seconds by Amazon Simple Notification Service (Amazon SNS).
What should the developer do to meet this requirement?
A company wants to implement authentication for its new REST service using Amazon API Gateway. To authenticate the calls, each request must include HTTP headers with a client ID and user ID. These credentials must be compared to authentication data in an Amazon DynamoDB table.
What MUST the company do to implement this authentication in API Gateway?
An application uses Lambda functions to extract metadata from files uploaded to an S3 bucket; the metadata is stored in Amazon DynamoDB. The application starts behaving unexpectedly, and the Developer wants to examine the logs of the Lambda function code for errors.
Based on this system configuration, where would the Developer find the logs?
A developer is working on an AWS Lambda function that accesses Amazon DynamoDB The Lambda function must retrieve an item and update some of its attributes. or create the item if it does not exist The Lambda function has access to the primary key.
Which IAM permissions should the developer request for the Lambda function to achieve this functionality?
A company is running a Docker application on Amazon ECS. The application must scale based on user load in the last 15 seconds.
How should a Developer instrument the code so that the requirement can be met?
A developer needs temporary access to resources in a second account
What is the MOST secure way to achieve this?
A developer has written an Amazon Kinesis Data Streams application. As usage grows and traffic increases over time, the application is regularly receiving ProvisionedThroughputExceededException error messages
Which steps should the developer take to resolve the error? (Select TWO.)
A team of Developers must migrate an application running inside an AWS Elastic Beanstalk environment from a Classic Load Balancer to an Application Load Balancer.
Which steps should be taken to accomplish the task using the AWS Management Console?
When developing an AWS Lambda function that processes Amazon Kinesis Data Streams, Administrators within the company must receive a notice that includes the processed data.
How should the Developer write the function to send processed data to the Administrators?
A Development team wants to instrument their code to provide more detailed information to AWS X-Ray than simple outgoing and incoming requests. This will generate large amounts of data, so the Development team wants to implement indexing so they can filter the data.
What should the Development team do to achieve this?
n application running on an Amazon Linux EC2 instance needs to manage the AWS infrastructure.
How can the EC2 instance be configured to make AWS API calls securely?
A company's fleet of Amazon EC2 instances receives data from millions of users through an API. The servers batch the data, add an object for each user, and upload the objects to an S3 bucket to ensure high access rates The object attributes are Customer ID, Server ID, TS-Server (TimeStamp and Server ID) the size of the object, and a timestamp A developer wants to find all the objects for a given user collected during a specified time range
After creating an S3 object created event, how can the developer achieve this requirement^
A developer is using Amazon S3 as the event source that invokes a Lambda function when new objects are created in the bucket The event source mapping Information Is stored in the bucket notification configuration The developer is working with different versions of the Lambda function, and has a constant need to update notification configuration so that Amazon S3 invokes the correct version
What is the MOST efficient and effective way to achieve mapping Between the S3 event and Lambda?
An IAM role is attached to an Amazon EC2 instance that explicitly denies access to all Amazon S3 API actions. The EC2 instance credentials file specifies the IAM access key and secret access key, which allow full administrative access.
Given that multiple modes of IAM access are present for this EC2 instance, which of the following is correct?
A company is adding items to an Amazon DynamoDB table from an AWS Lambda function that is written in Python A developer needs to implement a solution that inserts records in the DynamoDB table and performs automatic retry when the insert fails
Which solution meets these requirements with MINIMUM code changes?
A developer is building a static, client-side rendered website that is powered by ReactJS The code has no server-side generated components and does not need to run any programming languages on the server However the code serves static HTML, CSS, and JavaScript to the client on each request The developer's solution to host the website must maximize performance and cost-effectiveness
Which combination of AWS services or resources should the developer use to meet these requirements?
A developer needs to deploy a new version to an AWS Elastic Beanstalk application How can the developer accomplish this task?
A company recently experienced some unexpected downtime. After investigating, the company determines that a developer mistakenly terminated several production Amazon EC2 instances.
What should the company do to BEST protect against accidental terminations in the future.
A company has deployed an application on AWS Elastic Beanstalk The company has configured the Auto Scaling group that is associated with the Elastic Beanstalk environment to have five Amazon EC2 instances If the capacity is fewer than four EC2 instances during the deployment, application performance degrades The company is using the all-at-once deployment policy
What is the MOST cost-effective way to solve the deployment issue1?
A developer is using Amazon DynamoDB to store application data . The developer wants to further improve application performance by reducing response limes for read and write operations.
Which DynamoDB feature should be used to meet these requirement?
A developer has written a multi-threaded application that is running on a fleet of Amazon EC2 instances. The operations team has requested a graphical method to monitor the number of running threads over time.
What is the MOST efficient way to fulfill this request?
Company D is running their corporate website on Amazon S3 accessed from http//www.companyd.com. Their marketing team has published new web fonts to a separate S3 bucket accessed by the S3 endpoint https://s3-us-west-1.amazonaws.com/cdfonts. While testing the new web fonts, Company D recognized the web fonts are being blocked by the browser.
What should Company D do to prevent the web fonts from being blocked by the browser?
Developer is creating an AWS Lambda function to process a stream of data from an Amazon Kinesis Data Stream. When the Lambda function parses the data and encounters a missing field, it exits the function with an error. The function is generating duplicate records from the Kinesis stream. When the Developer looks at the stream output without the Lambda function, there are no duplicate records.
What is the reason for the duplicates?
A Developer is creating a web application that requires authentication, but also needs to support guest access
to provide users limited access without having to authenticate. What service can provide support for the application to allow guest access?
A Developer must re-implement the business logic for an order fulfilment system. The business logic has to make requests to multiple vendors to decide where to purchase an item. The whole process can take up to a week to complete.
What is the MOST efficient and SIMPLEST way to implement a system that meets these requirements?
What happens, by default, when one of the resources in a CloudFormation stack cannot be created?
A Developer is writing an imaging micro service on AWS Lambda. The service is dependent on several libraries that are not available in the Lambda runtime environment.
Which strategy should the Developer follow to create the Lambda deployment package?
How is provisioned throughput affected by the chosen consistency model when reading data from a DynamoDB table?
In DynamoDB, what type of HTTP response codes indicate that a problem was found with the client request sent to the service?
You have written an application that uses the Elastic Load Balancing service to spread traffic to several web servers. Your users complain that they are sometimes forced to login again in the middle of using your application, after they have already logged in. This is not behavior you have designed.
What is a possible solution to prevent this happening?
During non-peak hours, a Developer wants to minimize the execution time of a full Amazon DynamoDB table scan without affecting normal workloads. The workloads average half of the strongly consistent read capacity units during non-peak hours.
How would the Developer optimize this scan?
If an application is storing hourly log files from thousands of instances from a high traffic web site, which naming scheme would give optimal performance on S3?
A company wants to migrate its web application to AWS and leverage Auto Scaling to handle pear workloads.
The Solutions Architect determined that the best metric for an Auto Scaling event is the number of concurrent users.
Based on this information, what should the Developer use to autoscale based on concurrent users?
A company is providing services to many downstream consumers. Each consumer may connect to one or more services. This has resulted in a complex architecture that is difficult to manage and does not scale well. The company needs a single interface to manage these services to consumers.
Which AWS service should be used to refactor this architecture?
Which EC2 API call would you use to retrieve a list of Amazon Machine Images (AMIs)?
A Developer needs to use AWS X-Ray to monitor an application that is deployed on EC2 instances.
What steps have to be executed to perform the monitoring?
An existing serverless application processes uploaded image files. The process currently uses a single Lambda function that takes an image file, performs the processing, and stores the file in Amazon S3. Users of the application now require thumbnail generation of the images. Users want to avoid any impact to the time it takes to perform the image uploads.
How can thumbnail generation be added to the application, meeting user requirements while minimizing changes to existing code?
A company needs to secure its existing website running behind an Elastic Load Balancer. The website’s Amazon EC2 instances are CPU-constrained.
What should be done to secure the website while not increasing the CPU load on the EC2 web servers? (Select TWO.)
A Developer has created a large Lambda function, and deployment is failing with the following error:
ClientError: An error occurred (InvalidParameterValueException) when calling the
CreateFunction operation: Unzipped size must be smaller than XXXXXXXXX bytes’, where XXXXXXXXX is the current Lambda limit
What can the Developer do to fix this problem?
An AWS Lambda function generates a 3MB JSON file and then uploads it to an Amazon S3 bucket daily. The file contains sensitive information, so the Developer must ensure that it is encrypted before uploading to the bucket.
Which of the following modifications should the Developer make to ensure that the data is encrypted before uploading it to the bucket?
What are the steps to using the AWS CLI to launch a templatized serverless application?